Use cases
Monitoring the output of a command on an endpoint
In this example, we configure the agentless monitoring module to run some commands on a monitored VMware ESXI 8.0.0 endpoint and detect the output.
Configuration
Wazuh server
Perform the following steps on the Wazuh server.
Add the following block to the
/var/ossec/etc/ossec.confconfiguration file. This configuration runs a command to print the content of the/tmp/newfile.txtfile every 2 minutes. It also detects the difference between the outputs each time the command is run. Replaceuser@example.netwith the username and the hostname or IP address of your VMware ESXI endpoint.<agentless> <type>ssh_generic_diff</type> <frequency>200</frequency> <host>user@example.net</host> <state>periodic_diff</state> <arguments>cat /tmp/newfile.txt</arguments> </agentless>
Restart the Wazuh manager with the following command to apply the changes:
systemctl restart wazuh-manager
Test the configuration
Perform the following steps on the monitored VMware ESXI endpoint.
Create a file
/tmp/newfile.txt:$ touch /tmp/newfile.txt
Add the text “new addition” and wait for 3 minutes:
$ echo “new addition” > /tmp/newfile.txt
Visualize the alert
You can visualize the alert with any of these options
Navigate to the Discover section and open the visualization created in the Visualization section.
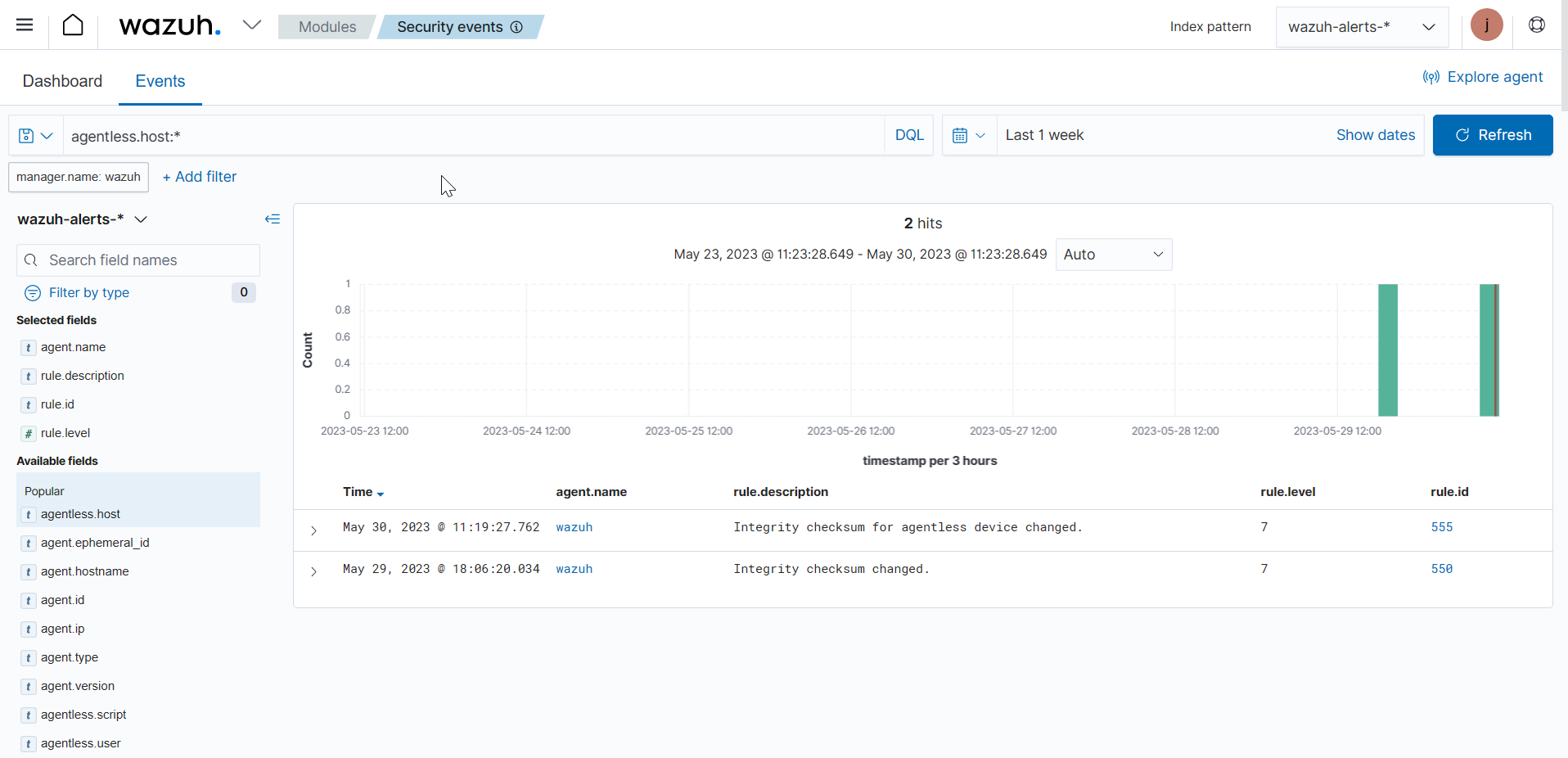
Navigate to Modules > Security events on the Wazuh dashboard. Search for
agentless.host:*to view the alert generated.
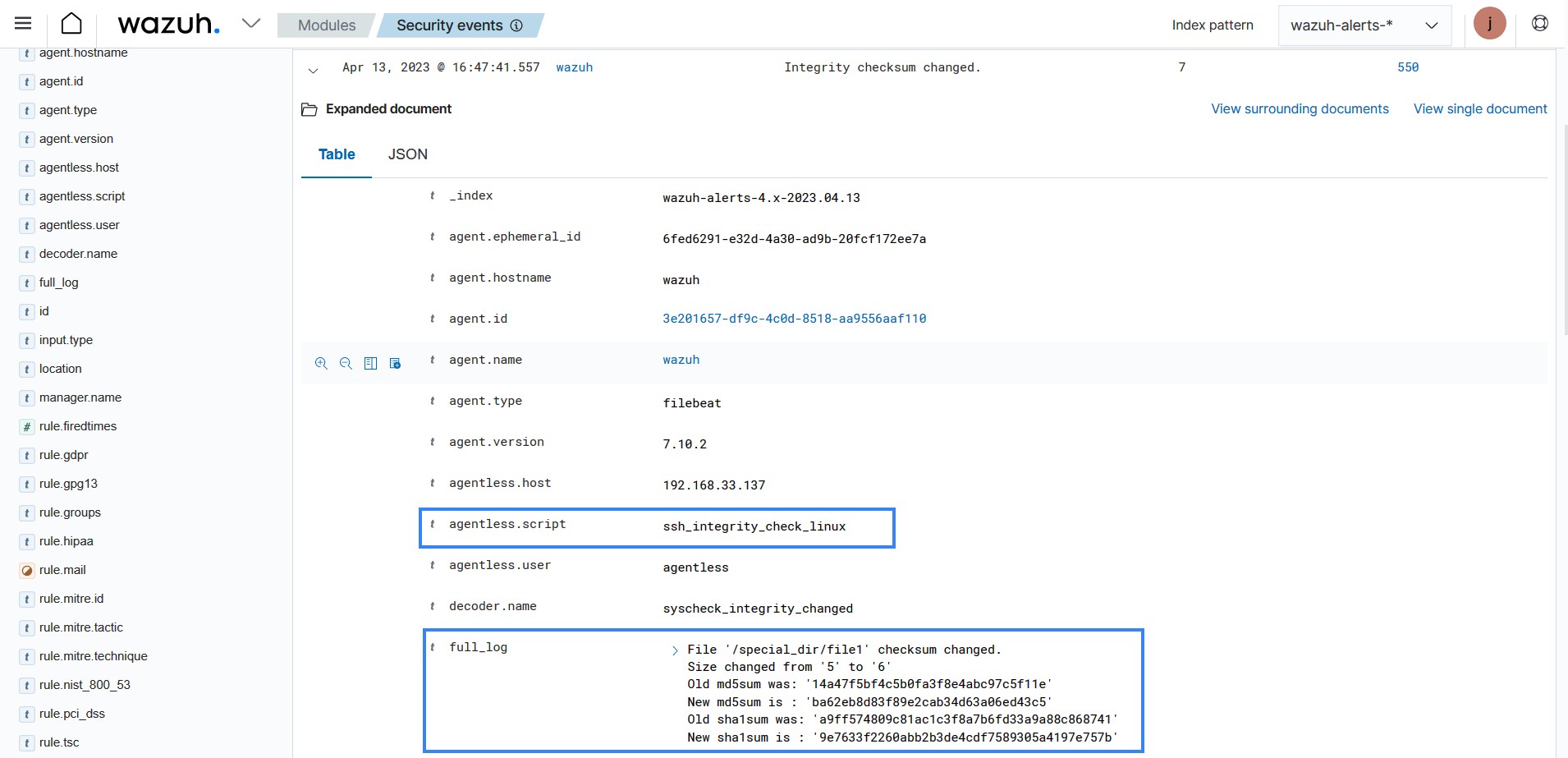
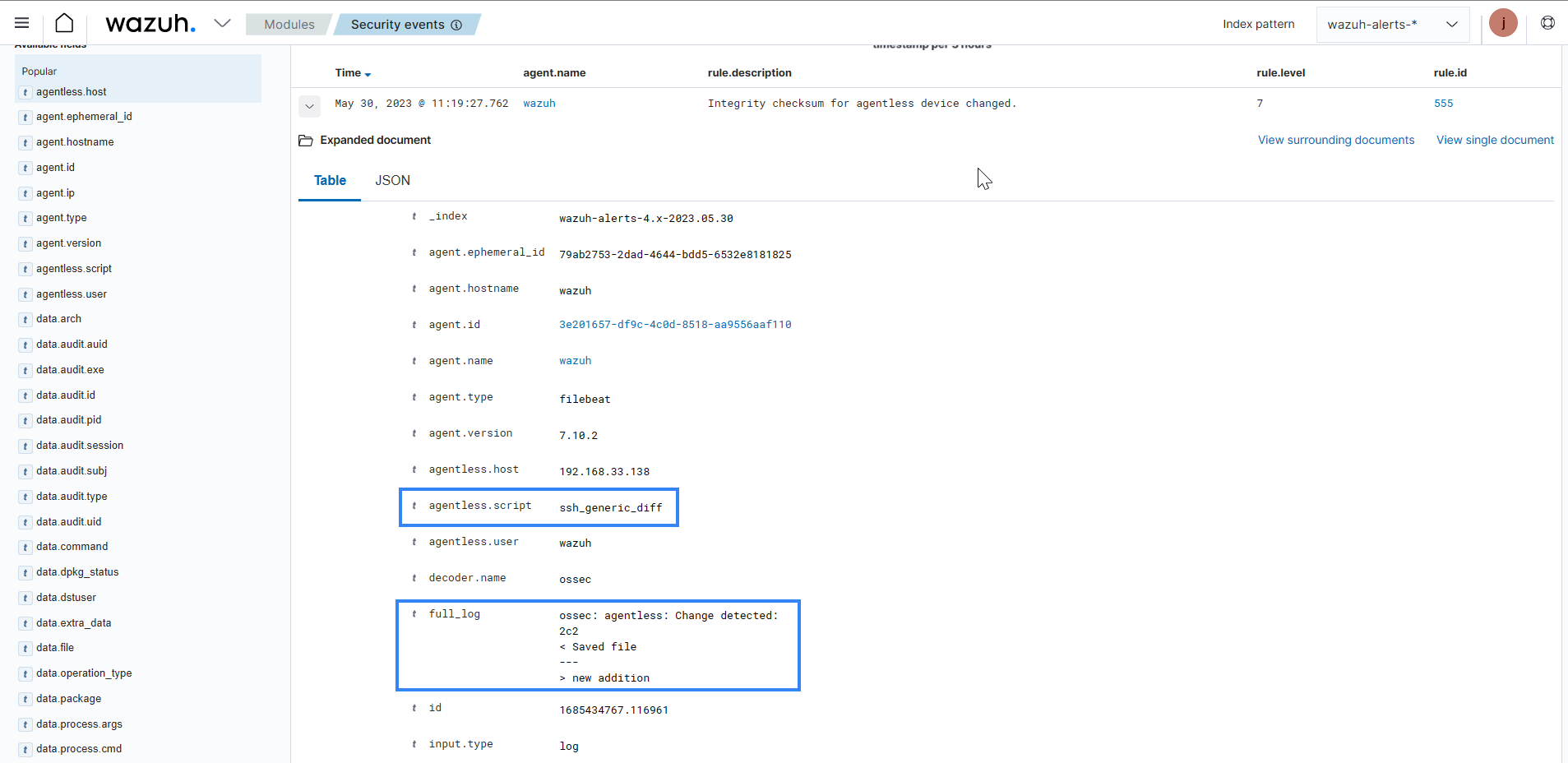
Expand the alert with rule.id:555 to view more information about the event. In the image below, under the full log, you can see the output of the command and the difference between the commands when the file was modified.
Monitor files and directories on an endpoint
In the example, we monitor changes to a specified file and directory on a monitored Linux endpoint using the agentless monitoring capability.
Configuration
Wazuh server
Perform the following steps on the Wazuh server.
Add the block below to the
/var/ossec/etc/ossec.confconfiguration file. This configuration monitors the/tmp/file.conffile for modification every 2 minutes. Replaceuser@example.netwith the username and the hostname or IP address of your Linux endpoint.<agentless> <type>ssh_integrity_check_linux</type> <frequency>120</frequency> <host>user@example.net</host> <state>periodic</state> <arguments>/tmp/file.conf /special_dir</arguments> </agentless>
Restart the Wazuh manager with the following command to apply the changes:
systemctl restart wazuh-manager
Test the configuration
Perform the following steps on the monitored endpoint.
Create a file
/tmp/file.conf:$ touch /tmp/file.conf
Modify the
/tmp/file.conf:$ echo demo > /tmp/file.conf
Make a directory
/special_dir:$ mkdir /special_dir
Add a file to the monitored directory:
$ cd /special_dir $ touch file1 file2
Modify the files by adding the string
demoand wait for 2 minutes:echo demo | tee /special_dir/file1 /special_dir/file2
Visualize the alert
You can visualize the alert with any of these options:
Navigate to the Discover section and open the visualization created in the Visualization section.
Navigate to Modules > Security events on the Wazuh dashboard. Search for
agentless.host:*to view the alert generated.
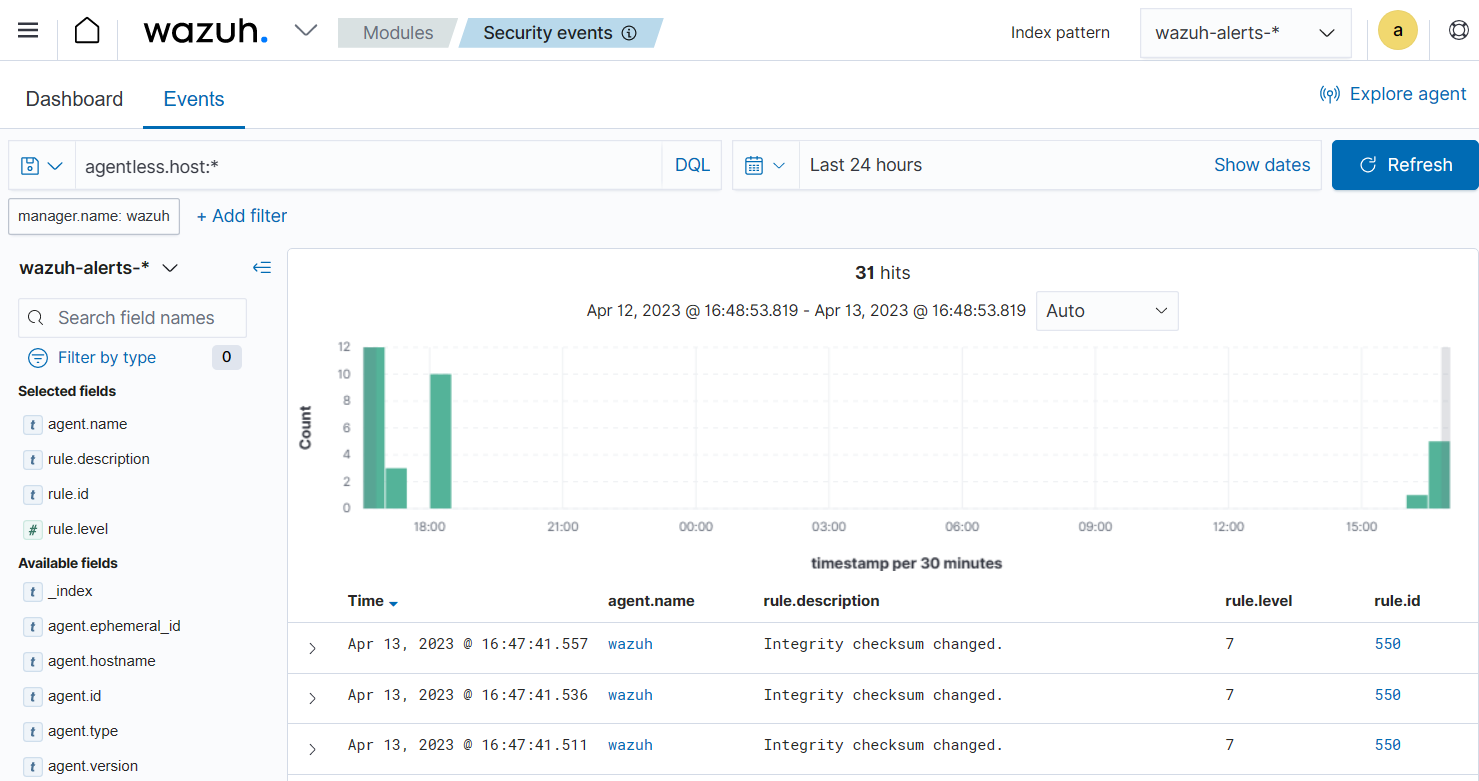
Select the syscheck.path field to add a column that shows all the monitored files.
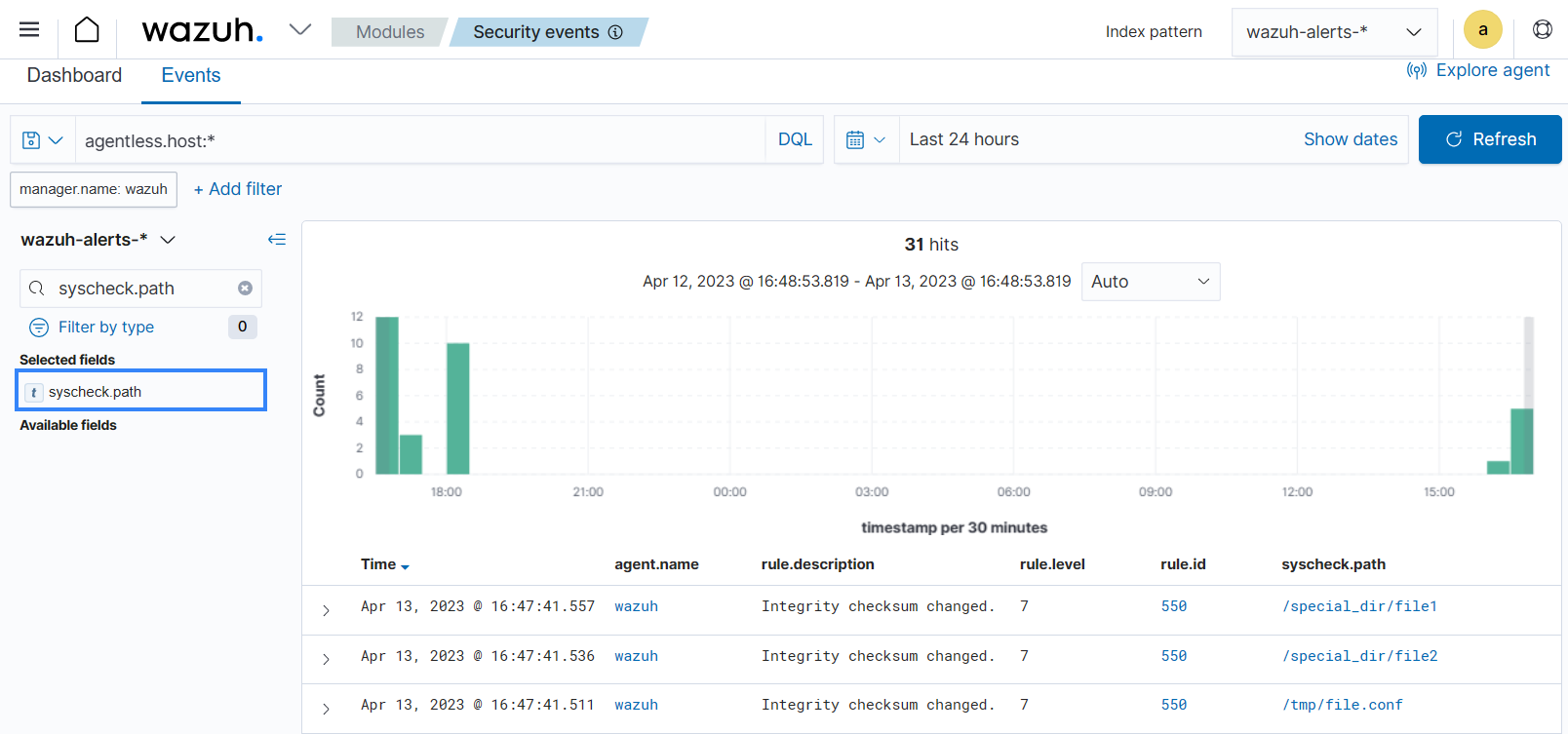
Expand one of the alerts with rule.id:550 to find information about the changes made to the file. You can see the file size and checksum have changed in the image below.