Amazon Inspector
Amazon Inspector is an automated security assessment service that helps improve the security and compliance of applications deployed on AWS. Two versions are available:
Amazon Inspector Classic: The original service, which assesses applications for exposure, vulnerabilities, and deviations from best practices.
Amazon Inspector (v2): The new version, offering consolidated scanning for EC2 instances, container images in Amazon ECR, and AWS Lambda functions.
Both versions produce detailed security findings prioritized by severity. Findings can be reviewed directly or included in assessment reports accessible via the Amazon Inspector console or API.
AWS configuration
Learn how to configure Amazon Inspector (Classic and v2) integration in Wazuh.
Amazon Inspector Classic configuration
Amazon Inspector (v2) is available in your AWS account. To start using it:
Open the Amazon Inspector page in the AWS Management Console.
Click Get Started to access the dashboard.
Configure your scanning preferences under General settings:
Enable EC2 scanning
Enable ECR scanning
Enable Lambda function scanning
Note
For detailed instructions on configuring scanning preferences, see the Amazon Inspector documentation.
To start using Amazon Inspector Classic, go to the AWS management console, search for "Amazon Inspector" and click it from the results. Once there, click on the left-side menu.
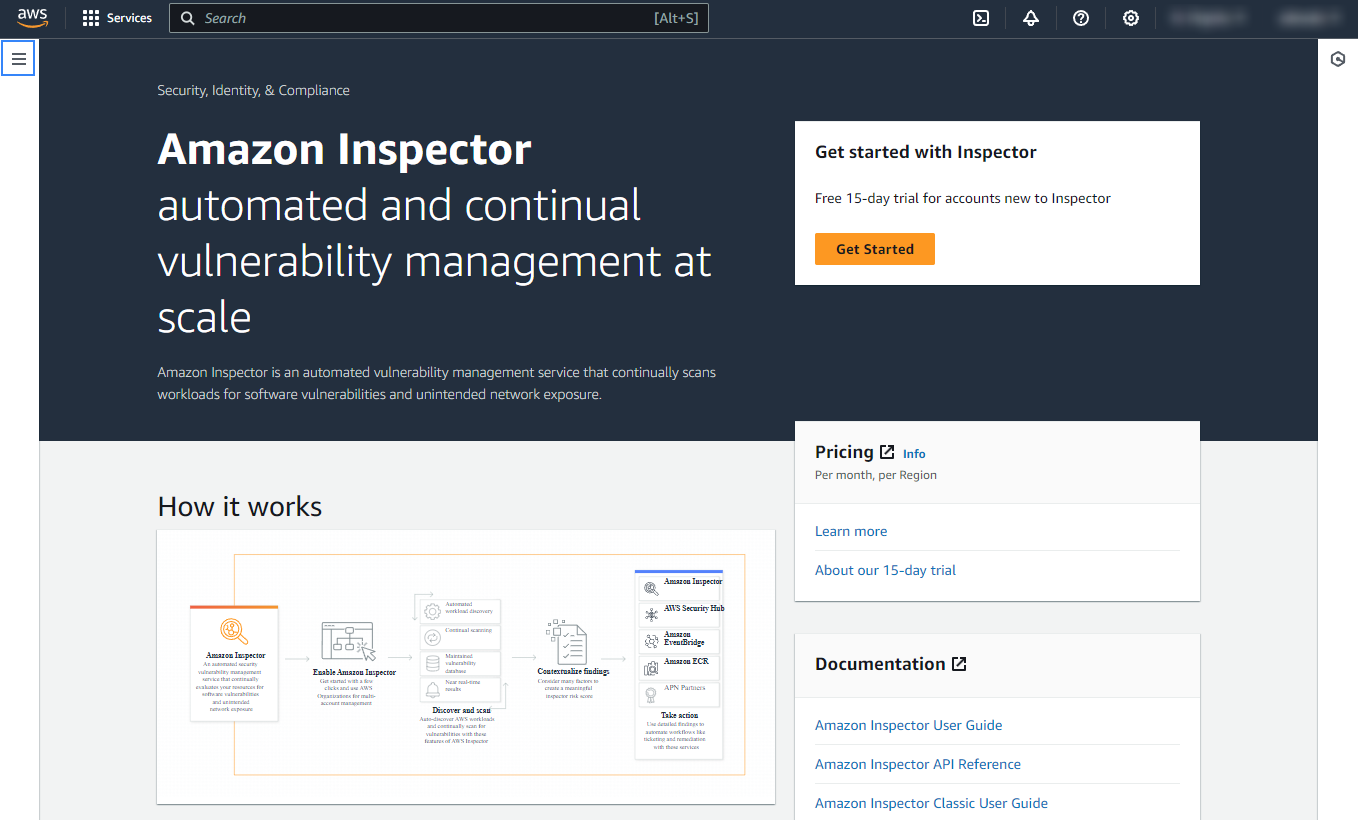
Click on Switch to Inspector Classic.
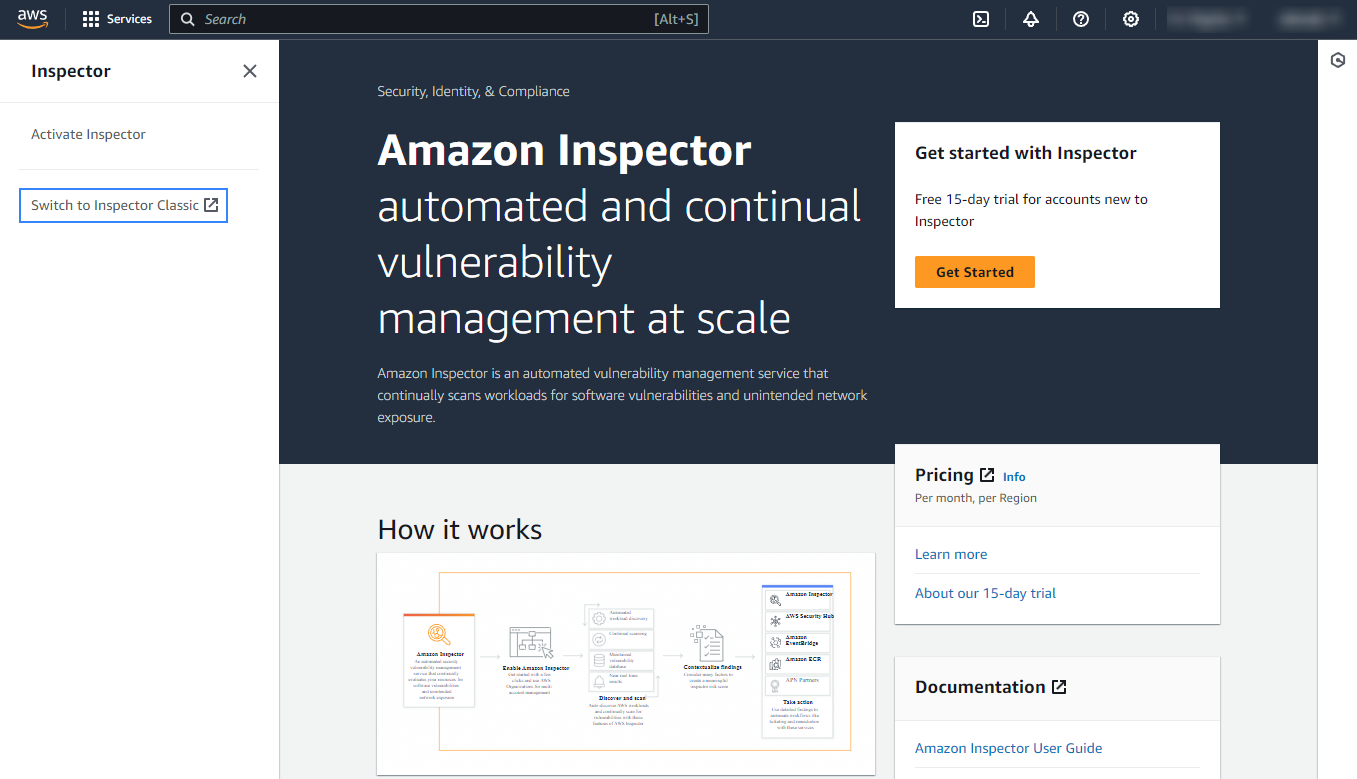
On the Amazon Inspector Classic page, click Get started.
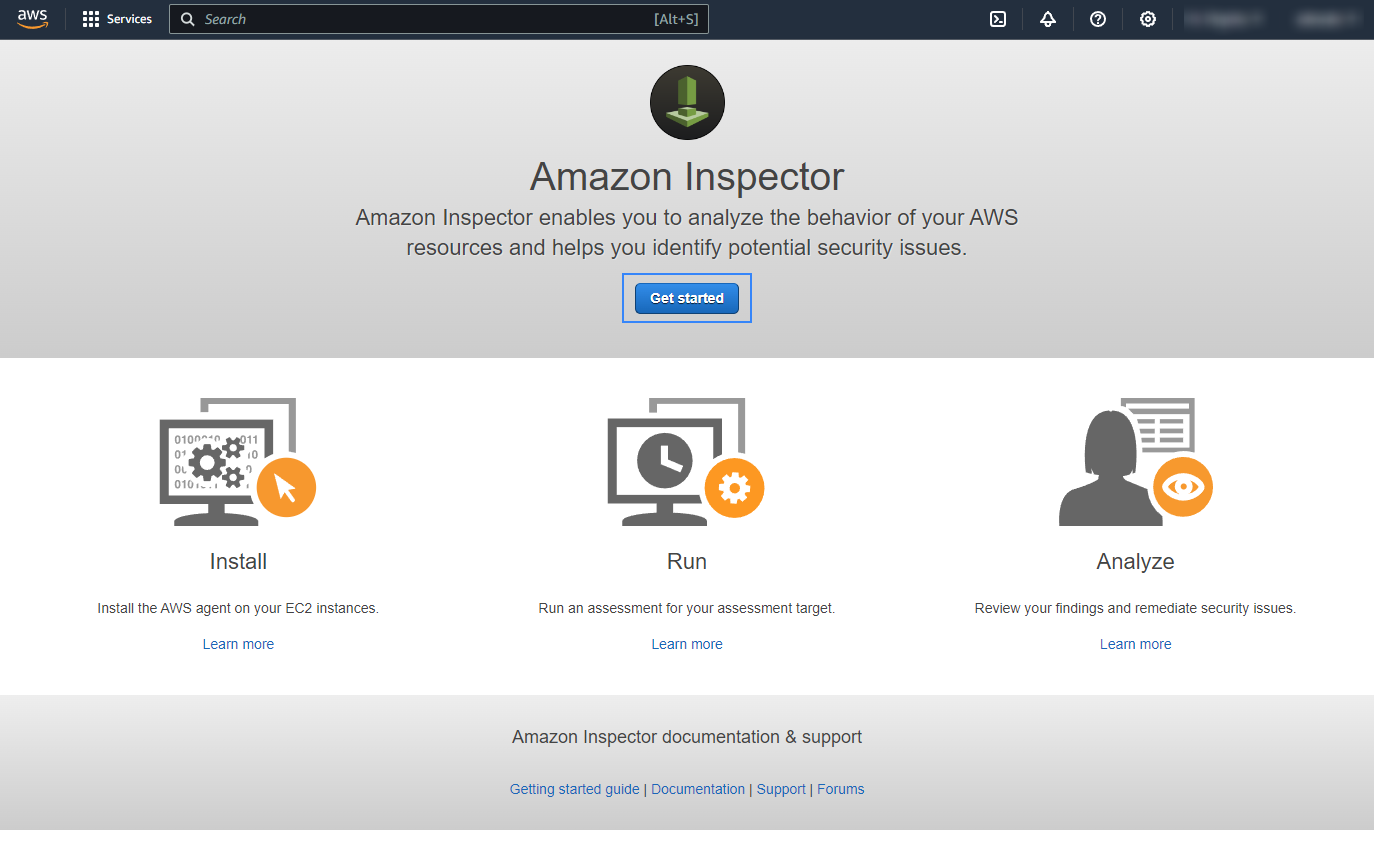
Click on Advanced setup.
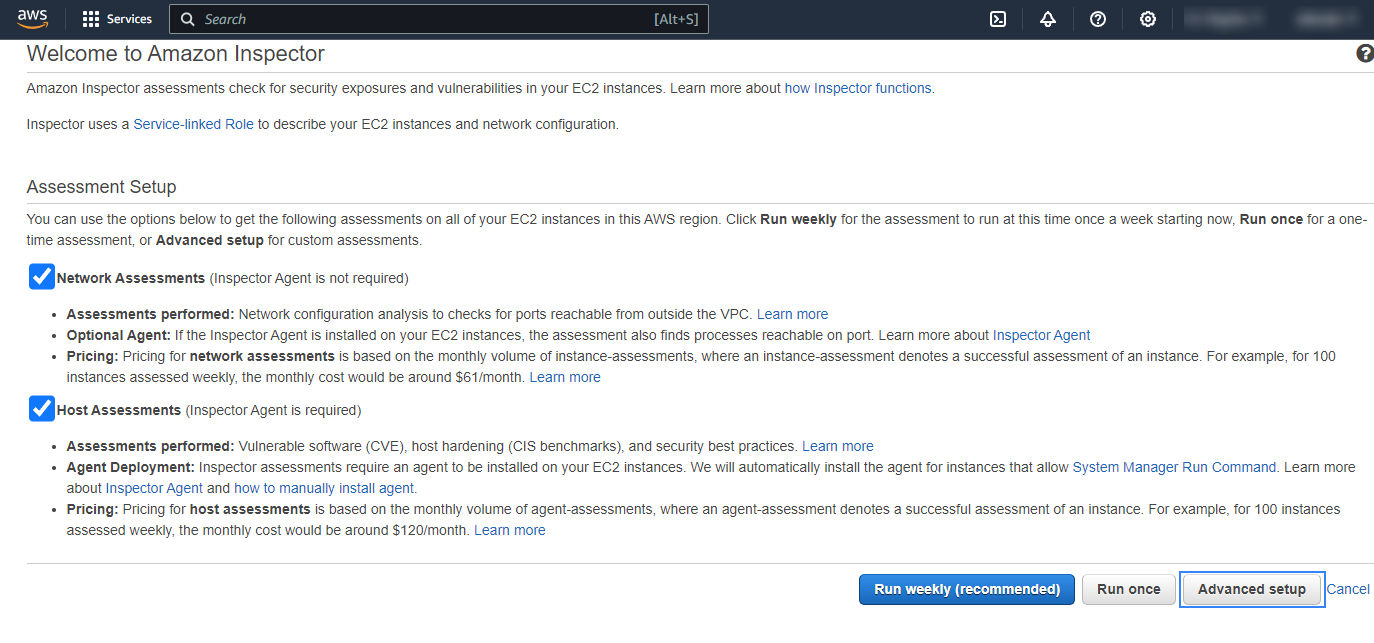
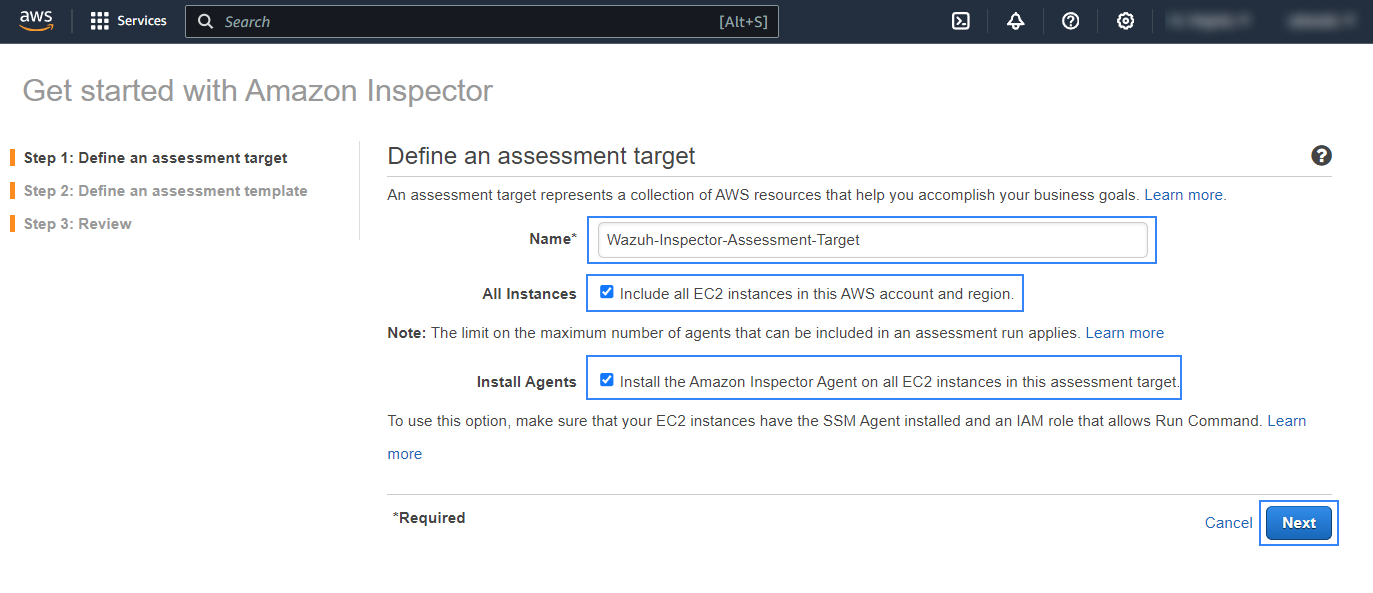
Configure the assessment target:
Choose a name for the assessment target.
Select if you are going to include all EC2 instances in the scans or if you prefer to filter them based on a tag by enabling or disabling the Include all EC2 instances in this AWS account and region checkbox.
If you prefer to install the agents manually, disable the Install the Amazon Inspector Agent on all EC2 instances in this assessment target checkbox.
Click on Next.
Note
If you prefer to install the Inspector Classic agents manually, follow the instructions on the installing Amazon Inspector Classic agents guide.
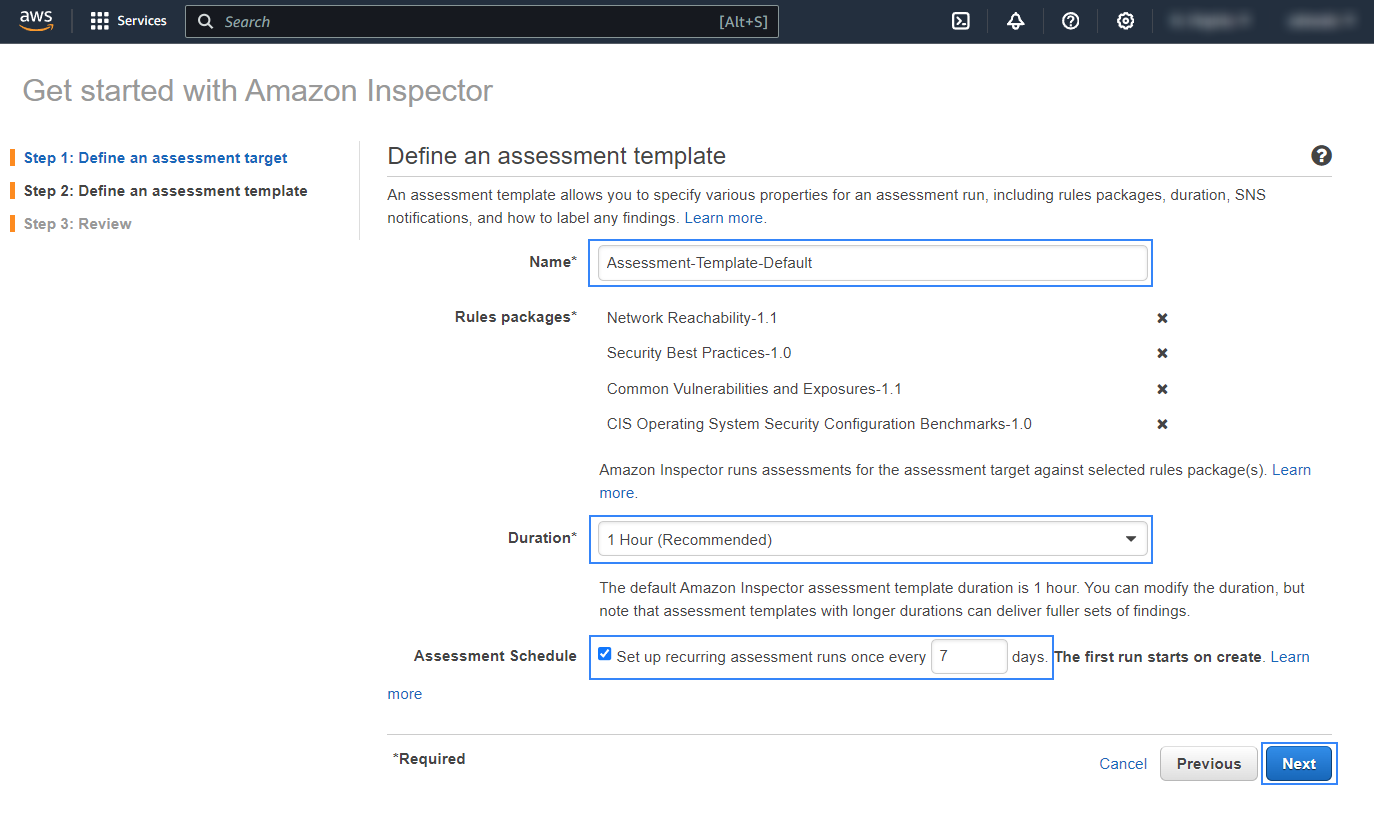
Configure the assessment template. Choose the name, duration, and frequency of the analysis and click on Next.
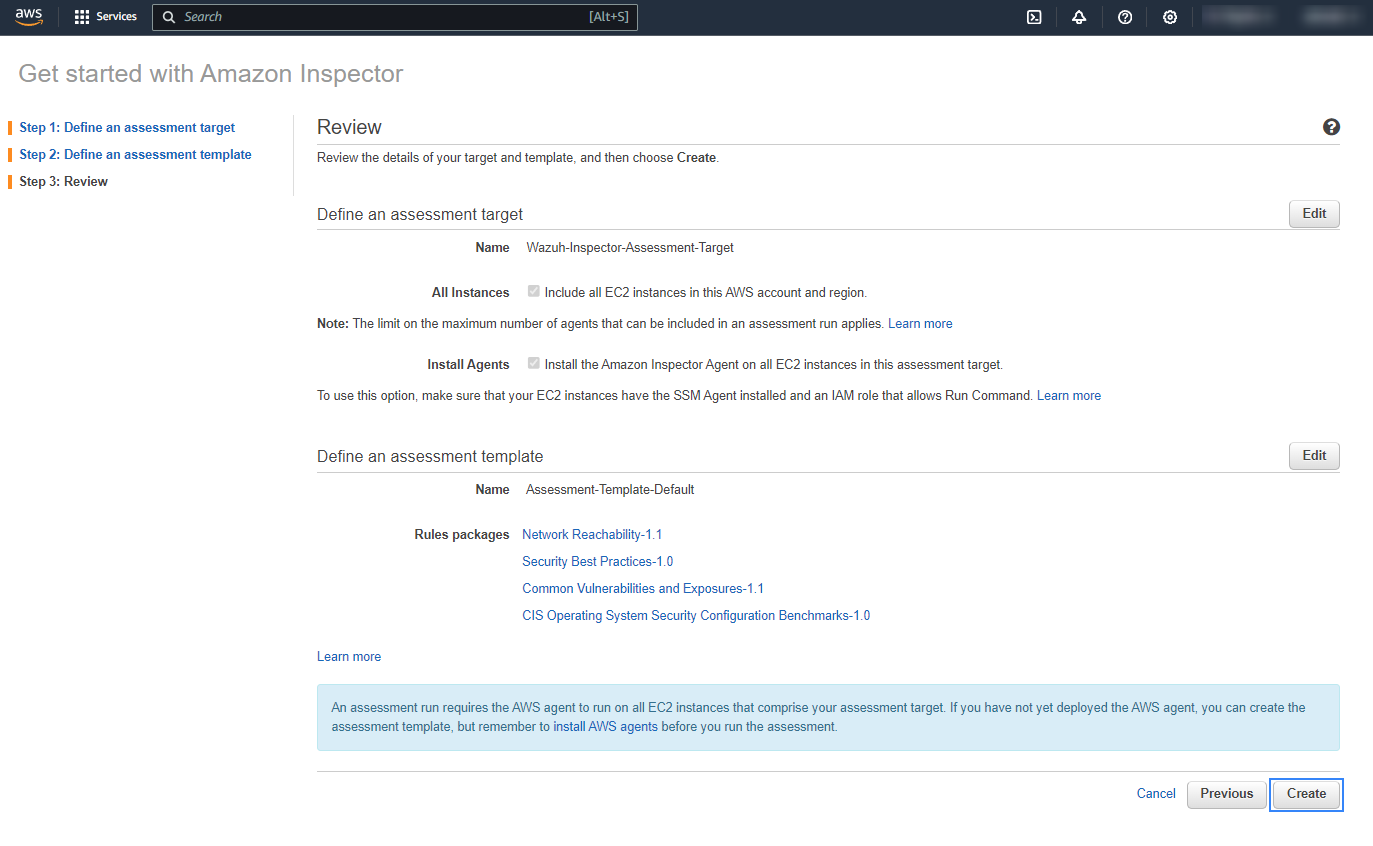
Finally, review the details of the configured target and template and click on Next.
Policy configuration
Follow the creating an AWS policy guide to create a policy using the Amazon Web Services console.
Take into account that the policies below follow the principle of least privilege to ensure that only the minimum permissions are provided to the AWS IAM user.
To allow an AWS user to use the Wazuh module for AWS with read-only permissions, it must have a policy like the following attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"inspector:ListFindings",
"inspector:DescribeFindings",
"inspector2:ListFindings"
],
"Resource": "*"
}
]
}
After creating a policy, you can attach it directly to a user or to a group to which the user belongs. In attaching a policy to an IAM user group, you see how to attach a policy to a group. More information on how to use other methods is available in the AWS documentation.
Configure Wazuh to process Amazon Inspector logs
Access the Wazuh configuration in Server management > Settings using the Wazuh dashboard or by manually editing the
/var/ossec/etc/ossec.conffile in the Wazuh server or agent.
Add the following Wazuh module for AWS configuration block to enable the integration with both Inspector versions:
<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>no</run_on_start> <skip_on_error>no</skip_on_error> <service type="inspector"> <aws_profile>default</aws_profile> <regions>us-east-1,us-east-2</regions> </service> </wodle>
You must specify at least a region. You can add multiple comma-separated regions.
Note
The same configuration block processes findings from both Inspector Classic and Inspector (v2). Findings from v2 will have
aws.sourceset toinspector2.Save the changes and restart Wazuh to apply the changes. The service can be manually restarted using the following command outside the Wazuh dashboard:
Wazuh manager:
# systemctl restart wazuh-manager
Wazuh agent:
# systemctl restart wazuh-agent