Detecting and removing malware using VirusTotal integration
Wazuh is capable of connecting to external APIs and alerting tools such as VirusTotal. In this POC, you scan a directory for changes and make the wazuh-integratord component query VirusTotal for threat results using the VirusTotal API. Once VirusTotal identifies a file as a threat, Wazuh is configured to trigger an active response to remove the file from the system.
For more information on this service, check the VirusTotal integration section of the documentation.
Configuration
Configure your environment as follows to test the POC.
Enable File Integrity Monitoring in
/var/ossec/etc/ossec.confat the CentOS 8 endpoint to monitor/rootin real time.<syscheck> <directories whodata="yes">/root</directories> </syscheck>
Add the following rules to
/var/ossec/etc/rules/local_rules.xmlat the Wazuh manager. These rules are to alert about changes in/rootdirectories detected by FIM scans.<group name="syscheck,pci_dss_11.5,nist_800_53_SI.7,"> <!-- Rules for Linux systems --> <rule id="100200" level="7"> <if_sid>550</if_sid> <field name="file">/root</field> <description>File modified in /root directory.</description> </rule> <rule id="100201" level="7"> <if_sid>554</if_sid> <field name="file">/root</field> <description>File added to /root directory.</description> </rule> </group>
Add the following configuration to the
/var/ossec/etc/ossec.conffile at the Wazuh manager, replacingYOUR_VIRUS_TOTAL_API_KEYwith your own VirusTotal API key. This enables the Virustotal integration, triggering a VirusTotal query whenever any of rules ID100200and100201are tripped.<ossec_config> <integration> <name>virustotal</name> <api_key>YOUR_VIRUS_TOTAL_API_KEY</api_key> <!-- Replace with your VirusTotal API key --> <rule_id>100200,100201</rule_id> <alert_format>json</alert_format> </integration> </ossec_config>
If you have a premium VirusTotal API key, with high frequency of queries allowed, you can add more rules besides these two. You could also add to your rules more directories to monitor besides
/root.Create the
/var/ossec/active-response/bin/remove-threat.shactive response script at the CentOS 8 endpoint for the removal of a file from the system.#!/bin/bash LOCAL=`dirname $0`; cd $LOCAL cd ../ PWD=`pwd` read INPUT_JSON FILENAME=$(echo $INPUT_JSON | jq -r .parameters.alert.data.virustotal.source.file) COMMAND=$(echo $INPUT_JSON | jq -r .command) LOG_FILE="${PWD}/../logs/active-responses.log" #------------------------ Analyze command -------------------------# if [ ${COMMAND} = "add" ] then # Send control message to execd printf '{"version":1,"origin":{"name":"remove-threat","module":"active-response"},"command":"check_keys", "parameters":{"keys":[]}}\n' read RESPONSE COMMAND2=$(echo $RESPONSE | jq -r .command) if [ ${COMMAND2} != "continue" ] then echo "`date '+%Y/%m/%d %H:%M:%S'` $0: $INPUT_JSON Remove threat active response aborted" >> ${LOG_FILE} exit 0; fi fi # Removing file rm -f $FILENAME if [ $? -eq 0 ]; then echo "`date '+%Y/%m/%d %H:%M:%S'` $0: $INPUT_JSON Successfully removed threat" >> ${LOG_FILE} else echo "`date '+%Y/%m/%d %H:%M:%S'` $0: $INPUT_JSON Error removing threat" >> ${LOG_FILE} fi exit 0;
Change
/var/ossec/active-response/bin/remove-threat.showner and file permissions.# chmod 750 /var/ossec/active-response/bin/remove-threat.sh # chown root:ossec /var/ossec/active-response/bin/remove-threat.sh
Run
yum install jqif jq is missing. This allows theremove-threat.shscript to process the JSON input.Append the following blocks to
/var/ossec/etc/ossec.confat the Wazuh manager. This is to enable an active response and callremove-threat.shwhen VirusTotal query results for threats are positive matches.<ossec_config> <command> <name>remove-threat</name> <executable>remove-threat.sh</executable> <timeout_allowed>no</timeout_allowed> </command> <active-response> <disabled>no</disabled> <command>remove-threat</command> <location>local</location> <rules_id>87105</rules_id> </active-response> </ossec_config>
Edit
/var/ossec/etc/decoders/local_decoder.xmlat the Wazuh manager and add the following active response decoder configuration.<decoder name="ar_log_fields"> <parent>ar_log</parent> <regex offset="after_parent">^(\S+) Removed threat located at (\S+)</regex> <order>script_name, path</order> </decoder>
Add rules to the
/var/ossec/etc/rules/local_rules.xmlfile at the Wazuh manager to alert about the active response results.<group name="virustotal,"> <rule id="100092" level="12"> <if_sid>657</if_sid> <match>Successfully removed threat</match> <description>$(parameters.program) removed threat located at $(parameters.alert.data.virustotal.source.file)</description> </rule> <rule id="100093" level="12"> <if_sid>657</if_sid> <match>Error removing threat</match> <description>Error removing threat located at $(parameters.alert.data.virustotal.source.file)</description> </rule> </group>
Restart the Wazuh agent to apply local configuration changes.
# systemctl restart wazuh-agent
Restart Wazuh manager to apply the configuration changes.
# systemctl restart wazuh-manager
Steps to generate the alerts
Download a malicious file to
/rootdirectory. This triggers a VirusTotal query and generates an alert. In addition, the file will be automatically removed by the active response to this threat.# cd /root # curl -LO http://www.eicar.org/download/eicar.com && ls -lah eicar.com
Query the alerts
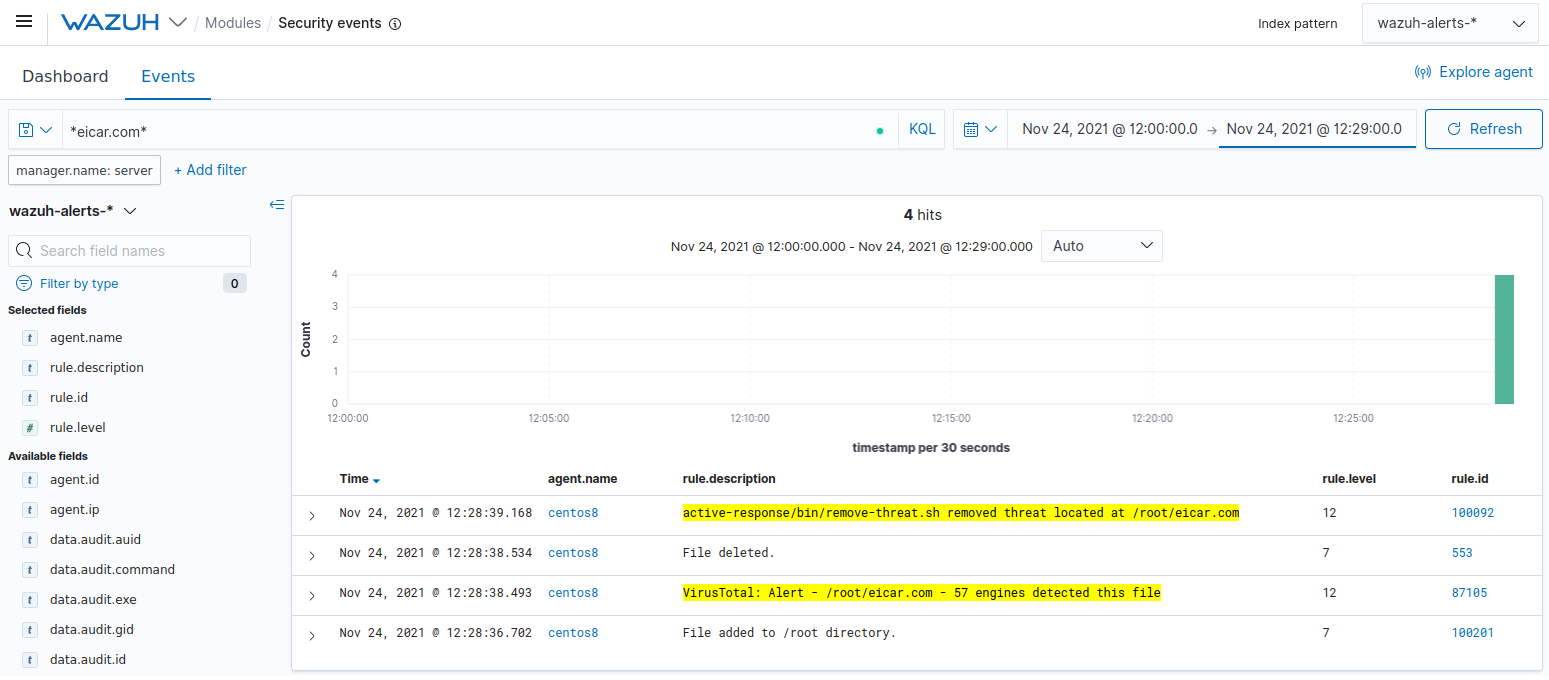
You can visualize the alert data in the Wazuh Kibana plugin. To do this, go to the Security events module and add the filters in the search bar to query the alerts.
*eicar.com*