File integrity monitoring
In this POC, the Wazuh File Integrity Monitoring (FIM) system watches for modifying files in the monitored directories. Then FIM triggers alerts when these files are modified. Additionally, it enriches alert data by fetching information about the user who made the changes and the process at play.
See the File integrity monitoring section of our documentation for more information about FIM functionality and configuration.
Configuration
Configure your environment as follows to test the POC.
Edit
/var/ossec/etc/ossec.confin the monitored CentOS 8 endpoint and enable whodata by addingwhodata="yes"to the monitored directories.<syscheck> <directories check_all="yes" whodata="yes">/usr/bin,/usr/sbin</directories> <directories check_all="yes" whodata="yes">/bin,/sbin,/boot</directories> <directories check_all="yes" report_changes="yes" whodata="yes" tags="cron">/etc/cron*</directories> <directories check_all="yes" report_changes="yes" whodata="yes" recursion_level="2">/home,/root</directories> </syscheck>
Edit
C:\Program Files (x86)\ossec-agent\ossec.confin the monitored Windows endpoint and add directories for monitoring including thewhodata="yes"switch.<syscheck> <scan_on_start>yes</scan_on_start> <directories check_all="yes" report_changes="yes" whodata="yes">C:\\Users\\Administrator\\Desktop</directories> <directories check_all="yes" report_changes="yes" whodata="yes">C:\\Wazuh</directories> </syscheck>
As an alternative to local configurations, you can centrally configure groups of agents.
Steps to generate the alerts
Create, remove, or modify a file in the monitored directories.
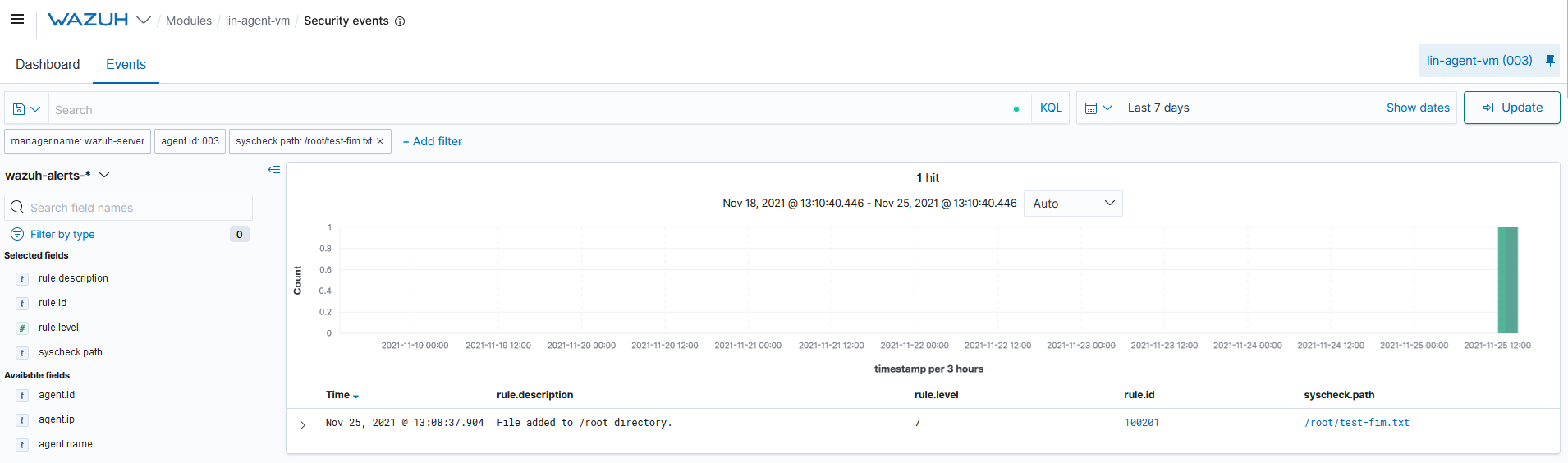
Query the alerts
You can visualize the alert data in the Wazuh Kibana plugin. To do this, go to the Security events module and add the filters in the search bar to query the alerts.
syscheck.path: "{path_to_the_modified_file}"