Detecting account manipulation
Account manipulation refers to the creation, modification, or deletion of user accounts or other credentials within an organization's IT infrastructure. Monitoring this activity is critical to the cybersecurity of an organization. Unauthorized account manipulations might grant an attacker access to sensitive systems and data.
To maintain persistence on a victim endpoint, adversaries can alter the SSH authorized_keys file in Linux. The .ssh directory within a user home directory holds this file. For example, for a user named smith, you can find the authorized_keys file located at /home/smith/.ssh/authorized_keys. This file defines the public keys this user uses to login into some of their accounts. Each line in the file represents a single public key.
You can configure the Wazuh FIM module to monitor the authorized_keys file. This triggers an alert whenever a user or process modifies the public keys in the file. Detecting the modification of the SSH keys allows you to take action before a system compromise occurs.
Use case description
Endpoint
Description
Ubuntu 20.04
The FIM module detects SSH key modification on this endpoint.
Configuration
Perform the following steps to configure the FIM module to monitor SSH key modification.
Edit the
/var/ossec/etc/ossec.confconfiguration file and addauthorized_keysfor monitoring:<syscheck> <directories whodata="yes">/home/*/.ssh/authorized_keys</directories> </syscheck>
Restart the Wazuh agent to apply the configuration:
systemctl restart wazuh-agent
Test the configuration
Generate an SSH key-pair for user authentication and save it as
.ssh/test_keyusing the following command:ssh-keygen -f .ssh/test_keyRun the following command to copy the content of the generated SSH public key
test_key.puband add it to theauthorized_keysfile in the target Ubuntu user.sshdirectory:cat ~/.ssh/test_key.pub | ssh <UBUNTU_USER>@<UBUNTU_IP> "sudo tee -a /home/<UBUNTU_USER>/.ssh/authorized_keys"
Replace <UBUNTU_USER> and <UBUNTU_IP> with the user and IP address for your Ubuntu endpoint respectively.
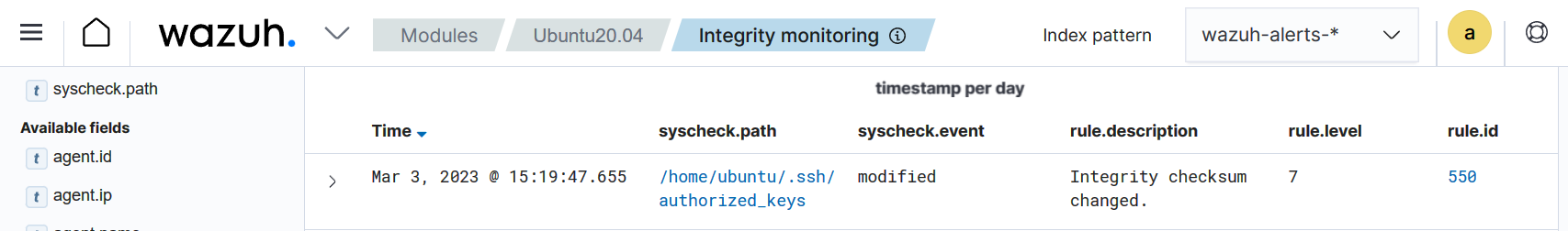
Visualize the alert
Navigate to Modules > Integrity monitoring on the Wazuh dashboard to view the alert generated when the FIM module detects changes to the authorized_keys file.