Vulnerability detection
Added in version 3.2.0.
This capability can be used to detect applications that are known to be vulnerable (affected by a CVE).
How it works
To be able to detect vulnerabilities, now agents are able to natively collect a list of installed applications, sending it periodically to the manager (where it is stored in local sqlite databases, one per agent). In addition, the manager builds a global vulnerabilities database, using public OVAL CVE repositories, using it later to cross correlate this information with agent's applications inventory data.
The global vulnerabilities database is created automatically, currently pulling data from the following repositories:
https://canonical.com: Used to pull CVEs for Ubuntu Linux distributions.
https://access.redhat.com: Used to pull CVEs for Red Hat and CentOS Linux distributions.
https://www.debian.org: Used to pull CVEs for Debian Linux distributions.
This database can be configured to be updated periodically, ensuring that the solution will check for the very latest CVEs.
Once the global vulnerabilty database (with the CVEs) is created, the detection process will look for vulnerable packages in the inventory databases (unique per agent). Alerts are generated when a CVE (Common Vulnerabilities and Exposures) affects a package that is known to be installed in one of the monitored servers.
Compatibility matrix
The following table shows the operating systems that the vulnerability detector currently supports (we are working in supporting new ones) and the OVAL configuration needed for each distribution:
Distribution |
Versions |
Configuration feed |
|---|---|---|
Red Hat & CentOS |
5 |
Red Hat Security Data |
6 |
||
7 |
||
Ubuntu |
12 |
Ubuntu 12 OVAL |
14 |
Ubuntu 14 OVAL |
|
16 |
Ubuntu 16 OVAL |
|
18 |
Ubuntu 18 OVAL |
|
Debian |
7 |
Debian 7 OVAL |
8 |
Debian 8 OVAL |
|
9 |
Debian 9 OVAL |
|
Amazon Linux |
1 |
Red Hat Security Data |
2 |
Use case: Running a vulnerability scan
The following example shows how to configure the necessary components to run the vulnerability detection process.
Enable the agent module used to collect installed packages on the monitored system.
You can do this adding the following block of settings to your shared agent configuration file:
<wodle name="syscollector"> <disabled>no</disabled> <interval>1h</interval> <packages>yes</packages> </wodle>
Check Syscollector settings for more details.
Enable the manager module used to detect vulnerabilities.
You can do this adding the following block of settings to your manager configuration file:
<wodle name="vulnerability-detector"> <disabled>no</disabled> <interval>5m</interval> <run_on_start>yes</run_on_start> <feed name="ubuntu-18"> <disabled>no</disabled> <update_interval>1h</update_interval> </feed> </wodle>
Remember to restart the manager to apply the changes:
For Systemd:
# systemctl restart wazuh-manager
For SysV Init:
# service wazuh-manager restart
Check Vulnerability detector settings for more details.
The following fields are captured in every alert:
CVE: The CVE identifier for the corresponding vulnerability.
Title: Short description of the impact of vulnerability.
Severity: It specifies the impact of the vulnerability in terms of security.
Published: Date when the vulnerability was included in the official database.
Reference: URL of the official database website with extra information of the vulnerability.
Rationale: Broad description of the vulnerability.
State: This field informs if it exists a patch for the vulnerability (fixed) or instead, its state.
See below for examples of alerts:
2019 Apr 23 08:21:06 master->vulnerability-detector
{"vulnerability":{"cve":"CVE-2018-18445","title":"kernel: Faulty computation of numberic bounds in the BPF verifier","severity":"Medium","published":"2018-10-05T00:00:00+00:00","state":"Fixed","cvss":{"cvss3_score":"4.700000"},"package":{"name":"kernel","version":"3.10.0-957.5.1.el7","condition":"less than 3.10.0-957.10.1.el7"},"advisories":"RHSA-2019:0512,RHSA-2019:0514","cwe_reference":"CWE-125","bugzilla_reference":"https://bugzilla.redhat.com/show_bug.cgi?id=1640596","reference":"https://access.redhat.com/security/cve/CVE-2018-18445"}}
vulnerability.cve: CVE-2018-18445
vulnerability.title: kernel: Faulty computation of numberic bounds in the BPF verifier
vulnerability.severity: Medium
vulnerability.published: 2018-10-05T00:00:00+00:00
vulnerability.state: Fixed
vulnerability.cvss.cvss3_score: 4.700000
vulnerability.package.name: kernel
vulnerability.package.version: 3.10.0-957.5.1.el7
vulnerability.package.condition: less than 3.10.0-957.10.1.el7
vulnerability.advisories: RHSA-2019:0512,RHSA-2019:0514
vulnerability.cwe_reference: CWE-125
vulnerability.bugzilla_reference: https://bugzilla.redhat.com/show_bug.cgi?id=1640596
vulnerability.reference: https://access.redhat.com/security/cve/CVE-2018-18445
2019 Apr 23 08:21:06 master->vulnerability-detector
{"vulnerability":{"cve":"CVE-2019-9636","title":"python: Information Disclosure due to urlsplit improper NFKC normalization","severity":"High","published":"2019-03-06T00:00:00+00:00","state":"Fixed","cvss":{"cvss3_score":"9.800000"},"package":{"name":"python","version":"2.7.5-76.el7","condition":"less than 2.7.5-77.el7_6"},"advisories":"RHSA-2019:0710,RHSA-2019:0765","cwe_reference":"CWE-172","bugzilla_reference":"https://bugzilla.redhat.com/show_bug.cgi?id=1688543","reference":"https://access.redhat.com/security/cve/CVE-2019-9636"}}
vulnerability.cve: CVE-2019-9636
vulnerability.title: python: Information Disclosure due to urlsplit improper NFKC normalization
vulnerability.severity: High
vulnerability.published: 2019-03-06T00:00:00+00:00
vulnerability.state: Fixed
vulnerability.cvss.cvss3_score: 9.800000
vulnerability.package.name: python
vulnerability.package.version: 2.7.5-76.el7
vulnerability.package.condition: less than 2.7.5-77.el7_6
vulnerability.advisories: RHSA-2019:0710,RHSA-2019:0765
vulnerability.cwe_reference: CWE-172
vulnerability.bugzilla_reference: https://bugzilla.redhat.com/show_bug.cgi?id=1688543
vulnerability.reference: https://access.redhat.com/security/cve/CVE-2019-9636
Here we can see an alert in Kibana:
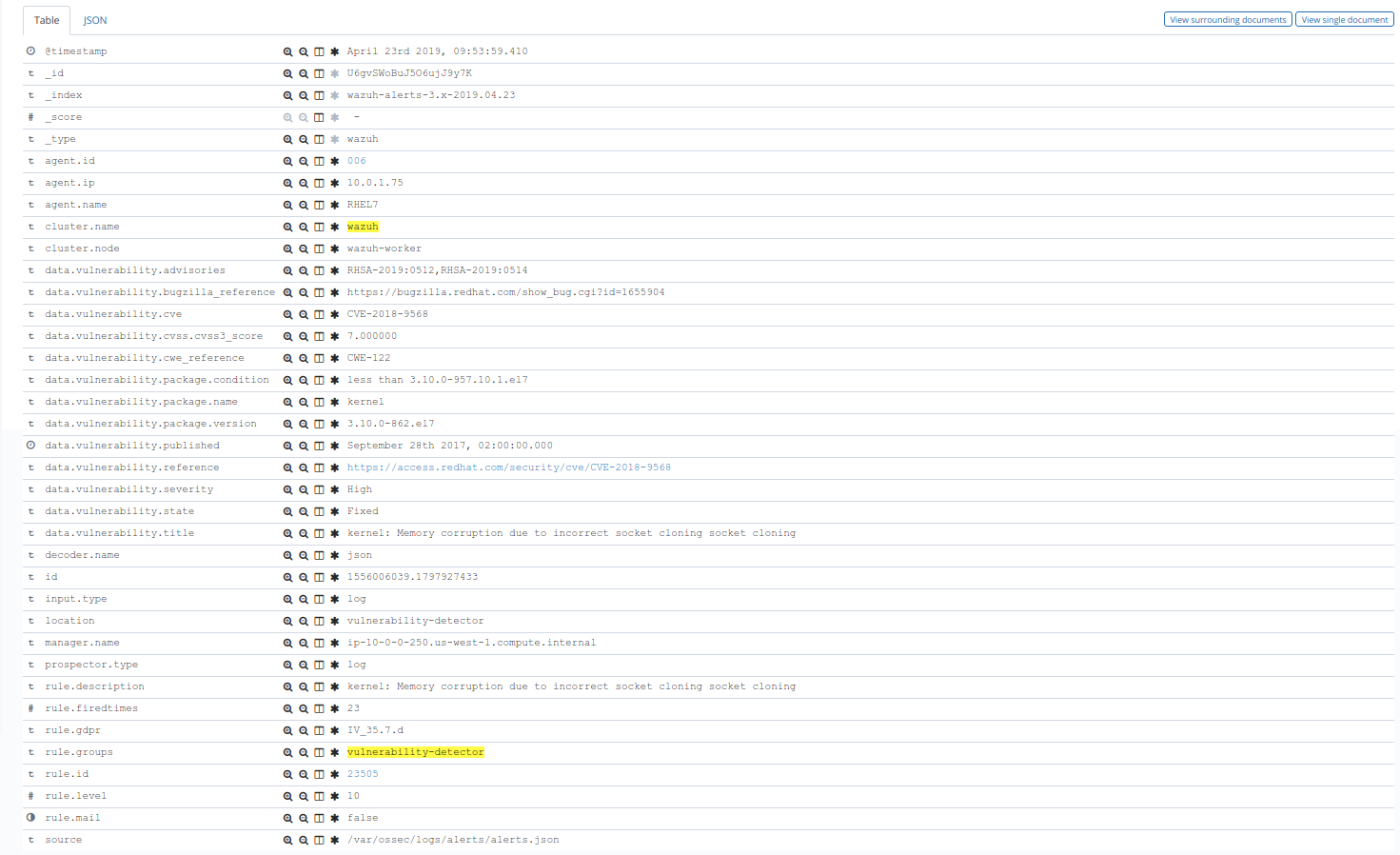
One more example, this time in Splunk:
