Vulnerability Detector
Wazuh is able to detect vulnerabilities in the applications installed on the endpoints using the Vulnerability Detector module. This POC shows specifically how Wazuh helps to detect if installed applications have unpatched Common Vulnerabilities and Exposures (CVE) in the monitored system.
For more information on this capability, check the Vulnerability Detection section of the documentation.
Configuration
Configure your environment as follows to test the POC.
Enable the vulnerability detector wodle in the
/var/ossec/etc/ossec.conffile at the Wazuh manager.<ossec_config> <vulnerability-detector> <enabled>yes</enabled> <interval>5m</interval> <ignore_time>6h</ignore_time> <run_on_start>yes</run_on_start> <!-- Ubuntu OS vulnerabilities --> <provider name="canonical"> <enabled>yes</enabled> <os>trusty</os> <os>xenial</os> <os>bionic</os> <os>focal</os> <update_interval>1h</update_interval> </provider> <!-- Debian OS vulnerabilities --> <provider name="debian"> <enabled>yes</enabled> <os>stretch</os> <os>buster</os> <update_interval>1h</update_interval> </provider> <!-- RedHat OS vulnerabilities --> <provider name="redhat"> <enabled>yes</enabled> <os>5</os> <os>6</os> <os>7</os> <os>8</os> <os allow="Centos Linux-8">8</os> <update_interval>1h</update_interval> </provider> <!-- Windows OS vulnerabilities --> <provider name="msu"> <enabled>yes</enabled> <update_interval>1h</update_interval> </provider> <!-- Aggregate vulnerabilities --> <provider name="nvd"> <enabled>yes</enabled> <update_from_year>2010</update_from_year> <update_interval>1h</update_interval> </provider> </vulnerability-detector> </ossec_config>
Enable
hotfixesandpackagescollection in the syscollector component. This is done in the Wazuh agent configuration file/var/ossec/etc/ossec.confat the monitored Windows endpoint.<wodle name="syscollector"> <disabled>no</disabled> <interval>1h</interval> <scan_on_start>yes</scan_on_start> <hardware>yes</hardware> <os>yes</os> <network>yes</network> <packages>yes</packages> <hotfixes>yes</hotfixes> <ports all="no">yes</ports> <processes>yes</processes> </wodle>
Enable software
packagescollection in the syscollector component of the Wazuh agent configuration file/var/ossec/etc/ossec.confat the monitored CentOS 8 endpoint.<wodle name="syscollector"> <disabled>no</disabled> <interval>1h</interval> <scan_on_start>yes</scan_on_start> <hardware>yes</hardware> <os>yes</os> <network>yes</network> <packages>yes</packages> <ports all="no">yes</ports> <processes>yes</processes> </wodle>
Steps to generate the alerts
No action is required. A CVE database is created in /var/ossec/queue/vulnerabilities/cve.db at the Wazuh manager. Vulnerability scans are performed periodically on the applications for each monitored endpoint.
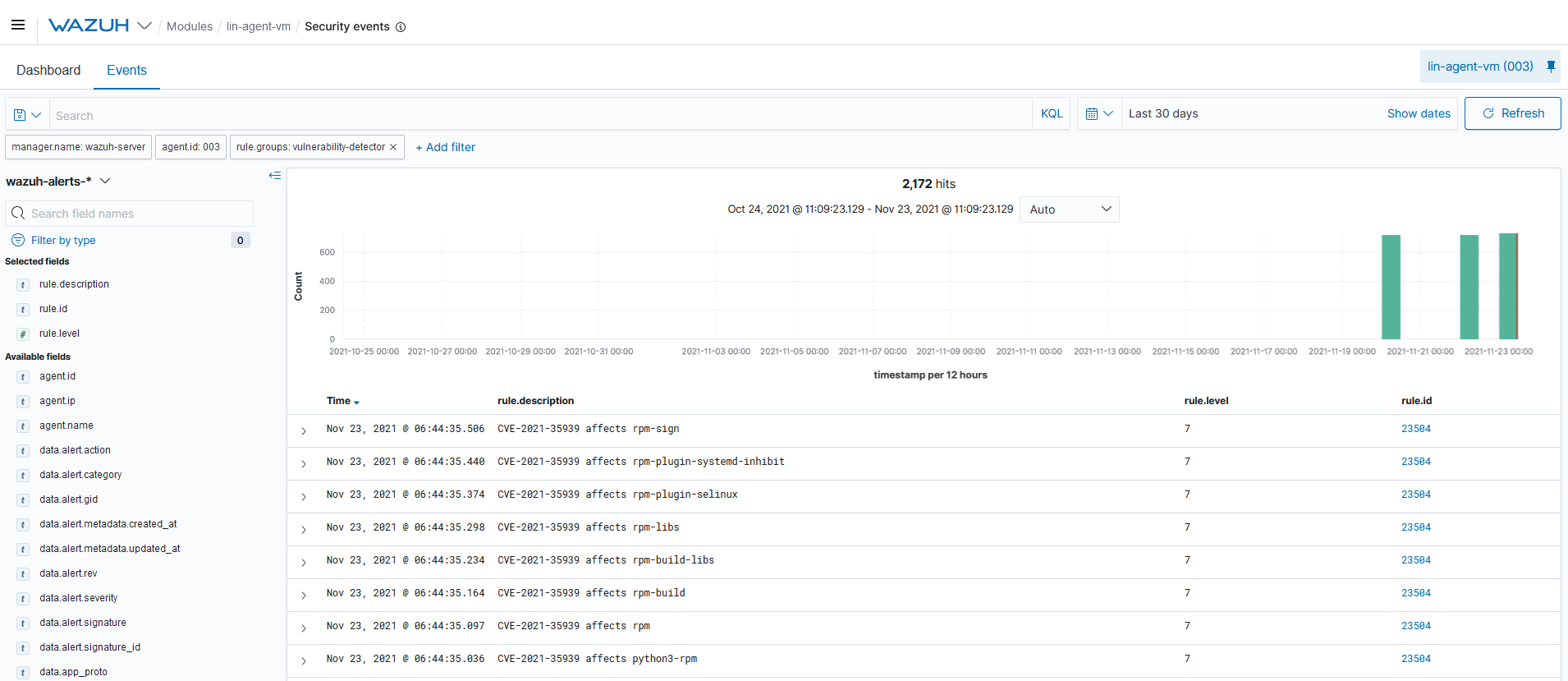
Query the alerts
You can visualize the alert data in the Wazuh Kibana plugin. To do this, go to the Security events module and add the filters in the search bar to query the alerts.
rule.groups:vulnerability-detector