How it works
To detect vulnerabilities, Wazuh agents collect a list of installed applications from monitored endpoints and send it periodically to the Wazuh server. Local SQLite databases in the Wazuh server store this list. Also, the Wazuh server builds a global vulnerability database from publicly available CVE repositories. It uses this database to cross-correlate this information with the application inventory data of the agent:
Start SQLite and open the vulnerability database using the following command.
# sqlite3 /var/ossec/queue/vulnerabilities/cve.db
List the tables in the database using the following command.
sqlite> .tables
Retrieve the data in a table by running the following command.
sqlite> select * from <table>;
Warning
Don’t make changes to the database. It can lead to issues when the Vulnerability Detector is running a scan.
The Wazuh server automatically creates the global vulnerability database with data from the following repositories:
https://canonical.com: Used to pull CVEs for Ubuntu Linux distributions.
https://www.redhat.com: Used to pull CVEs for Red Hat and CentOS Linux distributions.
https://www.debian.org: Used to pull CVEs for Debian Linux distributions.
https://security.archlinux.org: Used to pull CVEs for Arch Linux distributions.
https://nvd.nist.gov: Used to pull CVEs from the National Vulnerability Database.
https://feed.wazuh.com: Used to pull Microsoft Security Updates (MSU) and ALAS feeds. The feeds contain CVE and patch information for Microsoft products and Amazon Linux. They use the Microsoft Update Catalog and the Amazon Linux Security Center as sources of information. Wazuh parses and formats the data before uploading them to the Wazuh feed.
Wazuh updates this database on a regular basis, ensuring the solution checks for the latest CVEs. You can configure the update interval.
Once the Vulnerability Detector module has created the global vulnerability database containing the CVEs, the detection process looks for vulnerable packages in the inventory databases. These inventories are unique to each agent. A package is labeled as vulnerable when its version matches those within the affected range of a CVE. Alerts show the results, and the module stores the findings in a per-agent vulnerability inventory. This inventory contains the current state of every agent and includes vulnerabilities that have been detected and not resolved. Users can query the inventory to check for alerts and vulnerability information.
For Microsoft Windows systems and specific Microsoft products, the Vulnerability Detector has the hotfixes option in the syscollector settings on the Wazuh agent. Using this option enables the module to detect packages that the user has patched. When the Vulnerability Detector detects a patch, it uses the information provided by Microsoft to decide if the patch has resolved the CVEs. Then, it removes them from the list of vulnerabilities.
Alert generation
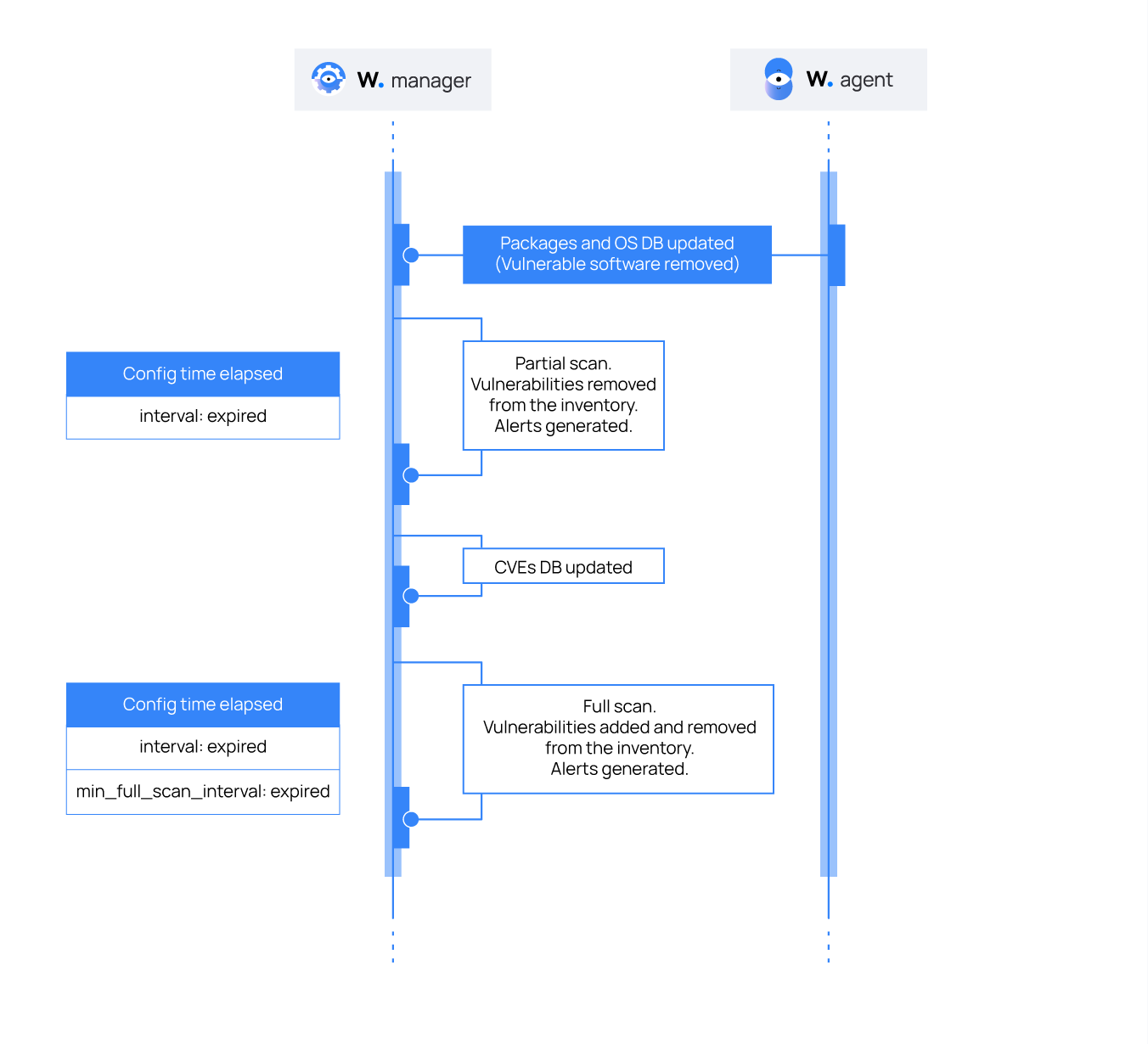
The Vulnerability Detector generates alerts during the baseline scan for every detected vulnerability. You can see this workflow in the diagram below.
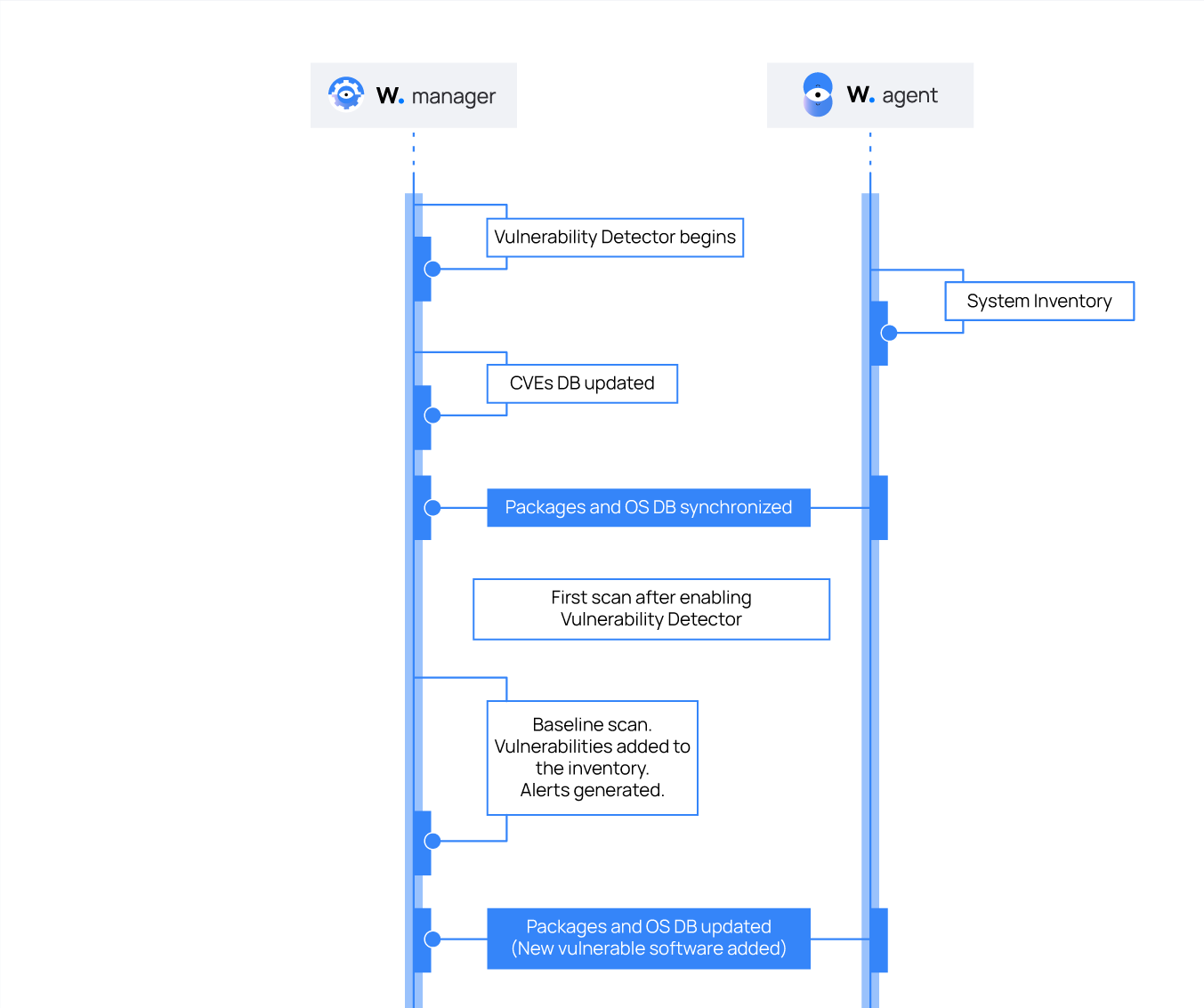
The Vulnerability Detector also generates alerts when it detects new vulnerabilities or when users fix identified vulnerabilities.
Compatibility matrix
The following table shows the operating systems the Vulnerability Detector currently supports and the provider(s) needed for each distribution.
Distribution |
Versions |
Provider |
|---|---|---|
CentOS |
5 |
|
6 |
||
7 |
||
8 |
||
9 |
||
Red Hat |
5 |
|
6 |
||
7 |
||
8 |
||
9 |
||
Ubuntu |
trusty / 14 |
|
xenial / 16 |
||
bionic / 18 |
||
focal / 20 |
||
jammy / 22 |
||
Debian |
buster / 10 |
|
bullseye / 11 |
||
bookworm / 12 |
||
Amazon Linux |
Amazon Linux 1 |
|
Amazon Linux 2 |
||
Amazon Linux 2023 |
||
Arch Linux |
Rolling release |
|
SUSE |
SLES 11 server |
|
SLED 11 desktop |
||
SLES 12 server |
||
SLED 12 desktop |
||
SLES 15 server |
||
SLED 15 desktop |
||
AlmaLinux |
AlmaLinux 8 |
|
AlmaLinux 9 |
||
Windows |
Windows XP and later |
|
macOS |
macOS Sierra and later |
|
Note
Users can extend support for operating systems that aren't listed above by using the allow option.