Jumpcloud
Jumpcloud, is a Unified Device and Identity Access Management platform that provides services such as Multi-Factor Authentication (MFA), Single Sign-On, password management, and cloud directory. In this guide, we integrate the Jumpcloud SSO to authenticate users into the Wazuh platform.
There are three stages in the single sign-on integration.
Jumpcloud Configuration
Create an account in Jumpcloud. Request a free trial if you don't have a paid license.
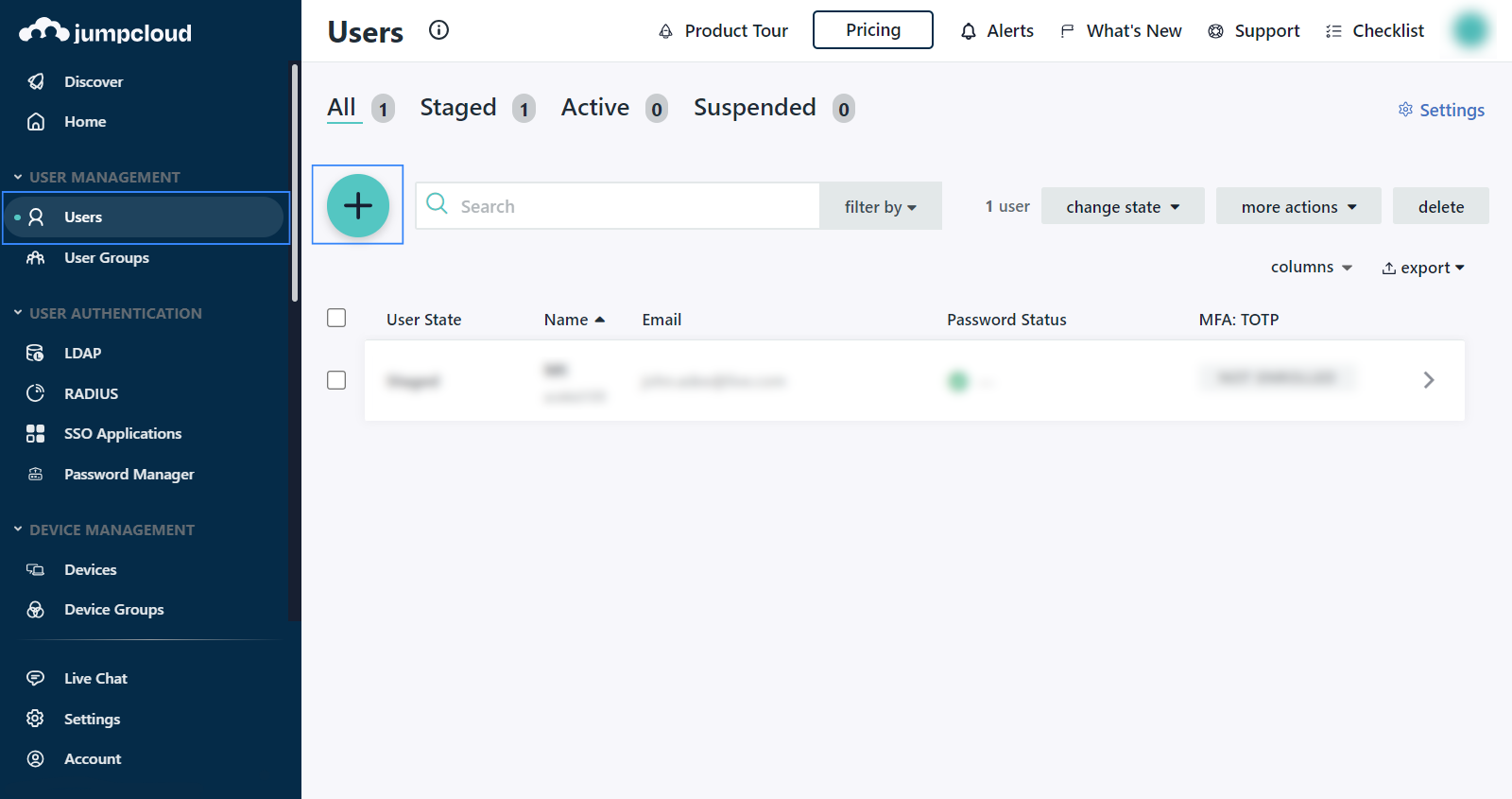
Create a new user. This step can be skipped if you are just testing, you can use your Jumpcloud
adminuser for example.Go to User Management, click on Users > (+) > Manual user entry. Fill in the user information, activate the user and click on save user.
Create a new group and assign the user.
Go to User Management > User Groups > (+) and give a name to the group. In our case, this is
Wazuh admins.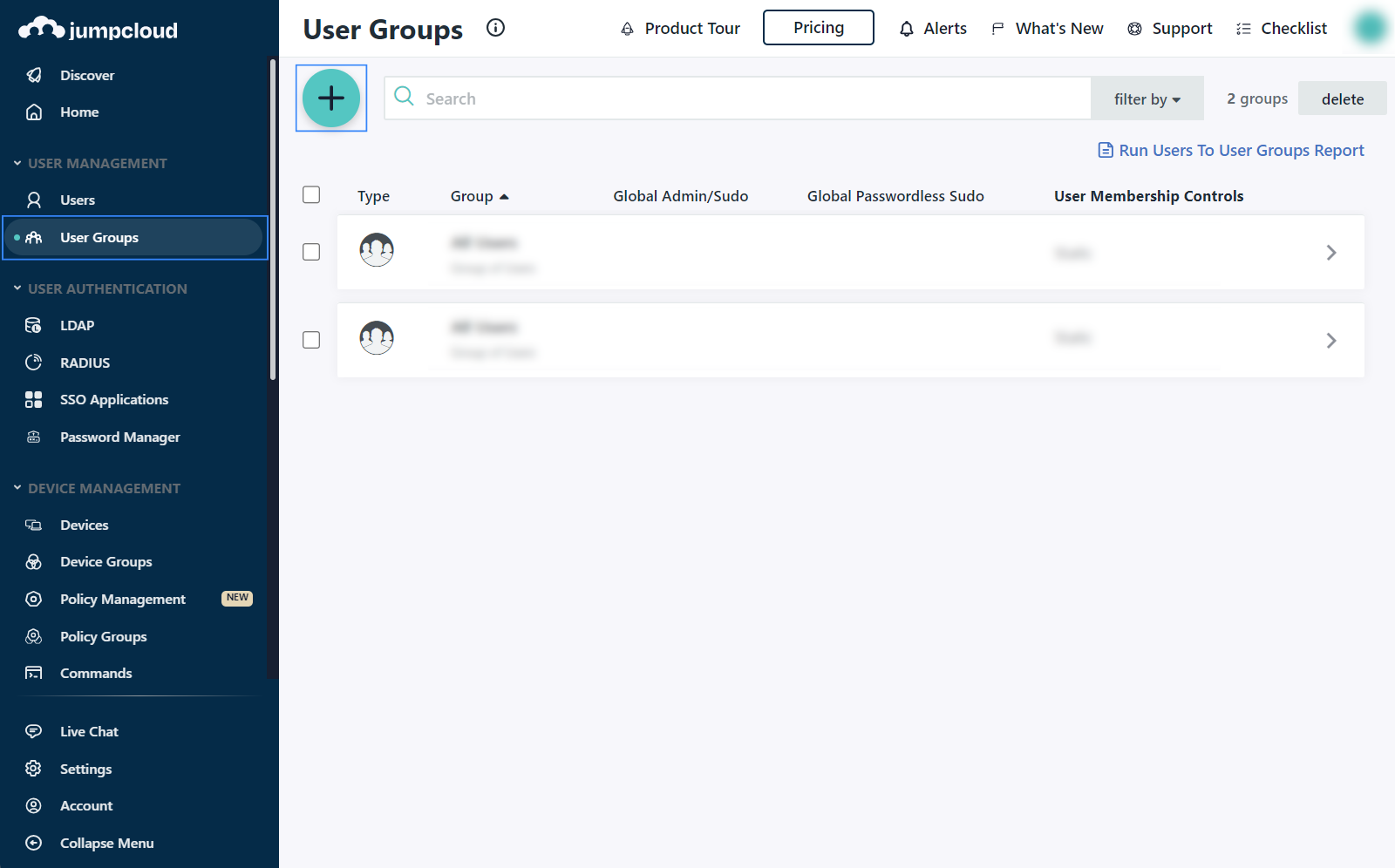
The name you give to your group will be used in the configuration. It will be our
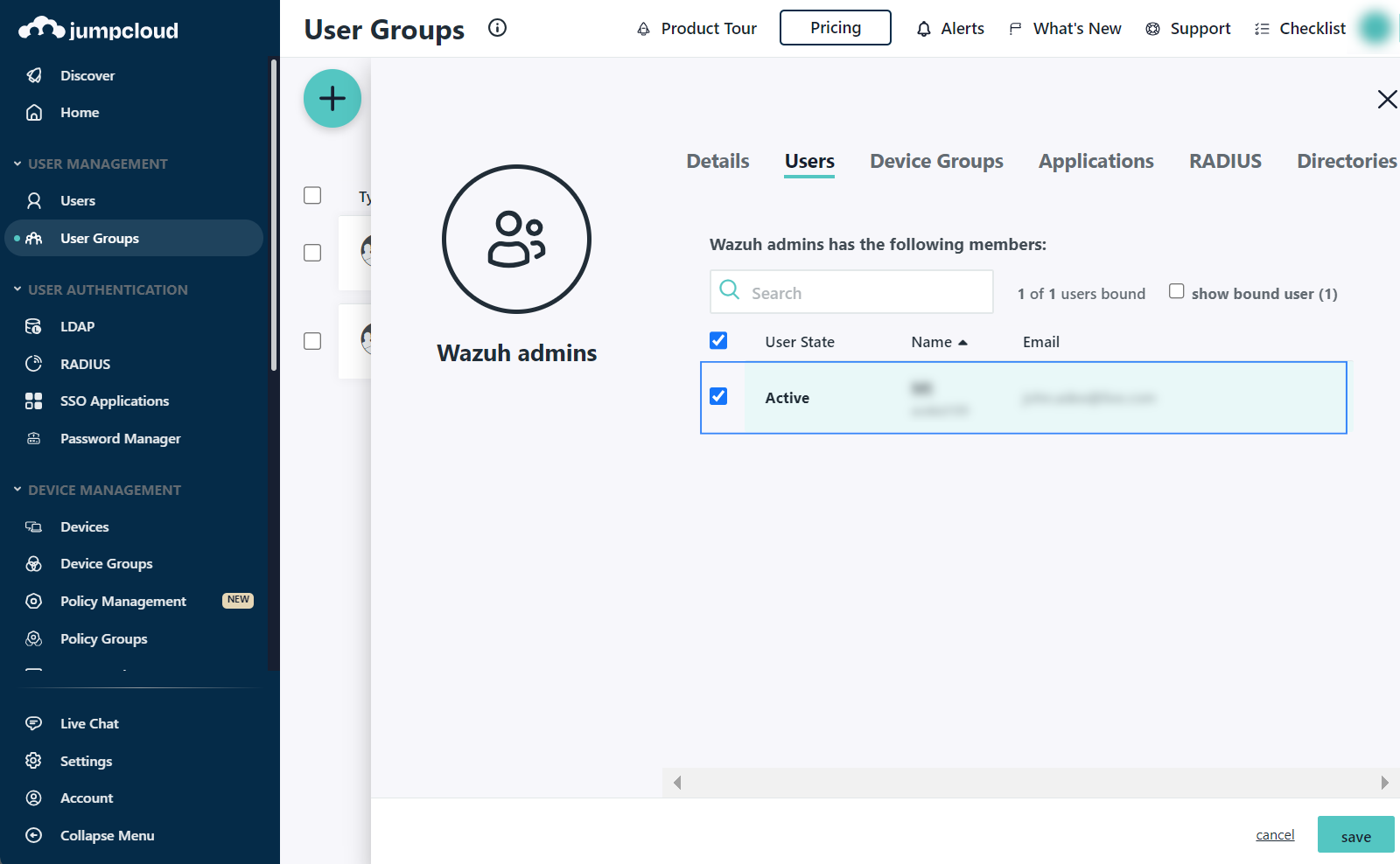
backend_rolesinroles_mapping.yml.In the selected User Groups, go to the Users tab, select the newly created user and Save the changes.
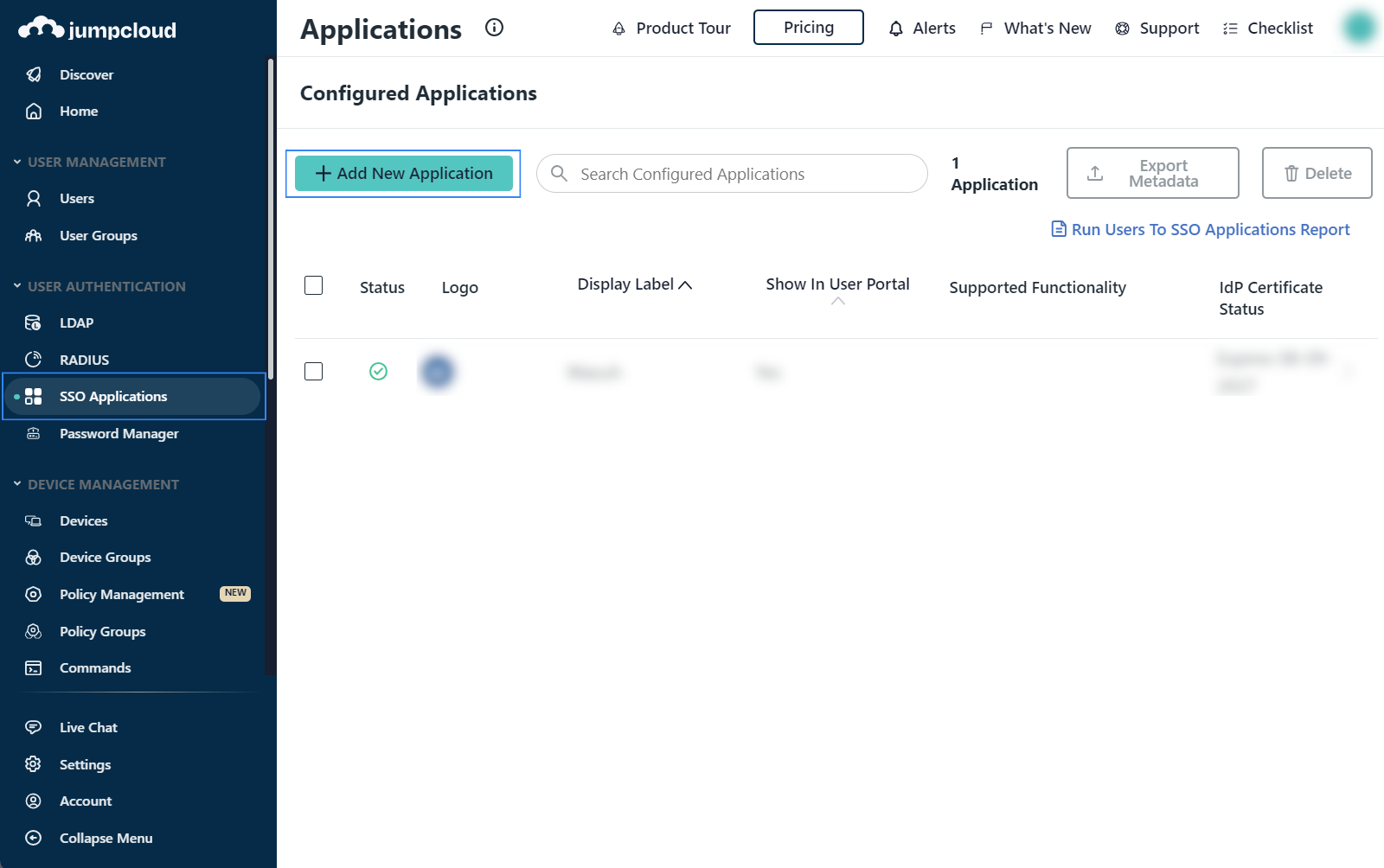
Create a new app. Configure the SAML settings while you create the app.
Under the User Authentication section, go to SSO Applications, select + Add New Application, and select Custom Application.
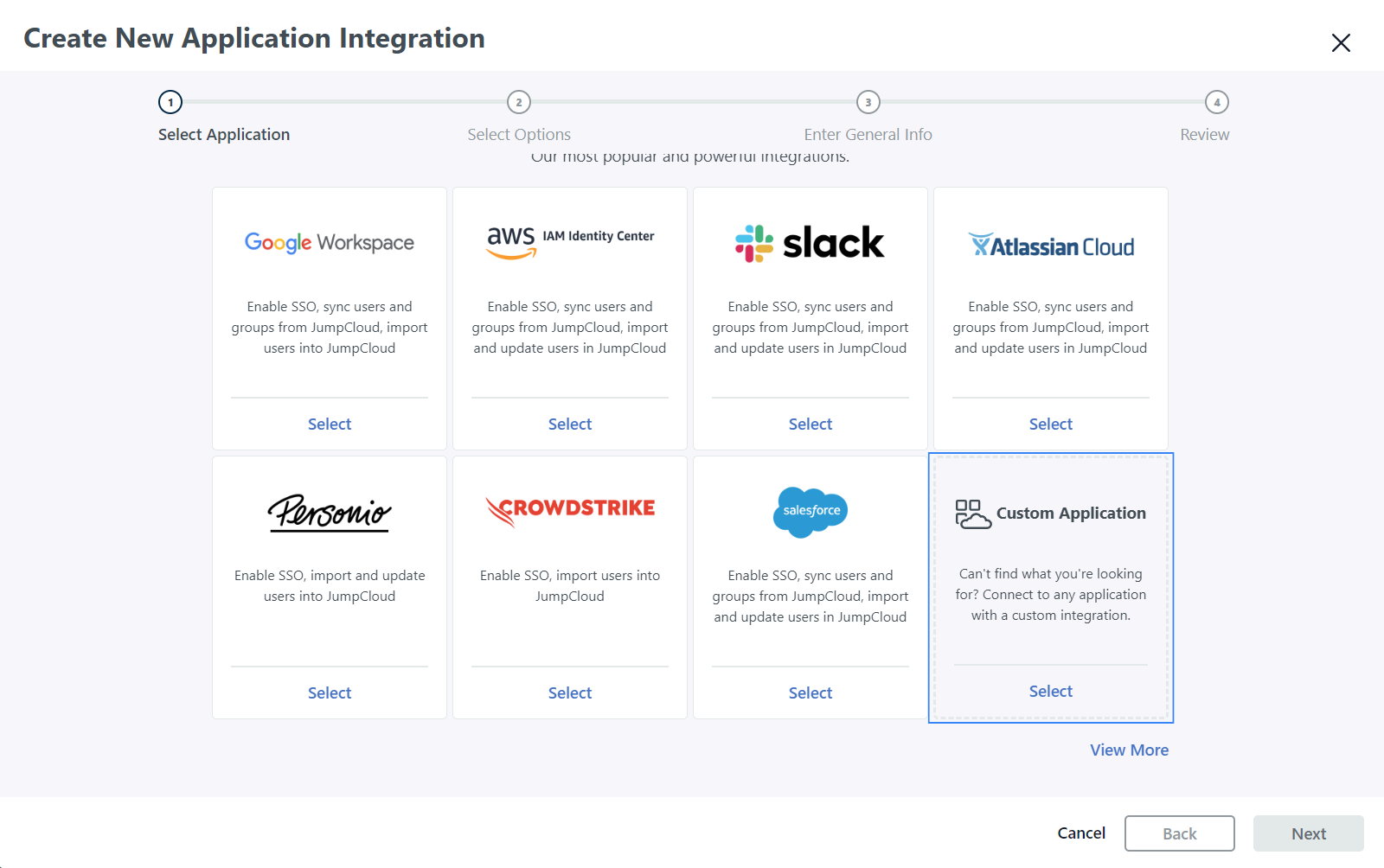
Complete the Create New Application Integration page with the appropriate information.
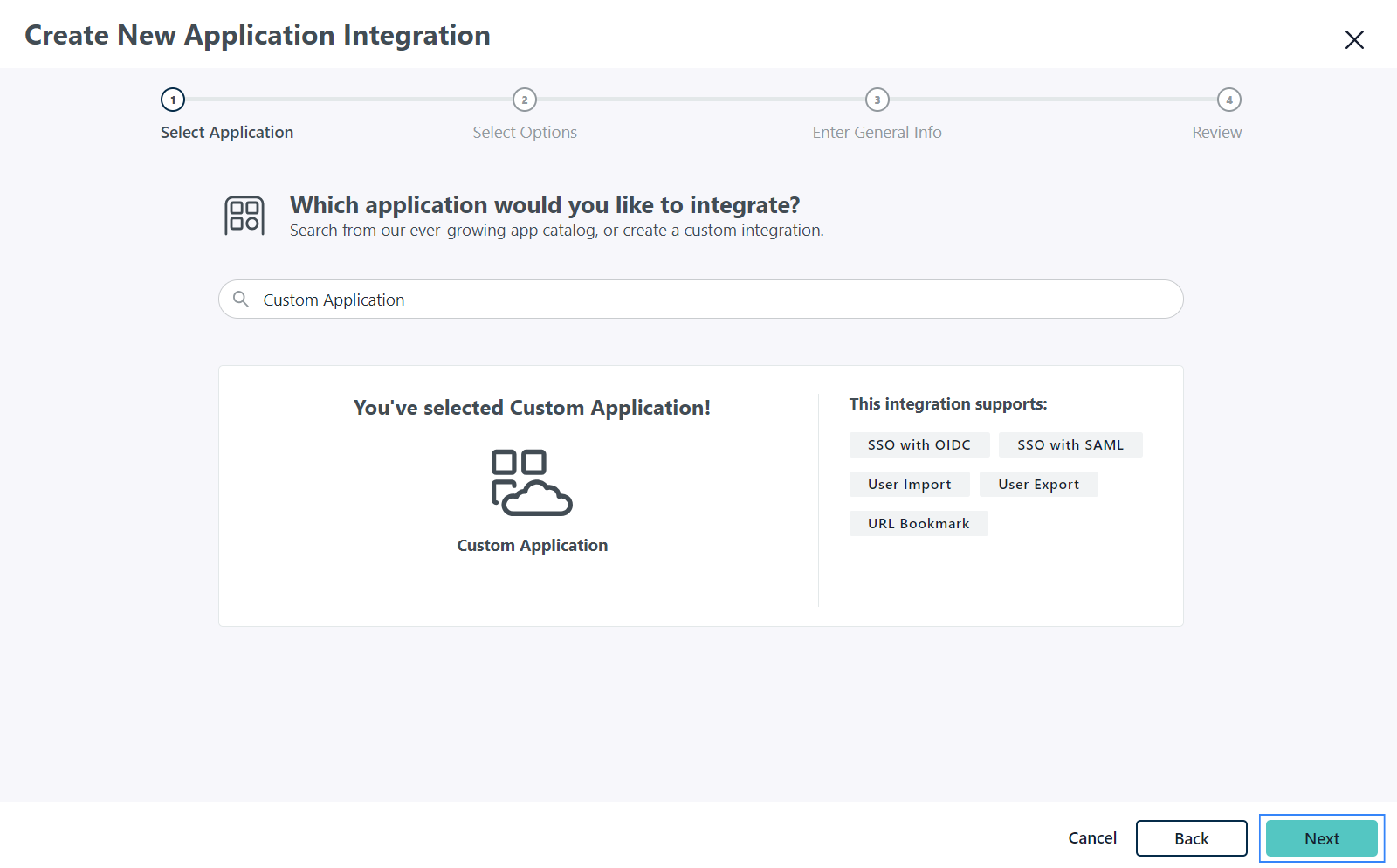
Click Next on the Select Application page.
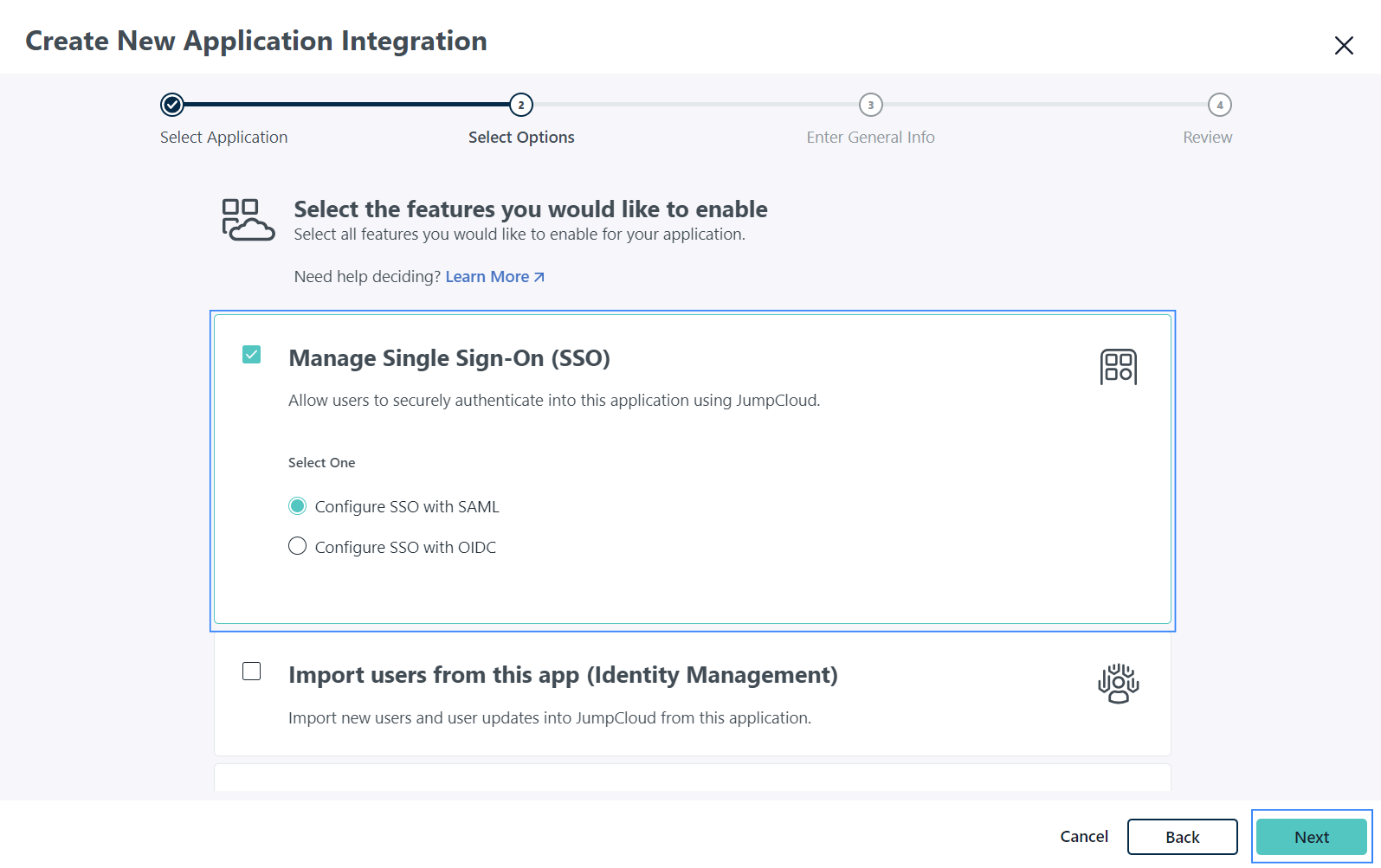
Check the Manage Single Sign-On (SSO) and Configure SSO with SAML options on the Select Options page. Click Next to proceed to the next step.
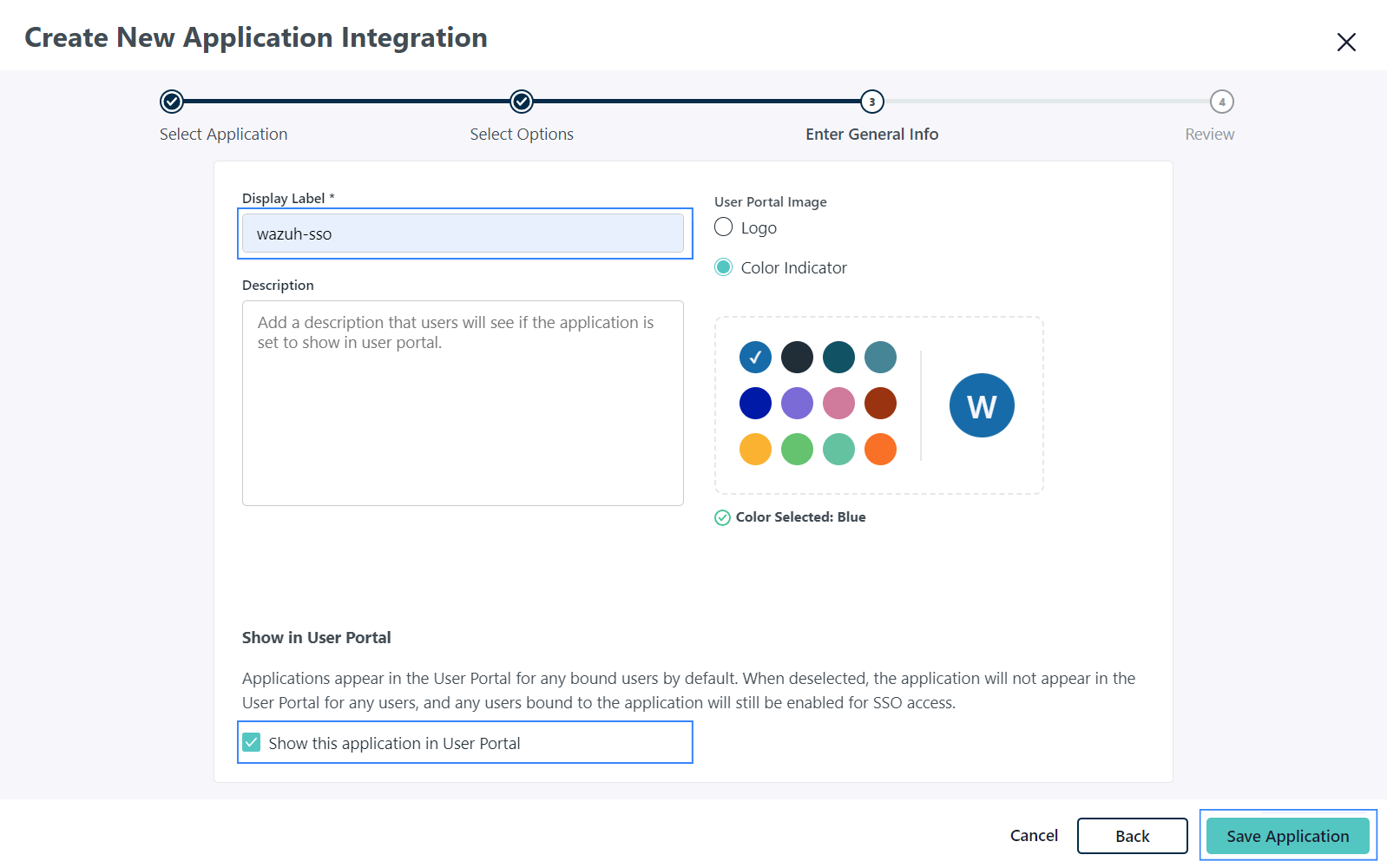
Assign a Display Label to the application, and click the Show this application in User Portal checkbox on the Enter General Info page. Click Save Application to apply the settings.
Click Configure Application on the Review page.
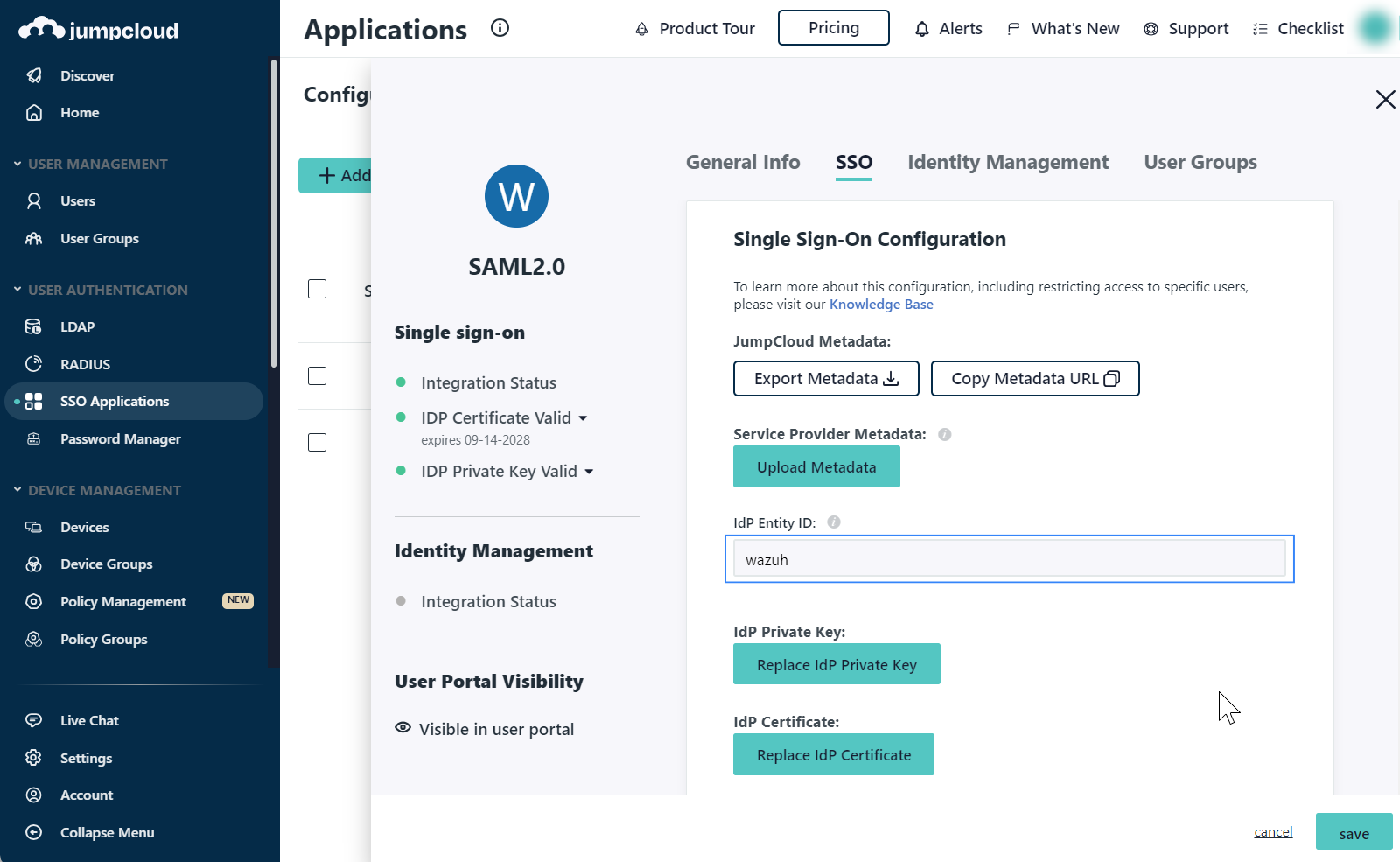
Complete the SSO tab with the appropriate information.
IdP Entity ID:
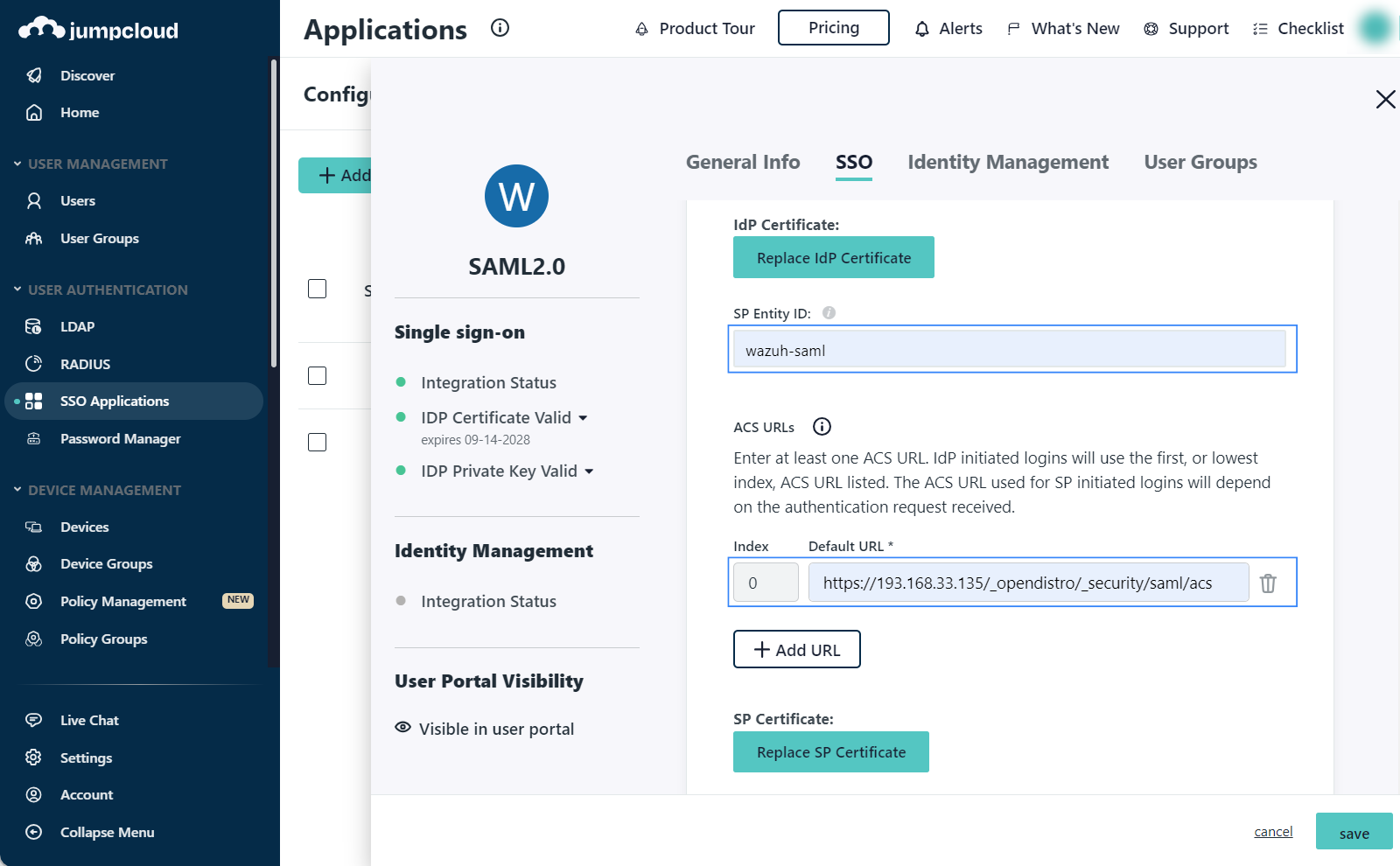
wazuh(this will be theidp.entity_idin our Wazuh indexer configuration).SP Entity ID:
wazuh-saml(this will be thesp.entity_idin our Wazuh indexer configuration).ACS URL:
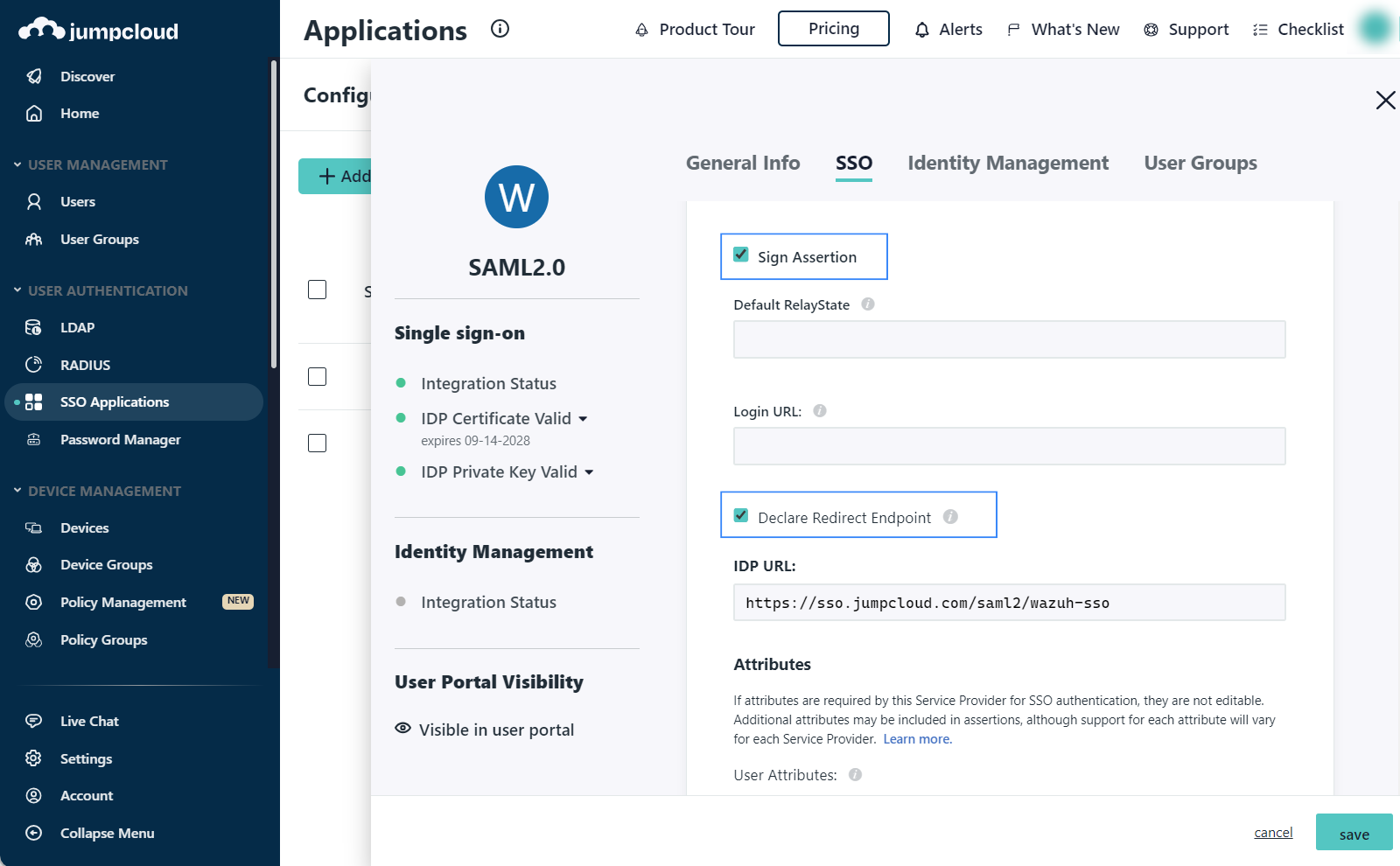
https://<WAZUH_DASHBOARD_URL>/_opendistro/_security/saml/acsCheck Sign Assertion.
Check Declare Redirect Endpoint.
Check include group attribute and add Roles as the attribute. This will be used later in the
config.ymlconfiguration file.
The rest of the options can be left as their default values.
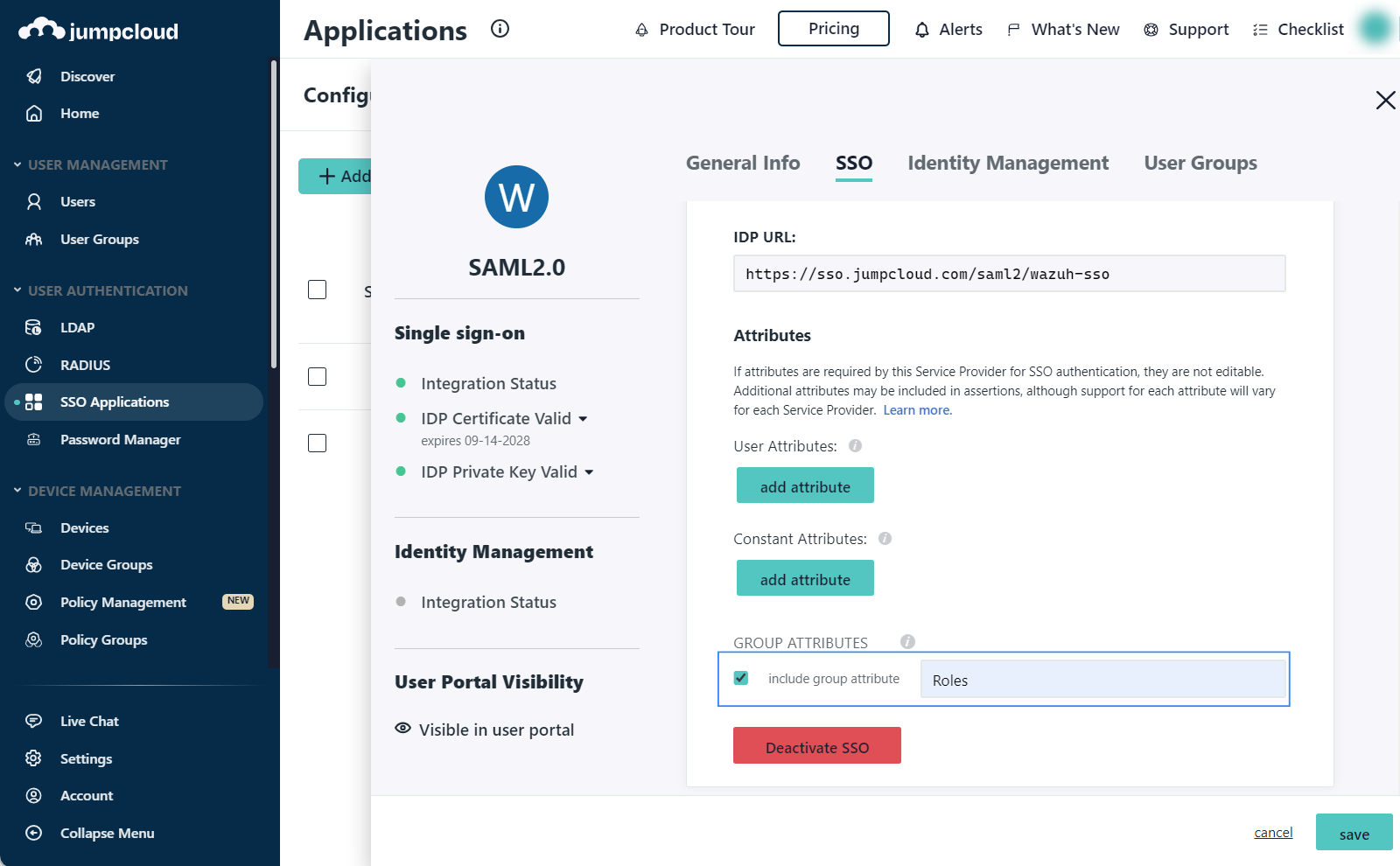
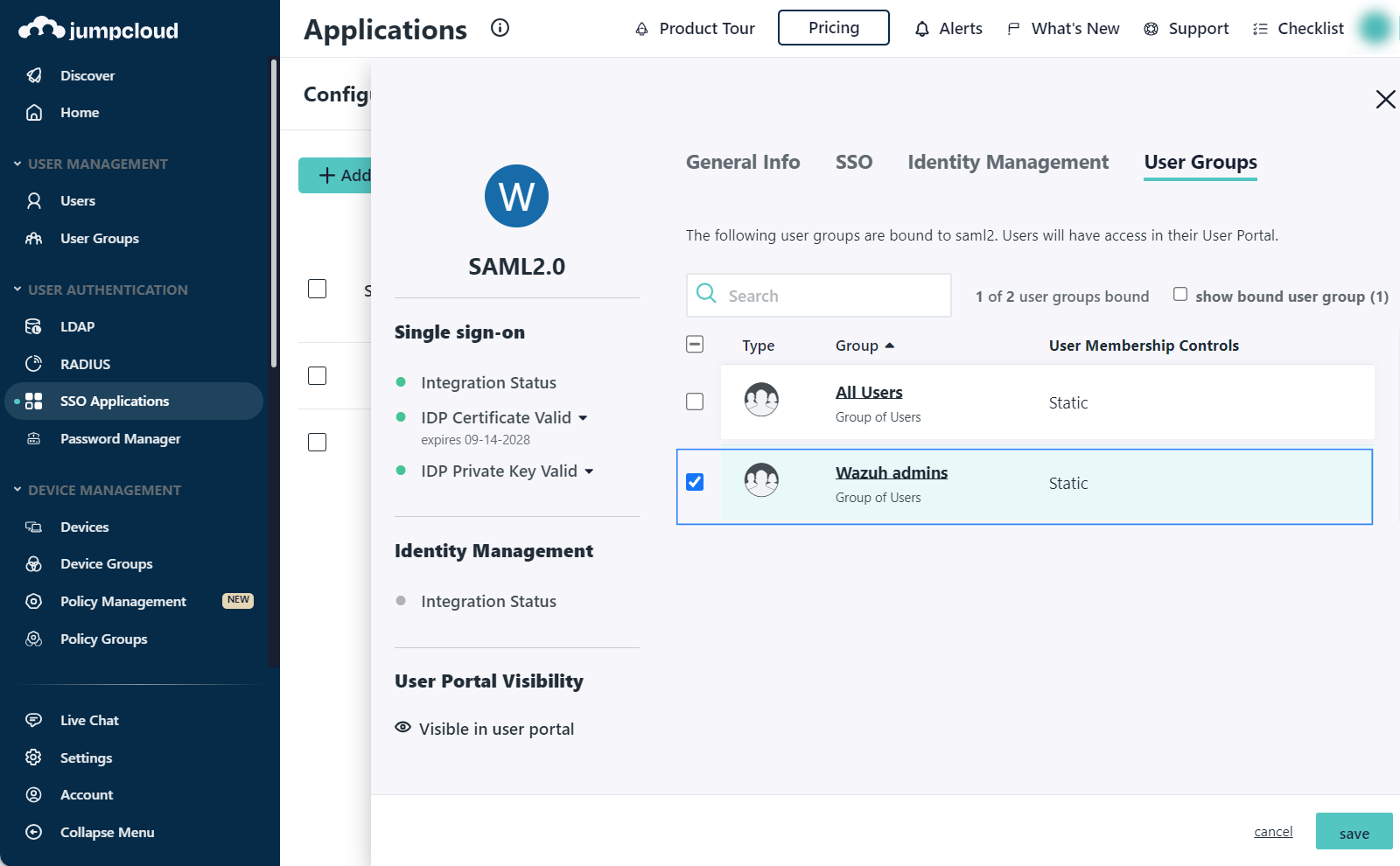
On the User Groups tab, select the Group created previously and click save.
Note the necessary parameters from the SAML settings of the new app.
Open the recently created application and go to the SSO tab, select Export Metadata. This will be our
metadata_file. Place the metadata file in the configuration directory of the Wazuh indexer. The path to the directory is/etc/wazuh-indexer/opensearch-security/.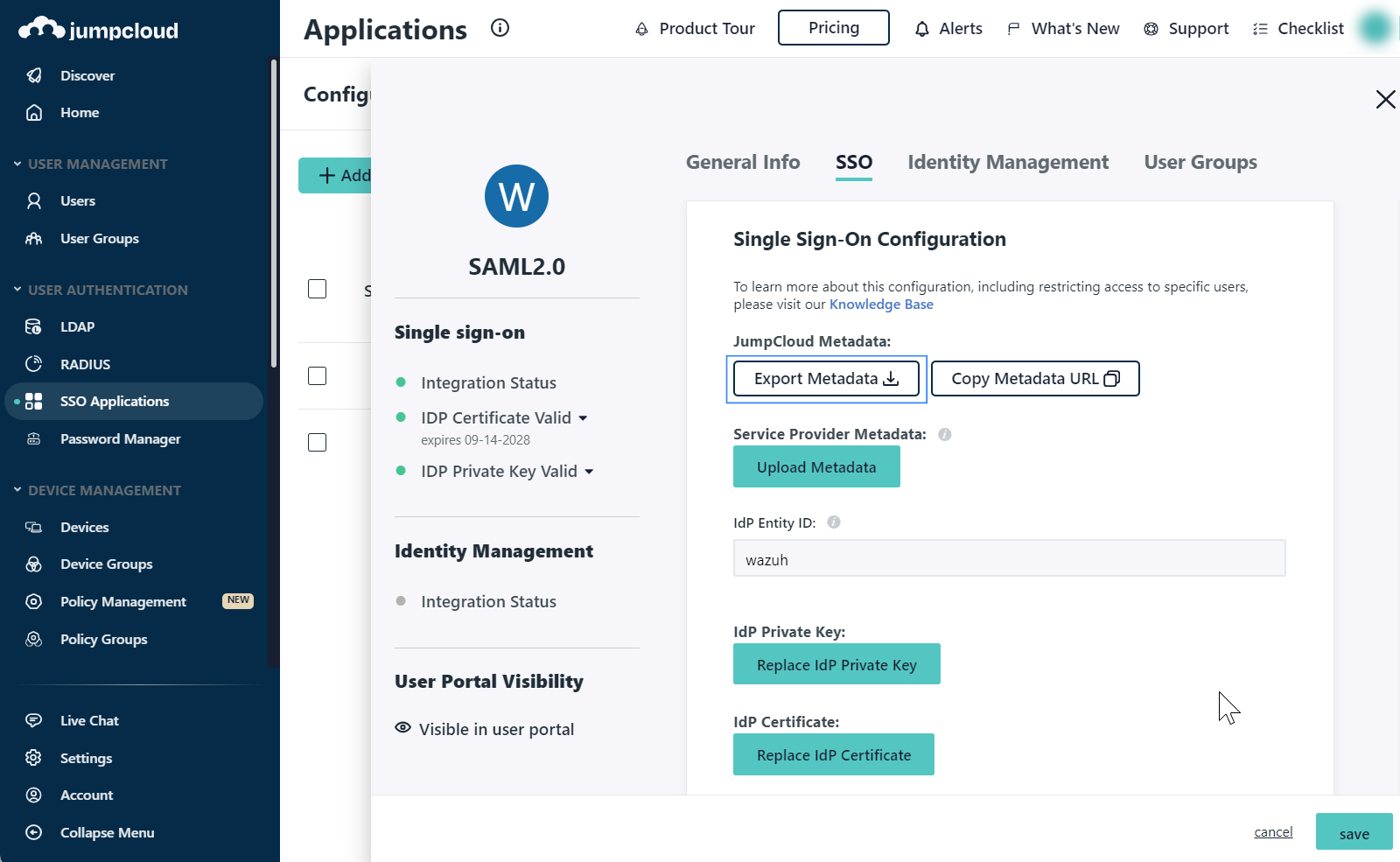
Wazuh indexer configuration
Edit the Wazuh indexer security configuration files. We recommend that you back up these files before you carry out the configuration.
Generate a 64-character long random key using the following command.
openssl rand -hex 32The output will be used as the
exchange_keyin the/etc/wazuh-indexer/opensearch-security/config.ymlfile.Place the
metadata_jumpcloud.xmlfile within the/etc/wazuh-indexer/opensearch-security/directory. Set the file ownership towazuh-indexerusing the following command:# chown wazuh-indexer:wazuh-indexer /etc/wazuh-indexer/opensearch-security/metadata_jumpcloud.xml
Edit the
/etc/wazuh-indexer/opensearch-security/config.ymlfile and change the following values:Set the
orderinbasic_internal_auth_domainto0and thechallengeflag tofalse.Include a
saml_auth_domainconfiguration under theauthcsection similar to the following:
authc: ... basic_internal_auth_domain: description: "Authenticate via HTTP Basic against internal users database" http_enabled: true transport_enabled: true order: 0 http_authenticator: type: "basic" challenge: false authentication_backend: type: "intern" saml_auth_domain: http_enabled: true transport_enabled: true order: 1 http_authenticator: type: saml challenge: true config: idp: metadata_file: '/etc/wazuh-indexer/opensearch-security/metadata_jumpcloud.xml' entity_id: wazuh sp: entity_id: wazuh-saml forceAuthn: true kibana_url: https://<WAZUH_DASHBOARD_URL> roles_key: Roles exchange_key: 'b1d6dd32753374557dcf92e241.......' authentication_backend: type: noop
Ensure to change the following parameters to their corresponding value:
idp.metadata_fileidp.entity_idsp.entity_idkibana_urlroles_keyexchange_key
Run the
securityadminscript to load the configuration changes made in theconfig.ymlfile.# export JAVA_HOME=/usr/share/wazuh-indexer/jdk/ && bash /usr/share/wazuh-indexer/plugins/opensearch-security/tools/securityadmin.sh -f /etc/wazuh-indexer/opensearch-security/config.yml -icl -key /etc/wazuh-indexer/certs/admin-key.pem -cert /etc/wazuh-indexer/certs/admin.pem -cacert /etc/wazuh-indexer/certs/root-ca.pem -h 127.0.0.1 -nhnv
The
-hflag specifies the hostname or the IP address of the Wazuh indexer node. Note that this command uses 127.0.0.1, set your Wazuh indexer address if necessary.The command output must be similar to the following:
Security Admin v7 Will connect to 127.0.0.1:9200 ... done Connected as "CN=admin,OU=Wazuh,O=Wazuh,L=California,C=US" OpenSearch Version: 2.10.0 Contacting opensearch cluster 'opensearch' and wait for YELLOW clusterstate ... Clustername: wazuh-cluster Clusterstate: GREEN Number of nodes: 1 Number of data nodes: 1 .opendistro_security index already exists, so we do not need to create one. Populate config from /etc/wazuh-indexer/opensearch-security Will update '/config' with /etc/wazuh-indexer/opensearch-security/config.yml SUCC: Configuration for 'config' created or updated SUCC: Expected 1 config types for node {"updated_config_types":["config"],"updated_config_size":1,"message":null} is 1 (["config"]) due to: null Done with success
Edit the
/etc/wazuh-indexer/opensearch-security/roles_mapping.ymlfile and change the following values:Configure the
roles_mapping.ymlfile to map the Jumpcloud user group to the appropriate Wazuh indexer role. In our case, we map theWazuh adminsgroup to theall_accessrole:all_access: reserved: false hidden: false backend_roles: - "admin" - "Wazuh admins" description: "Maps admin to all_access"
Run the
securityadminscript to load the configuration changes made in theroles_mapping.ymlfile.# export JAVA_HOME=/usr/share/wazuh-indexer/jdk/ && bash /usr/share/wazuh-indexer/plugins/opensearch-security/tools/securityadmin.sh -f /etc/wazuh-indexer/opensearch-security/roles_mapping.yml -icl -key /etc/wazuh-indexer/certs/admin-key.pem -cert /etc/wazuh-indexer/certs/admin.pem -cacert /etc/wazuh-indexer/certs/root-ca.pem -h 127.0.0.1 -nhnv
The
-hflag specifies the hostname or the IP address of the Wazuh indexer node. Note that this command uses 127.0.0.1, set your Wazuh indexer address if necessary.The command output must be similar to the following:
Security Admin v7 Will connect to 127.0.0.1:9200 ... done Connected as "CN=admin,OU=Wazuh,O=Wazuh,L=California,C=US" OpenSearch Version: 2.10.0 Contacting opensearch cluster 'opensearch' and wait for YELLOW clusterstate ... Clustername: wazuh-cluster Clusterstate: GREEN Number of nodes: 1 Number of data nodes: 1 .opendistro_security index already exists, so we do not need to create one. Populate config from /etc/wazuh-indexer/opensearch-security Will update '/rolesmapping' with /etc/wazuh-indexer/opensearch-security/roles_mapping.yml SUCC: Configuration for 'rolesmapping' created or updated SUCC: Expected 1 config types for node {"updated_config_types":["rolesmapping"],"updated_config_size":1,"message":null} is 1 (["rolesmapping"]) due to: null Done with success
Wazuh dashboard configuration
Check the value of
run_asin the/usr/share/wazuh-dashboard/data/wazuh/config/wazuh.ymlconfiguration file. Ifrun_asis set tofalse, proceed to the next step.hosts: - default: url: https://127.0.0.1 port: 55000 username: wazuh-wui password: "<WAZUH_WUI_PASSWORD>" run_as: false
If
run_asis set totrue, you need to add a role mapping on the Wazuh dashboard. To map the backend role to Wazuh, follow these steps:Click ☰ to open the menu on the Wazuh dashboard, go to Server management > Security, and then Roles mapping to open the page.
Click Create Role mapping and complete the empty fields with the following parameters:
Role mapping name: Assign a name to the role mapping.
Roles: Select
administrator.Custom rules: Click Add new rule to expand this field.
User field:
backend_rolesSearch operation:
FINDValue: Assign the name of the Jumpcloud user group. In our case, this is
Wazuh admins.
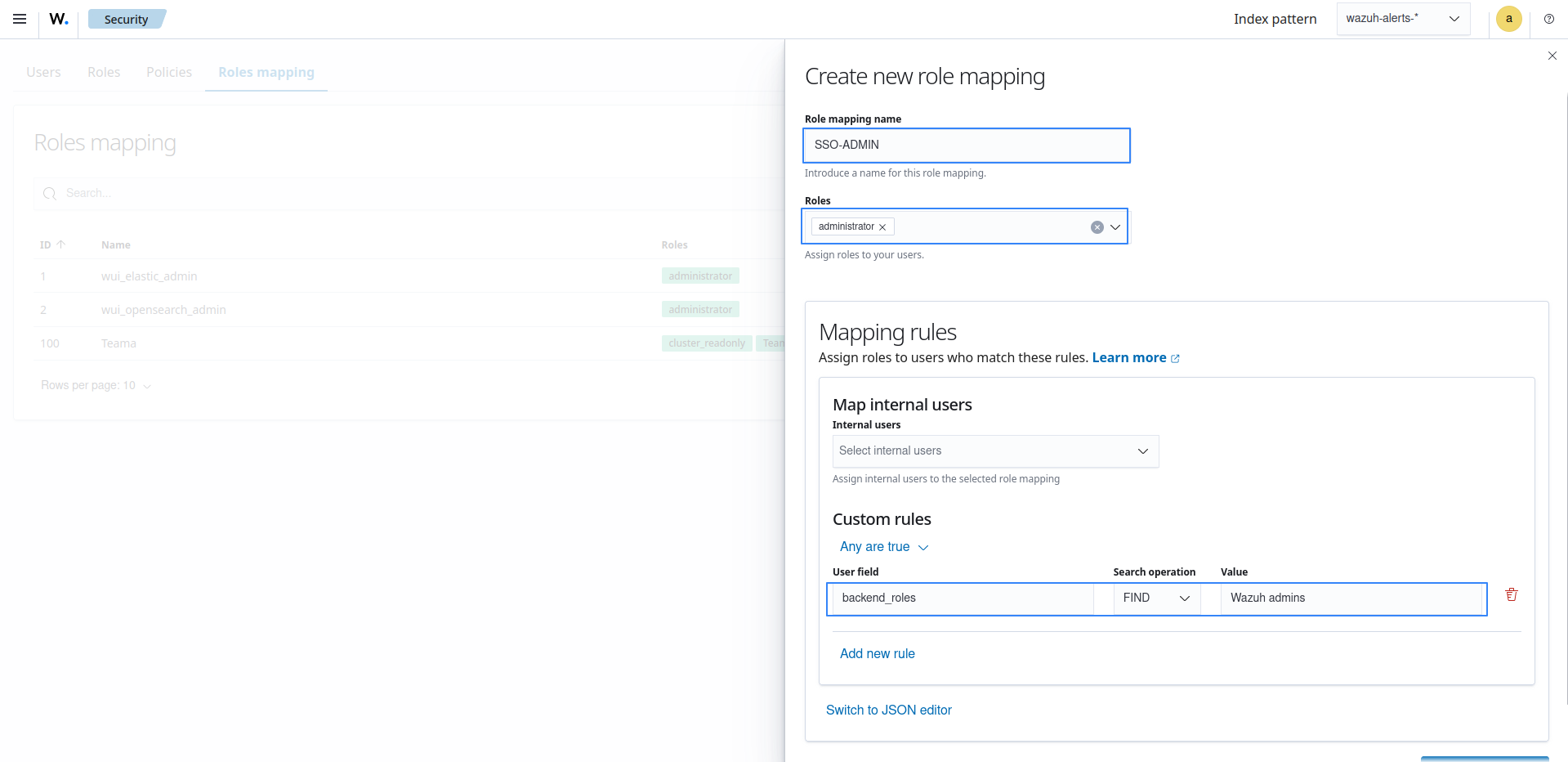
Click Save role mapping to save and map the backend role with Wazuh as administrator.
Edit the Wazuh dashboard configuration file. Add these configurations to
/etc/wazuh-dashboard/opensearch_dashboards.yml. We recommend that you back up these files before you carry out the configuration.opensearch_security.auth.type: "saml" server.xsrf.allowlist: ["/_opendistro/_security/saml/acs", "/_opendistro/_security/saml/logout", "/_opendistro/_security/saml/acs/idpinitiated"] opensearch_security.session.keepalive: false
Restart the Wazuh dashboard service.
# systemctl restart wazuh-dashboard
# service wazuh-dashboard restart
Test the configuration. Go to your Wazuh dashboard URL and log in with your Jumpcloud account.