Installation guide
This section aims to guide the user through the process of installing Wazuh and its multiple components. A brief explanation about each component and its capabilities can be found in the getting started section.
Install Wazuh server
There are two different alternatives to deploy a Wazuh installation:
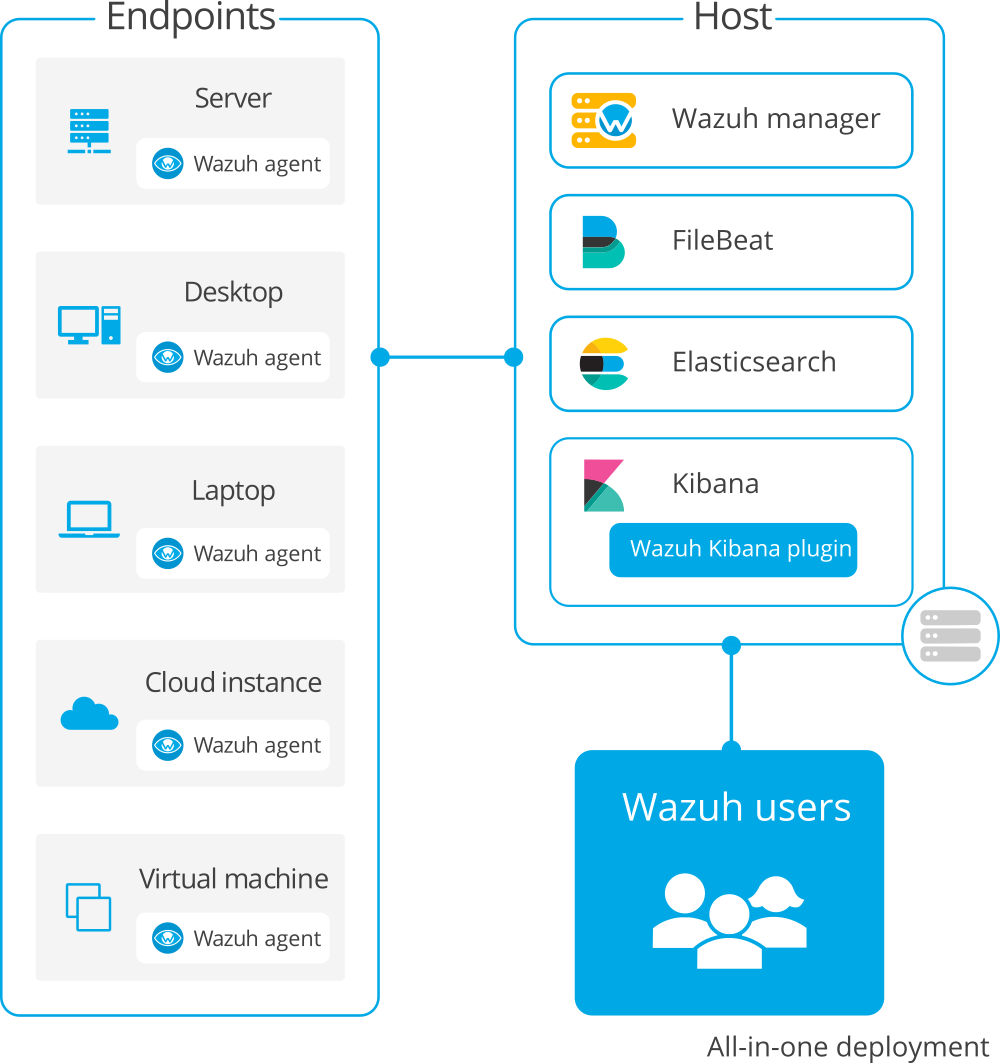
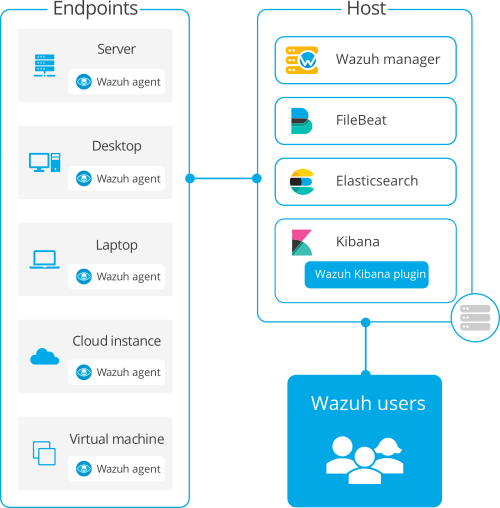
All-in-one: All the Wazuh components are installed in the same host. This type of deployment is appropriate for testing and small working environments. If you want to test Wazuh, you can download our ready-to-use OVA.
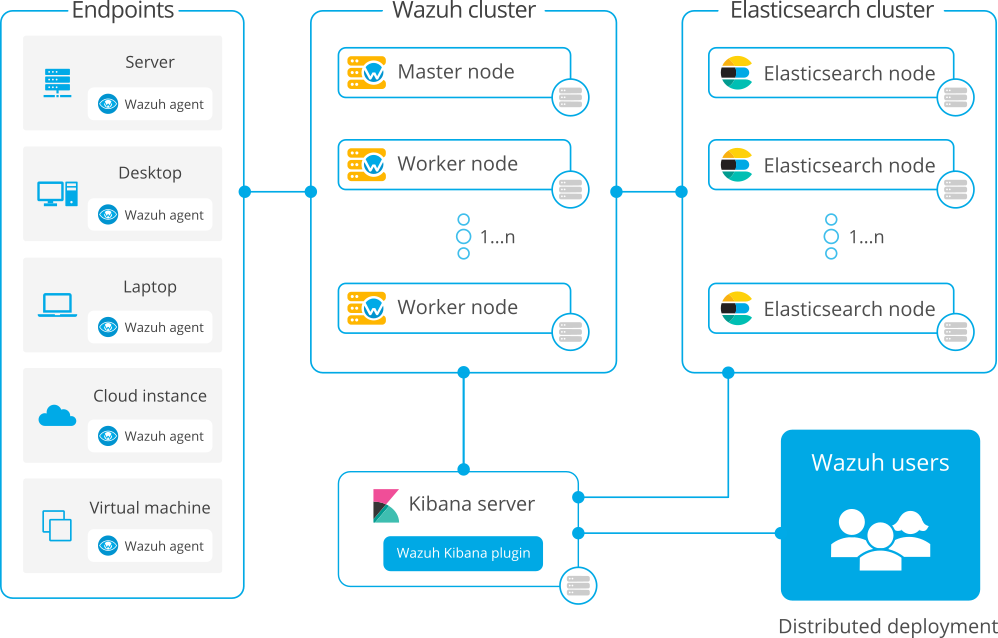
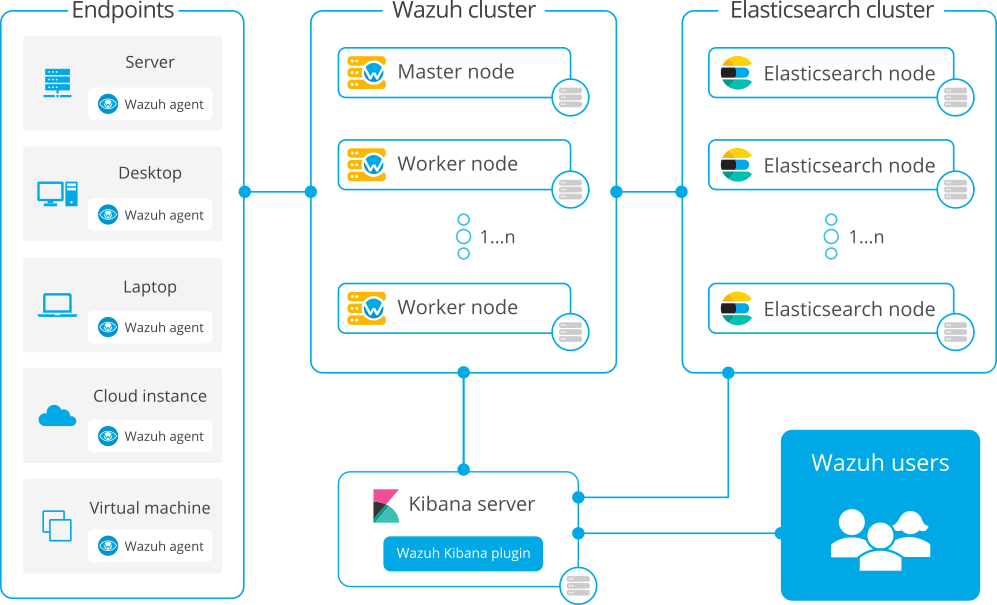
Distributed: Each component is installed in a separate host as a single-node or multi-node cluster. This type of deployment allows high availability and scalability of the product and is convenient for large working environments.
All-in-one deployment
Distributed deployment
Note
Wazuh also offers the Wazuh Cloud, where all components are hosted on our PCI-DSS certified SaaS solution and maintained by our team. With the Wazuh cloud, no dedicated hardware is required and everything is ready to use. This service offers a highly flexible infrastructure to match your enterprise needs.
This installation guide will teach you how to install all Wazuh components: the Wazuh agent, the Wazuh manager and Elastic Stack. Alternatively, Wazuh can be installed with commercial options like Elastic Stack basic license or Splunk. To learn more about these options and other installation alternatives, visit the more installation alternatives section.
Install Wazuh agents
The Wazuh Agent is a single, light-weight monitoring software that that runs on most operating systems and provides visibility into the security of that endpoint by collecting critical system and application records, inventory data and detecting potential anomalies. To install a Wazuh agent, select your operating system and follow the installation steps:
Requirements
The requirements section specifies the supported operating systems as well as the minimum recommended hardware specifications to guarantee the expected performance. Furthermore, information about the expected alerts per second depending on the different types of monitored endpoints can be found, allowing users to calculate the expected data storage needed for their environments.




