Monitoring file and directory access
In this example, we monitor various types of access to the /home directory of the monitored endpoint. This includes write, read, execution access, and changes in the directory's attributes.
Ubuntu endpoint
Run the commands below to configure the following audit rules:
# echo "-w /home -p w -k audit-wazuh-w" >> /etc/audit/audit.rules # echo "-w /home -p a -k audit-wazuh-a" >> /etc/audit/audit.rules # echo "-w /home -p r -k audit-wazuh-r" >> /etc/audit/audit.rules # echo "-w /home -p x -k audit-wazuh-x" >> /etc/audit/audit.rules
Reload the audit rules to apply the changes:
# auditctl -R /etc/audit/audit.rules # auditctl -l
-w /home -p w -k audit-wazuh-w -w /home -p a -k audit-wazuh-a -w /home -p r -k audit-wazuh-r -w /home -p x -k audit-wazuh-x
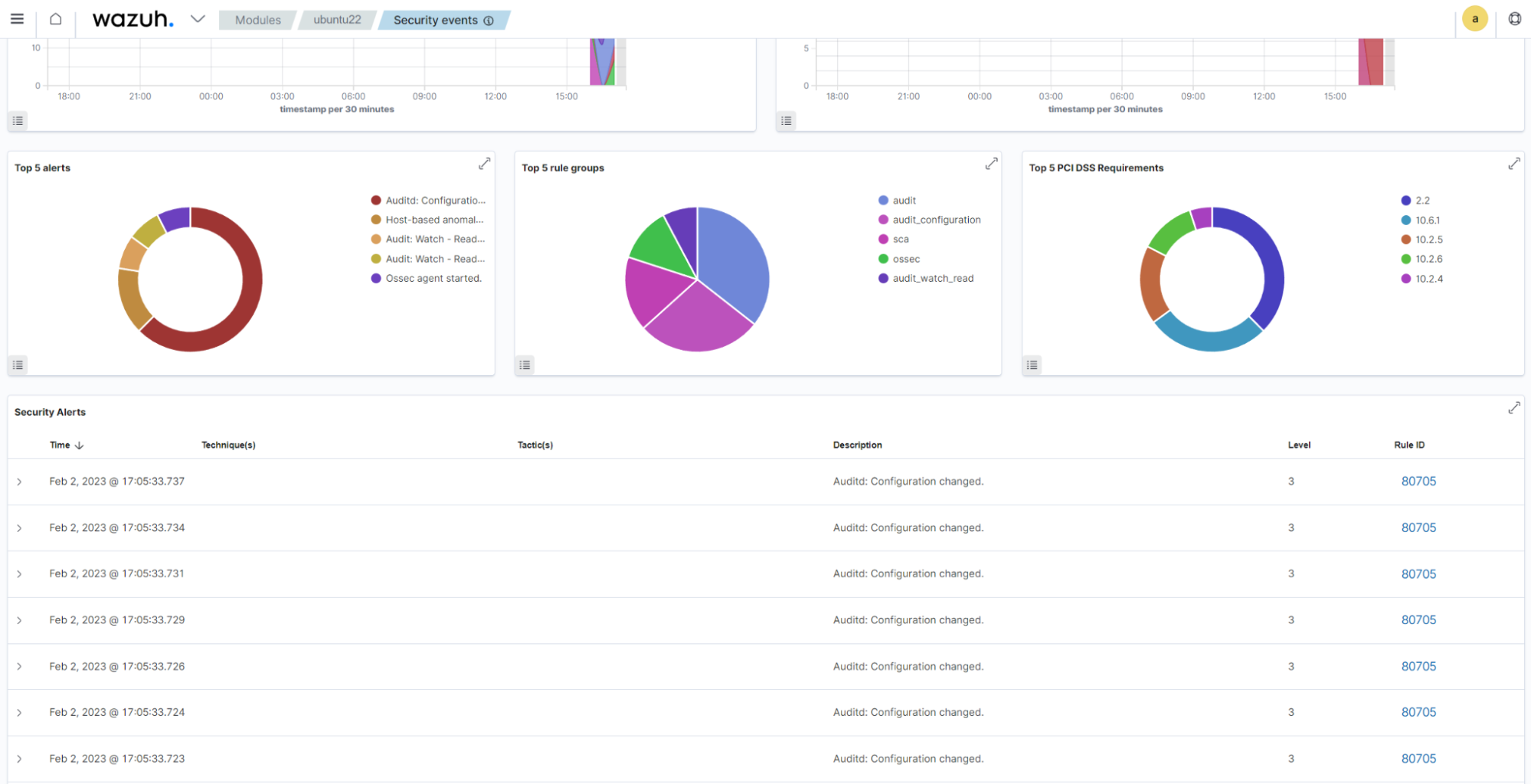
Audit configuration alerts are displayed in the Security Events and System Auditing tab of the Wazuh dashboard.
Note
While it would be possible to define the previous audit rules as one rule specifying -p warx,we intentionally separate them out. So, each rule has its own unique key value that is important for analysis.
Test the configuration
Perform the following actions on the monitored endpoint.
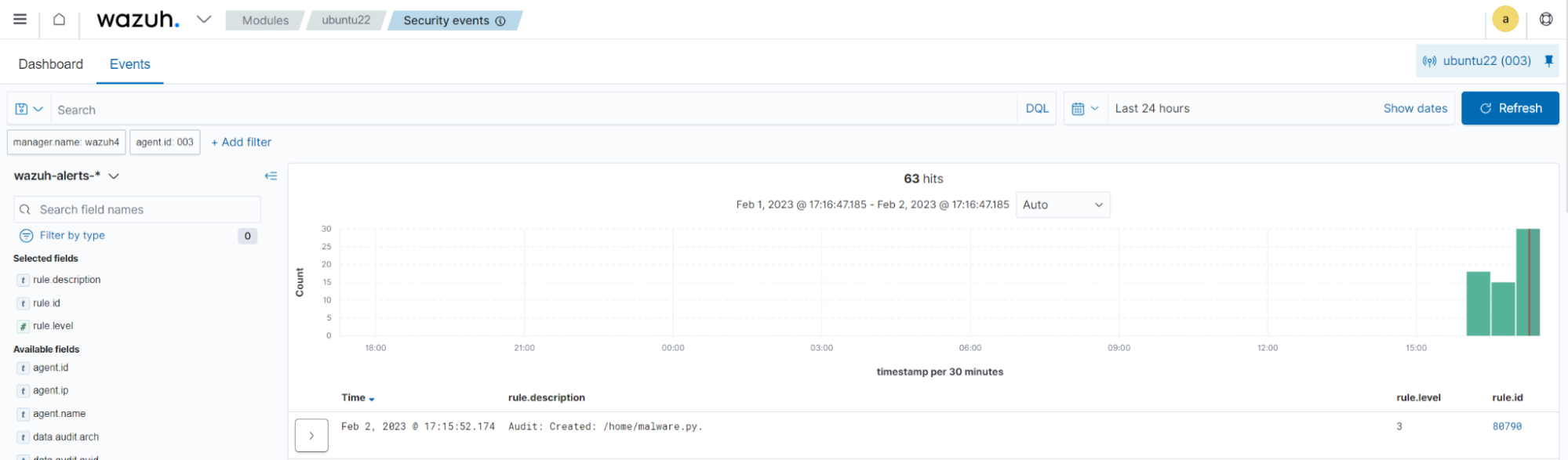
Create a new file
Run the command below to create a new file in the /home directory:
$ touch /home/malware.py
You can visualize the alert data in the Wazuh dashboard. To do this, go to the Security events module and apply the rule.id:80790 filter to query the alert.
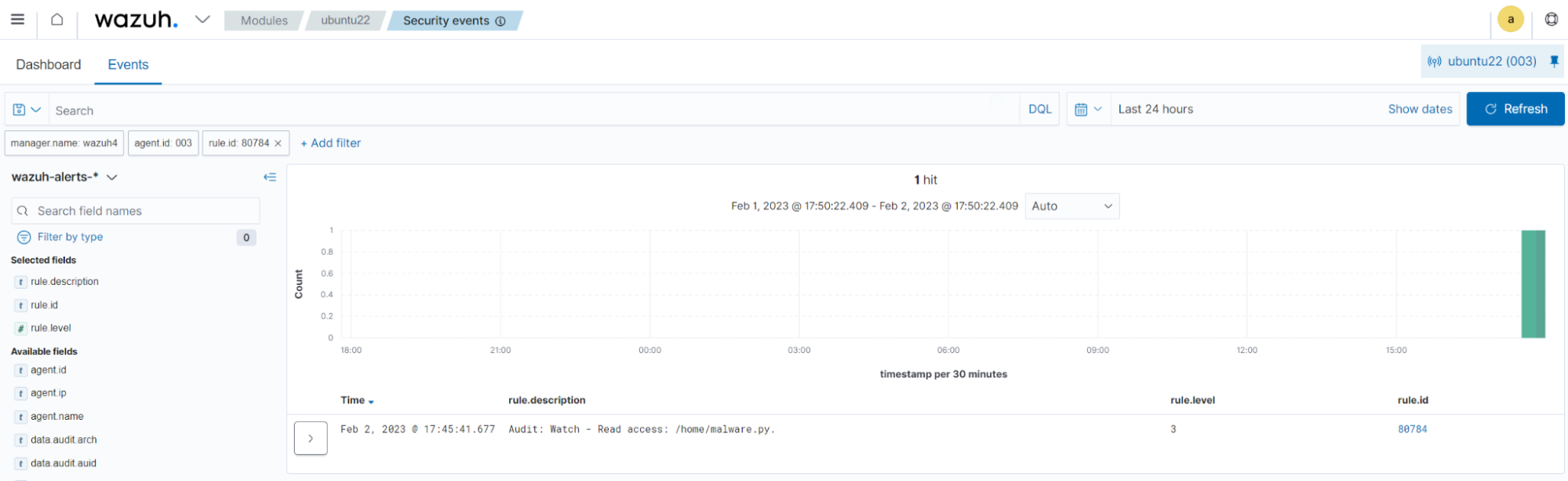
Write access
Run the command below to read the new file:
$ nano /home/malware.py
You can visualize the alert data in the Wazuh dashboard. To do this, go to the Security events module and apply the rule.id:80784 filter to query the alert.
Change permissions
Run the command below to change the permission of the /home/malware.py file:
$ chmod u+x /home/malware.py
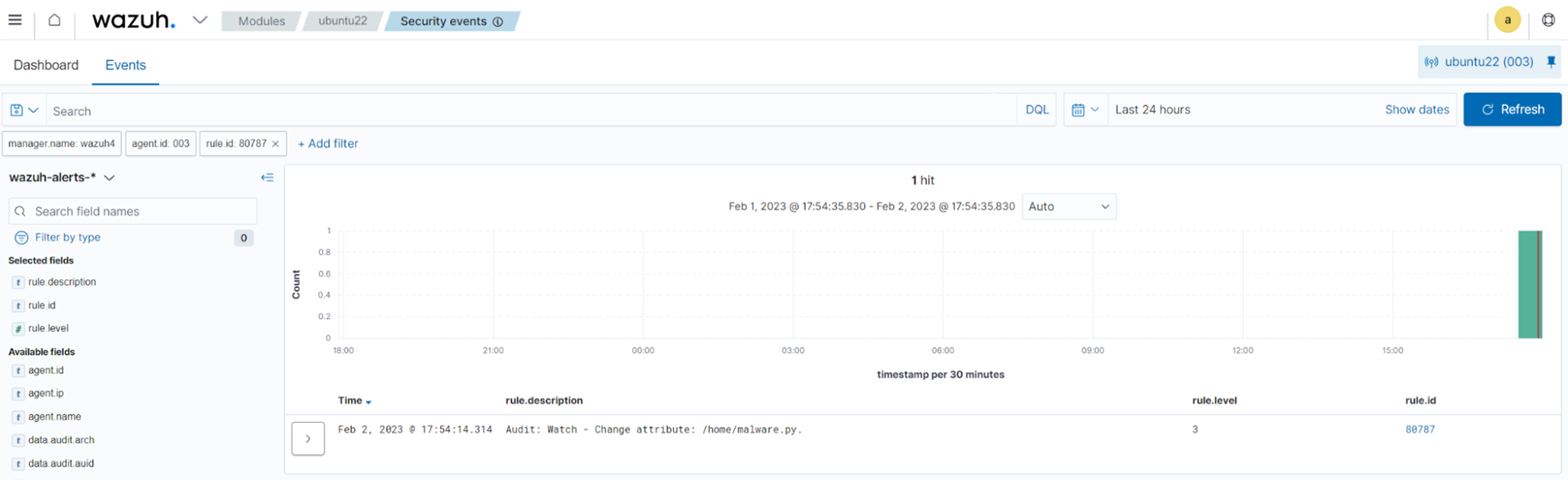
You can visualize the alert data in the Wazuh dashboard. To do this, go to the Security events module and apply the rule.id:80787 filter to query the alert.
Read and execute access
Run the command below to execute the /home/malware.py file:
$ /home/malware.py
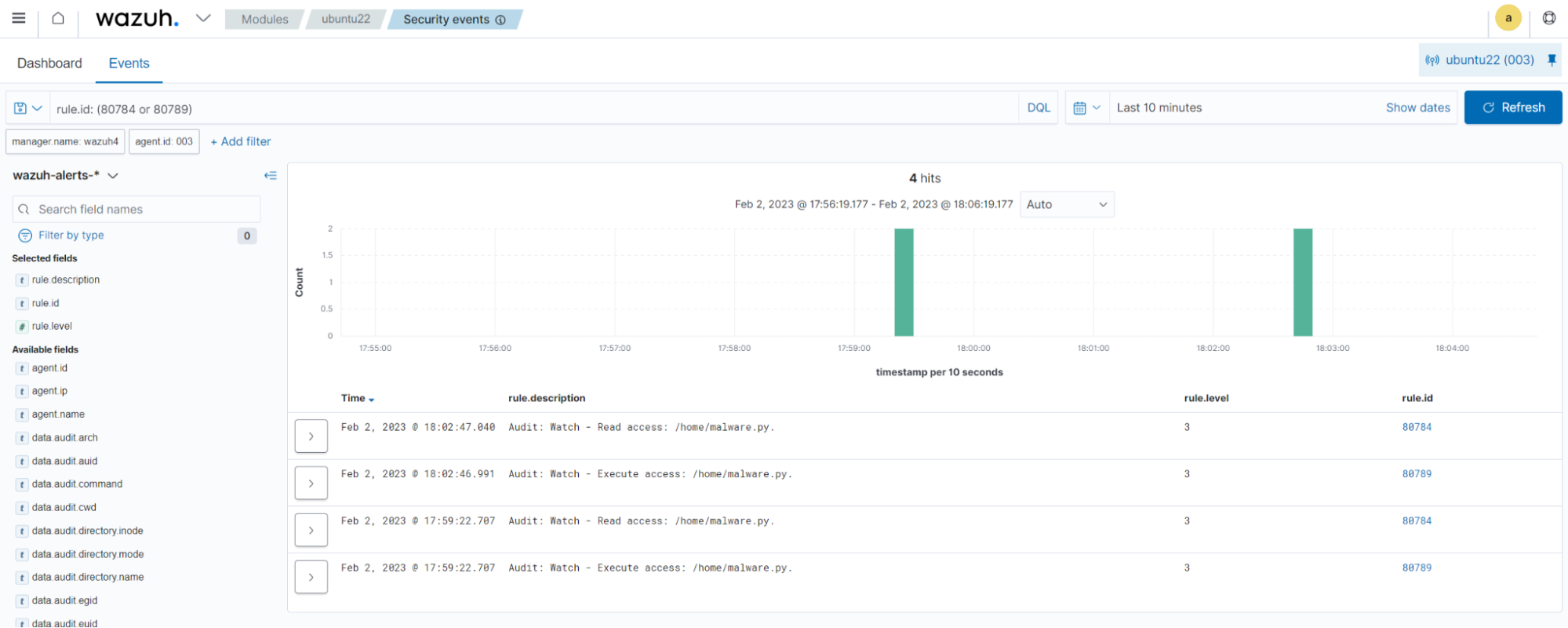
You can visualize the alert data in the Wazuh dashboard. To do this, go to the Security events module and apply the rule.id: (80784 or 80789) filters to query the alerts.
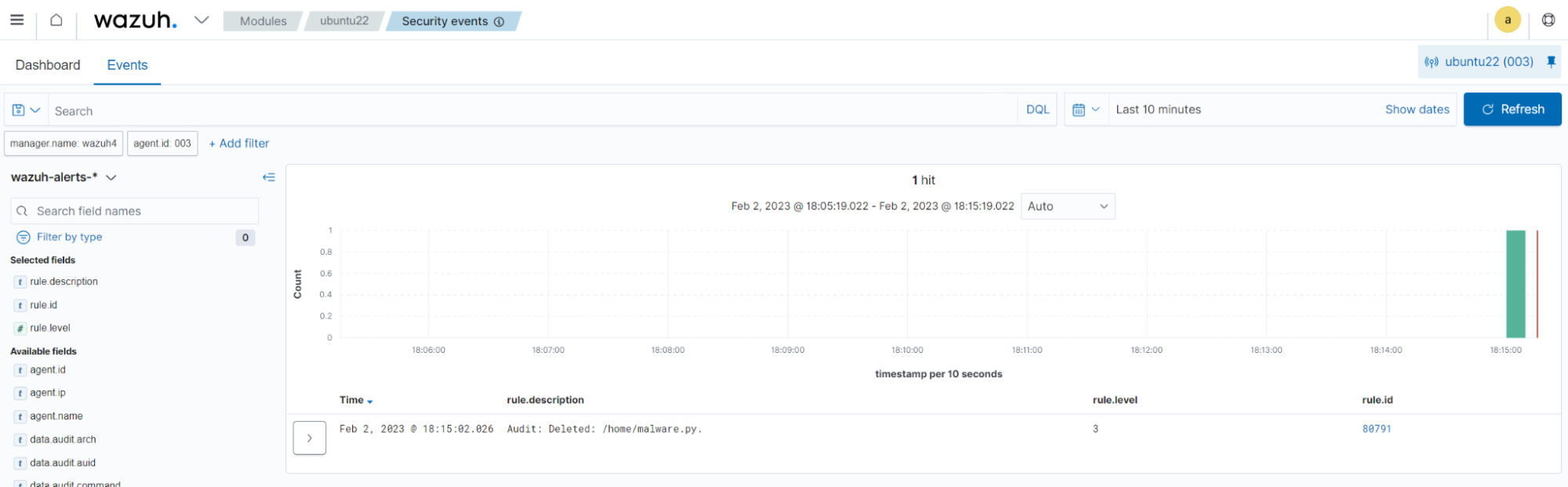
Delete file
Run the command below to delete the /home/malware.py file:
$ rm /home/malware.py
You can visualize the alert data in the Wazuh dashboard. To do this, go to the Security events module and apply the rule.id:80791 filter to query the alert.