Installation
Prior to enabling the Wazuh rules for Amazon Web Services, follow the steps below to configure AWS to generate log messages, and store them as JSON data files in an Amazon S3 bucket. A detailed description of each of the steps can be found below.
Note
The integration with AWS Cloudtrail can be done at the Wazuh manager (which also behaves as an agent) or directly at a Wazuh agent. This choice merely depends on how you decide to access your AWS infrastructure in your environment.
Requirements
AWS CloudTrail
Wazuh >= 3.2
Python >= 2.7
Pip
Boto3
Subscribe to CloudTrail
From your AWS console, choose “CloudTrail” from the Deployment & Management section:
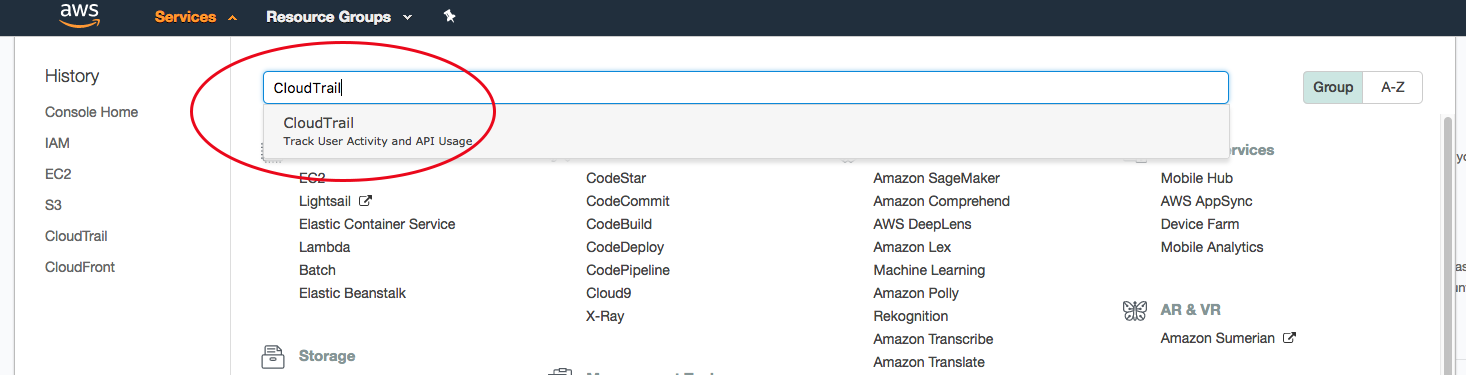
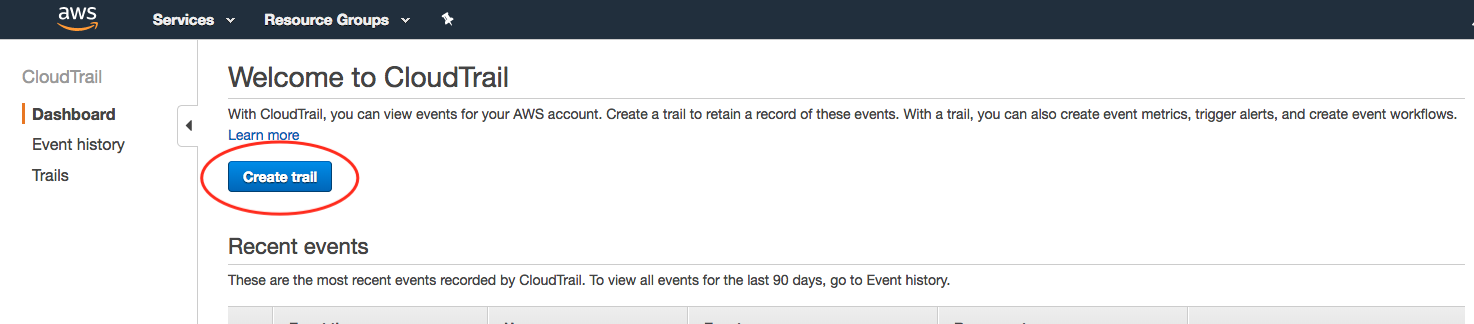
Create a new trail:
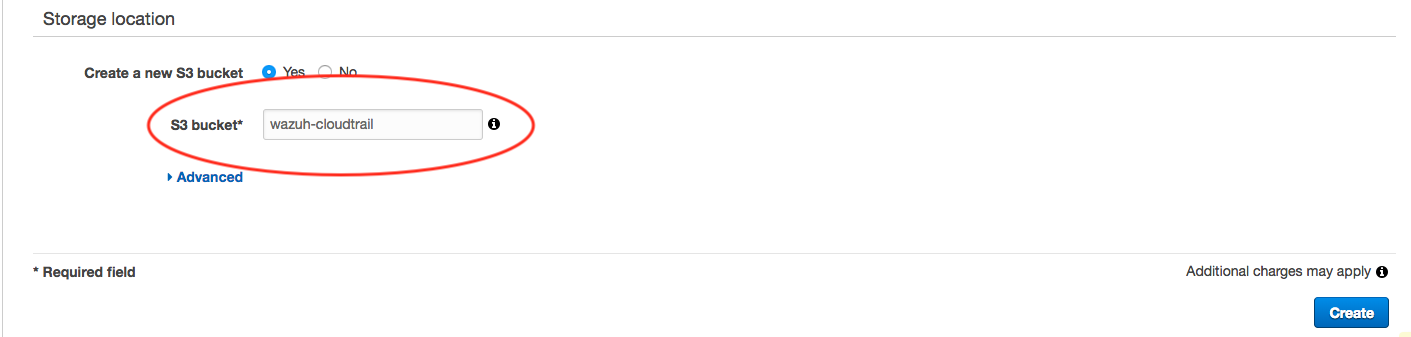
Provide a name for the new S3 bucket that will be used to store the CloudTrail logs (reemember the name you provide here, you’ll need to reference it during plugin setup):
Create an IAM User
Wazuh will need a user with permissions to pull the CloudTrail log data from your S3 bucket. The easiest way to accomplish this is by creating a new IAM user for your account. We will only allow it to read data from the S3 bucket.
Create new user:
Navigate to Services > IAM > Users
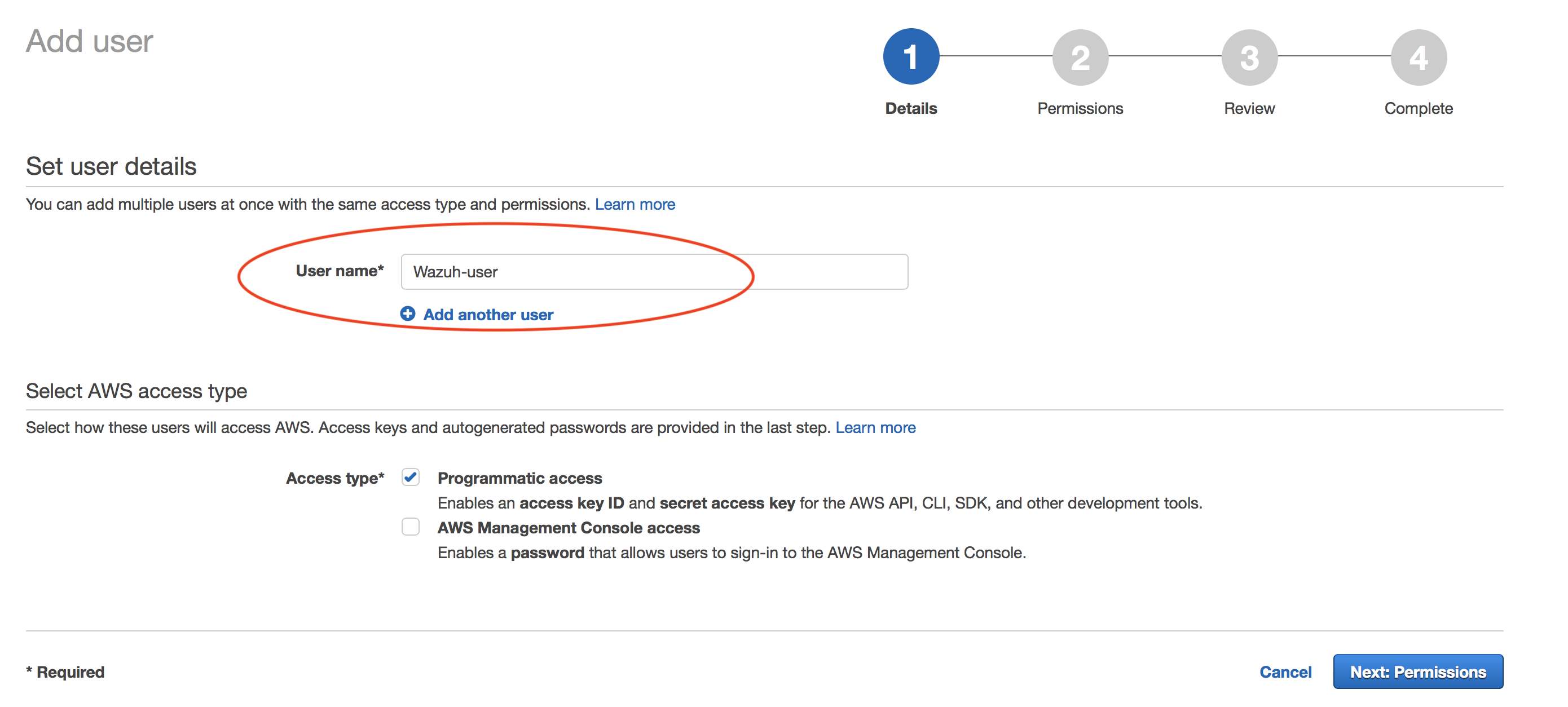
Click on "Next: Permissions" to continue.
Create policy:
We will attach this policy later to the user we are creating.
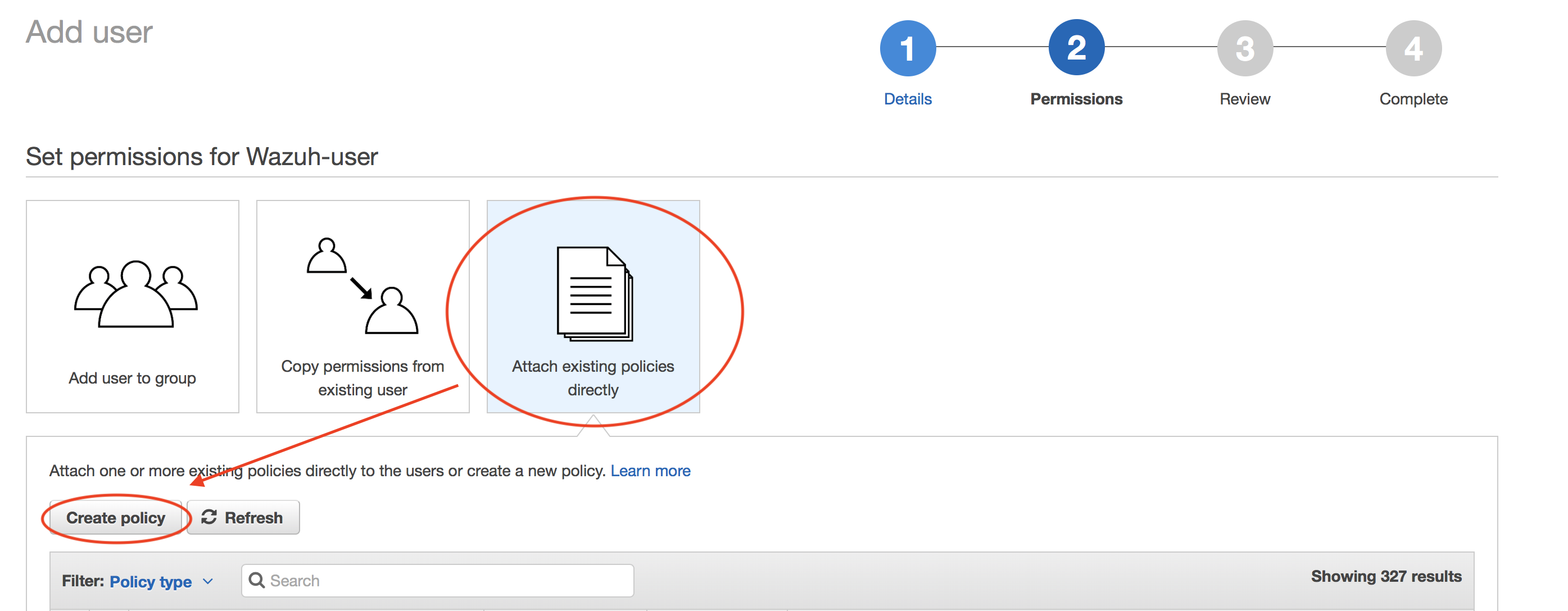
Check that your new policy looks like this:
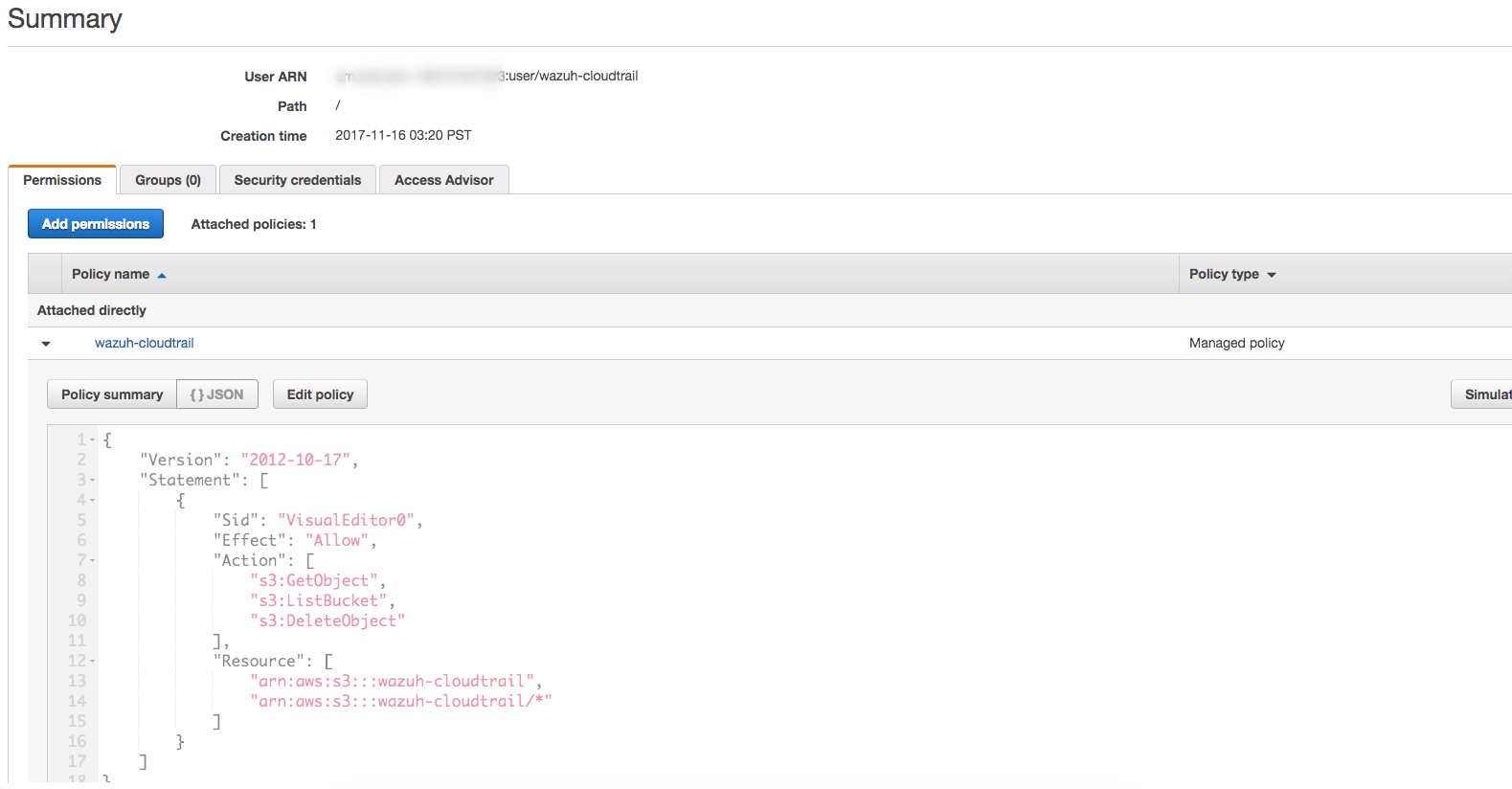
Raw output for the example policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::wazuh-cloudtrail",
"arn:aws:s3:::wazuh-cloudtrail/*"
]
}
]
}
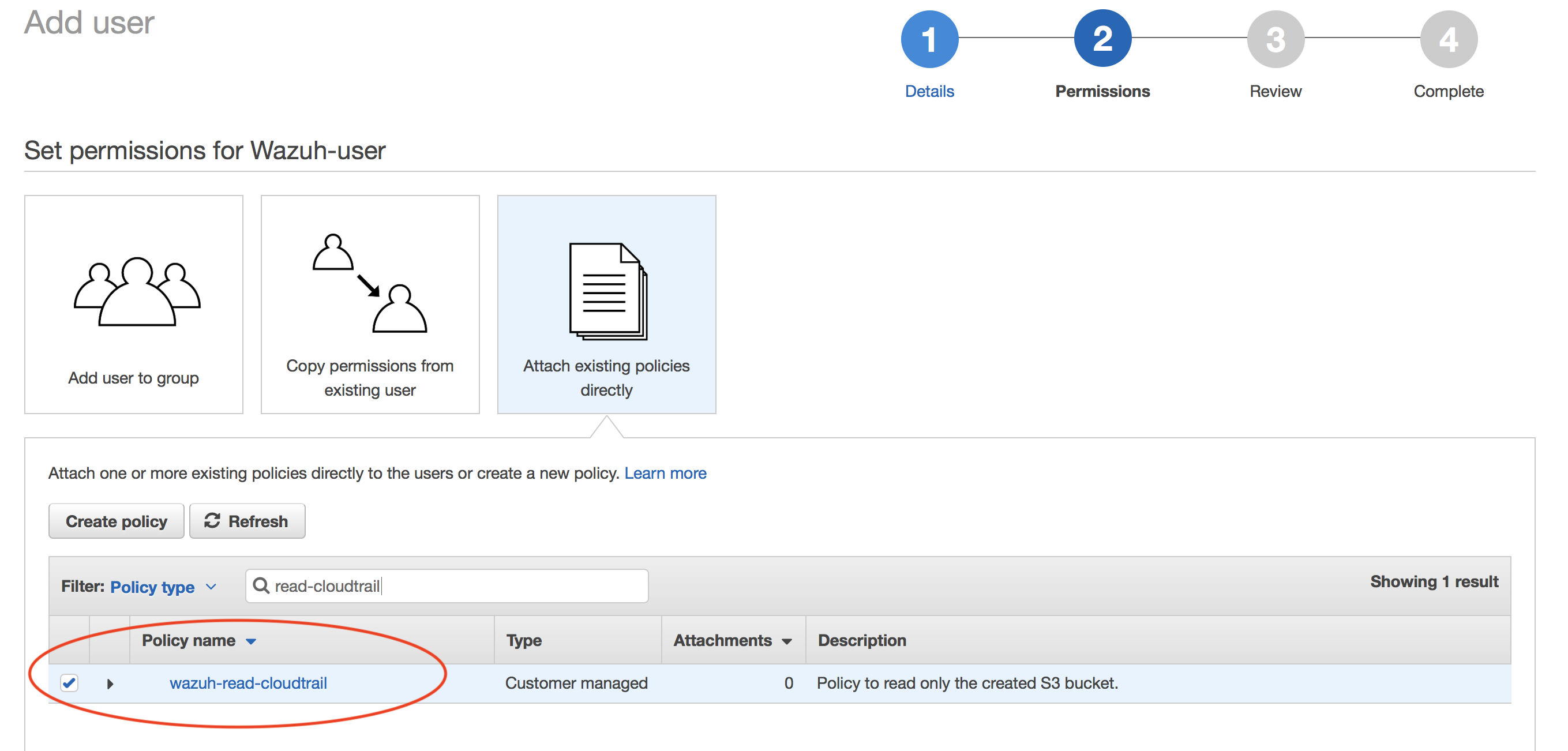
Attach policy:
Confirm user creation and get credentials:
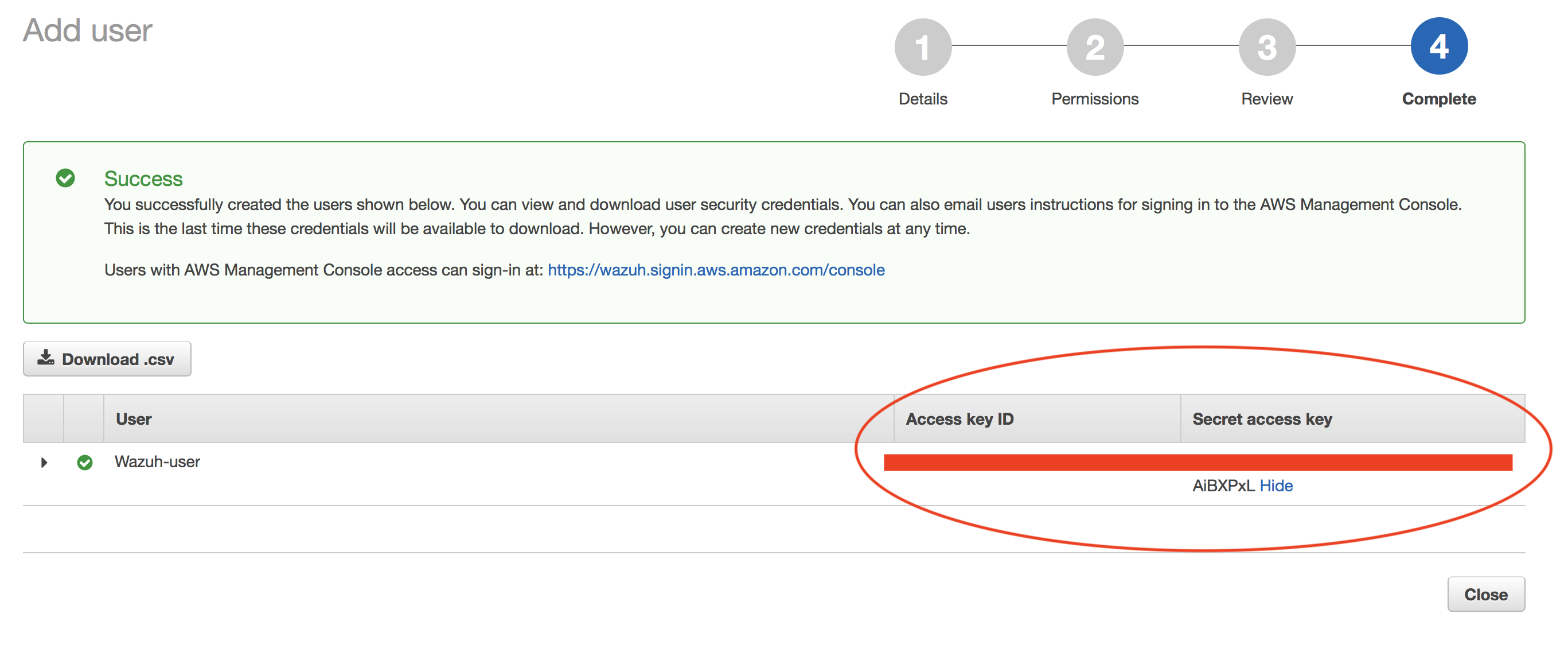
Save the credentials, you will use them later to configure the module.
Installing dependencies
Python Boto3 module is required on the system running the Wazuh module to pull AWS events. This will usually be one of your agents (or your manager).
Pip
Pip can be used as Python package manager to install the required module. In order to use it, we will start installing this tool.
CentOS/RHEL/Fedora:
# yum install python-pip
Debian/Ubuntu:
# apt-get update && apt-get install python-pip
From sources:
# curl -O https://bootstrap.pypa.io/get-pip.py
# python get-pip.py
Boto3
Boto3 is the official package supported by Amazon to manage AWS resources. It will be used to download the log messages from the S3 Bucket.
# pip install boto3
Plugin configuration
Open Wazuh configuration file:
# vi /var/ossec/etc/ossec.conf
Add the following block of configuration to enable the integration, enter the AWS IAM User credentials you created before:
<wodle name="aws-cloudtrail">
<disabled>no</disabled>
<bucket>wazuh-cloudtrail</bucket>
<access_key>insert_access_key</access_key>
<secret_key>insert_secret_key</secret_key>
<remove_from_bucket>no</remove_from_bucket>
<interval>10m</interval>
<run_on_start>no</run_on_start>
</wodle>
Check the user manual reference to read more details about each setting: AWS CloudTrail settings
Note
Credentials can be loaded from different locations, you can either specify the credentials as they are in the previous block of configuration or load them from other Boto3 supported locations.
Restart your Wazuh system to apply the changes:
# /var/ossec/bin/ossec-control restart
Testing the integration
After configuring the module successfully you can expect to see the following log messages in your agent log file: /var/ossec/logs/ossec.log
Module starting:
2018/01/12 18:47:09 wazuh-modulesd:aws-cloudtrail: INFO: Module AWS-CloudTrail started
Scheduled scan:
2018/01/12 18:49:10 wazuh-modulesd:aws-cloudtrail: INFO: Fetching logs started
2018/01/12 18:49:11 wazuh-modulesd:aws-cloudtrail: INFO: Fetching logs finished.
Troubleshooting
Wrong credentials:
AWS IAM credentials were not set properly or they don't have enough privileges.
2018/01/12 19:02:22 wazuh-modulesd:aws-cloudtrail: WARNING: Returned exit code 3.
2018/01/12 19:02:22 wazuh-modulesd:aws-cloudtrail: WARNING: Invalid credentials to access S3 Bucket
Missing Boto3 dependency:
Boto3 package is not installed in the system. Please, Boto3 installation section.
2018/01/12 19:03:17 wazuh-modulesd:aws-cloudtrail: WARNING: Returned exit code 4.
2018/01/12 19:03:17 wazuh-modulesd:aws-cloudtrail: WARNING: boto3 module is required.
Time interval is shorter than the time taken to pull log data:
In this case a simple warning will be displayed. There is no impact in the event data fetching process and the module will keep running.
2018/01/12 19:10:37 wazuh-modulesd:aws-cloudtrail: WARNING: Interval overtaken.