Configuring AWS credentials
You can configure the Wazuh module for AWS on the Wazuh server (which also behaves as the Wazuh agent) or on a Wazuh agent installed on a Linux endpoint. Depending on the authentication option used, the Wazuh module for AWS will require access credentials of an AWS Identity and Access Management (IAM) identity to collect log data from the different AWS services. These credentials need to be stored in a file named .aws/credentials on the Wazuh server or agent.
You need to create the credentials file using the root user because the wazuh-modulesd daemon runs with root permission. Ensure the .aws/credentials file is saved in the home directory of the root user, therefore the absolute file path will be /root/.aws/credentials. This file is required for all authentication options except IAM roles for EC2 instances.
In the following sections, we describe how to configure the Wazuh module for AWS to pull AWS services logs using these credentials.
Authenticating options
Credentials can be loaded from different locations. You can specify the credentials in a file, assume an IAM role, or load them from other Boto3 supported locations.
In this section, we describe the several methods of adding the AWS credentials to Wazuh and how to configure the Wazuh module for AWS to use the credentials.
Profiles
Profiles are logical groups of configuration settings. You can set up multiple profiles in the following files.
/root/.aws/credentials: Each profile defines the access keys for a previously created IAM user./root/.aws/config: Each corresponding profile specifies an AWS region.
In the example below, the /root/.aws/credentials file defines the default, dev, and prod profiles.
[default]
aws_access_key_id=foo
aws_secret_access_key=bar
[dev]
aws_access_key_id=foo2
aws_secret_access_key=bar2
[prod]
aws_access_key_id=foo3
aws_secret_access_key=bar3
The /root/.aws/config file specifies the AWS region for each profile:
[default]
region = us-east-1
[profile dev]
region = us-east-1
[profile prod]
region = us-east-1
After setting up the profiles, define which one the Wazuh module for AWS will use to collect logs. Configure this in the /var/ossec/etc/ossec.conf file of the Wazuh server or agent. The example below configures the module to pull Amazon CloudTrail logs from the specified bucket using the prod profile.
<bucket type="cloudtrail">
<name>wazuh-s3-bucket</name>
<aws_profile>prod</aws_profile>
</bucket>
IAM Roles
An IAM role is an identity within your AWS account with specific permissions. It's similar to an IAM user but isn't associated with a specific person. Trusted entities can also use IAM roles to interact with different AWS services. An IAM role can be assumed by AWS services, applications running on Amazon EC2 instances, and AWS Identity and Access Management (IAM) users.
Note
This authentication method requires some credentials to be previously added to the configuration using any other authentication method.
This section shows how to create a sample IAM role with read-only permissions to pull data from a bucket:
Go to Services > Security, Identity, & Compliance > IAM.

Go to Roles on the left side of the AWS console and click Create role.
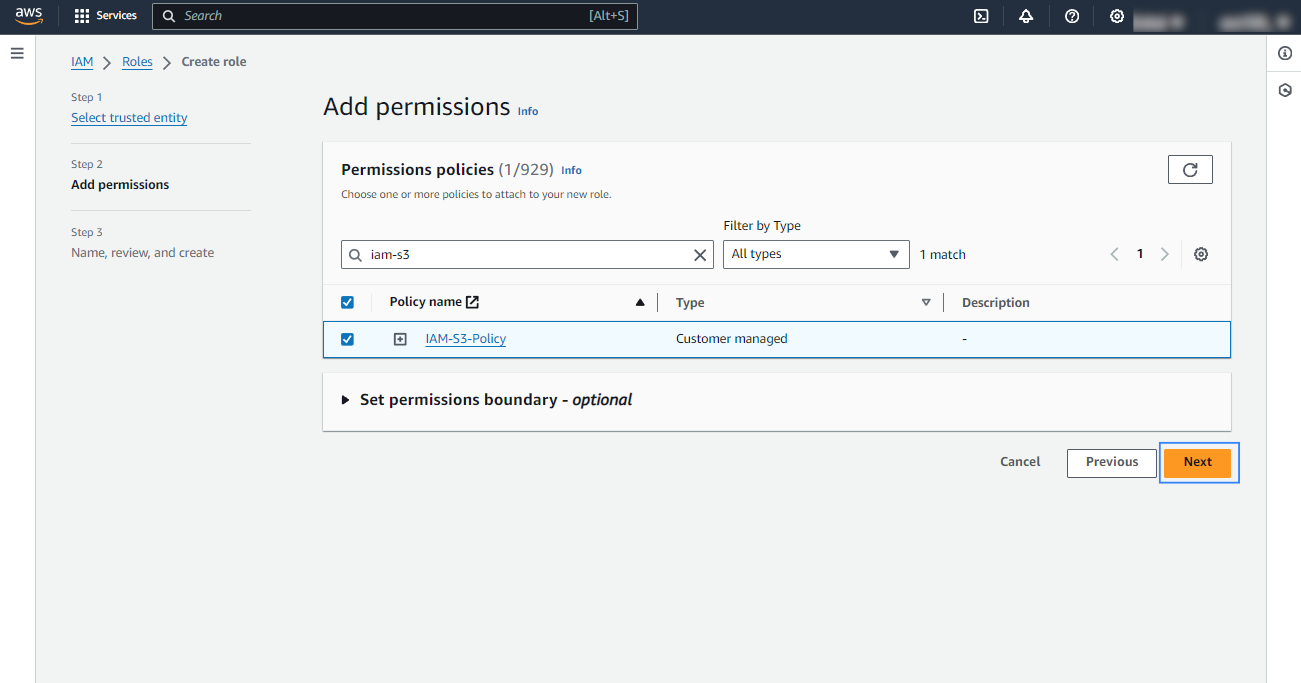
Choose AWS service as Trusted entity type, S3 as service and Use case then click Next.

Select a previously created policy and click Next.
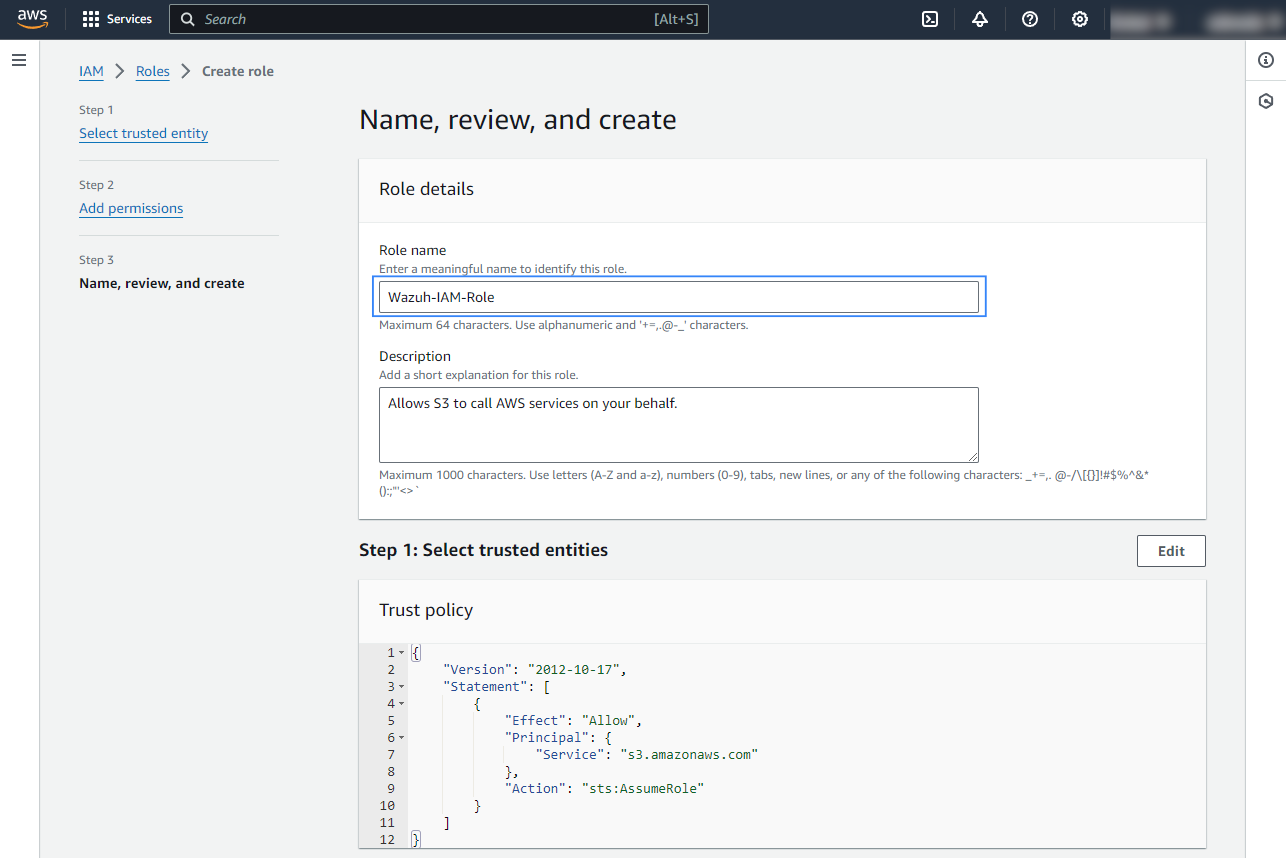
Give the role a descriptive name and click Create role.
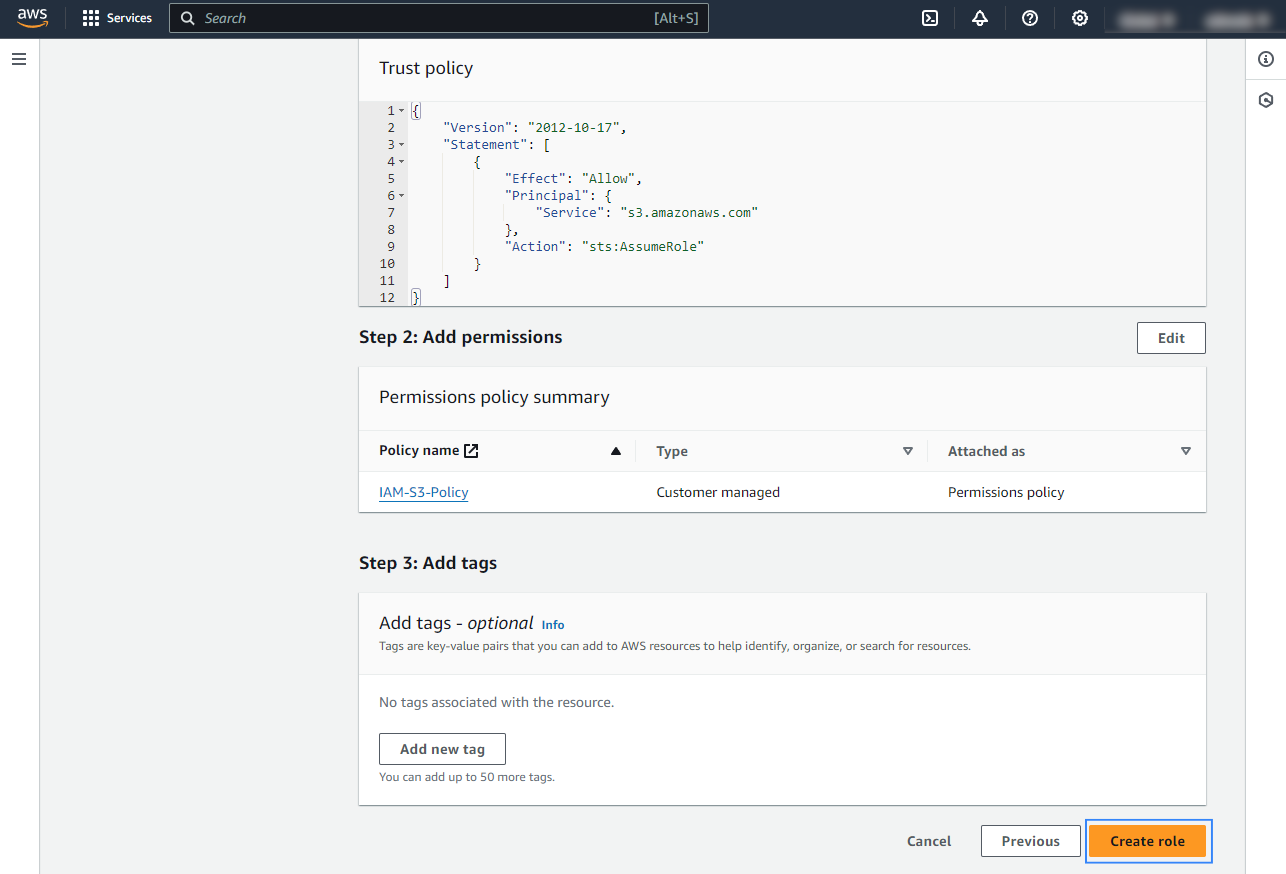
Access the role Summary and click on its Policy name.

Add permissions so the new role can do sts:AssumeRole action.
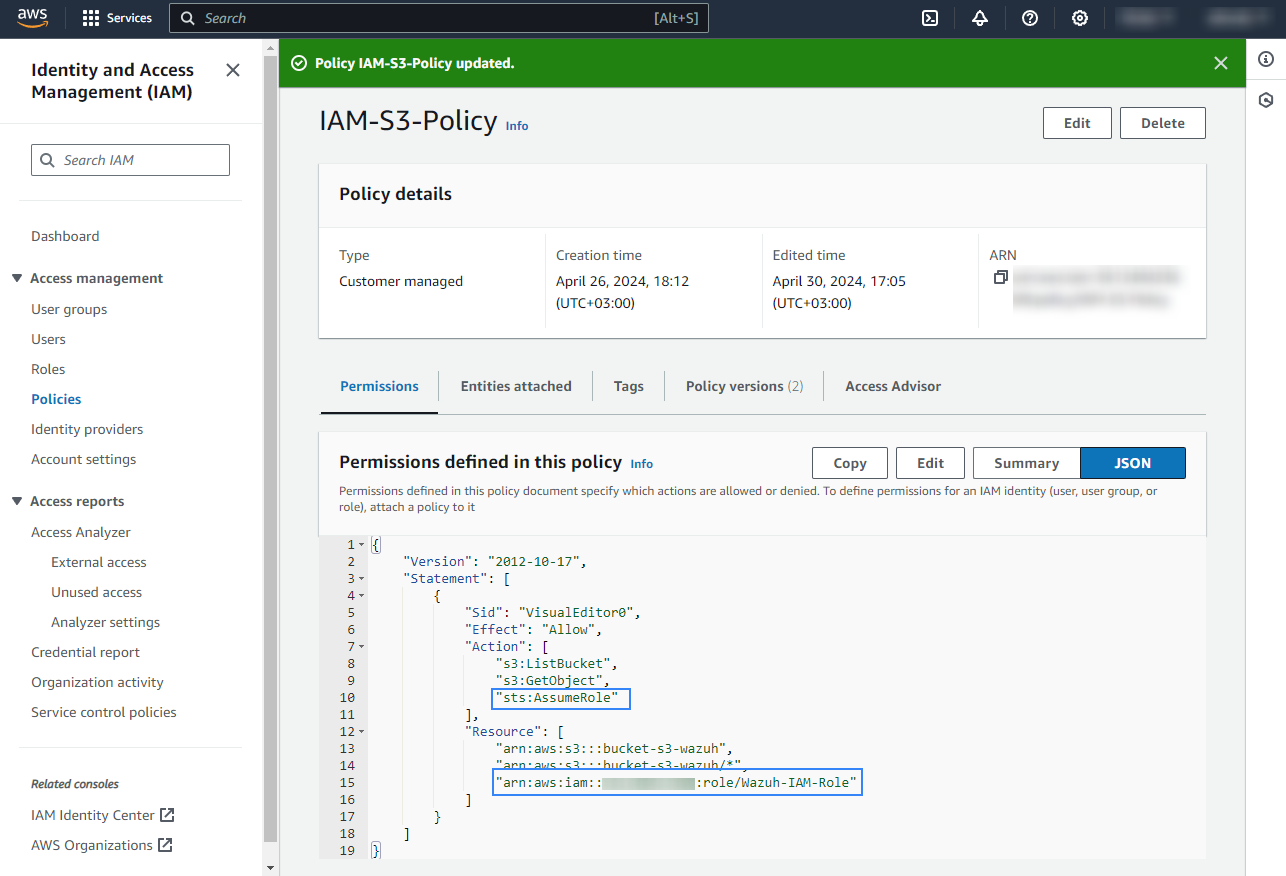
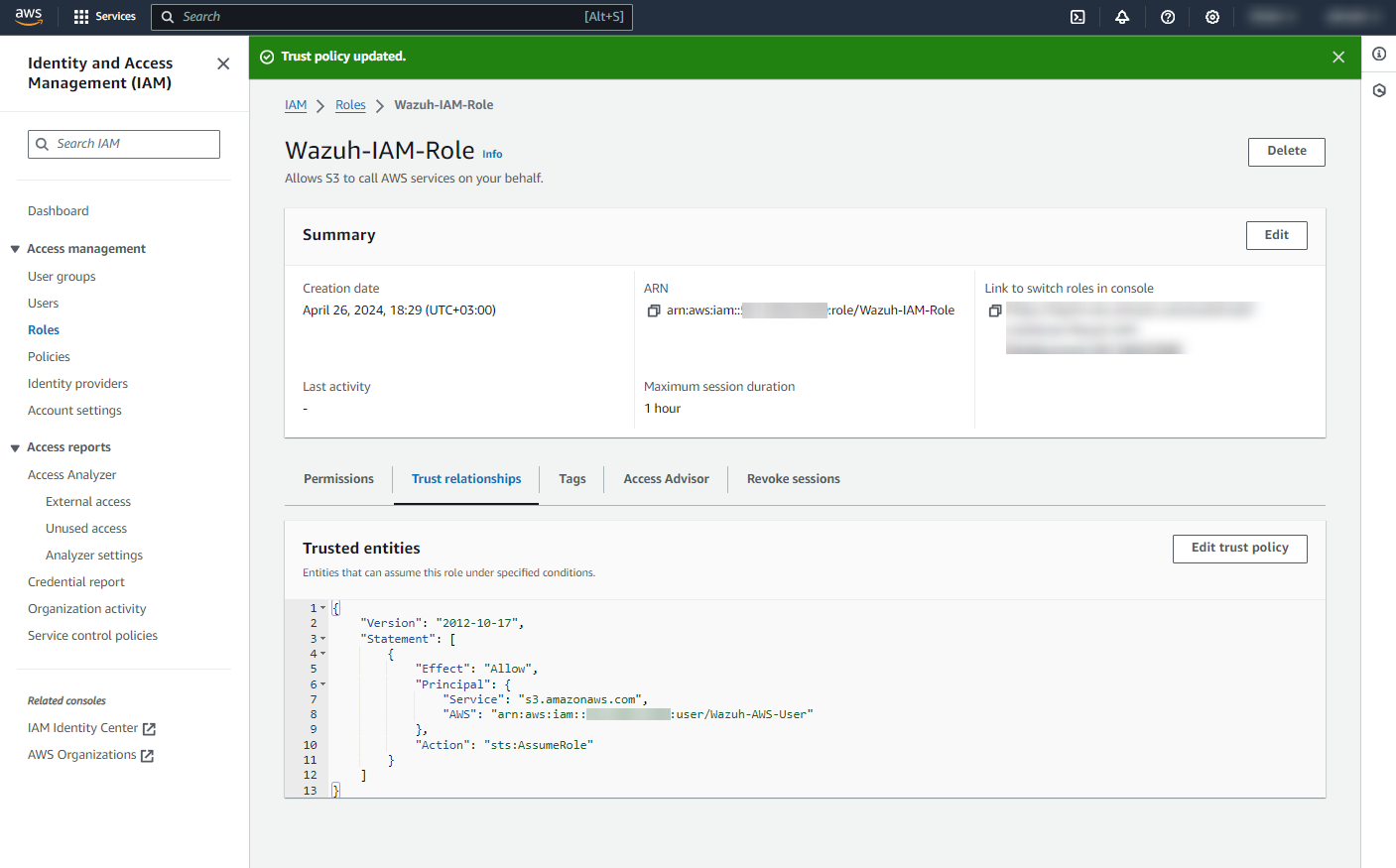
Go back to the role Summary, go to the Trust relationships tab, and click Edit trust policy.

Add the AWS IAM user to the
Principaltag and click Update policy.
After updating the trust policy, copy the Amazon Resource Name (ARN) of the role as this will be used to configure the Wazuh module for AWS.
It is necessary to configure the Wazuh module for AWS using the /var/ossec/etc/ossec.conf file of the Wazuh server or agent. In the example below, we configure the Wazuh module for AWS to pull Amazon CloudTrail logs from the specified bucket using the default profile and the Wazuh-IAM-Role IAM role.
<bucket type="cloudtrail">
<name><WAZUH_AWS_BUCKET></name>
<aws_profile>default</aws_profile>
<iam_role_arn>arn:aws:iam::xxxxxxxxxxx:role/Wazuh-IAM-Role</iam_role_arn>
</bucket>
IAM roles for EC2 instances
You can use IAM roles and assign them to EC2 instances so there's no need to insert authentication parameters in the /var/ossec/etc/ossec.conf file of the Wazuh server or agent. This is the recommended configuration if the Wazuh server or agent is running on an EC2 instance. Find more information about IAM roles on EC2 instances in the official Amazon AWS documentation.
In the example below, we configure the Wazuh module for AWS to pull Amazon CloudTrail logs from the specified bucket using the IAM roles for EC2 instances.
<bucket type="cloudtrail">
<name><WAZUH_AWS_BUCKET></name>
</bucket>