Running a vulnerability scan
The following example shows how to configure the necessary components to run the vulnerability detection process.
Enable the agent module used to collect installed packages on the monitored system.
It can be done by adding the following block of settings to your shared agent configuration file:
<wodle name="syscollector"> <disabled>no</disabled> <interval>1h</interval> <packages>yes</packages> </wodle>If you want to scan vulnerabilities in Windows agents, you will also have to add the
osandhotfixesscans:<wodle name="syscollector"> <disabled>no</disabled> <interval>1h</interval> <packages>yes</packages> <os>yes</os> <hotfixes>yes</hotfixes> </wodle>These scans are enabled by default. For more information about the inventory module, check Syscollector settings.
Enable the manager module used to detect vulnerabilities.
You can do this adding a block like the following to your manager configuration file:
<vulnerability-detector> <enabled>yes</enabled> <interval>5m</interval> <run_on_start>yes</run_on_start> <provider name="canonical"> <enabled>yes</enabled> <os>bionic</os> <update_interval>1h</update_interval> </provider> </vulnerability-detector>Remember to restart the manager to apply the changes:
For Systemd:
# systemctl restart wazuh-manager
For SysV Init:
# service wazuh-manager restart
Check Vulnerability detector settings for more details.
The following fields are included in every alert:
CVE: The Common Vulnerabilities and Exposures identifier for the corresponding vulnerability.
Title: Short description of the impact of vulnerability.
Severity: It specifies the impact of the vulnerability in terms of security.
Published: Date when the vulnerability was included in the official database.
Updated: Date of the last vulnerability update.
Package: Information about the affected package.
Reference: URL of the official database website with extra information on the vulnerability.
Rationale: Broad description of the vulnerability. To avoid extra-data, this field only appears if no reference is included.
State: This field informs if it exists a patch for the vulnerability (fixed) or instead, its state.
Condition: Reason for reporting the vulnerability.
CWE: The Common Weakness Enumeration reference.
Bugzilla reference: Link to the reference of the vulnerability in Bugzilla.
CVSS: Vulnerability assessment according to the Common Vulnerability Scoring System (versions 2 and 3).
Advisories: Red Hat security advisories.
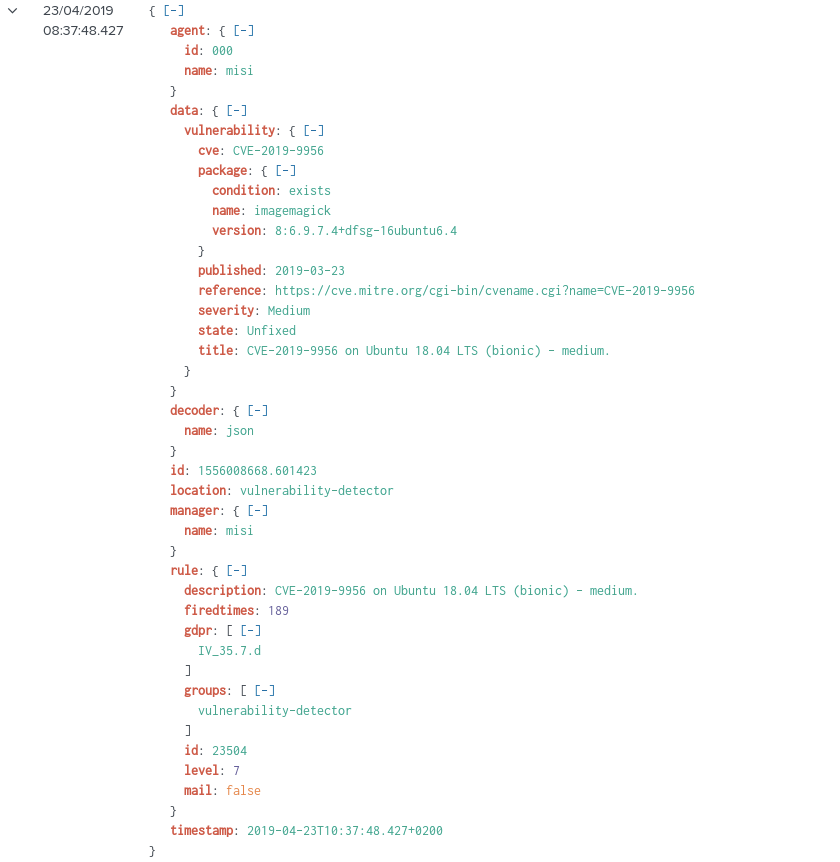
See below for examples of alerts:
** Alert 1571137967.2083: - vulnerability-detector,gdpr_IV_35.7.d,
2019 Oct 15 11:12:47 c31dd66f7e82->vulnerability-detector
Rule: 23503 (level 5) -> 'CVE-2018-5710 on Ubuntu 18.04 LTS (bionic) - low.'
{"vulnerability":{"cve":"CVE-2018-5710","title":"CVE-2018-5710 on Ubuntu 18.04 LTS (bionic) - low.","severity":"Low","published":"2018-01-16T09:29:00Z","state":"Fixed","package":{"name":"libgssapi-krb5-2","version":"1.16-2ubuntu0.1","architecture":"amd64"},"condition":"Package less than 1.16.1-1","reference":"https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5710"}}
vulnerability.cve: CVE-2018-5710
vulnerability.title: CVE-2018-5710 on Ubuntu 18.04 LTS (bionic) - low.
vulnerability.severity: Low
vulnerability.published: 2018-01-16T09:29:00Z
vulnerability.state: Fixed
vulnerability.package.name: libgssapi-krb5-2
vulnerability.package.version: 1.16-2ubuntu0.1
vulnerability.package.architecture: amd64
vulnerability.package.condition: Package less than 1.16.1-1
vulnerability.reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5710
** Alert 1571138526.1319438: - vulnerability-detector,gdpr_IV_35.7.d,
2019 Oct 15 11:22:06 (b38c18f6620d) 172.17.0.3->vulnerability-detector
Rule: 23504 (level 7) -> 'nss: Empty or malformed p256-ECDH public keys may trigger a segmentation fault'
{"vulnerability":{"cve":"CVE-2019-11729","title":"nss: Empty or malformed p256-ECDH public keys may trigger a segmentation fault","severity":"Medium","published":"2019-07-10T00:00:00Z","state":"Fixed","cvss":{"cvss3":{}},"package":{"name":"nss","version":"3.36.0-9.el6_10","architecture":"x86_64"},"condition":"Package less than 3.44.0-7.el8_0","advisories":"RHSA-2019:1951","cwe_reference":"CWE-120","bugzilla_reference":"https://bugzilla.redhat.com/show_bug.cgi?id=1728437","reference":"https://access.redhat.com/security/cve/CVE-2019-11729"}}
vulnerability.cve: CVE-2019-11729
vulnerability.title: nss: Empty or malformed p256-ECDH public keys may trigger a segmentation fault
vulnerability.severity: Medium
vulnerability.published: 2019-07-10T00:00:00Z
vulnerability.state: Fixed
vulnerability.package.name: nss
vulnerability.package.version: 3.36.0-9.el6_10
vulnerability.package.architecture: x86_64
vulnerability.package.condition: Package less than 3.44.0-7.el8_0
vulnerability.advisories: RHSA-2019:1951
vulnerability.cwe_reference: CWE-120
vulnerability.bugzilla_reference: https://bugzilla.redhat.com/show_bug.cgi?id=1728437
vulnerability.reference: https://access.redhat.com/security/cve/CVE-2019-11729
** Alert 1571138525.1311925: - vulnerability-detector,gdpr_IV_35.7.d,
2019 Oct 15 11:22:05 (agwin) 172.16.210.128->vulnerability-detector
Rule: 23504 (level 7) -> 'The Windows kernel in Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows authenticated attackers to obtain sensitive information via a specially crafted document, aka "Windows Kernel Information Disclosure Vulnerability," a different vulnerability than CVE-2017-0220, CVE-2017-0258, and CVE-2017-0259.'
{"vulnerability":{"cve":"CVE-2017-0175","title":"The Windows kernel in Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows authenticated attackers to obtain sensitive information via a specially crafted document, aka \"Windows Kernel Information Disclosure Vulnerability,\" a different vulnerability than CVE-2017-0220, CVE-2017-0258, and CVE-2017-0259.","severity":"Medium","published":"2017-05-12","updated":"2018-10-30","state":"Fixed","cvss":{"cvss2":{"vector":{"attack_vector":"local","access_complexity":"low","authentication":"none","confidentiality_impact":"low","integrity_impact":"none","availability":"none"},"base_score":2.1},"cvss3":{"vector":{"attack_vector":"local","access_complexity":"high","confidentiality_impact":"high","integrity_impact":"none","availability":"none","privileges_required":"low","user_interaction":"none","scope":"unchanged"},"base_score":4.7}},"package":{"name":"Windows Server 2008 R2","generated_cpe":"o:microsoft:windows_server_2008:r2:sp1::::::"},"condition":"4019263 patch is not installed.","cwe_reference":"CWE-200","reference":"http://www.securityfocus.com/bid/98110"}}
vulnerability.cve: CVE-2017-0175
vulnerability.title: The Windows kernel in Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows authenticated attackers to obtain sensitive information via a specially crafted document, aka "Windows Kernel Information Disclosure Vulnerability," a different vulnerability than CVE-2017-0220, CVE-2017-0258, and CVE-2017-0259.
vulnerability.severity: Medium
vulnerability.published: 2017-05-12
vulnerability.updated: 2018-10-30
vulnerability.state: Fixed
vulnerability.cvss.cvss2.vector.attack_vector: local
vulnerability.cvss.cvss2.vector.access_complexity: low
vulnerability.cvss.cvss2.vector.authentication: none
vulnerability.cvss.cvss2.vector.confidentiality_impact: low
vulnerability.cvss.cvss2.vector.integrity_impact: none
vulnerability.cvss.cvss2.vector.availability: none
vulnerability.cvss.cvss2.base_score: 2.100000
vulnerability.cvss.cvss3.vector.attack_vector: local
vulnerability.cvss.cvss3.vector.access_complexity: high
vulnerability.cvss.cvss3.vector.confidentiality_impact: high
vulnerability.cvss.cvss3.vector.integrity_impact: none
vulnerability.cvss.cvss3.vector.availability: none
vulnerability.cvss.cvss3.vector.privileges_required: low
vulnerability.cvss.cvss3.vector.user_interaction: none
vulnerability.cvss.cvss3.vector.scope: unchanged
vulnerability.cvss.cvss3.base_score: 4.700000
vulnerability.package.name: Windows Server 2008 R2
vulnerability.package.generated_cpe: o:microsoft:windows_server_2008:r2:sp1::::::
vulnerability.package.condition: 4019263 patch is not installed.
vulnerability.cwe_reference: CWE-200
vulnerability.reference: http://www.securityfocus.com/bid/98110
Here we can see an alert in Kibana:
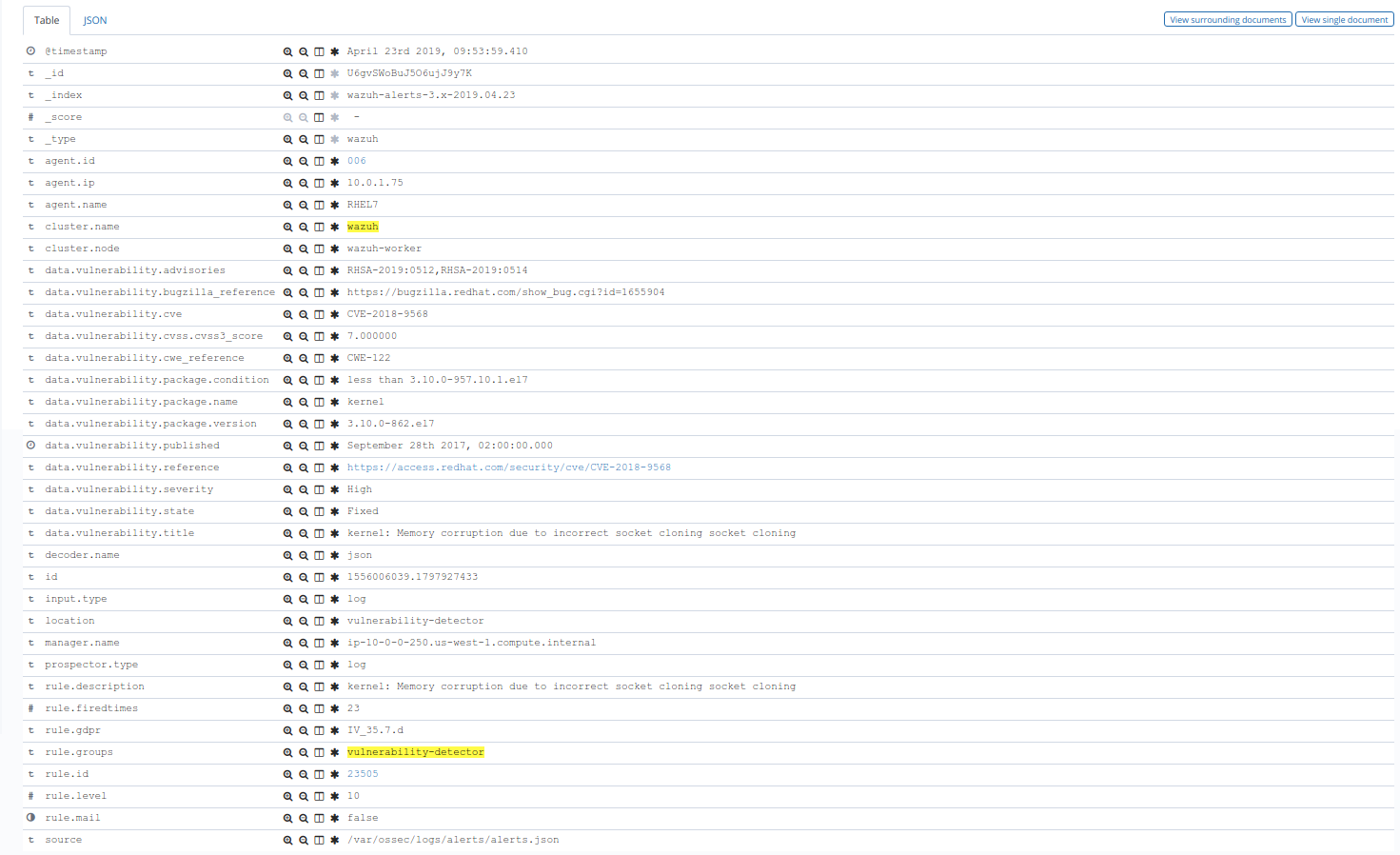
One more example, this time in Splunk: