Malware detection
Wazuh offers several capabilities that support malware detection. These detections can be done by:
These malware detection components help meet the following PCI DSS requirement:
Requirement 5 - Protect All Systems and Networks from Malicious Software: Malicious software (malware) is software or firmware designed to infiltrate or damage a computer system without the owner's knowledge or consent, with the intent of compromising the confidentiality, integrity, or availability of the owner’s data, applications, or operating system. The goal of this requirement is to protect systems from current and evolving malware threats.
To help meet the above PCI DSS requirement, Wazuh uses a combination of rootcheck, CDB lists, integrations with VirusTotal and Yara, and active response to detect and remove malicious files.
Use cases
PCI DSS 5.2.2 requires that the deployed anti-malware solution(s):
Detects all known types of malware.
Removes, blocks, or contains all known types of malware.
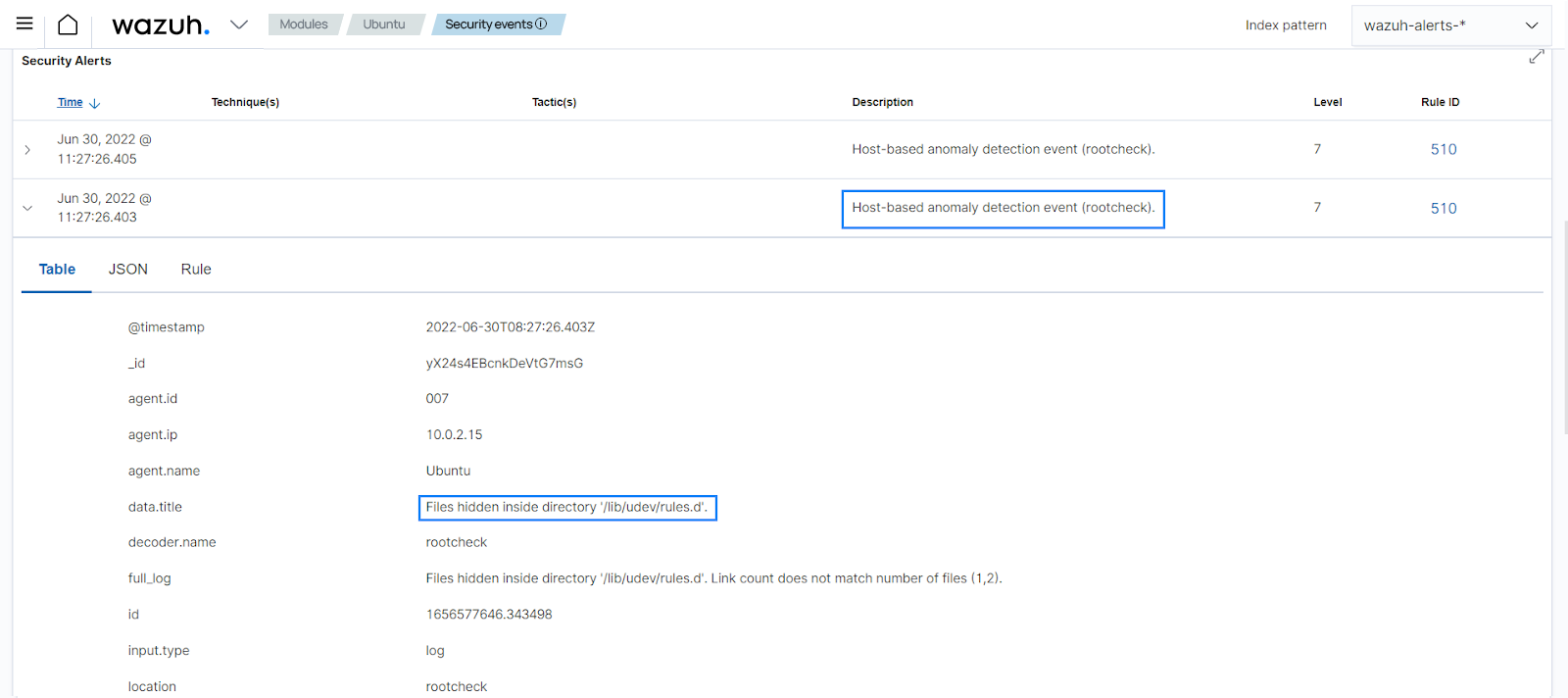
Detecting a rootkit is a sample case for malware detection. The rootcheck module runs several tests to detect rootkits. One of them checks for files hidden in
/dev. The/devdirectory should only contain device-specific files such as the primary IDE hard disk (/dev/hda), and the kernel random number generators (/dev/randomand/dev/urandom), among others. Any additional files, beyond the expected device-specific files, needs inspection. Many rootkits use/devas a storage partition to hide files.In the following example we have a rootkit on the endpoint that creates hidden files in
/lib/udev/rules.d. When the rootcheck scan is run, an alert is generated detecting the hidden files.