Detecting a brute-force attack
Brute forcing SSH (on Linux) or RDP (on Windows) are common attack vectors. Wazuh provides out-of-the-box rules capable of identifying brute-force attacks by correlating multiple authentication failure events.
To see an example use case where you configure an active response to block the IP of an attacker, check the Blocking attacks with Active Response section of the documentation.
Configuration
Configure your environment as follows to test the POC.
Make sure you have SSH installed and enabled in a system chosen to play as an attacker.
Install Hydra on an external Linux system to execute brute-force attacks.
yum install -y hydra
Steps to generate the alerts
Replace
<centos.agent.endpoint>for Linux and<win.agent.endpoint>for Windows with the appropriate destination in the following commands and run multiple failed authentication failure attempts against the monitored endpoints.For the monitored Linux endpoint:
# hydra -l badguy -p wrong_password <centos.agent.endpoint> ssh
For the monitored Windows endpoint:
# hydra -l Administrator -p wrong_password <win.agent.endpoint> rdp
Query the alerts
You can visualize the alert data in the Wazuh Kibana plugin. To do this, go to the Security events module and add the filters in the search bar to query the alerts.
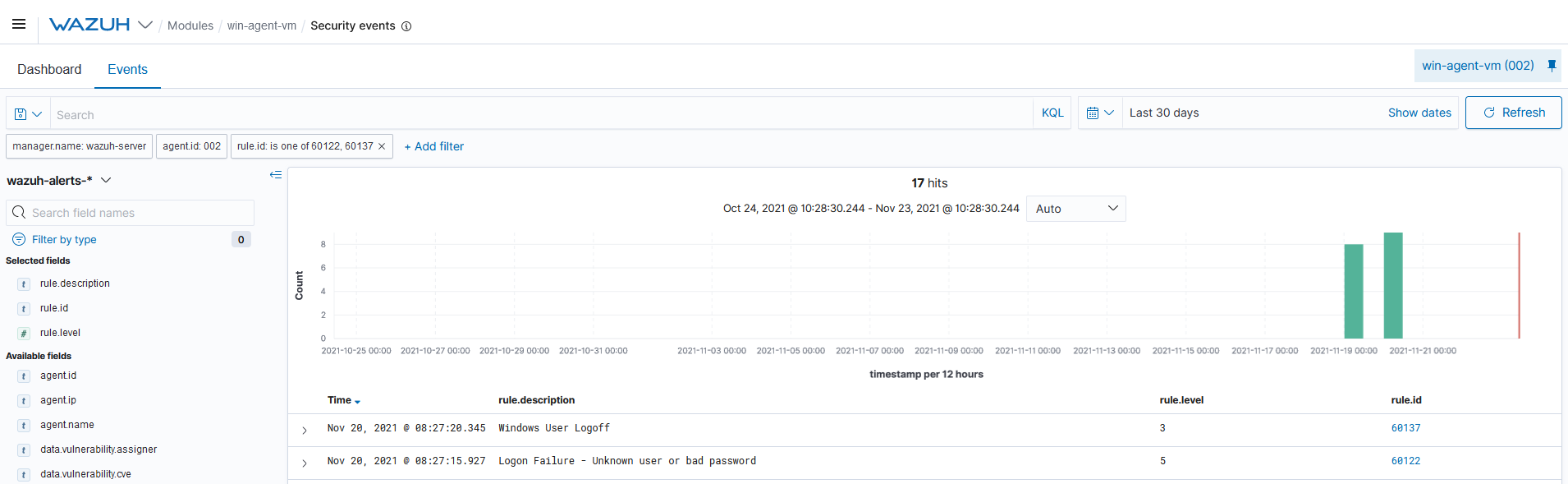
Linux:
rule.id:(5710 OR 5712). Other related rules are5711,5716,5720,5503,5504.
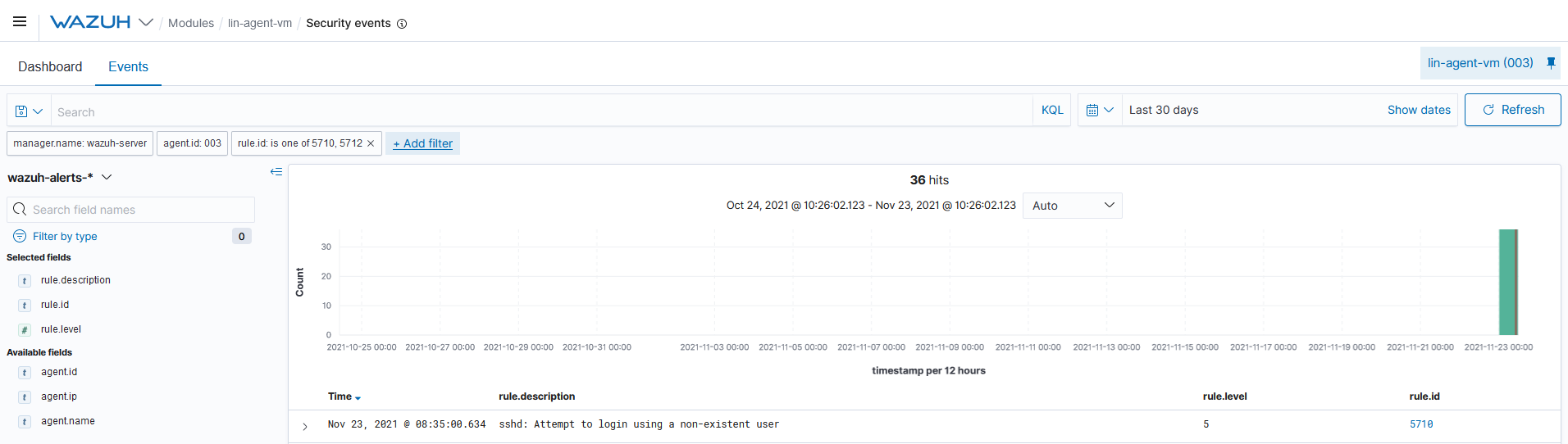
Windows:
rule.id:(60122 OR 60137)