System inventory
The Wazuh agents are able to collect interesting system information and store it into an SQLite database for each agent on the manager side. The Syscollector module is in charge of this task.
How it works
As mentioned above, the main purpose of this module is to gather the most relevant information from the monitored system.
Once the agent starts, Syscollector runs periodically scans of defined targets (hardware, OS, packages, etc.), forwarding the new collected data to the manager, which updates the appropriate tables of the database.
The agent's inventory is gathered for different goals. The entire inventory can be found at the inventory tab of the Wazuh APP for each agent, by querying the Wazuh API to retrieve the data from the DB. Also the Dev tools tab is available, with this feature the Wazuh API can be directly queried about the different scans being able to filter by any desired field.
In addition, the packages and hotfixes inventory is used as feed for the Vulnerability detector module.
Available scans
The collected information from Wazuh agents is stored in different SQLite tables. Here the content of each available table is described.
At present, this module is available for Linux, Windows, MacOS, OpenBS and FreeBSD. See the compatibility matrix for more information.
Hardware
Added in version 3.2.0.
Retrieve basic information about the hardware components of a system.
Field |
Description |
Example |
Available |
|---|---|---|---|
scan_id |
Scan identifier |
573872577 |
All |
scan_time |
Scan date |
2018/07/31 15:31:26 |
All |
board_serial |
Motherboard serial number |
XDR840TUGM65E03171 |
All |
cpu_name |
CPU name |
Intel(R) Core(TM) i7-7700HQ CPU @ 2.80GHz |
All |
cpu_cores |
Number of cores of the CPU |
4 |
All |
cpu_mhz |
Current processor frequency |
900.106 |
All |
ram_total |
Total RAM (KB) |
16374572 |
All |
ram_free |
Free RAM (KB) |
2111928 |
All |
ram_usage |
Percentage of RAM in use |
87 |
All |
Operating system
Added in version 3.2.0.
Retrieve basic information about the operating system.
Field |
Description |
Example |
Available |
|---|---|---|---|
scan_id |
Scan identifier |
468455719 |
All |
scan_time |
Scan date |
2018/07/31 15:31:26 |
All |
hostname |
Hostname of the machine |
ag-ubuntu-16 |
All |
architecture |
OS architecture |
x86_64 |
All |
os_name |
OS name |
Ubuntu |
All |
os_version |
OS version |
16.04.5 LTS (Xenial Xerus) |
All |
os_codename |
OS version codename |
Xenial Xerus |
All |
os_major |
Major release version |
16 |
All |
os_minor |
Minor release version |
04 |
All |
os_build |
Optional build-specific |
14393 |
Windows |
os_release |
Windows Release ID |
SP2 |
Windows |
os_platform |
OS platform |
ubuntu |
All |
sysname |
System name |
Linux |
Linux |
release |
Release name |
4.15.0-29-generic |
Linux |
version |
Release version |
#31~16.04.1-Ubuntu SMP Wed Jul 18 08:54:04 UTC 2018 |
All |
Packages
Added in version 3.2.0.
The current packages inventory of each Wazuh agent. On Linux systems, retrieved packages can be deb or rpm types.
Field |
Description |
Example |
Available |
|---|---|---|---|
scan_id |
Scan identifier |
1454946158 |
All |
scan_time |
Scan date |
2018/07/27 07:27:14 |
All |
format |
Format of the package |
deb |
All |
name |
Name of the package |
linux-headers-generic |
All |
priority |
Priority of the package |
optional |
deb |
section |
Section of the package |
kernel |
deb/rpm/pkg |
size |
Size of the installed package in bytes |
14 |
deb/rpm |
vendor |
Vendor name |
Ubuntu Kernel Team |
deb/rpm/win |
install_time |
Date when the package was installed |
2018/02/08 18:45:48 |
rpm/win |
version |
Version of the package |
4.4.0.130.136 |
All |
architecture |
Architecture of the package |
amd64 |
All |
multiarch |
Multiarchitecture support |
same |
deb |
source |
Source of the package |
linux-meta |
deb/rpm/pkg |
description |
Description of the package |
Generic Linux kernel headers |
deb/rpm/pkg |
location |
Location of the package |
C:\Program Files\VMware\VMware Tools\ |
win/pkg |
Network interfaces
Added in version 3.5.0.
The network interfaces scan retrieves information about the existing network interface of a system (up and down interfaces) as well as their routing configuration, it is composed of three tables to ensure that the information is as structured as possible.
sys_netiface table
Field |
Description |
Example |
Available |
|---|---|---|---|
id |
Id |
1 |
All |
scan_id |
Scan identifier |
160615720 |
All |
scan_time |
Scan date |
2018/07/31 16:46:20 |
All |
name |
Interface name |
eth0 |
All |
adapter |
Physical adapter name |
Intel(R) PRO/1000 MT Desktop Adapter |
Windows |
type |
Network adapter |
ethernet |
All |
state |
State of the interface |
up |
All |
mtu |
Maximum Transmission Unit |
1500 |
All |
mac |
MAC Address |
08:00:27:C0:14:A5 |
All |
tx_packets |
Transmitted packets |
30279 |
All |
rx_packets |
Received packets |
12754 |
All |
tx_bytes |
Transmitted bytes |
10034626 |
All |
rx_bytes |
Received bytes |
1111175 |
All |
tx_errors |
Transmission errors |
0 |
All |
rx_errors |
Reception errors |
0 |
All |
tx_dropped |
Dropped transmission packets |
0 |
All |
rx_dropped |
Dropped reception packets |
0 |
All |
sys_netaddr table
Referencing interfaces described at sys_netiface, this table shows the IPv4 and IPv6 addresses associated to that interfaces.
Field |
Description |
Example |
Available |
|---|---|---|---|
id |
Referenced id from sys_netiface |
1 |
All |
scan_id |
Scan identifier |
160615720 |
All |
proto |
Protocol name |
ipv4 |
All |
address |
IPv4/IPv6 address |
192.168.1.87 |
All |
netmask |
Netmask address |
255.255.255.0 |
All |
broadcast |
Broadcast address |
192.168.1.255 |
All |
sys_netproto table
Referencing interfaces described at sys_netiface, this table shows the routing configuration for each interface.
Field |
Description |
Example |
Available |
|---|---|---|---|
id |
Referenced id from sys_netiface |
1 |
All |
scan_id |
Scan identifier |
160615720 |
All |
iface |
Interface name |
eth0 |
All |
type |
Protocol of the interface data |
ipv4 |
All |
gateway |
Default gateway |
192.168.1.1 |
Linux/Windows/macOS |
dhcp |
DHCP status |
enabled |
Linux/Windows |
Ports
Added in version 3.5.0.
List the opened ports of a system.
Field |
Description |
Example |
Available |
|---|---|---|---|
scan_id |
Scan identifier |
1618114744 |
All |
scan_time |
Scan date |
2018/07/27 07:27:15 |
All |
protocol |
Protocol of the port |
tcp |
All |
local_ip |
Local IP |
0.0.0.0 |
All |
local_port |
Local port |
22 |
All |
remote_ip |
Remote IP |
0.0.0.0 |
All |
remote_port |
Remote port |
0 |
All |
tx_queue |
Packets pending to be transmitted |
0 |
Linux |
rx_queue |
Packets at the receiver queue |
0 |
Linux |
inode |
Inode of the port |
16974 |
Linux |
state |
State of the port |
listening |
All |
PID |
PID owner of the opened port |
4 |
Windows/macOS |
process |
Name of the PID |
System |
Windows/macOS |
Processes
Added in version 3.5.0.
List the current processes running in a system host.
Field |
Description |
Example |
Available |
|---|---|---|---|
scan_id |
Scan identifier |
215303769 |
All |
scan_time |
Scan date |
2018/08/03 12:57:58 |
All |
pid |
PID of the process |
603 |
All |
name |
Name of the process |
rsyslogd |
All |
state |
State of the process |
S |
Linux/macOS |
ppid |
PPID of the process |
1 |
All |
utime |
Time spent executing user code |
157 |
Linux |
stime |
Time spent executing system code |
221 |
All |
cmd |
Command executed |
/usr/sbin/rsyslogd |
Linux/Windows |
argvs |
Arguments of the process |
-n |
Linux |
euser |
Effective user |
root |
Linux/macOS |
ruser |
Real user |
root |
Linux/macOS |
suser |
Saved-set user |
root |
Linux |
egroup |
Effective group |
root |
Linux |
rgroup |
Real group |
root |
Linux/macOS |
sgroup |
Saved-set group |
root |
Linux |
fgroup |
Filesystem group name |
root |
Linux |
priority |
Kernel scheduling priority |
20 |
All |
nice |
Nice value of the process |
0 |
Linux/macOS |
size |
Size of the process |
53030 |
All |
vm_size |
Total VM size (KB) |
212120 |
All |
resident |
Residen size of the process in bytes |
902 |
Linux |
share |
Shared memory |
814 |
Linux |
start_time |
Time when the process started |
1893 |
Linux |
pgrp |
Process group |
603 |
Linux |
session |
Session of the process |
603 |
All |
nlwp |
Number of light weight processes |
3 |
All |
tgid |
Thread Group ID |
603 |
Linux |
tty |
Number of TTY of the process |
0 |
Linux |
processor |
Number of the processor |
0 |
Linux |
Windows updates
Added in version 3.11.0.
List the Windows updates installed on Windows agents, also known as hotfixes. They are used as feed for the Vulnerability detector to find out Windows vulnerabilities.
Field |
Description |
Example |
Available |
|---|---|---|---|
scan_id |
Scan identifier |
1618114744 |
Windows |
scan_time |
Scan date |
2019/08/22 07:27:15 |
Windows |
hotfix |
Windows update ID |
KB4489899 |
Windows |
Compatibility matrix
The following table shows the operating systems that this module currently supports.
Operating System |
Syscollector scan |
||||||
Hardware |
OS |
Packages |
Network |
Ports |
Processes |
Hotfixes |
|
Windows |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
Linux |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✗ |
macOS |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✗ |
FreeBSD |
✓ |
✓ |
✓ |
✓ |
✗ |
✗ |
✗ |
OpenBSD |
✓ |
✓ |
✗ |
✓ |
✗ |
✗ |
✗ |
Using Syscollector information to trigger alerts
Since Wazuh 3.9 version,
Syscollectormodule information can be used to trigger alerts and show that information in the alerts' description.To allow this configuration, in a rule declaration set the
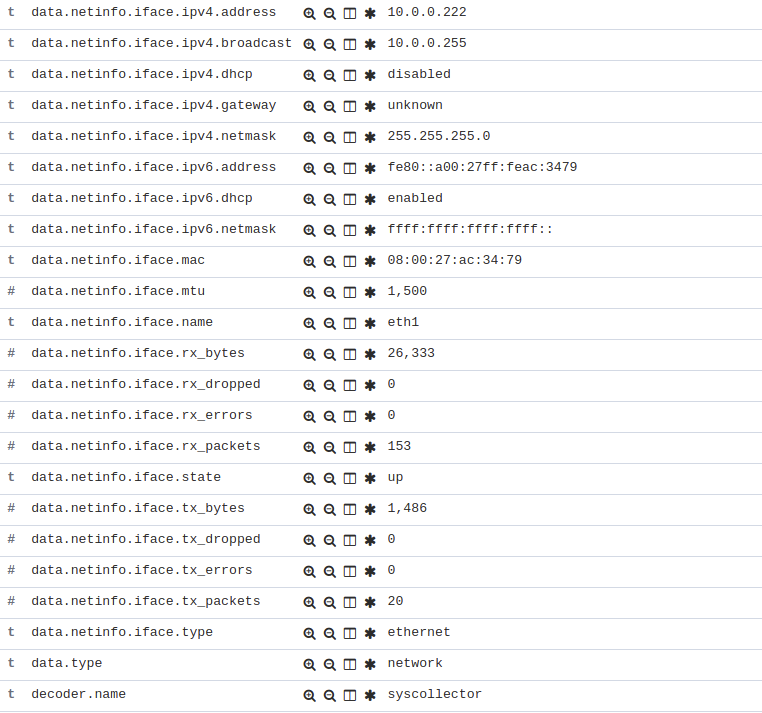
<decoded_as>field as syscollector.As an example, this rule will be triggered when the interface
eth0of an agent is enabled and will show what IPv4 has that interface.<rule id="100001" level="5"> <if_sid>221</if_sid> <decoded_as>syscollector</decoded_as> <field name="netinfo.iface.name">eth0</field> <description>eth0 interface enabled. IP: $(netinfo.iface.ipv4.address)</description> </rule>Warning
The tag
<if_sid>221</if_sid>is necessary because the events from Syscollector are muted by default with that rule.When the alerts are triggered they will be displayed in Kibana this way:
New searchable fields for Kibana
In Elasticsearch the fields will be saved as data.type.value. For example, for Hardware type, the cpu_name field can be found as data.hardware.cpu_name
Type |
Fields |
Example |
Hardware |
cpu_name, cpu_cores, cpu_mhz, ram_total, ram_free, ram_usage |
data.hardware.cpu_mhz |
Operating System |
architecture, name, version, codename, major, minor, build, platform, sysname, release, release_version |
data.os.codename |
Port |
local_ip, local_port, remote_ip, remote_port, tx_queue, rx_queue, inode, state, pid, process |
data.port.inode |
Program |
name, priority, section, size, vendor, install_time, version, architecture, multiarch, source, description, location |
data.program.name |
Process |
name, state, ppid, utime, stime, cmd, args, euser, ruser, suser, egroup, sgroup, fgroup, rgroup, priority, nice, size, vm_size, resident, share, start_time, pgrp, session, nlwp, tgid, tty, processor |
data.process.state |
Network |
mac, adapter, type, state, mtu, tx_bytes, rx_bytes, tx_errors, rx_errors, tx_dropped, rx_dropped, tx_packets, rx_packets, ipv4, ipv6 |
data.netinfo.iface.ipv4.address, data.netinfo.iface.mac |
Hotfix |
hotfix |
data.hotfix |
Use case: Visualize system inventory in the Wazuh app
The Syscollector module is enabled by default in all compatible systems including all the available scans. Here we can see the default configuration block:
<!-- System inventory -->
<wodle name="syscollector">
<disabled>no</disabled>
<interval>1h</interval>
<scan_on_start>yes</scan_on_start>
<hardware>yes</hardware>
<os>yes</os>
<network>yes</network>
<packages>yes</packages>
<ports all="no">yes</ports>
<processes>yes</processes>
</wodle>
Once the module starts, it will run periodically scans and send the new data in JSON events format to the manager, where it will be decoded and stored into a particular database for each agent.
The current inventory can be consulted in different ways. Let's see an example querying for a particular package in a Debian agent:
Querying the Database directly on the manager side, located at
$install_directory/queue/db/:agent_id.db.
# sqlite3 /var/ossec/queue/db/003.db
SQLite version 3.7.17 2013-05-20 00:56:22
Enter ".help" for instructions
Enter SQL statements terminated with a ";"
sqlite>
sqlite> select * from sys_programs where name="wazuh-agent";
696614220|2018/08/06 02:07:30|deb|wazuh-agent|extra|admin|105546|Wazuh, Inc <support@wazuh.com>||3.5.0-1|amd64|||Wazuh helps you to gain security visibility into your infrastructure by monitoring hosts at an operating system and application level. It provides the following capabilities: log analysis, file integrity monitoring, intrusions detection and policy and compliance monitoring||0
By querying the Wazuh API endpoint GET /syscollector/{agent_id}/packages, which retrieves nested data in JSON format.
# curl -k -X GET "https://localhost:55000/syscollector/003/packages?pretty=true&name=wazuh-agent" -H "Authorization: Bearer $TOKEN"
{
"data": {
"affected_items": [
{
"vendor": "Wazuh, Inc <support@wazuh.com>",
"description": "Wazuh helps you to gain security visibility into your infrastructure by monitoring hosts at an operating system and application level. It provides the following capabilities: log analysis, file integrity monitoring, intrusions detection and policy and compliance monitoring",
"scan": {"id": 696614220, "time": "2018/08/06 02:07:30"},
"section": "admin",
"format": "deb",
"name": "wazuh-agent",
"priority": "extra",
"version": "3.5.0-1",
"architecture": "amd64",
"size": 105546,
"agent_id": "003",
}
],
"total_affected_items": 1,
"total_failed_items": 0,
"failed_items": [],
},
"message": "All specified syscollector information was returned",
"error": 0,
}
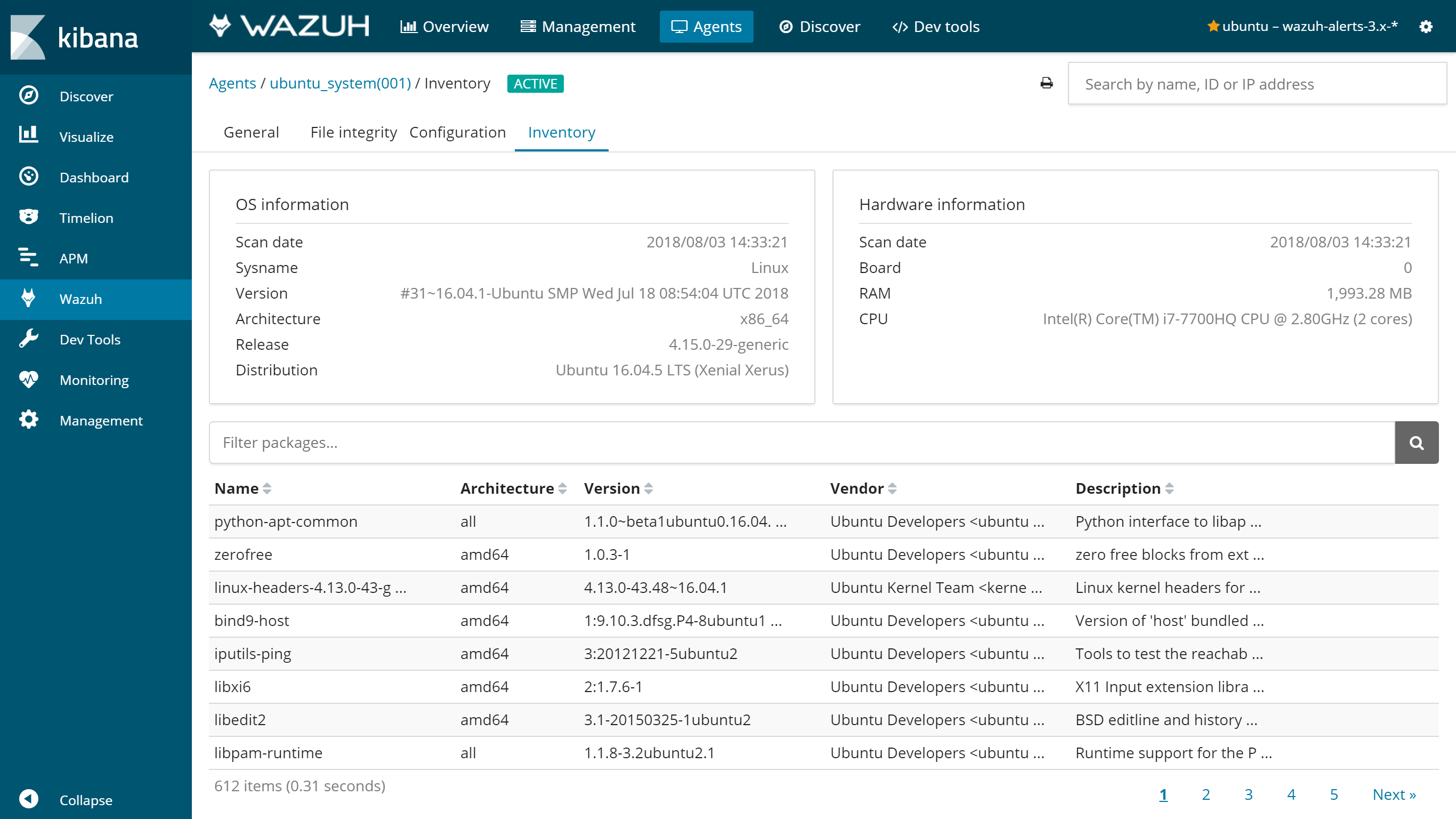
Moreover, the same information can be consulted at the Wazuh app, which includes an Inventory tab for each agent. For now, there are available OS, hardware and packages inventories at this tab, which looks like the following screenshot:
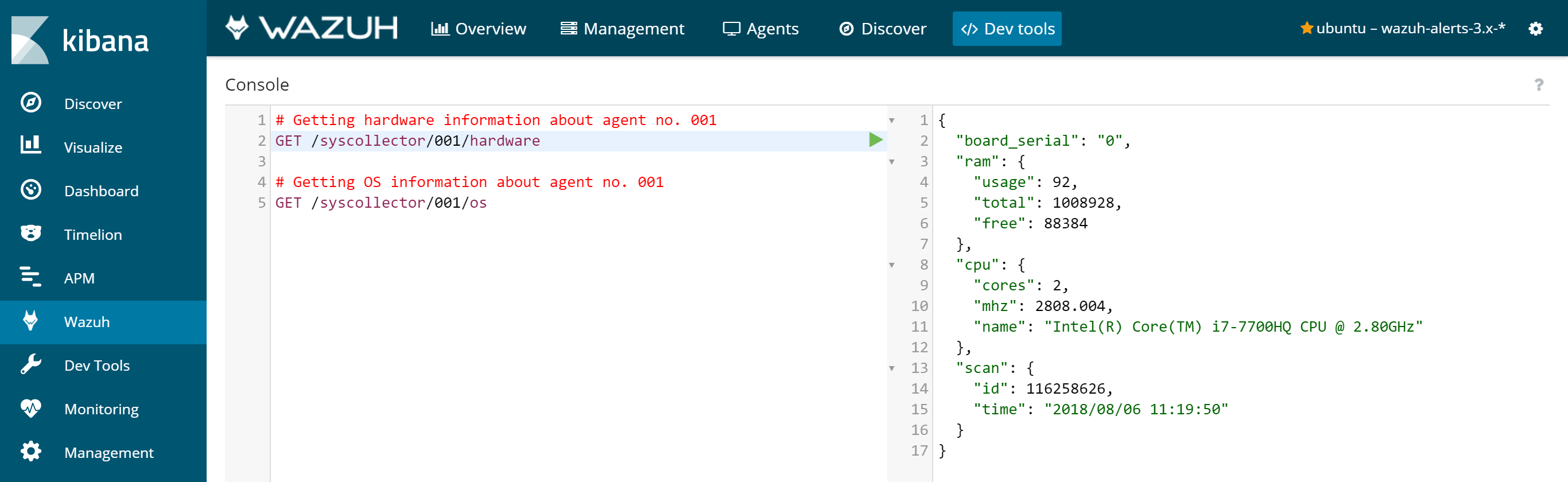
The Dev tools tab is also available to query the Wazuh API directly from the Wazuh app as shown below:
You could find more information about how to configure this capability at the Syscollector configuration reference.