How it works
To be able to detect vulnerabilities, now agents are able to natively collect a list of installed applications, sending it periodically to the manager (where it is stored in local sqlite databases, one per agent). Also, the manager builds a global vulnerability database, from publicly available CVE repositories, using it later to cross-correlate this information with the agent's applications inventory data.
The global vulnerability database is created automatically, currently pulling data from the following repositories:
https://canonical.com: Used to pull CVEs for Ubuntu Linux distributions.
https://www.redhat.com: Used to pull CVEs for Red Hat and CentOS Linux distributions.
https://www.debian.org: Used to pull CVEs for Debian Linux distributions.
https://nvd.nist.gov/: Used to pull CVEs from the National Vulnerability Database.
https://feed.wazuh.com/: Used to pull the MSU feed with CVEs and patches for Microsoft products.
This database can be configured to be updated periodically, ensuring that the solution will check for the very latest CVEs.
Once the global vulnerability database (with the CVEs) is created, the detection process looks for vulnerable packages in the inventory databases (unique per agent). Alerts are generated when a CVE (Common Vulnerabilities and Exposures) affects a package that is known to be installed in one of the monitored servers. A package is labeled as vulnerable when its version is contained within the affected range of a CVE. The results are presented as alerts and also stored in a database. So you can check the last scan alerts, or query every single agent's vulnerable software DB.
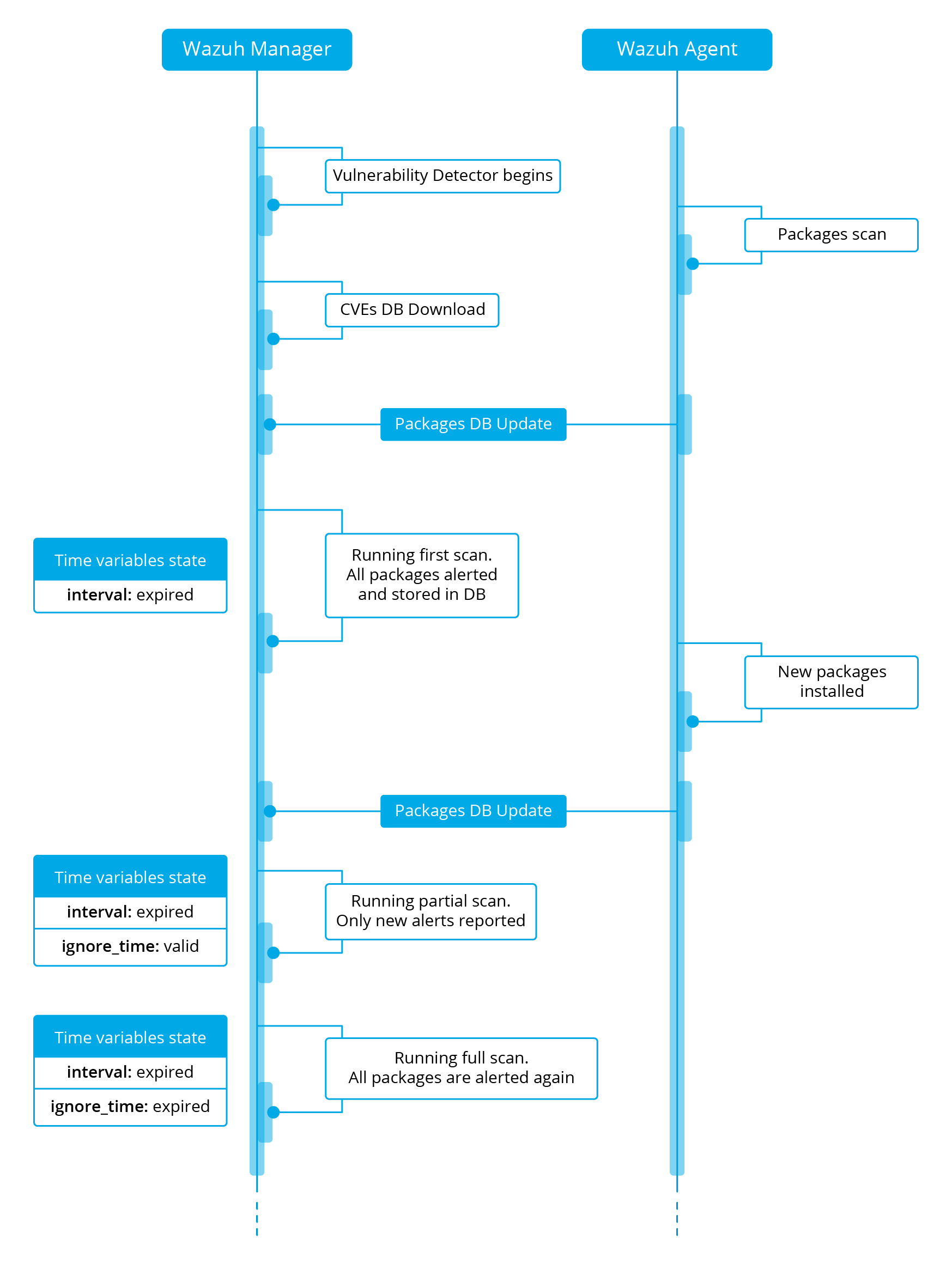
Scan types
The Vulnerability Detector module can run a scan on startup (run_on_start) and every certain period of time (interval). In any of these cases, the packages that have already been scanned will wait until the ignore_time expires to be re-scanned. This improves the performance and avoids repeated alerts during a configurable time. We have then two different types of scan:
Full scan: The first time, Vulnerability Detector scans every single package installed. After this, all the available packages are scanned again only when the configured ignore_time expires.
Partial scans: Only new packages are scanned while ignore_time is still valid.
There are few considerations that arise from this behavior:
Every full scan generates alerts for all the packages, so the alerts are repeated until they get fixed.
The user cannot trigger a full scan manually, the only option is to decrease the ignore_time setting.
The partial scans generate alerts for new packages, but they do not delete alerts for removed packages.
Partial scans can be triggered with a Manager restart.
Check Vulnerability detector settings for more configuration details.
The following example may be useful to understand all steps involved