AWS Config
AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. With Config, you can review changes in configurations and relationships between AWS resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines. This enables you to simplify compliance auditing, security analysis, change management, and operational troubleshooting.
Amazon configuration
On the AWS Config page, go to Settings.
Here, choose the Resource types to record (specify the AWS resource types you want AWS Config to record):
All resources
Specific types
Note
For more information about these options, see Selecting Which Resources AWS Config Records.
Select an existing S3 Bucket or create a new one.
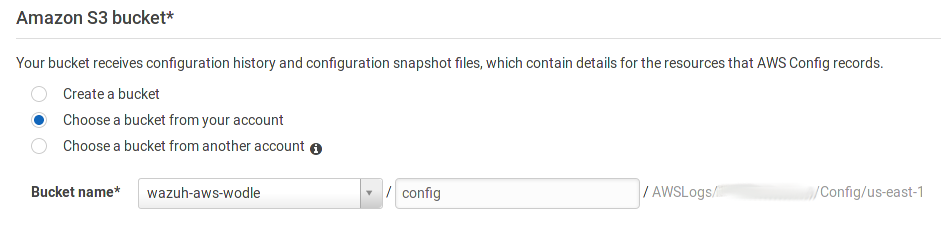
After these steps, it is necessary to configure the rules.
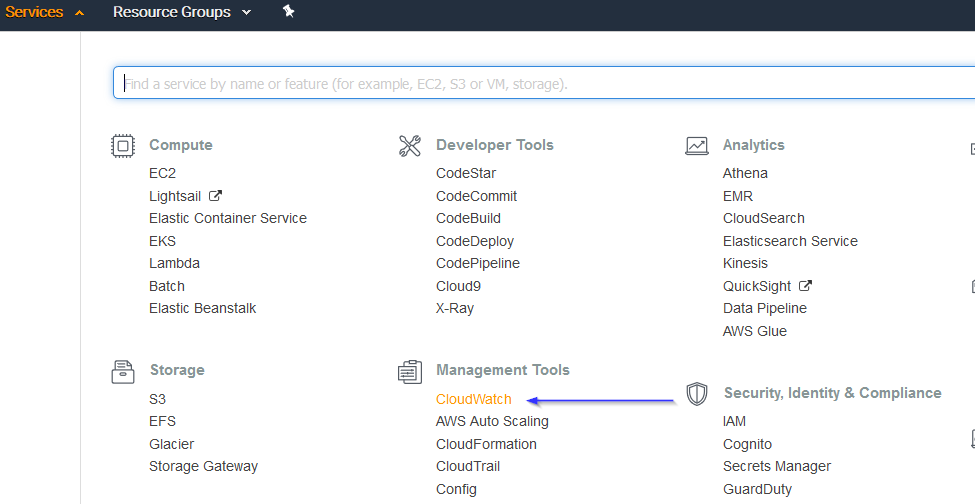
Go to Services > Management Tools > CloudWatch:
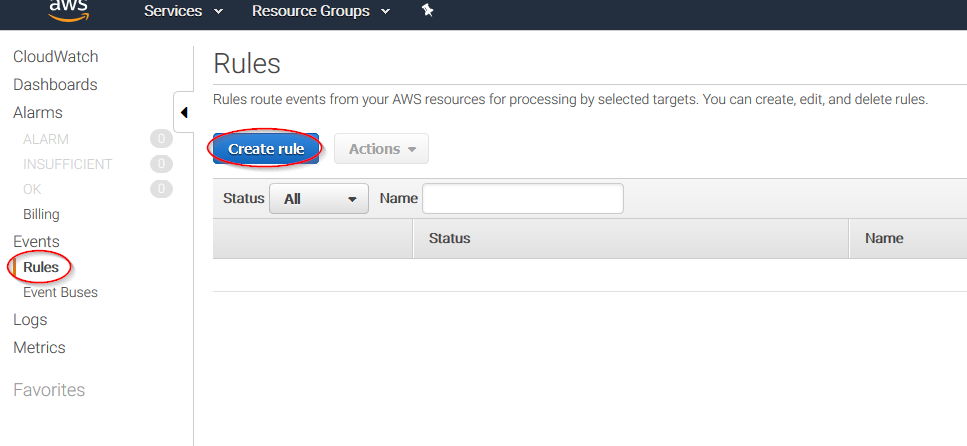
Select Rules on the left menu and click on the Create rule button:
Select the services you want to get logs from using the Service name slider, then, click on the Add target button and add the previously created Firehose delivery stream there. Also, create a new role to access the delivery stream:
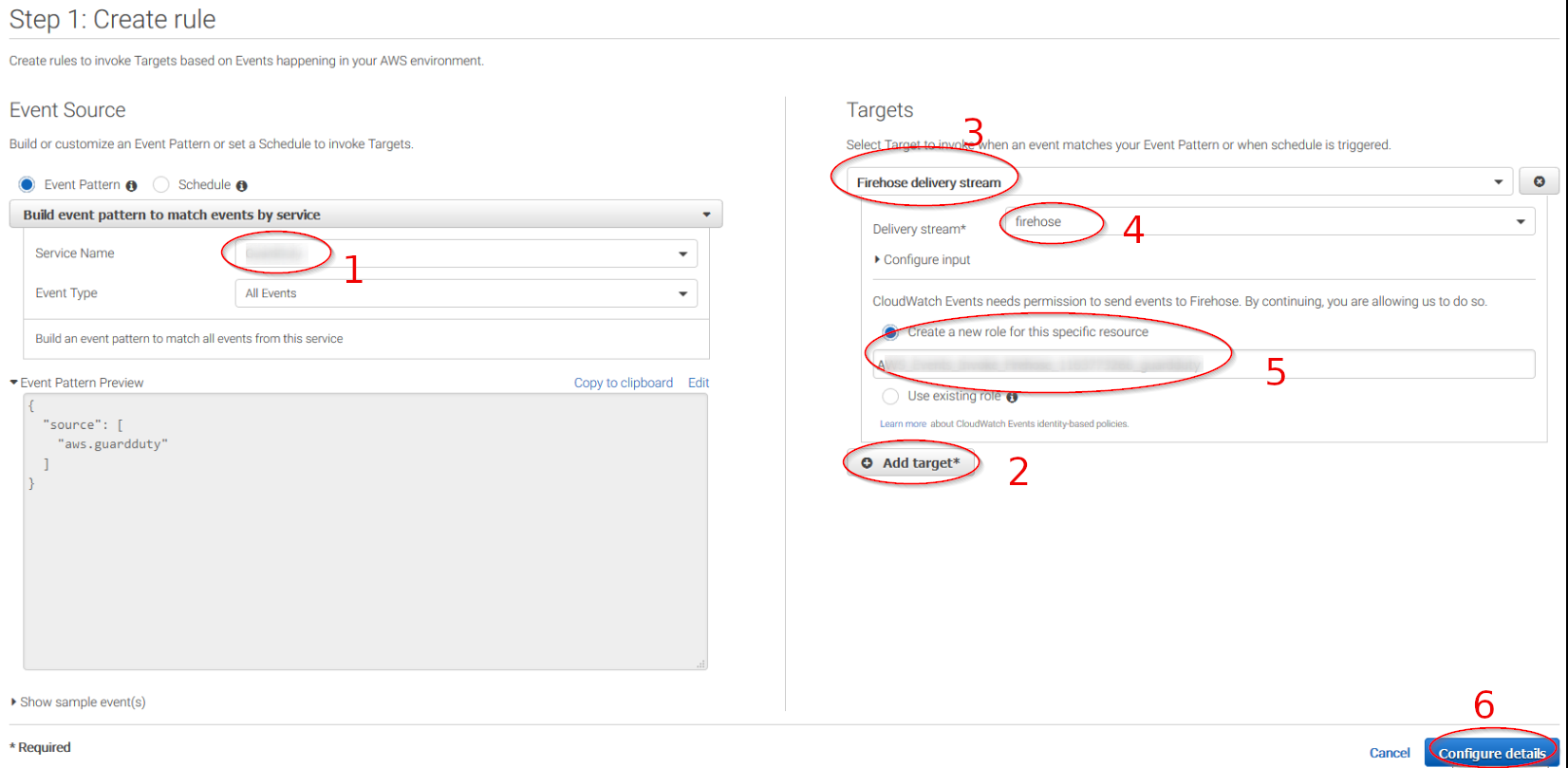
Give the rule some name and click on the Create rule button:
Once the rule is created, data will start to be sent to the previously created S3 bucket. Remember to first enable the service you want to monitor, otherwise, you won't get any data.
Policy configuration
To create a policy using the Amazon Web Services console, follow the AWS documentation.
Take into account that the policies below follow the principle of least privilege to ensure that only the minimum permissions are provided to the Wazuh user.
To allow an AWS user to use the module with read-only permissions, it must have a policy like the following attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::bucket-name/*",
"arn:aws:s3:::bucket-name"
]
}
]
}
If it is necessary to delete the log files once they have been collected, the associated policy would be as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::bucket-name/*",
"arn:aws:s3:::bucket-name"
]
}
]
}
Once a policy has been created, there are different methods available to attach it to a user, such as attaching it directly or to a group to which the user belongs. More information on how to perform those tasks on the AWS documentation.
Wazuh configuration
Open the Wazuh configuration file (
/var/ossec/etc/ossec.conf) and add the following block:<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>yes</run_on_start> <skip_on_error>yes</skip_on_error> <bucket type="config"> <name>wazuh-aws-wodle</name> <path>config</path> <aws_profile>default</aws_profile> </bucket> </wodle>
Note
Check the AWS S3 module reference manual to learn more about each setting.
Restart Wazuh in order to apply the changes:
If you're configuring a Wazuh manager:
# systemctl restart wazuh-manager
# service wazuh-manager restart
If you're configuring a Wazuh agent:
# systemctl restart wazuh-agent
# service wazuh-agent restart