How it works
Since v3.12.0, Wazuh uses the new FIM module. To learn about the functionality of the FIM used in the previous Wazuh releases, please refer to the corresponding version of the documentation.

The FIM module is located in the Wazuh agent, where runs periodic scans of the system and stores the checksums and attributes of the monitored files and Windows registry keys in a local FIM database. The module looks for the modifications by comparing the new files’ checksums to the old checksums. All detected changes are reported to the Wazuh manager.
The new FIM synchronization mechanism ensures the file inventory in the Wazuh manager is always updated with respect to the Wazuh agent, allowing servicing FIM-related API queries regarding the Wazuh agents. The FIM synchronization is based on periodic calculations of integrity between the Wazuh agent’s and the Wazuh manager’s databases, updating in the Wazuh manager only those files that are outdated, optimizing the data transfer of FIM. Anytime the modifications are detected in the monitored files and/or registry keys, an alert is generated.
An example alert generated by FIM looks as follow:
** Alert 1540815355.847397: - ossec,syscheck,pci_dss_11.5,gpg13_4.11,gdpr_II_5.1.f,
2018 Oct 29 13:15:55 (ubuntu) 10.0.0.144->syscheck
Rule: 550 (level 7) -> 'Integrity checksum changed.'
File '/test/hello' checksum changed.
Old md5sum was: '2a4732b1de5db823e94d662d207b8fb2'
New md5sum is : '146c07ef2479cedcd54c7c2af5cf3a80'
Old sha1sum was: 'b89f4786dcf00fb1c4ddc6ad282ca0feb3e18e1b'
New sha1sum is : 'e1efc99729beb17560e02d1f5c15a42a985fe42c'
Old sha256sum was: 'a8a3ea3ddbea6b521e4c0e8f2cca8405e75c042b2a7ed848baaa03e867355bc2'
New sha256sum is : 'a7998f247bd965694ff227fa325c81169a07471a8b6808d3e002a486c4e65975'
Old modification time was: 'Mon Oct 29 13:15:19 2018', now it is 'Mon Oct 29 13:15:54 2018'
(Audit) User: 'root (0)'
(Audit) Login user: 'test (1000)'
(Audit) Effective user: 'root (0)'
(Audit) Group: 'root (0)'
(Audit) Process id: '26089'
(Audit) Process name: '/bin/nano'
Attributes:
- Size: 4
- Permissions: 100644
- Date: Mon Oct 29 13:15:54 2018
- Inode: 537259
- User: root (0)
- Group: root (0)
- MD5: 146c07ef2479cedcd54c7c2af5cf3a80
- SHA1: e1efc99729beb17560e02d1f5c15a42a985fe42c
- SHA256: a7998f247bd965694ff227fa325c81169a07471a8b6808d3e002a486c4e65975
By default, each Wazuh agent has the syscheck enabled and preconfigured but it is recommended to review and amend the configuration of the monitored host.
File integrity monitoring results for the whole environment can be observed in Kibana app in the Overview > Integrity monitoring section:
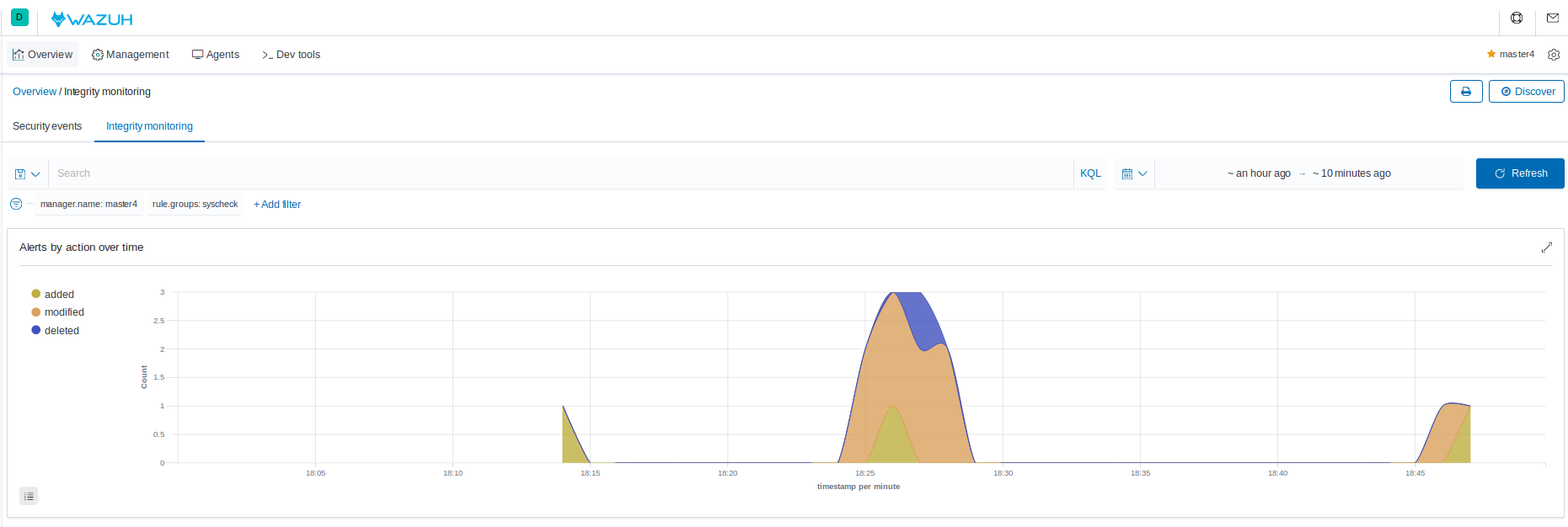
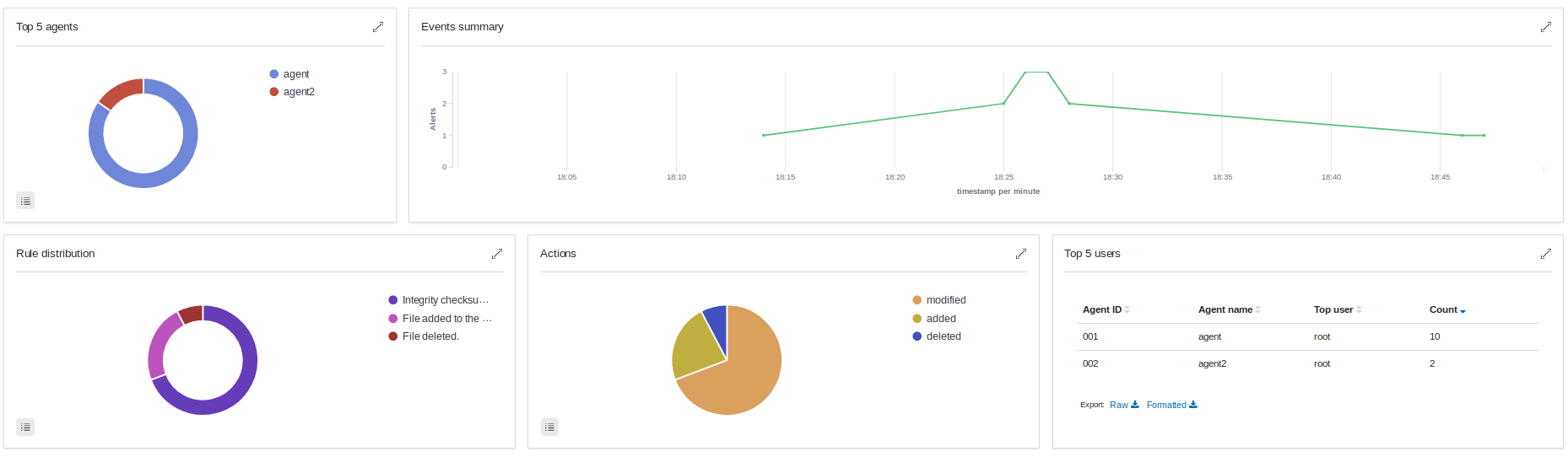
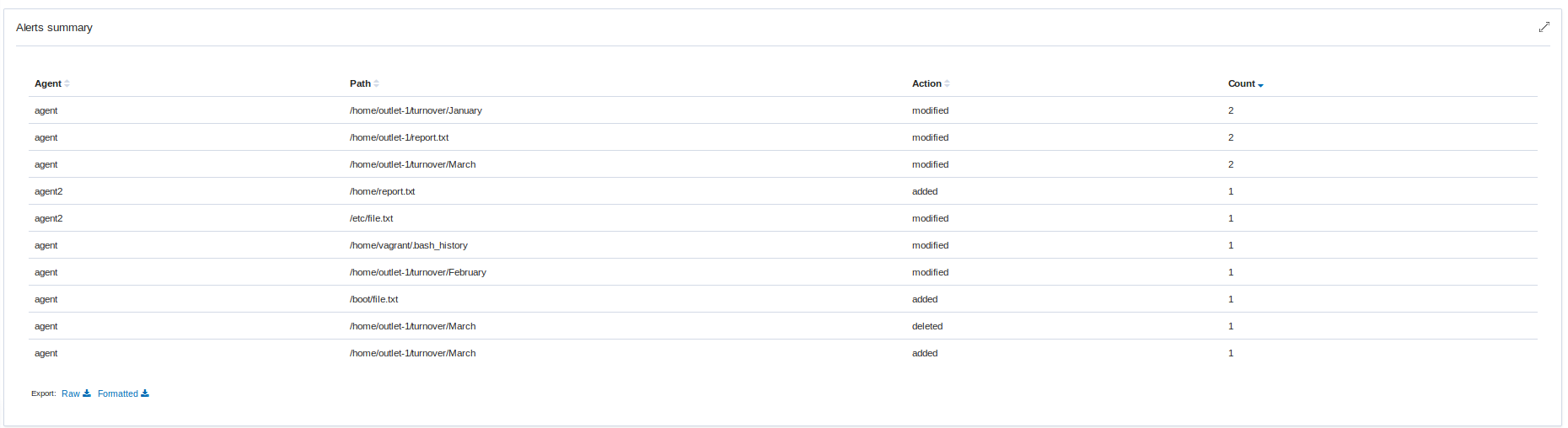
Due to the changes made on the newest FIM, only the Wazuh agents which are in version starting from 3.12 will use new functionality. All the Wazuh agents below that version will keep reporting syscheck scan results as in the older versions. If the Wazuh agent is upgraded to the v3.12 and keeps its old configuration, will still use the new FIM module and the default synchronization settings.
After the Wazuh agent service restart, the FIM database is cleared. Changes in the monitored directories done while the service is not running will not be reported to the Wazuh manager. The same will happen to the changes that occur after the last scan and before the restart, the synchronization will not take place on the directories that are not monitored with the realtime or with the whodata.
The following document contains examples for most of FIM use cases: configuring FIM.