Vulnerability detection
Vulnerable software applications are commonly targeted by attackers to compromise endpoints and gain a persistent presence on targeted networks. Relying on its software inventory capabilities, the Wazuh platform maintains an up-to-date list of all applications installed on the endpoints where the Wazuh agent is located.
In addition, Wazuh identifies vulnerable applications and produces risk reports by correlating that list with the National Vulnerability Database (NVD) and with information collected from different operating system vendors. To detect vulnerable software, Wazuh uses a database of Common Vulnerabilities and Exposures (CVE) created automatically by processing data pulled from the following sources:
In order to enable vulnerability detection, users need to configure the Wazuh agent to collect software inventory data and the Wazuh server to pull CVE information from the different vulnerability feeds.
See below an example of a vulnerability detection alert:
{
"agent": {
"id": "003",
"ip": "10.0.1.102",
"name": "Windows"
},
"location": "vulnerability-detector",
"data": {
"vulnerability": {
"assigner": "cve@mitre.org",
"cve": "CVE-2020-12395",
"cve_version": "4.0",
"cvss": {
"cvss2": {
"base_score": "10",
"vector": {
"access_complexity": "low",
"attack_vector": "network",
"authentication": "none",
"availability": "complete",
"confidentiality_impact": "complete",
"integrity_impact": "complete"
}
}
},
"cwe_reference": "CWE-119",
"package": {
"architecture": "x86_64",
"condition": "less than 68.8.0",
"generated_cpe": "a:mozilla:thunderbird:68.0::::::x86_64:",
"name": "Mozilla Thunderbird 68.0 (x64 en-US)",
"version": "68.0"
},
"published": "2020-05-26",
"references": [ "https://bugzilla.mozilla.org/buglist.cgi?bug_id=1595886%2C1611482%2C1614704%2C1624098%2C1625749%2C1626382%2C1628076%2C1631508",
"https://security.gentoo.org/glsa/202005-03",
"https://security.gentoo.org/glsa/202005-04",
"https://usn.ubuntu.com/4373-1/",
"https://www.mozilla.org/security/advisories/mfsa2020-16/",
"https://www.mozilla.org/security/advisories/mfsa2020-17/",
"https://www.mozilla.org/security/advisories/mfsa2020-18/",
"https://nvd.nist.gov/vuln/detail/CVE-2020-12395"
],
"severity": "High",
"title": "Mozilla developers and community members reported memory safety bugs present in Firefox 75 and Firefox ESR 68.7. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code. This vulnerability affects Firefox ESR < 68.8, Firefox < 76, and Thunderbird < 68.8.0.",
"updated": "2020-06-12"
}
},
"rule": {
"description": "CVE-2020-12395 affects Mozilla Thunderbird 68.0 (x64 en-US)",
"id": "23505",
"level": 10
},
"timestamp": "2020-07-20T00:41:36.302+0000"
}
Vulnerability detection dashboard:
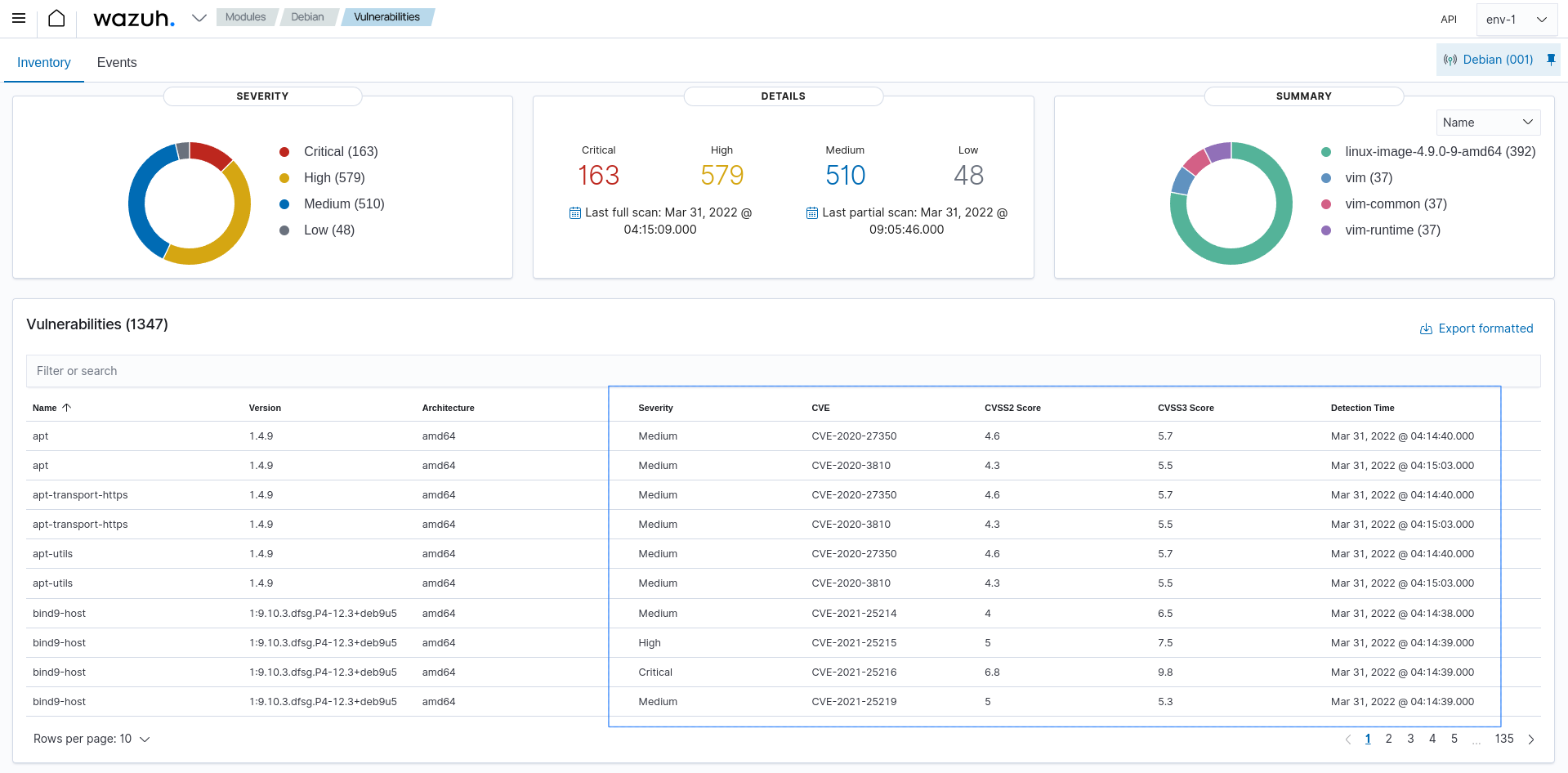
You can find more information on how Wazuh detects software vulnerabilities in the user manual.