Malware detection
Malware, short for malicious software, refers to any software specifically designed to harm or exploit computer systems, networks, or users. It is created with the intention of gaining unauthorized access, causing damage, stealing sensitive information, or performing other malicious activities on a target system. There are various types of malware, each with specific functions and infection methods. Some common types of malware include viruses, worms, ransomware, botnets, spyware, trojans, and rootkits.
Malware detection is crucial for safeguarding computer systems and networks from cyber threats. It helps identify and mitigate malicious software that can cause a data breach, system compromise, and financial loss.
Wazuh for malware detection
Traditional methods, which rely solely on signature-based detections, have limitations and fail to capture new threats. Signature-based approaches struggle with detecting zero-day attacks, polymorphic malware, and other evasion techniques employed by threat actors. As a result, organizations are at risk of undetected breaches and data exfiltration. Wazuh empowers organizations to detect and respond to sophisticated and evasive threats effectively. Wazuh encompasses different modules that identify malware properties, activities, network connections, and more.
Detecting malicious activities with threat detection rules
Wazuh has threat detection rules that enable behavior-based malware detection. Instead of relying solely on predefined signatures, Wazuh focuses on monitoring and analyzing abnormal behavior exhibited by malware. This allows Wazuh to detect known and previously unknown threats. This way, Wazuh provides a proactive and adaptable defense against cyber threats.
Wazuh has out-of-the-box rulesets that are specifically designed to trigger alerts for recognized malware patterns, providing a quick response to potential security incidents. For example, the image below shows an alert with rule ID 92213 triggered when an executable is dropped in a folder commonly used by malware. This alert prompts security teams to begin the investigation and remediation process.
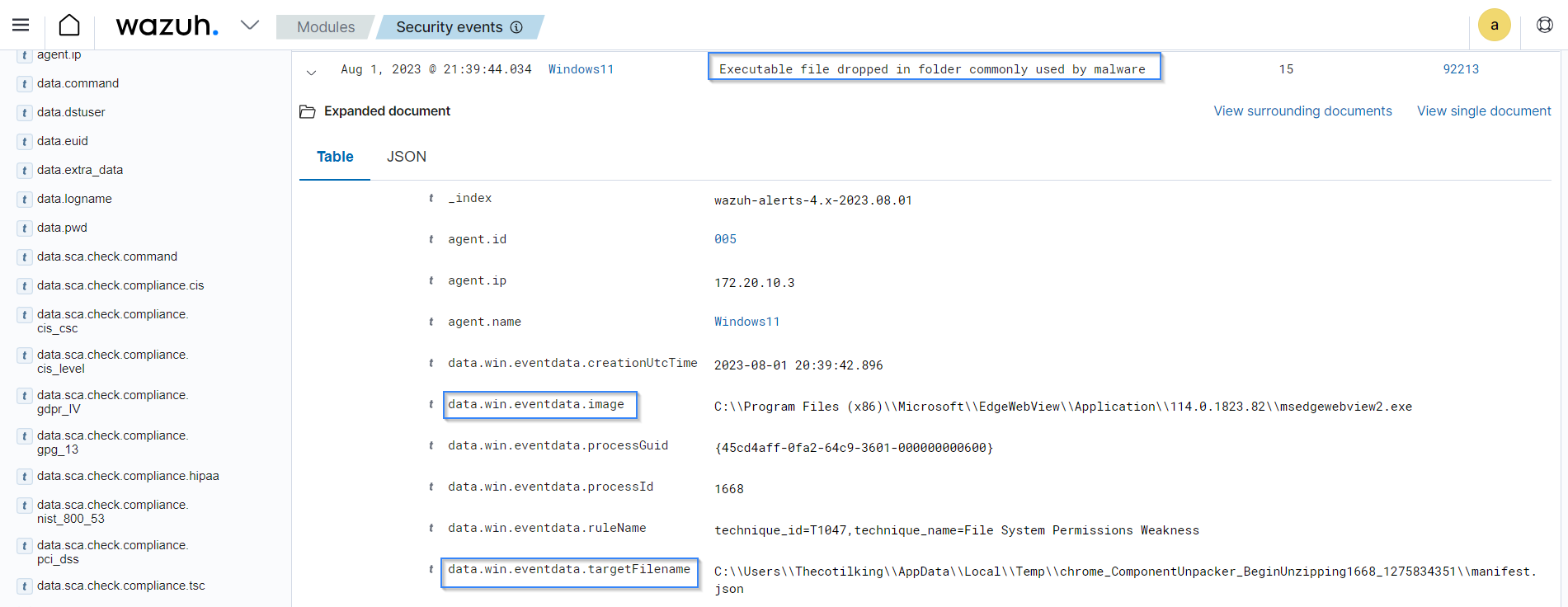
Wazuh allows users to create custom rules for more flexibility in detection, empowering them to focus on relevant activities, and optimizing malware detection. Wazuh decodes and organizes logs from monitored endpoints into fields, which can then be utilized to create custom rules for alerting when malicious activity is detected.
Wazuh rules use multiple fields that denote indicators of compromise (IOCs) to reduce false positives and detect known malware based on specific behaviors. These rules can connect related malware activities, such as intrusion, privilege escalation, lateral movement, obfuscation, and exfiltration for comprehensive detection.
Below is an example of some Wazuh custom rules created to alert on malicious activities of the LimeRAT malware:
<group name="lime_rat,sysmon,">
<!-- Rogue create netflix.exe creation -->
<rule id="100024" level="12">
<if_sid>61613</if_sid>
<field name="win.eventdata.image" type="pcre2">\.exe</field>
<field name="win.eventdata.targetFilename" type="pcre2">(?i)[c-z]:\\\\Users\\\\.+\\\\AppData\\\\Roaming\\\\checker netflix\.exe</field>
<description>Potential LimeRAT activity detected: checker netflix.exe created at $(win.eventdata.targetFilename) by $(win.eventdata.image).</description>
<mitre>
<id>T1036</id>
</mitre>
</rule>
<!-- Registry key creation for persistence -->
<rule id="100025" level="12">
<if_group>sysmon</if_group>
<field name="win.eventdata.details" type="pcre2">(?i)[c-z]:\\\\Users\\\\.+\\\\AppData\\\\Roaming\\\\checker netflix\.exe</field>
<field name="win.eventdata.targetObject" type="pcre2" >HKU\\\\.+\\\\Software\\\\Microsoft\\\\Windows\\\\CurrentVersion\\\\Run\\\\checker netflix\.exe</field>
<field name="win.eventdata.eventType" type="pcre2" >^SetValue$</field>
<description>Potential LimeRAT activity detected: $(win.eventdata.details) added itself to the Registry as a startup program $(win.eventdata.targetObject) to establish persistence.</description>
<mitre>
<id>T1547.001</id>
</mitre>
</rule>
<!-- Network activity detection -->
<rule id="100026" level="12">
<if_sid>61605</if_sid>
<field name="win.eventdata.image" type="pcre2">(?i)[c-z]:\\\\Users\\\\.+\\\\AppData\\\\Roaming\\\\checker netflix\.exe</field>
<description>Potential LimeRAT activity detected: Suspicious DNS query made by $(win.eventdata.image).</description>
<mitre>
<id>T1572</id>
</mitre>
</rule>
<!-- LimeRAT service creation -->
<rule id="100028" level="12">
<if_sid>61614</if_sid>
<field name="win.eventdata.targetObject" type="pcre2" >HKLM\\\\System\\\\CurrentControlSet\\\\Services\\\\disk</field>
<field name="win.eventdata.eventType" type="pcre2" >^CreateKey$</field>
<description>Potential LimeRAT activity detected: LimeRAT service $(win.eventdata.targetObject) has been created on $(win.system.computer).</description>
<mitre>
<id>T1543.003</id>
</mitre>
</rule>
</group>
These rules create alerts that are visible in the Security Events module on the Wazuh dashboard.
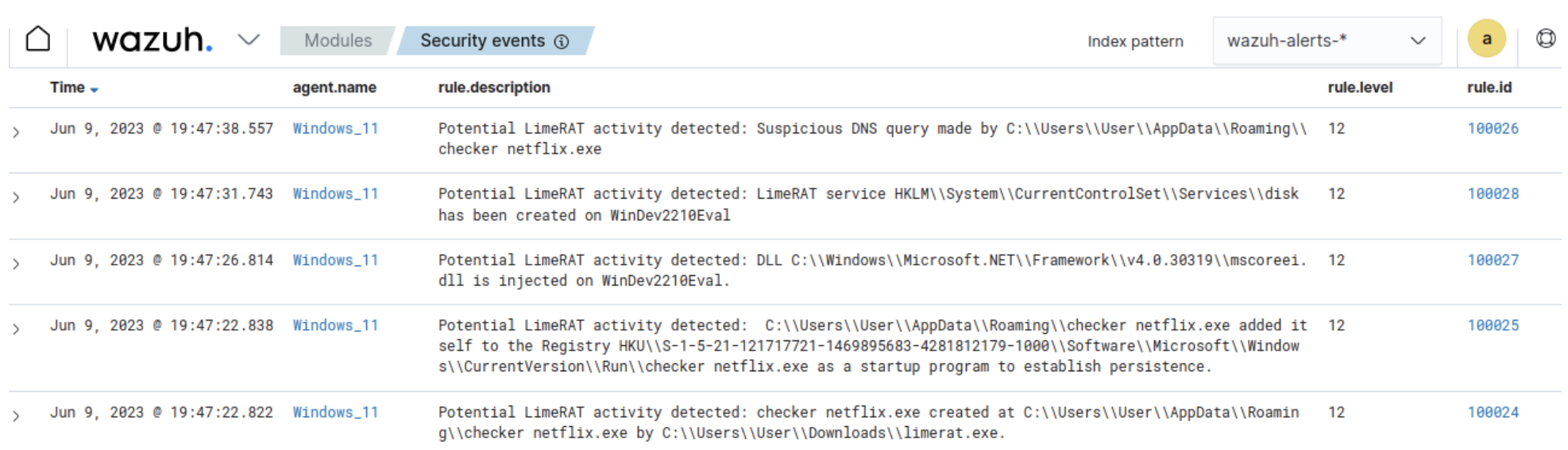
Refer to the blog post on LimeRat detection and response with Wazuh for the full configuration.
Wazuh identifies behavior indicative of malware, it generates real-time alerts and notifications, enabling security teams to respond swiftly and mitigate potential risks before they escalate.
Leveraging file integrity monitoring for detecting malware activity
File Integrity Monitoring (FIM) is a valuable component in malware detection. Wazuh provides FIM capabilities to monitor and detect changes to files and directories on monitored endpoints. These changes include creation, modification, or deletion. While FIM provides essential insights, combining it with other capabilities and integrations further enhances its effectiveness for malware detection. Wazuh allows security teams to create custom rules based on FIM events, enabling targeted malware detection. These customizable rules correlate FIM events with specific indicators of compromises such as suspicious file extensions, code snippets, or known malware signatures.
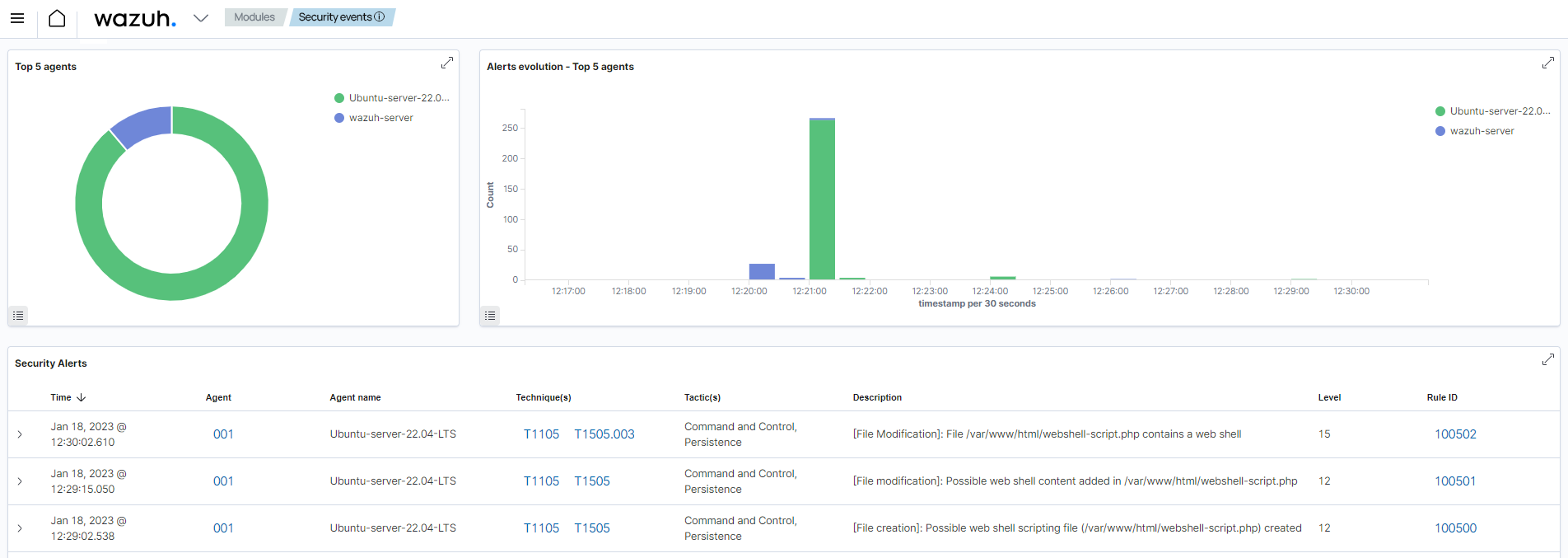
The image below shows an alert when a web shell creates or modifies a file on a web server.
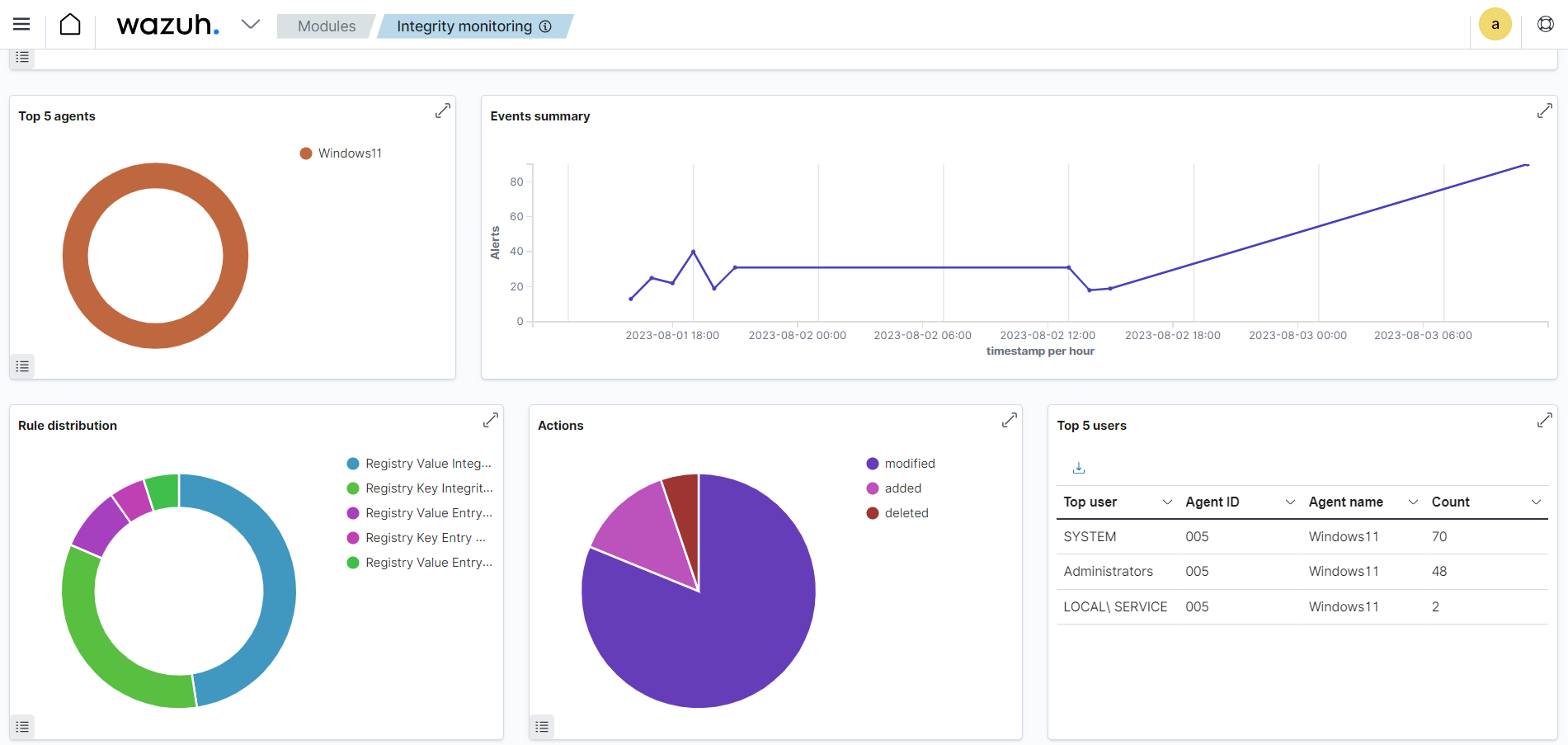
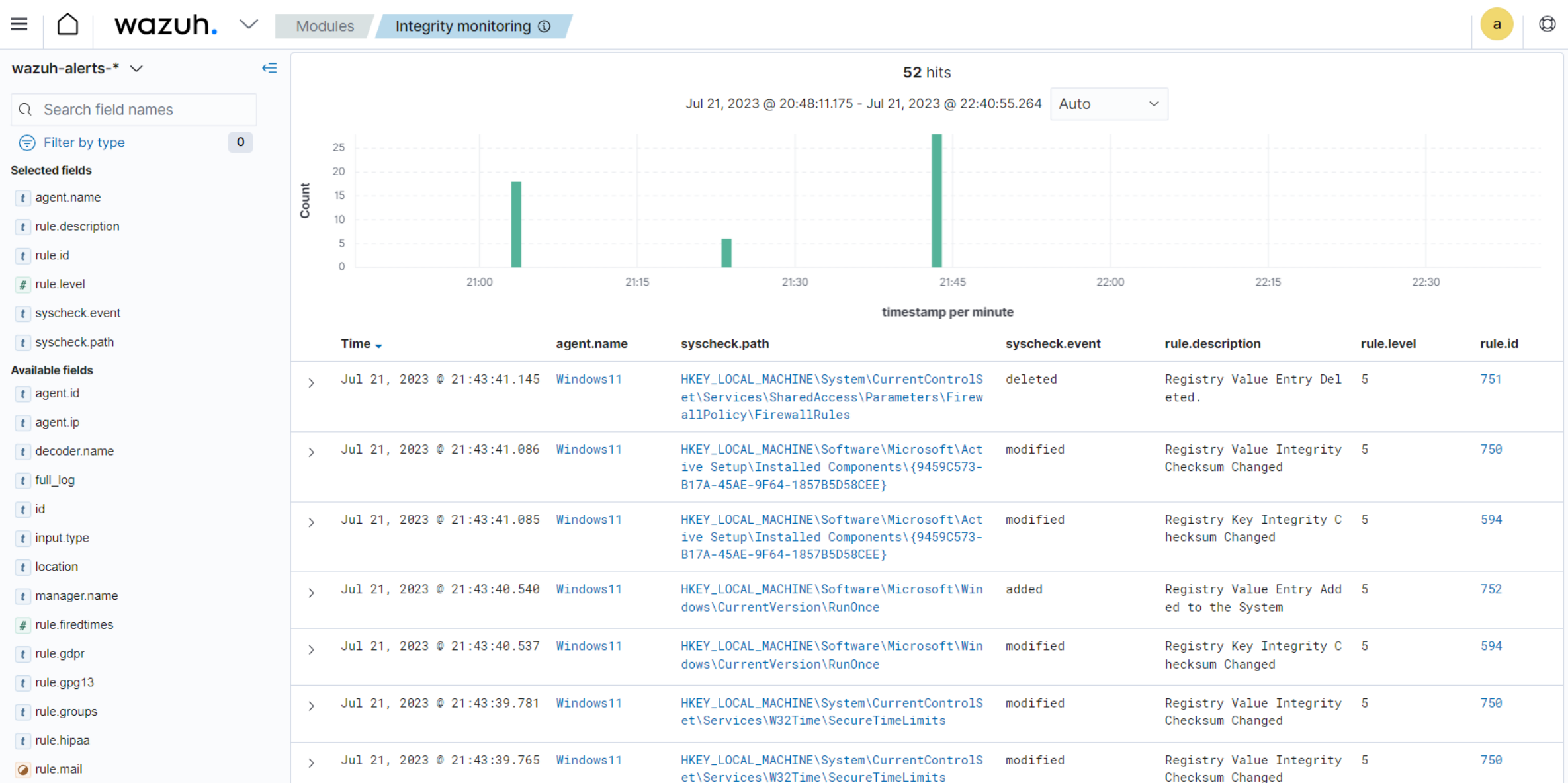
Malware frequently targets Windows Registry to achieve malicious objectives, such as establishing persistence and performing other malicious actions. The Wazuh File Integrity Monitoring (FIM) module includes Windows Registry monitoring that monitors commonly targeted registry paths to detect modifications. When changes occur, the FIM module triggers real-time alerts, empowering security teams to swiftly identify and respond to suspicious registry key manipulation.
The images below display the Wazuh FIM module dashboard and events of Windows Registry modifications.
Enhancing malware detection with threat intelligence integration
Users can boost their malware detection capabilities by integrating with threat intelligence sources. These intelligence feeds enrich the Wazuh knowledge base with additional up-to-date information on known malicious IP addresses, domains, URLs, and other indicators of compromise. Examples of threat intelligence sources Wazuh can integrate with include VirusTotal, MISP, and more.
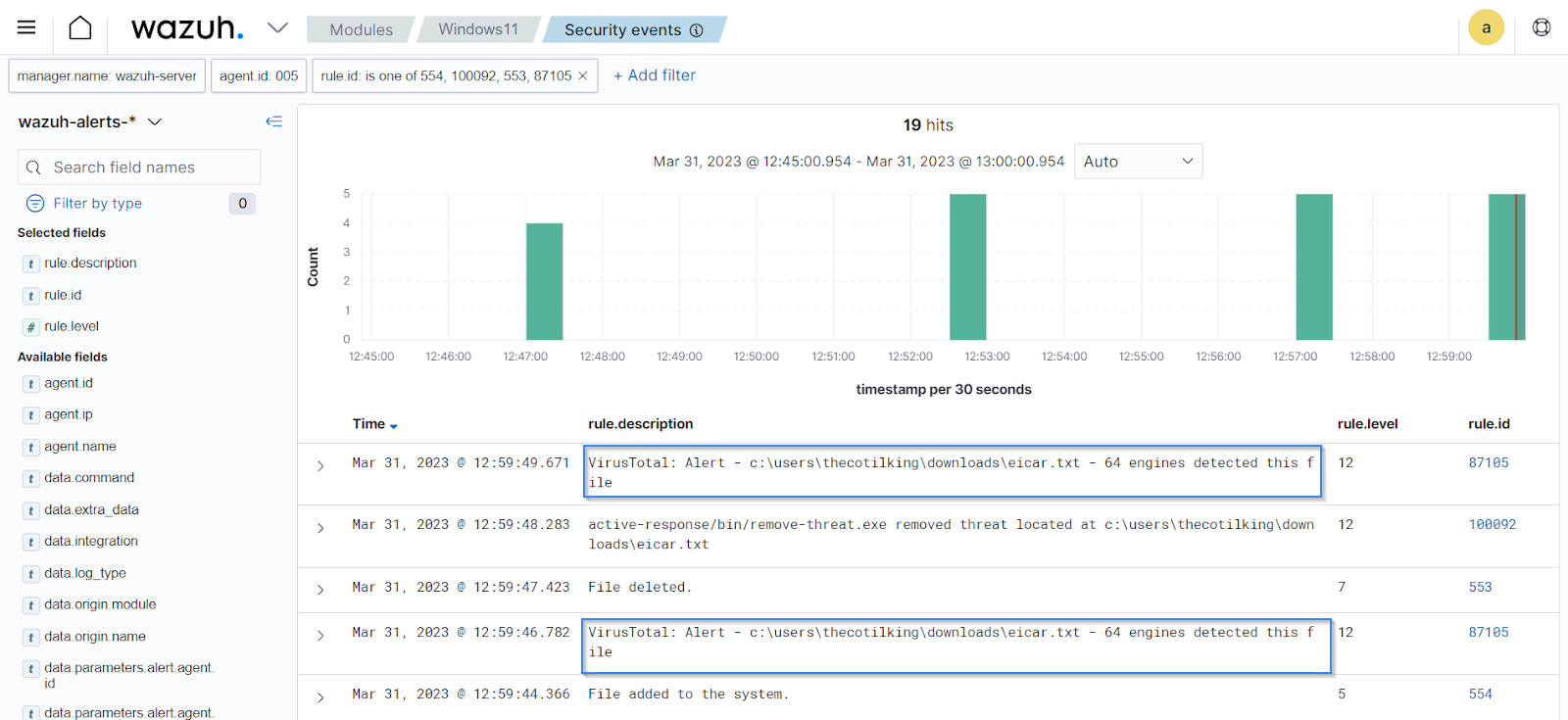
Wazuh proactively identifies malicious files by comparing the identified IOCs with the information stored in the CDB lists (constant databases). These lists can store known malware indicators of compromise (IOCs) including file hashes, IP addresses, and domain names.
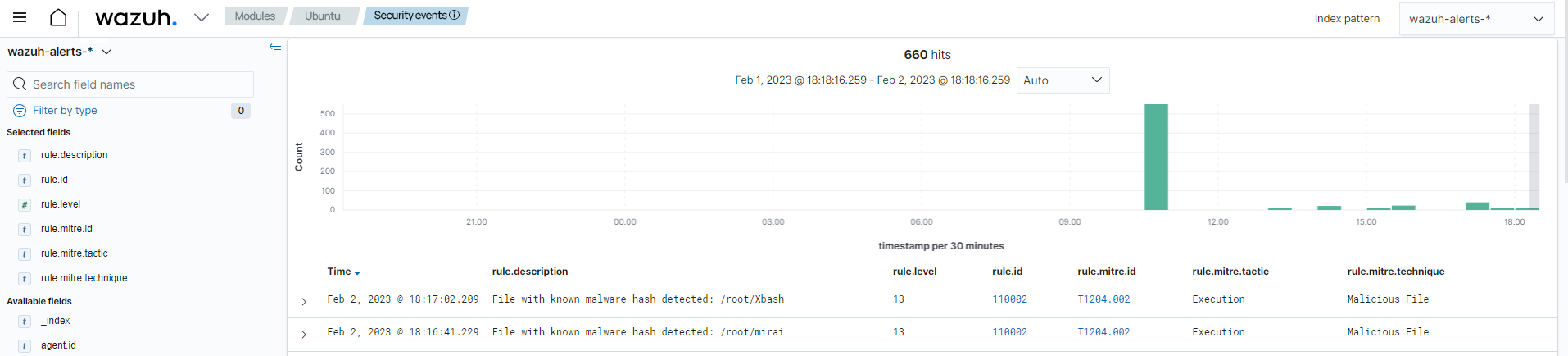
You can customize entries in either key:value or key: format for tailored detection, an example of such is seen below. A CBD list containing known MD5 malware hashes of the Mirai and Xbash malware is used for detection:
e0ec2cd43f71c80d42cd7b0f17802c73:mirai
55142f1d393c5ba7405239f232a6c059:Xbash
Upon detection, these alerts are observed within the Security Events module of the Wazuh dashboard, as seen below.
Refer to the Use case: Detecting malware using file hashes in a CDB list for full configurations.
Unveiling stealthy threats with rootkit detection
Rootkits are malicious software designed to conceal the presence of malware on an endpoint by manipulating operating system functions such as altering system calls or modifying kernel data structures. Wazuh has a Rootcheck module that periodically scans the monitored endpoint to detect rootkits both at the kernel and the user space level. The rootcheck identifies and alerts potential rootkit activity. By analyzing system behavior and comparing it to known rootkit patterns, Wazuh promptly detects rootkit-related patterns and raises alerts for further investigation.
Below, we show an example of an alert generated by the Wazuh Rootcheck module when it detects an anomaly in the filesystem:
** Alert 1668497750.1838326: - ossec,rootcheck,pci_dss_10.6.1,gdpr_IV_35.7.d,
2022 Nov 15 09:35:50 (Ubuntu) any->rootcheck
Rule: 510 (level 7) -> 'Host-based anomaly detection event (rootcheck).'
Rootkit 't0rn' detected by the presence of file '/usr/bin/.t0rn'.
title: Rootkit 't0rn' detected by the presence of file '/usr/bin/.t0rn'.
While Wazuh continues to enhance its rootkit behavior detection capabilities, the Command monitoring module can also be configured to monitor command-line activities across endpoints, enabling the detection of malicious commands and malware activities. This module provides organizations with a comprehensive approach to uncovering hidden threats and safeguarding their systems effectively.
Monitoring system calls for malware and anomaly detection
Wazuh monitors system calls on Linux endpoints to bolster malware detection and aid in anomaly detection. Wazuh utilizes the Linux Audit system to monitor system calls.
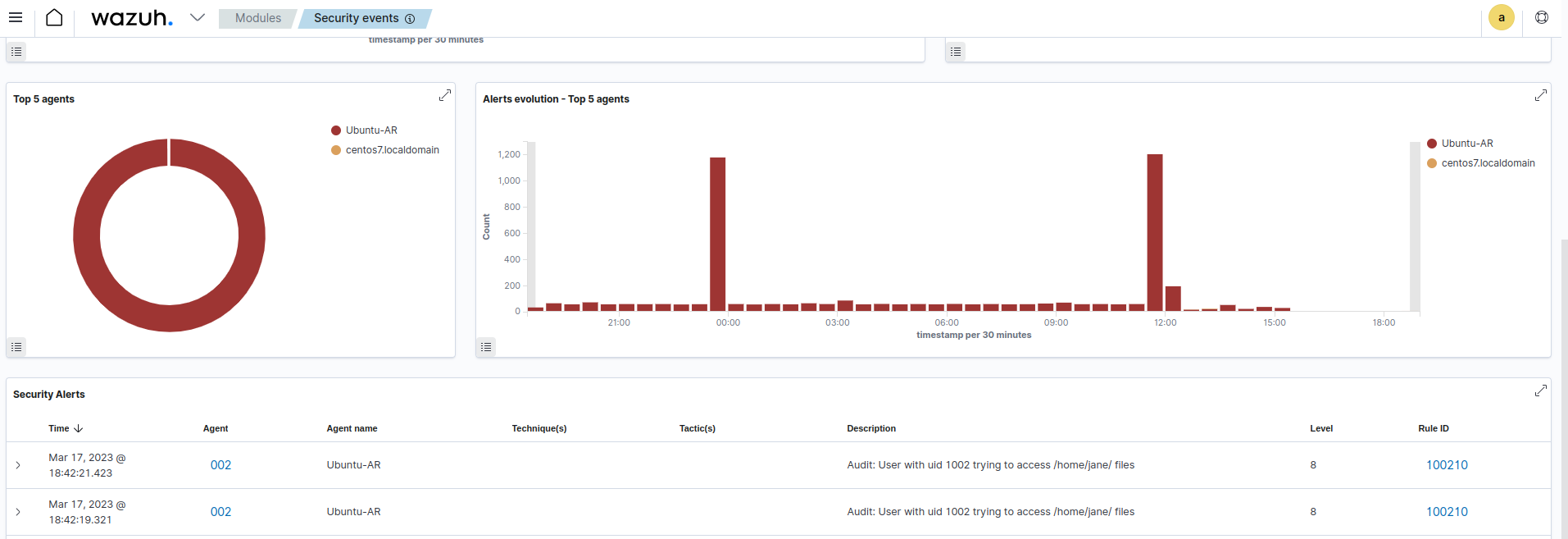
System call monitoring in combination with Wazuh File Integrity Monitoring (FIM) and threat intelligence integration enhances malware detection. It captures security-relevant events like file access, command execution, and privilege escalation, providing real-time insights into potential security incidents. This comprehensive approach strengthens organizations' cybersecurity resilience. In the image below, you can visualize the alerts for privilege abuse on the Wazuh dashboard for Ubuntu Linux 22.04.
Wazuh empowers security teams to leverage the audit rules provided by Auditd. Creating custom rules based on system call events enhances malware detection efforts and strengthens overall cybersecurity resilience.