Amazon Virtual Private Cloud (VPC)
Amazon Virtual Private Cloud (Amazon VPC) lets users provision a logically isolated section of the AWS Cloud where they can launch AWS resources in a virtual network that they define. Users have complete control over their virtual networking environment, including the selection of their own IP address range, creation of subnets, and configuration of route tables and network gateways. Users can use both IPv4 and IPv6 in their VPC for secure and easy access to resources and applications.
Amazon configuration
Select an existing S3 Bucket or create a new one.
Go to Services > Compute > EC2:
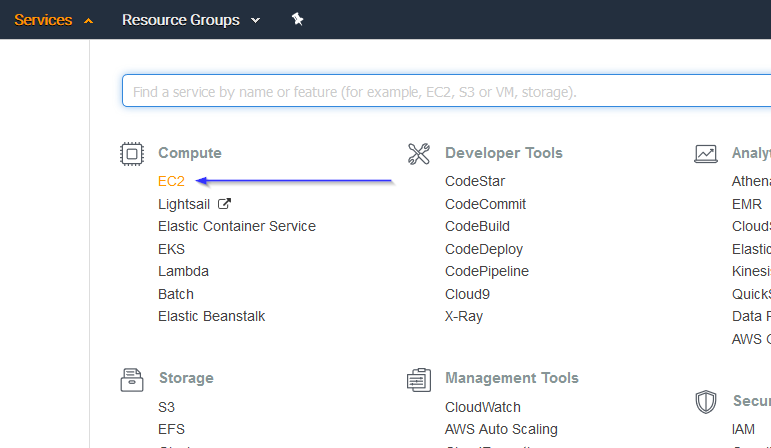
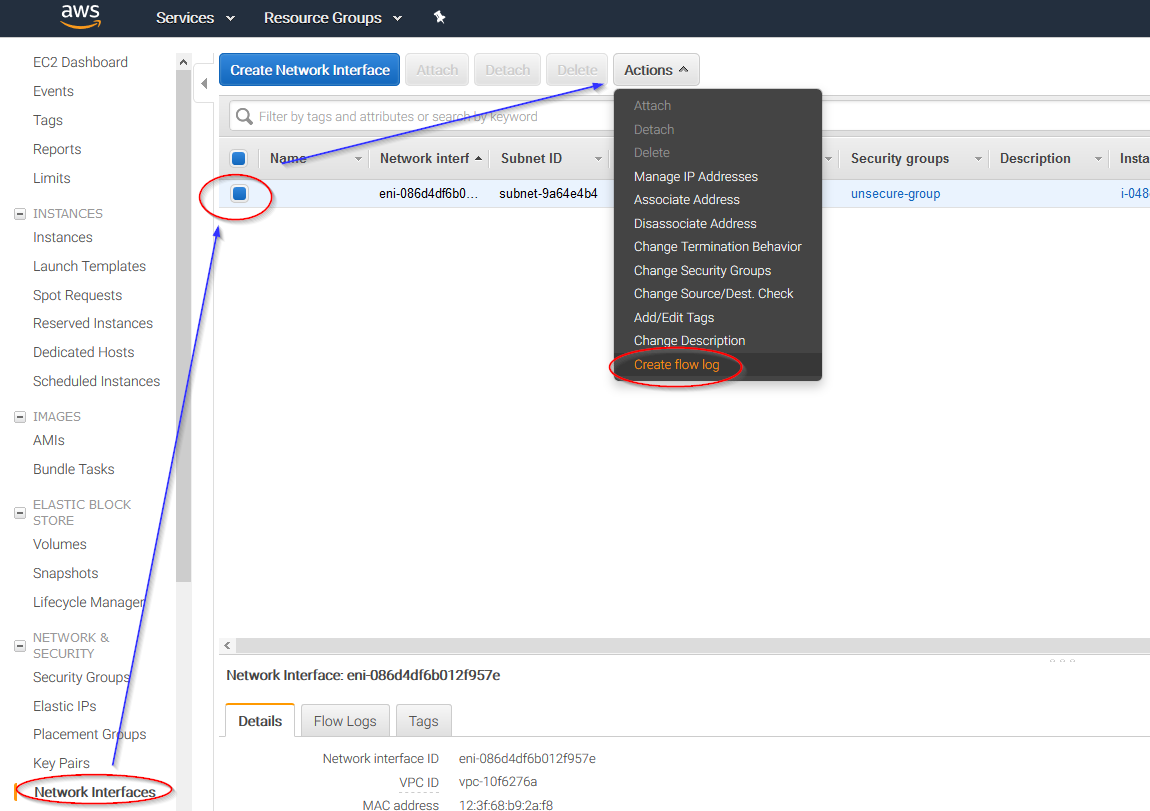
Go to Network & Security > Network Interfaces on the left menu. Select a network interface and select Create a flow log on the Actions menu:
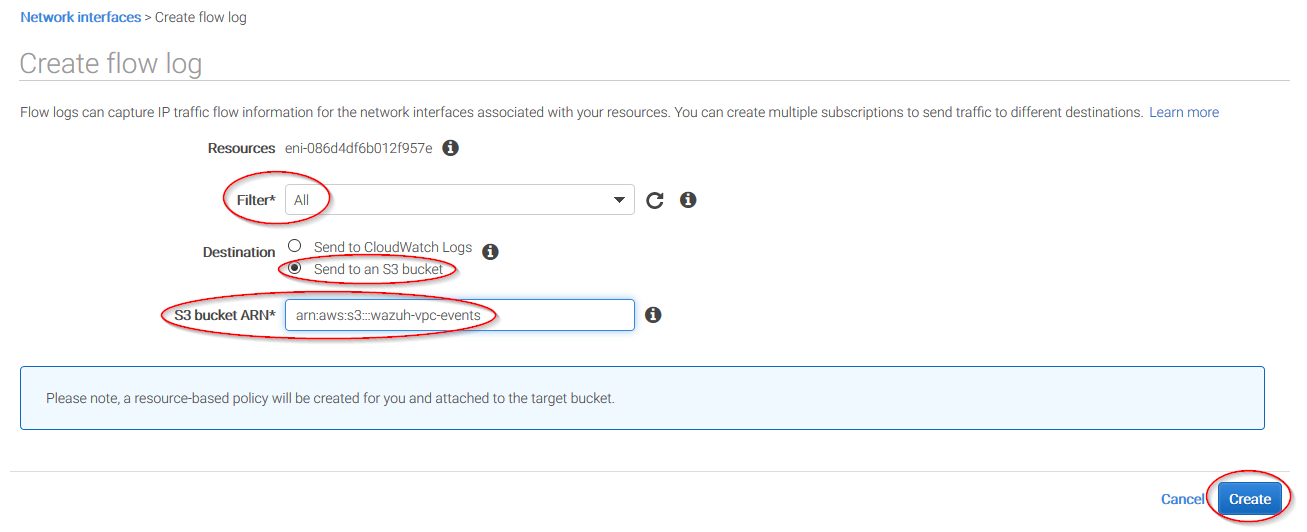
Change all fields to look like the following screenshot and paste the ARN of the previously created bucket:
Policy configuration
To create a policy using the Amazon Web Services console, follow the AWS documentation.
Take into account that the policies below follow the principle of least privilege to ensure that only the minimum permissions are provided to the Wazuh user.
To allow an AWS user to use the module with read-only permissions, it must have a policy like the following attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::bucket-name/*",
"arn:aws:s3:::bucket-name"
]
}
]
}
If it is necessary to delete the log files once they have been collected, the associated policy would be as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::bucket-name/*",
"arn:aws:s3:::bucket-name"
]
}
]
}
Once a policy has been created, there are different methods available to attach it to a user, such as attaching it directly or to a group to which the user belongs. More information on how to perform those tasks on the AWS documentation.
To allow an AWS user to execute the VPC integration, it must also have a policy like the following attached:
{ "Sid": "VisualEditor0", "Effect": "Allow", "Action": "ec2:DescribeFlowLogs", "Resource": "*" }
Wazuh configuration
Open the Wazuh configuration file (
/var/ossec/etc/ossec.conf) and add the following block:<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>yes</run_on_start> <skip_on_error>yes</skip_on_error> <bucket type="vpcflow"> <name>wazuh-aws-wodle</name> <aws_profile>default</aws_profile> </bucket> </wodle>
Note
Check the AWS S3 module reference manual to learn more about each setting.
Restart Wazuh in order to apply the changes:
If you're configuring a Wazuh manager:
# systemctl restart wazuh-manager
# service wazuh-manager restart
If you're configuring a Wazuh agent:
# systemctl restart wazuh-agent
# service wazuh-agent restart
Use cases
Using an Amazon VPC (Virtual Private Cloud), users can logically isolate some of their AWS assets from the rest of their cloud infrastructure. Users can actually set up their own networks in the cloud. This is why it is usually important to monitor changes to their VPCs.
Create a VPC
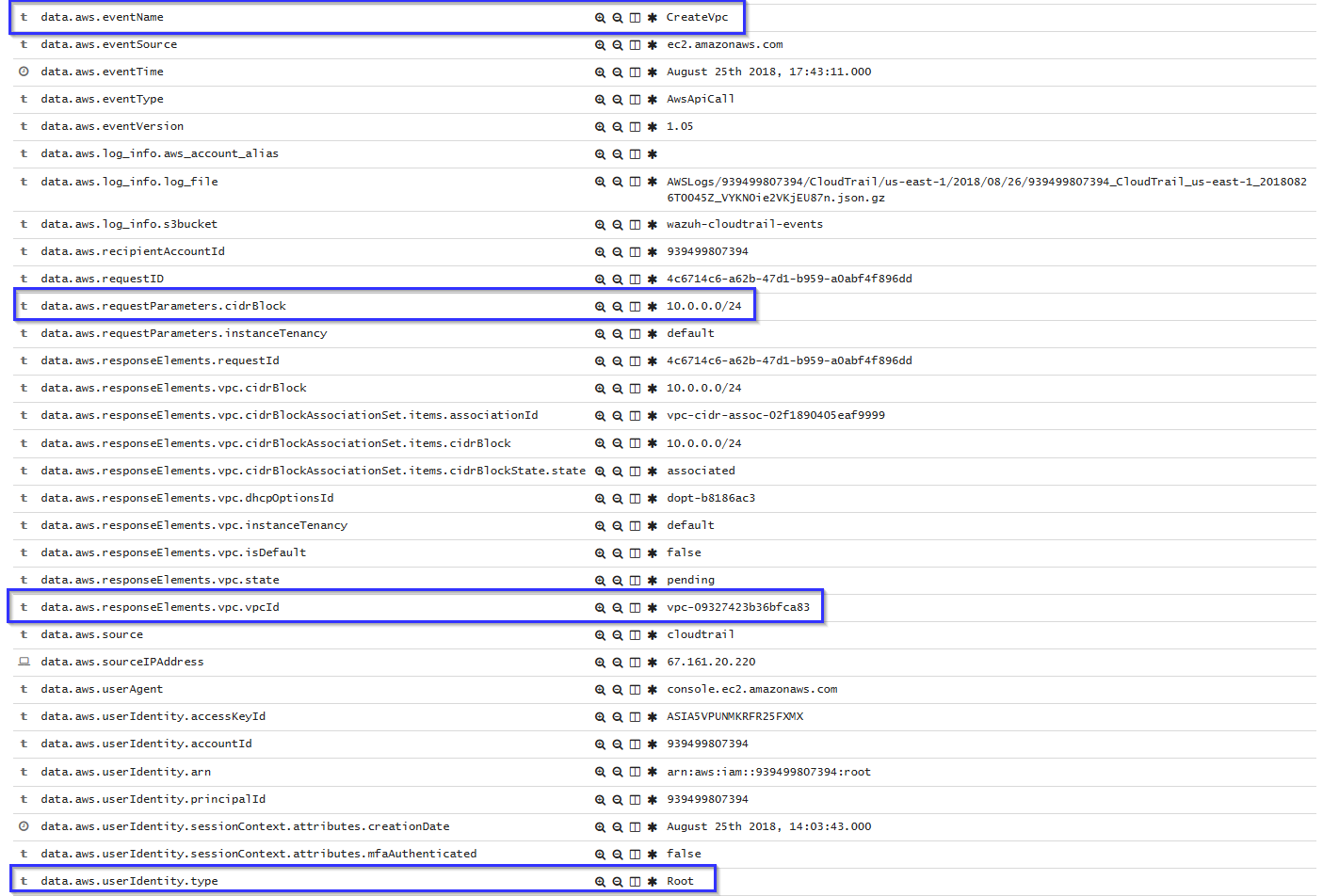
If a VPC is created, the following alert will be shown on Kibana:
If a user without proper permissions attempts to create a VPC, the following alert will be shown on Kibana:
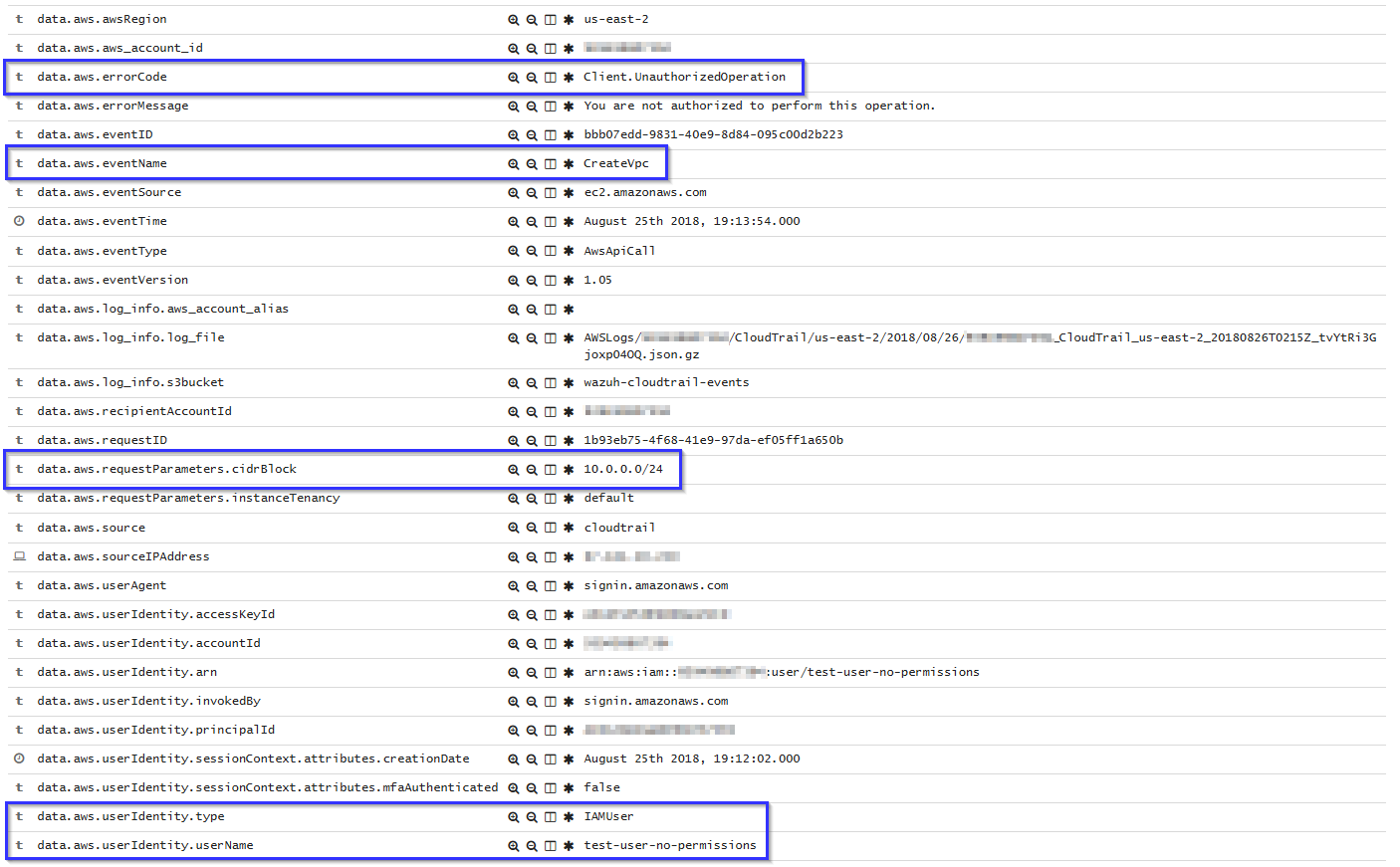
Working with VPC Data
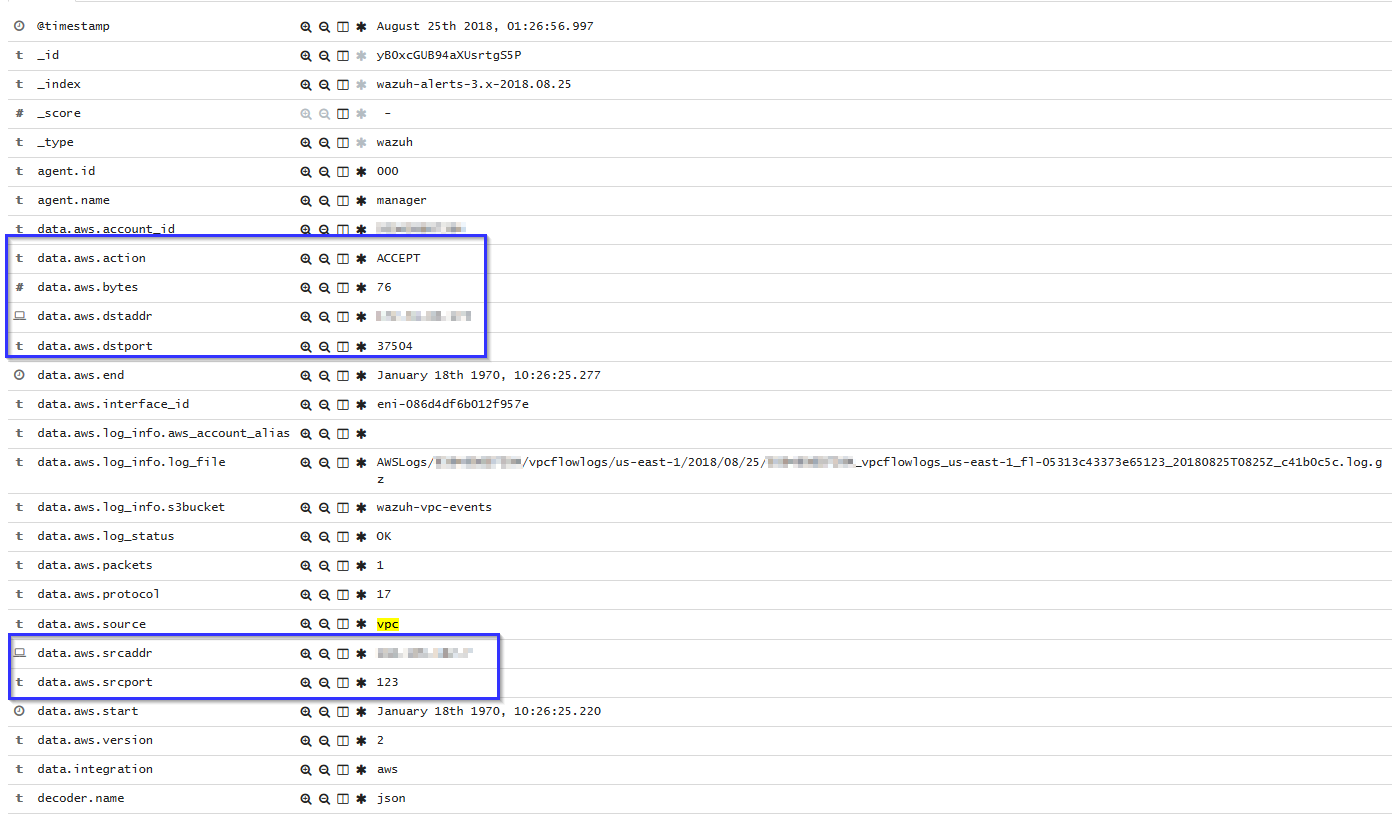
A VPC alert contains data such as dest and source IP address, dst and source port, and how many bytes were sent:
These alerts can be easily analyzed using visualizations like the following one:
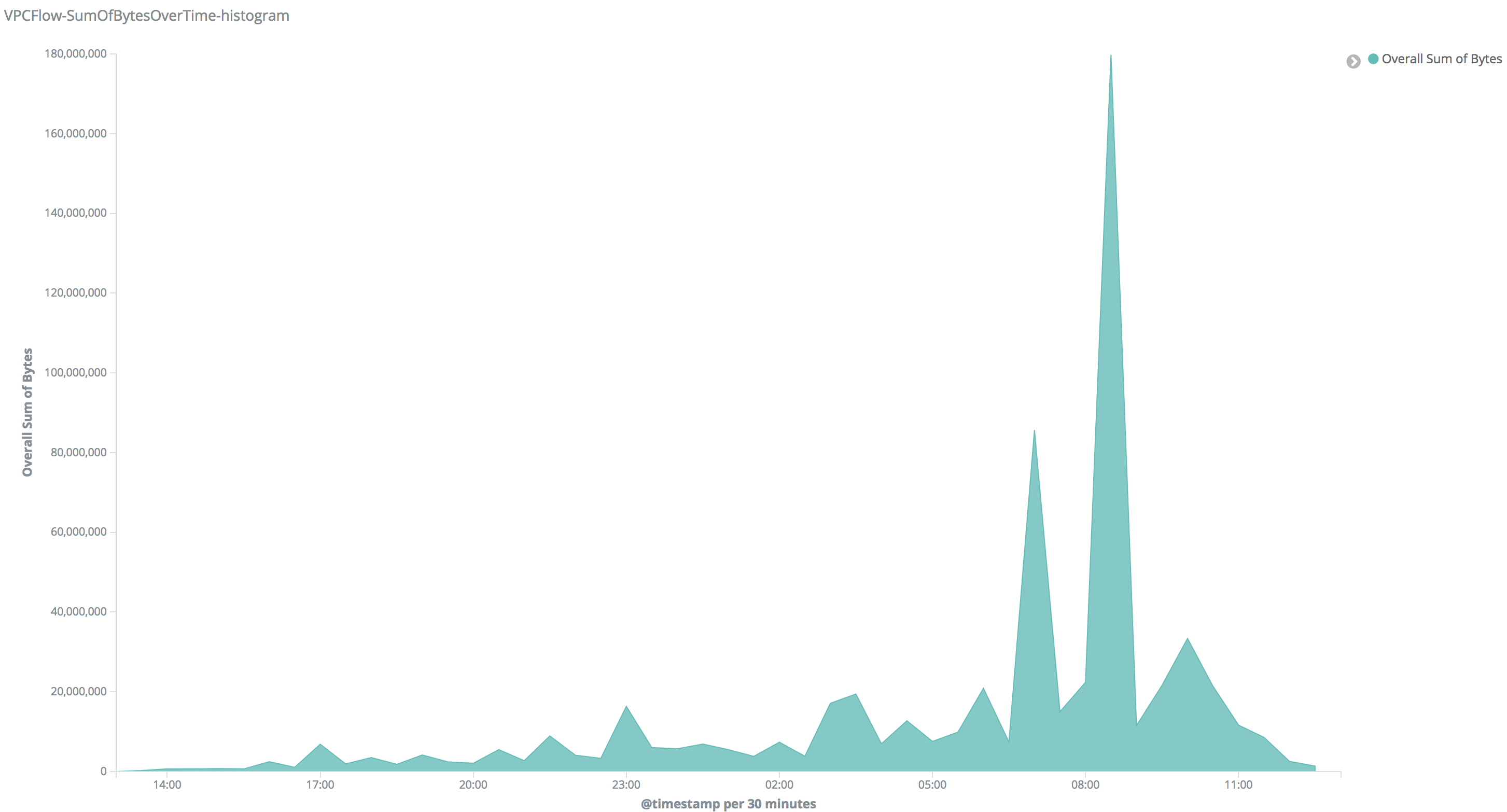
On that visualization users can look for peaks in their network, once they found a peak they can filter, the alerts generated on that time and check which IP addresses were communicating. Since IP address is a field used in many AWS alerts, they'll probably found other alerts and find out what happened.