Vulnerability detection
The Wazuh Vulnerability Detector module performs a software audit. It identifies vulnerabilities in the operating system and installed applications in monitored endpoints. The module builds a global vulnerability database from vulnerability feeds indexed by Canonical, Debian, Red Hat, Arch Linux, ALAS (Amazon Linux Advisories Security), Microsoft, and the National Vulnerability Database. Then it cross-correlates these feeds with data from the endpoint application inventory.
The Vulnerability Detector module helps to implement the following NIST 800-53 controls:
RA-5 Vulnerability monitoring and scanning: “Vulnerability monitoring includes scanning for patch levels; scanning for functions, ports, protocols, and services that should not be accessible to users or devices; and scanning for flow control mechanisms that are improperly configured or operating incorrectly. Vulnerability monitoring may also include continuous vulnerability monitoring tools that use instrumentation to continuously analyze components. Instrumentation-based tools may improve accuracy and may be run throughout an organization without scanning. Vulnerability monitoring tools that facilitate interoperability include tools that are Security Content Automation Protocol (SCAP)-validated. Thus, organizations consider using scanning tools that express vulnerabilities in the Common Vulnerabilities and Exposures (CVE) naming convention and that employ the Open Vulnerability Assessment Language (OVAL) to determine the presence of vulnerabilities. Sources for vulnerability information include the Common Weakness Enumeration (CWE) listing and the National Vulnerability Database (NVD). Control assessments, such as red team exercises, provide additional sources of potential vulnerabilities for which to scan. Organizations also consider using scanning tools that express vulnerability impact by the Common Vulnerability Scoring System (CVSS).”
SC-38 Operations security: “Operations security (OPSEC) is a systematic process by which potential adversaries can be denied information about the capabilities and intentions of organizations by identifying, controlling, and protecting generally unclassified information that specifically relates to the planning and execution of sensitive organizational activities. The OPSEC process involves five steps: identification of critical information, analysis of threats, analysis of vulnerabilities, assessment of risks, and the application of appropriate countermeasures. OPSEC controls are applied to organizational systems and the environments in which those systems operate. OPSEC controls protect the confidentiality of information, including limiting the sharing of information with suppliers, potential suppliers, and other non-organizational elements and individuals. Information critical to organizational mission and business functions includes user identities, element uses, suppliers, supply chain processes, functional requirements, security requirements, system design specifications, testing and evaluation protocols, and security control implementation details.”
The Wazuh Vulnerability Detector module assists with the above requirements by scanning an endpoint for vulnerable applications/packages and missing OS updates.
Use case: Detect vulnerabilities on a Windows endpoint
This use case shows how Wazuh helps meet the NIST RA-5 Vulnerability monitoring and scanning requirement using the Vulnerability detection module to identify system vulnerabilities.
In this use case, you configure the Wazuh Vulnerability detector module to perform a vulnerability scan on a monitored Windows 10 endpoint. The Vulnerabilities tab of the Wazuh dashboard shows the result of the scan.
Follow the steps below to activate the Wazuh Vulnerability Detector module:
Windows endpoint
Check that the following highlighted options are within the
syscollectorwodle block of the/var/ossec/etc/ossec.conffile of your Wazuh agent:<!-- System inventory --> <wodle name="syscollector"> <disabled>no</disabled> <interval>1h</interval> <scan_on_start>yes</scan_on_start> <hardware>yes</hardware> <os>yes</os> <network>yes</network> <packages>yes</packages> <ports all="no">yes</ports> <processes>yes</processes> <!-- Database synchronization settings --> <synchronization> <max_eps>10</max_eps> </synchronization> </wodle>
Wazuh server
Edit the
<vulnerability-detector>block within the/var/ossec/etc/ossec.conffile and set<enabled>toyes. This enables the vulnerability detector module.<vulnerability-detector> <enabled>yes</enabled> <interval>5m</interval> <min_full_scan_interval>6h</min_full_scan_interval> <run_on_start>yes</run_on_start> </vulnerability-detector>
You can also set other options such as <interval> and <run_on_start>.
Enable the
<provider>options formsuandnvdin the<vulnerability-detector>block of the/var/ossec/etc/ossec.confconfiguration file:<!-- Windows OS vulnerabilities --> <provider name="msu"> <enabled>yes</enabled> <update_interval>1h</update_interval> </provider> <!-- Aggregate vulnerabilities --> <provider name="nvd"> <enabled>yes</enabled> <update_from_year>2010</update_from_year> <update_interval>1h</update_interval> </provider>
Save the changes:
msu: Pulls CVEs from the Microsoft vulnerability updates database.nvd: Pulls CVEs from the National Vulnerability Database.
Restart the Wazuh server to apply the configuration changes:
# systemctl restart wazuh-manager
# service wazuh-manager restart
Go to Modules > Vulnerabilities on the Wazuh dashboard. Select the Windows agent to find vulnerable applications and packages.
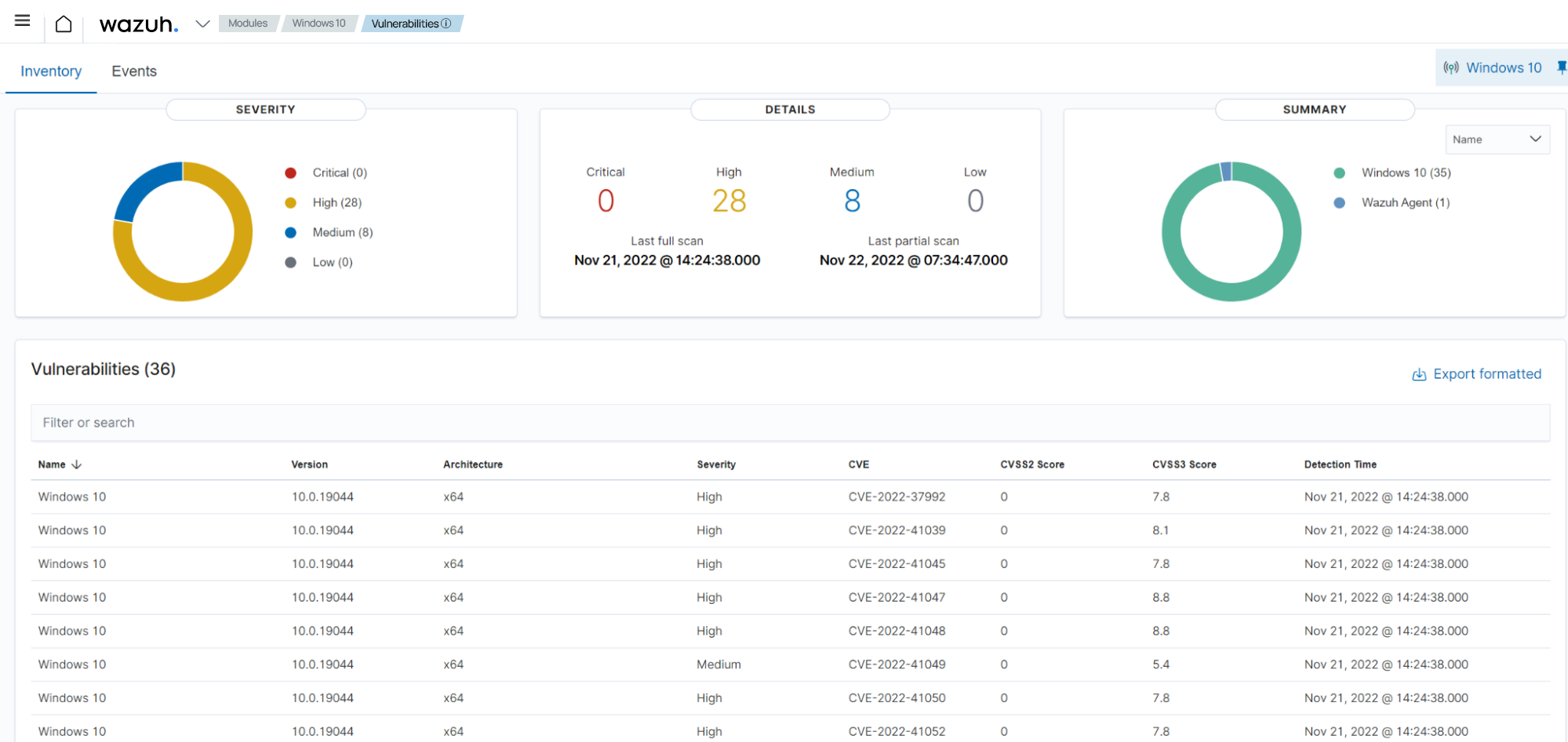
The alert details include the detection time, CVE number, and severity, amongst other information.