4.3.0 Release notes - 5 May 2022
This section lists the changes in version 4.3.0. Every update of the Wazuh solution is cumulative and includes all enhancements and fixes from previous releases.
Highlights
Wazuh 4.3.0 includes many new additions, such as a remarkable enhancement with the new Wazuh indexer and Wazuh dashboard that improve the user experience and facilitate the management of the whole platform.
Version 4.3.0 enhances the performance of the Wazuh solution and adds new integrations such as the following:
Vulnerability Detector support for Amazon Linux and Arch Linux
New agent integrations with logs from Office 365 and GitHub
Improved RESTful API availability thanks to the API now using multiple processes
Now the Wazuh manager cluster uses multiple processes for improved performance
Wazuh now supports Logcollector with native macOS logs (Unified Logging System)
AWS S3 Server Access logs, Google Cloud Storage buckets, and access logs are now supported too
Below you will find more information about each of these new features.
With Wazuh 4.3.0, two new installers called the Wazuh indexer, and the Wazuh dashboard are available to users to facilitate installation, upgrades, and configuration. The Wazuh indexer is a customized OpenSearch distribution with configurations and tools needed to run out of the box for Wazuh. The Wazuh dashboard is a customized OpenSearch dashboards distribution with the Wazuh plugin embedded, plus new configurations and customizations.
The new Wazuh dashboard is a flexible and intuitive web interface for mining, analyzing, and visualizing data. It provides out-of-the-box dashboards, allowing users to navigate the interface that now presents a renewed design with a new palette of colors. The versioning equivalent to the Wazuh manager will allow upgrades without the risk of incompatibilities.
An installation assistant wazuh-install.sh is available to users, allowing any type of installation, whether an all-in-one, single node, or multi-node. This is possible by simply defining a configuration file, with everything connected and secured, including random passwords and generated certificates. In addition, Debian and RPM packages for ppc64le architectures are made available to users.

Now, the agent is able to collect the installed packages inventory on Amazon Linux and Arch Linux, giving support to Vulnerability Detector for reporting vulnerability exposures. In addition, the Vulnerability Detector now manages a vulnerability inventory and produces alerts during the first agents scan and when a new vulnerability is either found or solved.
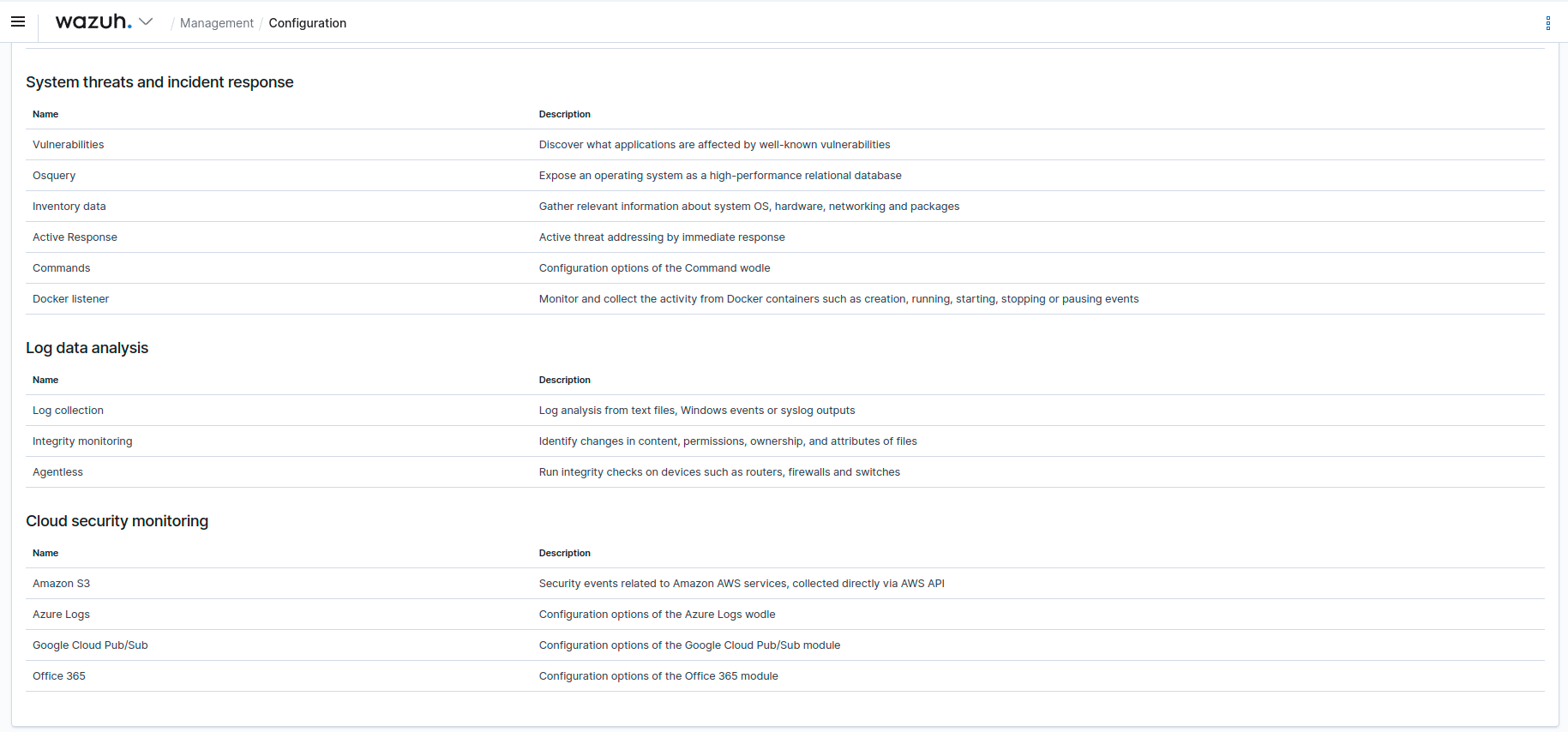
New integrations to collect auditing logs from Office 365 and GitHub are added to the agent in this new version. A side panel component that displays information about the active module of the Office 365 setup is introduced, and the Wazuh dashboard now includes events from Office 365. Moreover, Wazuh now supports Logcollector with native macOS logs (Unified Logging System), AWS S3 Server Access logs, and Google Cloud Storage buckets and access logs.
The RESTful API availability has been enhanced thanks to the API now using multiple processes. The performance of several API endpoints is also improved, which is especially palpable in large environments. Additionally, the agent batch is upgraded with an increased limit of agents per request and a new set of filters.
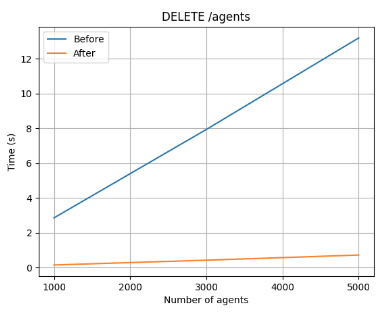
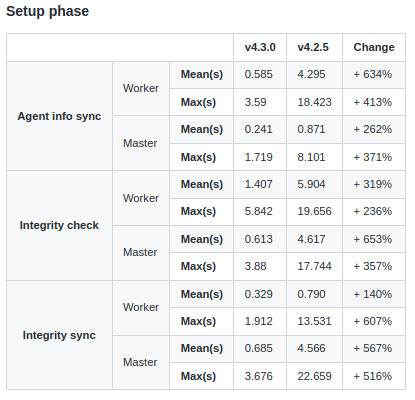
Wazuh v4.3.0 brings significant changes to the cluster, which now uses multiple processes to improve the performance. The results in the table below show a significant improvement for the cluster in this new version. The cluster tasks are performed 423% faster than in the previous version, approximately five times faster, while the RAM consumption decreased to a third. This performance is especially appreciable during the setup phase, where the cluster load is at its highest.
We want to mention another Wazuh 4.3.0 significant new feature. It is related to a new Intelligence tab added to the MITRE ATT&CK module. This tab provides further information about MITRE resources such as groups, mitigations, tactics, and techniques using the new Wazuh API endpoints. Additionally, the Framework tab is adapted to the new Wazuh API endpoints.
Finally, it is important to remark that we maintain support for all installation alternatives. Indeed we maintain and extend this support by adding more recent versions.
What's new
This release includes new features or enhancements.
Manager
#8178 Wazuh adds support for Arch Linux OS in Vulnerability Detector.
#8749 A log message in the
cluster.logfile is added to notify that wazuh-clusterd has been stopped.#9077 Wazuh improves API and cluster processes behavior by adding the PID of the
wazuh-clusterdprocesses and the API when these processes are started in foreground mode.#10492 Time calculation is added when extra information is requested to the
cluster_controlbinary.#9209 Wazuh adds a context variable to indicate the origin module in socket communication messages.
#9733 A unit tests for framework/core files is added to increase coverage.
#9204 A verbose mode is added in the wazuh-logtest tool.
#8830 Wazuh adds Vulnerability Detector support for Amazon Linux.
#10693 The new option
<force>to set the behavior is introduced when Authd finds conflicts on agent enrollment requests.#9099 Wazuh adds sanitizers to the unit tests execution.
#8237 Vulnerability Detector introduces vulnerability inventory.
The manager will only deliver alerts when new vulnerabilities are detected in agents or when they stop applying.
#11031 A mechanism to ensure the worker synchronization permissions are reset after a fixed period of time is added.
#11799 A new mechanism is now added to create and handle PID files for each child process of the API and cluster.
#8083 The internal handling of agent keys is changed in Remoted to speed up key reloading.
#7885 The option
<server>of the Syslog output now supports hostname resolution.#7763 The product's UNIX user and group are renamed to "wazuh".
#7865 The MITRE database is redesigned to provide full and searchable data.
#7358 The static fields related to FIM are ported to dynamic fields in Analysisd.
#8351 All randomly generated IDs used for cluster tasks are changed. Now, uuid4 is used to ensure IDs are not repeated.
#8873 The sendsync error log is Improved to provide more details of the used parameters.
#9708 The
walk_dirfunction is changed to be iterative instead of recursive.#10183 The Integrity sync behavior is refactored so that new synchronizations do not start until extra-valid files are processed.
#10101 Cluster synchronization is changed so that the content of the etc/shared folder is synchronized.
#8351 All XML file loads are changed. Now,
defusedxmllibrary is used to avoid possible XML-based attacks.#8535 Configuration validation from execq socket is changed to com socket.
#8392 The utils unittest is updated to improve
process_arrayfunction coverage.#8885 The
request_slicecalculation is changed to improve efficiency when accessing wazuh-db data.#9273 The retrieval of information from
wazuh-dbis improved to reach the optimum size in a single iteration.#9234 The way framework uses context cached functions and adds a note on context_cached docstring is optimized.
#9332 The framework regexes is improved to be more specific and less vulnerable.
#9423 The framework exceptions are unified for non-active agents.
#9433 The RBAC policies are changed to case insensitive.
#9548 Framework stats module is refactored into SDK and core components to comply with Wazuh framework code standards.
#10309 The size of the agents' chunks sent to the upgrade socket is changed to make the upgrade endpoints faster.
#9408 The rootcheck and syscheck SDK code are refactored to make it clearer.
#9738 The Azure-logs module is adapted to use Microsoft Graph API instead of Active Directory Graph API.
#8060 Analysisd now reconnects to Active Response if Remoted or Execd gets restarted.
#10335 Agent key polling now supports cluster environments.
#10357 The support of Vulnerability Detector is extended for Debian 11 (Bullseye).
#10326 The remoted performance with an agent TCP connection sending queue is improved.
#9093 Agent DB synchronization has been boosted by caching the last data checksum in Wazuh DB.
#8892 Logtest now scans new ruleset files when loading a new session.
#8237 CVE alerts by Vulnerability Detector now include the time of detection, severity, and score.
#10849 The manager startup is fixed when
<database_output>is enabled.- Improved cluster performance using multiprocessing:
#10767 The cluster
local_integritytask is changed to run in a separate process to improve overall performance.#10807 Now, the cluster communication with the database for agent information synchronization runs in a separate parallel process.
#10920 Now, the cluster processing of the extra-valid files in the master node is carried out in a separate parallel process.
#11328 The cluster's file compression task in the master node is carried out in a separate parallel process.
#11364 Now, the processing of Integrity files in worker nodes is carried out in a separate parallel process.
#11386 Use cluster and API single processing when the wazuh user doesn't have permissions to access
/dev/shm.
#12446 Support for Windows 11 is added in Vulnerability Detector.
#12491 The Ubuntu OVAL feed URL to security-metadata.canonical.com is changed.
#12652 Now,
Analysisdwarns about missing rule dependencies instead of rejecting the ruleset.#8399 The data reporting for Rootcheck scans in the agent_control tool has been deprecated.
#8846 The old framework functions used to calculate agent status are now removed.
Agent
#8016 An option is added to allow the agent to refresh the connection to the manager.
#8532 A new module to collect audit logs from GitHub is introduced.
#8461 FIM now expands wildcarded paths in the configuration on Windows agents.
#8754 FIM reloads wildcarded paths on full scans.
#8306 Wazuh adds a new
path_suffixoption to the AWS module configuration.#8331 A new
discard_regexoption is added to the AWS module configuration.#8482 Wazuh adds support for the S3 Server Access bucket type in the AWS module.
#9119 Wazuh adds support for Google Cloud Storage buckets using a new GCP module called
gcp-bucket.#9119 Wazuh adds support for Google Cloud Storage access logs to the
gcp-bucketmodule.#9420 Wazuh adds support for VPC endpoints in the AWS module.
#9279 Wazuh adds support for GCS access logs in the GCP module.
#10198 An AIM role session duration parameter to the AWS module is added.
#8826 Wazuh adds support for variables in SCA policies.
#7721 FIM now fills an audit rule file to support who-data, although Audit is in immutable mode.
#8957 An integration to collect audit logs from Office 365 is introduced.
#10168 A new field
DisplayVersionto Syscollector to help Vulnerability Detector match vulnerabilities for Windows is added.#10148 Wazuh adds support for macOS agent upgrade via WPK.
#8632 Wazuh adds Logcollector support for macOS logs (Unified Logging System).
#8381 The agent now reports the version of the running AIX operating system to the manager.
#8604 The reliability of the user ID parsing in FIM who-data mode on Linux is improved.
#10230 AWS
service_endpointparameter description to suit FIPS endpoints too is reworded.#5047 The support of Logcollector for MySQL 4.7 logs is extended.
#9887 Agents running on FreeBSD and OpenBSD now report their IP addresses.
#8202 The verbosity of FIM debugging logs is reduced.
#9992 The agent's IP resolution frequency has been limited to prevent high CPU load.
#10236 Syscollector is optimized to use less memory.
#10337 Wazuh adds support of ZscalerOS system information in the agent.
#10259 Syscollector is extended to collect missing Microsoft product hotfixes.
#10396 The osquery integration is updated to find the new osqueryd location as of version 5.0.
#9123 The internal FIM data handling has been simplified to find files by their path instead of their inode.
#9764 The WPK installer rollback on Windows is reimplemented.
#10208 Active responses for Windows agents now support native fields from Eventchannel.
#10651 Error logs by Logcollector when a file is missing have been changed to info logs.
#8724 The agent MSI installer for Windows now detects the platform version to install the default configuration.
#3659 Agent logs for inability to resolve the manager hostname now have info level.
#11276 An ID number to connection enrollment logs is added.
#10838 Standardized the use of the
only_logs_afterparameter in the external integration modules.#10900 The oscap module files are removed as it was already deprecated in version 4.0.0.
#12150 DockerListener integration shebang is updated to python3 for Wazuh agents.
#12779 The ico and jpg files have been updated with the new Wazuh logo for the Windows installer.
RESTful API
#7988 A new
PUT /agents/reconnectendpoint is added to force agents reconnection to the manager.#6761 The
selectparameter is added to theGET /security/users,GET /security/roles,GET /security/rulesandGET /security/policiesendpoints.#8100 The type and status filters are added to
GET /vulnerability/{agent_id}endpoint.#7490 An option is added to configure SSL ciphers.
#8919 An option is added to configure the maximum response time of the API.
#8945 A new
DELETE /rootcheck/{agent_id}endpoint is added.#9028 A new
GET /vulnerability/{agent_id}/last_scanendpoint is added to check the latest vulnerability scan of an agent.#9028 A new
cvssandseverityfields and filters are added toGET /vulnerability/{agent_id}endpoint.#9100 An option is added to configure the maximum allowed API upload size.
#9142 A new unit and integration tests for API models are added.
#9077 A message with the PID of
wazuh-apidprocess when launched in foreground mode is added.#9144 Wazuh adds
external id,source, andurlto the MITRE endpoints responses.#9297 Custom healthchecks for legacy agents are added in API integration tests, improving maintainability.
#9914 A new unit test for the API python module is added to increase coverage.
#10238 A docker logs separately in API integration tests environment are added to get cleaner reports.
#10437 A new
disconnection_timefield is added toGET /agentsresponse.#10457 New filters are added to agents' upgrade endpoints.
#8288 New MITRE API endpoints and framework functions are added to access all the MITRE information.
#10947 Show agent-info permissions flag is added when using cluster_control and in the
GET /cluster/healthcheckAPI endpoint.#11931 Save agents' ossec.log if an API integration test fails.
#12085 POST /security/user/authenticate/run_as endpoint is added to API bruteforce blocking system.
#12638 A new API endpoint is added to obtain summaries of agent vulnerabilities' inventory items.
#12727 The new fields external_references, condition, title, published, and updated are added to GET /vulnerability/{agent_id} API endpoint.
#13262 The possibility to include strings in brackets in values of the q parameter is added.
#7490 The SSL protocol configuration parameter is renamed.
#8827 The API spec examples and JSON body examples are reviewed and updated.
- The performance of several API endpoints is improved. This is especially appreciable in environments with a big number of agents:
#8937 The endpoint parameter
PUT /agents/groupis improved.#8938 The endpoint parameter
PUT /agents/restartis improved.#8950 The endpoint parameter
DELETE /agentsis improved.#8959 The endpoint parameter
PUT /rootcheckis improved.#8966 The endpoint parameter
PUT /syscheckis improved.#9046 The endpoint parameter
DELETE /groupsis improved and API response is changed to be more consistent.
#8945 The endpoint parameter
DELETE /rootcheckis changed toDELETE /experimental/rootcheck.#9012 The time it takes for
wazuh-apidprocess is reduced to check its configuration when using the -t parameter.#9019 The malfunction in the
sortparameter of syscollector endpoints is fixed.#9113 The API integration tests stability when failing in entrypoint is improved.
#9228 The SCA API integration tests dynamic to validate responses coming from any agent version are fixed.
#9227 All the date fields in the API responses to use ISO8601 are refactored and standardized.
#9263 The
Serverheader from API HTTP responses is removed.#9371 The JWT implementation by replacing HS256 signing algorithm with RS256 is improved.
#10009 The limit of agents to upgrade using the API upgrade endpoints is removed.
#10158 The Windows agent's FIM responses are changed to return permissions as JSON.
#10389 The API endpoints are adapted to changes in
wazuh-authddaemonforceparameter.#10512 The
use_only_authdAPI configuration option and related functionality are deprecated.wazuh-authdwill always be required for creating and removing agents.#10745 The API validators and related unit tests are improved.
#10905 The specific module healthchecks in API integration tests environment is improved.
#10916 The thread pool executors for process pool executors to improve API availability is changed.
#11410 The HTTPS options to use files instead of relative paths are changed.
#8599 The select parameter from GET /agents/stats/distinct endpoint is removed.
#8099 The
GET /mitreendpoint is removed.#11410 The option to set the log
pathin the configuration is deprecated.
Ruleset
#11306 Carbanak detection rules are added.
#11309 Cisco FTD rules and decoders are added.
#11284 Decoders for AWS EKS service are added.
#11394 F5 BIG IP ruleset is added.
#11191 GCP VPC storage, firewall, and flow rules are added.
#11323 GitLab 12.0 ruleset are added.
#11289 Microsoft Exchange Server rules and decoders are added.
#11390 Microsoft Windows persistence by using registry keys detection is added.
#11274 Oracle Database 12c rules and decoders are added.
#8476 Rules for Carbanak step 1.A - User Execution: Malicious files are added.
#11212 Rules for Carbanak step 2.A - Local discoveries are added.
#9075 Rules for Carbanak step 2.B - Screen capture is added.
#9097 Rules for Carbanak step 5.B - Lateral movement via SSH are added.
#11342 Rules for Carbanak step 9.A - User monitoring is added.
#11373 Rules for Cloudflare WAF are added.
#11013 Ruleset for ESET Remote console is added.
#8532 Ruleset for GitHub audit logs are added.
#11137 Ruleset for Palo Alto v8.X - v10.X are added.
#11431 SCA policy for Amazon Linux 1 is added.
#11480 SCA policy for Amazon Linux 2 is added.
#7035 SCA policy for apple macOS 10.14 Mojave is added.
#7036 SCA policy for apple macOS 10.15 Catalina is added.
#11454 SCA policy for macOS Big Sur is added.
#11250 SCA policy for Microsoft IIS 10 is added.
#11249 SCA policy for Microsoft SQL 2016 is added.
#11247 SCA policy for Mongo Database 3.6 is added.
#11248 SCA policy for NGINX is added.
#11245 SCA policy for Oracle Database 19c is added.
#11154 SCA policy for PostgreSQL 13 is added.
#11223 SCA policy for SUSE Linux Enterprise Server 15
#11432 SCA policy for Ubuntu 14 is added.
#11452 SCA policy for Ubuntu 16 is added.
#11453 SCA policy for Ubuntu 18 is added.
#11430 SCA policy for Ubuntu 20 is added.
#11286 SCA policy for Solaris 11.4 is added.
#11122 Sophos UTM Firewall ruleset is added.
#11357 Wazuh-api ruleset is added.
#11016 Audit rules are updated.
#11177 AWS s3 ruleset is updated.
#11344 Exim 4 decoder and rules to latest format is updated.
#8738 MITRE DB with the latest MITRE JSON specification is updated.
#11255 Multiple rules to remove alert_by_email option are updated.
#11795 NextCloud ruleset is updated.
#11232 ProFTPD decoder is updated.
#11242 RedHat Enterprise Linux 8 SCA up to version 1.0.1 is updated.
#11100 Rules and decoders for FortiNet products are updated.
#11429 SCA policy for CentOS 7 is updated.
#8751 SCA policy for CentOS 8 is updated.
#11263 SonicWall decoder values are fixed.
#11388 SSHD ruleset is updated.
#8552 From file 0580-win-security_rules.xml, rules with id 60198 and 60199 are moved to file 0585-win-application_rules.xml, with rule ids 61071 and 61072 respectively.
Wazuh Kibana plugin
#3557 GitHub and Office365 modules are added.
#3541 A new
Panelmodule tab for GitHub and Office365 modules is added.#3639 Wazuh adds the ability to filter the results for the
Network Portstable in theInventory datasection.#3324 A new endpoint service is added to collect the frontend logs into a file.
#3327 #3321 #3367 #3373 #3374 #3390 #3410 #3408 #3429 #3427 #3417 #3462 #3451 #3442 #3480 #3472 #3434 #3392 #3404 #3432 #3415 #3469 #3448 #3465 #3464 #3478 The frontend handle errors strategy is improved: UI, Toasts, console log, and log in file.
#3368 #3344 #3726 Intelligence tab is added to the MITRE ATT&CK module.
#3424 Sample data for office365 events are added.
#3475 A separate component to check for sample data is created.
#3506 A new hook for getting value suggestions is added.
#3531 Dynamic simple filters and simple GitHub filters fields are added.
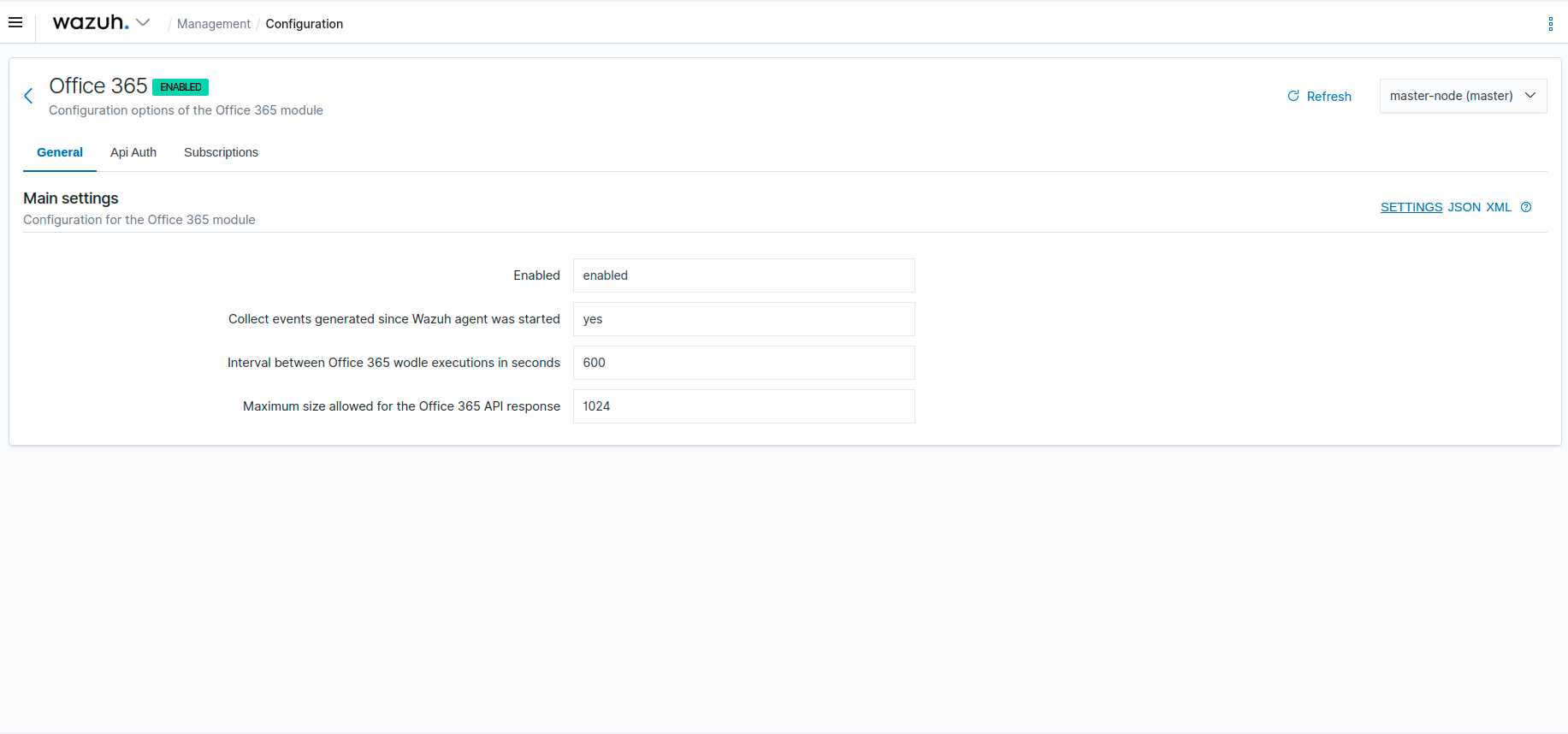
#3524 Configuration viewer for Module Office 365 is added to the Configuration section of the Management menu.
#3518 A side panel component that displays information about the active module of the Office 365 setup is introduced.
#3533 Specifics and custom filters for Office 365 search bar are added.
#3544 Pagination and filter are added to drilldown tables at the Office pannel.
#3568 Simple filters change between panel and drilldown panel.
#3525 New fields are added to the Inventory table and Flyout Details.
#3691 Columns selector are added in agents table.
#3742 A new workflow is added for creating wazuh packages.
#3783
templateandfieldschecks in the health check run correctly according to the app configuration.#3804 A toast message lets you know when there is an error creating a new group.
#3846 A step to start the agent is added to the deploy new Windows agent guide.
#3893 3 new panels are added to Vulnerabilities/Inventory.
#3893 A new field of Vulnerabilities is added to the details flyout.
#3924 Missing fields used in visualizations are added to the known fields related to alerts.
#3946 A troubleshooting link is added to the "index pattern was refreshed" toast.
#4041 More number options are added to the tables widget in Modules -> "Mitre".
#3121 Ossec to wazuh is changed in all sample-data files.
#3279 Empty fields are modified in FIM tables and
syscheck.value_namein discovery now shows an empty tag for visual clarity.#3346 The MITRE tactics and techniques resources are adapted to use the API endpoints.
#3517 The filterManager subscription is moved to the hook useFilterManager.
#3529 Filter is changed from "is" to "is one of" in the custom search bar.
#3494 Refactor
modules-defaults.jsto define what buttons and components are rendered in each module tab.#3663 #3806 The deprecated and new references for the
authdconfiguration are updated.#3549 Time subscription is added to the Discover component.
#3446 Testing logs using the Ruletest Test don't display the rule information if not matching a rule.
#3649 The format permissions are changed in the FIM inventory.
#3686 #3728 The request to agents that do not return data is now changed to avoid unnecessary heavy load requests.
#3788 Rebranding. Replaced the brand logos, set module icons with brand colors
#3795 User used for sample data management is changed.
#3792 The agent install codeblock copy button and PowerShell terminal warning is changed.
#3811 The naming related to the plugin platform from a specific one to a generic one using the term plugin platform is replaced.
#3893 Dashboard tab of Vulnerabilities module is removed, three new panels to Vulnerabilities/Inventory are added, and details Flyout fields are enhanced.
#3908 Now, all available fields are shown in the Discover Details Flyout table. Furthermore, the open row icon width is fixed in the first column when the table has a few columns.
#3924 Missing fields used in visualizations to the known fields related to alerts are added.
#3946 Troubleshooting link to "index pattern was refreshed" toast is added.
#3196 The table in Vulnerabilities/Inventory is refactored.
#3949 Google Groups app icons are changed.
#3857 Sorting for Agents or Configuration checksum column in the table of Management/Groups is removed due to this is not supported by the API.
Wazuh Splunk app
Support for Wazuh 4.3.0
#1166 Alias field is added to API to facilitate distinguishing between different managers.
#1126 Ensure backwards compatibility.
#1148 A Security Section is added to manage security related configurations.
#1171 Crud Policies are added to the security section.
#1168 Crud Roles are added to the security section.
#1169 Crud Role Mapping is added to the security section.
#1173 Crud Users is added to the security section.
#1147 Created a permissions validation service.
#1164 Implemented the access control on the App's views.
#1155 Implemented a service to fetch Wazuh's users and their roles.
#1156 Implemented a server to fetch Splunk's users and their roles.
#1149 A run_as checkbox is added to the API configuration.
#1174 The ability to use the Authorization Context login method is added.
#1228 Extensions now can only be changed by Splunk Admins.
#1186 Wazuh rebranding.
#1172 Deprecated authd options are updated.
#1236 Refactored branding color styles to improve maintainability.
#1243 Wazuh API's name is changed to its alias in the quick settings selector.
Other
#10247 External SQLite library dependency is upgraded to version 3.36.
#10247 External BerkeleyDB library dependency is upgraded to version 18.1.40.
#10247 External OpenSSL library dependency is upgraded to version 1.1.1l.
#10927 External Google Test library dependency is upgraded to version 1.11.
#11436 External Aiohttp library dependency is upgraded to version 3.8.1.
#11436 External Werkzeug library dependency is upgraded to version 2.0.2.
#11436 Embedded Python is upgraded to version 3.9.9.
Packages
#1518 Changed default attributes in Wazuh dashboard package. (A wazuh-dashboard new package with -2 revision was released)
#1496 Hide passwords in log file.
#1500 The dashboard IP messages are fixed.
#1499 Improved APT locked message and retry time.
#1497 Unhandled promise for the dashboard is fixed.
#1494 Update ova
motdmessage 4.3.#1471 Remove service disable from RPM and Debian packages.
#1471 Disabled multitenancy by default in the dashboard and changed the app default route.
#1434 Set as a warning the unhandled promises in the Wazuh dashboard.
#1395 Remove IP message from OVA.
#1390 Remove demo certificates from indexer and dashboard packages.
#1307 Add centos8 vault repository due to EOL.
#1302 The user deletion warning RPM manager is fixed.
#1292 The issue where Solaris 11 was not executed in clean installations is fixed.
#1280 The error where Wazuh could continue running after uninstalling is fixed.
#1274 The AIX partition size is fixed.
#1147 The Solaris 11 upgrade from previous packages is fixed.
#1126 Add new GCloud integration files to Solaris 11.
#689 Update SPECS.
#888 An error in CentOS 5 building is fixed.
#944 Add new SCA files to Solaris 11.
#915 Improved support for ppc64le on CentOS and Debian.
#1005 The error with
wazuhuser in Debian packages is fixed.#1023 Add ossec user and group during compilation.
#1261 Merge Wazuh Dashboard v3 #.
#1256 The certs permissions in RPM is fixed.
#1208 Kibana app now supports
pluginPlatform.versionproperty in the app manifest.#1162 The certificates creation using parameters 4.3 is fixed.
#1193 The Archlinux package generation parameters 4.3 are fixed.
#1132 Add new 2.17.1 log4j mitigation version 4.3.
#1123 The client keys Ownership for 3.7.x and previous versions is fixed.
#1106 A new log4j remediation 4.3 is added.
#1112 The Linux
wpkgeneration 4.3 is fixed.#1096 Add log4j mitigation 4.3.
#1086 Increase admin.pem cert expiration date 4.3.
#1078 Remove wazuh user from unattended/OVA/AMI 4.3.
#1074 The
groupdelossec error during upgrade to 4.3.0 is fixed.#1067 The curl kibana.yml 4.3 is fixed.
#1060 Remove
restore-permissions.shfrom Debian Packages.#1048 Bump unattended 4.3.0.
#1012 Removed cd usages in unattended installer and fixed uninstaller 4.3.
#1023 Add ossec user and group during compilation.
#1020 Removed warning and added text in
wazuh-passwords-tool.shfinal message 4.3.
Resolved issues
This release resolves known issues.
Manager
Reference |
Description |
|---|---|
A memory defect is fixed in Remoted when closing connection handles. |
|
A timing problem is fixed in the manager that might prevent Analysisd from sending Active responses to agents. |
|
A bug in Analysisd that did not apply field lookup in rules that overwrite other ones is fixed. |
|
The manager is now prevented from leaving dangling agent database files. |
|
The remediation message for error code 6004 is updated. |
|
A bug when deleting non-existing users or roles in the security SDK is now fixed. |
|
A bug with |
|
Wrong exceptions with wdb pagination mechanism are fixed. |
|
An error when loading some rules with the |
|
The |
|
An error in the API configuration when using the |
|
The |
|
An issue with duplicated logs in Azure-logs module is fixed and several improvements are applied to it. |
|
The query parameter validation is fixed to allow usage of special chars in Azure module. |
|
A bug running |
|
Cluster is now allowed to send and receive messages with a size higher than request_chunk. |
|
A bug that caused |
|
Race condition due to lack of atomicity in the cluster synchronization mechanism is fixed. |
|
A bug when displaying the dates of the cluster tasks that have not finished yet is fixed. Now, |
|
Missing field |
|
A typo in the SSH Integrity Check script for Agentless is fixed. |
|
Multiple race conditions in Remoted are fixed. |
|
The manager agent database is fixed to prevent dangling entries from removed agents. |
|
The alerts generated by FIM when a lookup operation on a SID fails are fixed. |
|
A bug that caused cluster agent-groups files to be synchronized multiple times unnecessarily is fixed. |
|
An issue in Wazuh DB that compiled the SQL statements multiple times unnecessarily is fixed. |
|
A crash in Analysisd when setting Active Response with agent_id = 0 is fixed. |
|
An uninitialized Blowfish encryption structure warning is fixed. |
|
A memory overrun hazard in Vulnerability Detector is fixed. |
|
A bug when using a limit parameter higher than the total number of objects in the wazuh-db queries is fixed. |
|
A false positive for MySQL in Vulnerability Detector is prevented. |
|
The segmentation fault when the wrong configuration is set is fixed. |
|
A false positive in Vulnerability Detector is fixed when scanning OVAl for Ubuntu Xenial and Bionic. |
|
An argument injection hazard is fixed in the Pagerduty integration script. Thank you Jose Maria Zaragoza (@JoseMariaZ) for reporting this issue. |
|
Memory leaks in the feed parser at Vulnerability Detector are fixed. Architecture data member from the RHEL 5 feed. RHSA items containing no CVEs. Unused RHSA data member when parsing Debian feeds. |
|
Now, Authd ignores the pipe signal if Wazuh DB gets closed. |
|
A buffer handling bug is fixed in Remoted that left the syslog TCP server stuck. |
|
A memory leak in Vulnerability Detector is fixed when discarding kernel packages. |
|
A memory leak at wazuh-logtest-legacy is fixed when matching a level-0 rule. |
|
Now, the cluster is disabled by default when the "disabled" tag is not included. |
|
A bug in the Vulnerability Detector CPE helper that may lead to producing false positives about Firefox ESR is fixed. |
Agent
Reference |
Description |
|---|---|
A bug in FIM that did not allow monitoring new directories in real-time mode if the limit was reached at some point is fixed. |
|
A bug in FIM that threw an error when a query to the internal database returned no data is fixed. |
|
An error where the IP address was being returned along with the port for Amazon NLB service is fixed. |
|
AWS module is fixed to properly handle the exception raised when processing a folder without logs. |
|
A bug with the AWS module when pagination is needed in the bucket is fixed. |
|
An error with the ipGeoLocation field in AWS Macie logs id fixed. |
|
An incorrect debug message in the GCloud integration module is changed. |
|
Data race conditions are fixed in FIM. |
|
A wrong command line display in the Syscollector process report on Windows is fixed. |
|
An issue that causes shutdown when agentd or analysisd is stopped is fixed. |
|
Wrong keepalive message from the agent when file merged.mg is missing is fixed. |
|
Missing logs from the Windows agent when it's getting stopped are fixed. |
|
Missing packages reporting in Syscollector for macOS due to empty architecture data is fixed. |
|
FIM on Linux to parse audit rules with multiple keys for who-data is fixed. |
|
Windows 11 version collection in the agent is fixed. |
|
Missing Eventchannel location in Logcollector configuration reporting is fixed. |
|
CloudWatch Logs integration is updated to avoid crashing when AWS raises Throttling errors. |
|
AWS modules' log file filtering is fixed when there are logs with and without a prefix mixed in a bucket. |
|
A bug on the installation script that made upgrades not to update the code of the external integration modules id fixed. |
|
An issue with the AWS integration module trying to parse manually created folders as if they were files is fixed. |
|
Some installation errors in OS with no subversion are fixed. |
|
A typo in an error log about enrollment SSL certificate is fixed. |
|
A unit tests for Windows agent when built on MinGW 10 is fixed. |
|
Windows agent compilation warnings are fixed. |
|
The OS version reported by the agent on OpenSUSE Tumbleweed is fixed. |
|
The Syscollector is prevented from truncating the open port inode numbers on Linux. |
|
An agent auto-restart on configuration changes, when started via |
|
A bug in the AWS module resulting in unnecessary API calls when trying to obtain the different Account IDs for the bucket is fixed. |
|
Azure integration's configuration parsing to allow omitting optional parameters is fixed. |
|
Azure Storage credentials validation bug is fixed. |
|
The read of the hostname in the installation process for openSUSE is fixed. |
|
The graceful shutdown when the agent loses connection is fixed. |
|
The error "Unable to set server IP address" is fixed on the Windows agent. |
|
The reparse option is fixed in the AWS VPCFlow and Config integrations. |
|
The way the AWS Config integration parses the dates used to search in the database for previous records was fixed. |
|
Now, Logcollector audit format parses logs with a custom name_format. |
|
An issue with the Agent bootstrap is fixed, it might lead to a startup timeout when it cannot resolve a manager hostname. |
|
A bug in the agent's leaky bucket throughput regulator that could leave it stuck if the time is advanced on Windows is fixed. |
RESTful API
Reference |
Description |
|---|---|
An inconsistency in RBAC resources for |
|
The handling of an API error message occurring when Wazuh is started with a wrong |
|
A bug with the |
|
The description of |
|
API incorrect path in remediation message when a maximum number of requests per minute is reached is fixed. |
|
Agents' healthcheck error in the API integration test environment is fixed. |
|
A bug with |
|
A bug with RBAC |
|
Temporal development keys and values from |
|
Several errors when filtering by dates are fixed. |
|
The limit in some endpoints like |
|
A bug with the |
|
Wrong values of |
|
The way how the API integration testing environment checks that wazuh-apid daemon is running before starting the tests is fixed. |
|
A healthcheck is added to verify that |
|
The API integration test healthcheck used in the |
|
An error with |
|
An RBAC experimental API integration test expecting a 1760 code in implicit requests is fixed. |
|
A cluster race condition that caused the API integration test to randomly fail is fixed. |
|
The |
|
The |
|
The agent endpoints q parameter to allow more operators when filtering by groups is fixed. |
|
The API integration tests related to rule, decoder, and task endpoints are fixed. |
|
Exceptions handling when starting the Wazuh API service is improved. |
|
The race condition while creating RBAC database is fixed. |
|
The API integration tests failures caused by race conditions are fixed. |
Ruleset
Reference |
Description |
|---|---|
Bad characters are fixed on rules 60908 and 60884 - win-application rules. |
|
Microsoft logs rules are fixed. |
|
PHP rules for MITRE and groups are fixed. |
|
Rules id for Microsoft Windows PowerShell is fixed. |
Wazuh Kibana plugin
Reference |
Description |
|---|---|
The creation of log files is fixed. |
|
The double fetching alerts count when pinning/unpinning the agent in MITRE ATT&CK/Framework is fixed. |
|
A refactor of the query Config is changed from Angular to React. |
|
The flyout closing when dragging and releasing mouse event outside the Rule-test and Decoder-test flyout is fixed. |
|
Now Wazuh notifies you when you are registering an agent without permission. |
|
Not used |
|
The code overflows over the line numbers in the API Console editor is fixed. |
|
The issue that avoids opening the main menu when changing the selected API or index pattern is fixed. |
|
An error message in conf management is fixed. |
|
An issue related to the size API selector when the name is too long is fixed. |
|
An error when editing a rule or decoder is fixed. |
|
An issue about the index pattern selector doesn't display the ignored index patterns is fixed. |
|
An error in /Management/Configuration when the cluster is disabled is fixed. |
|
An issue related to pinned filters removed when accessing the |
|
Multi-select component searcher handler is fixed. |
|
The order logs properly in Management/Logs are fixed. |
|
The Wazuh API requests to |
|
Missing MITRE tactics are fixed. |
|
The CDB list views not working with IPv6 is fixed. |
|
The bad requests using the Console tool to |
|
An issue related to the group agent management table does not update on error is fixed. |
|
An issue about not showing packages details in agent inventory for a FreeBSD agent SO is fixed. |
|
Wazuh token deleted twice is fixed. |
|
The handler of an error on dev-tools is fixed. |
|
The compatibility with wazuh 4.3 - kibana 7.13.4 is fixed. |
|
The registry values without agent pinned in FIM>Events are fixed. |
|
The breadcrumbs style compatibility for Kibana 7.14.2 is fixed. |
|
The security alerts table when filters change is fixed. |
|
An error that shows we're using X-Pack when we have Basic is fixed. |
|
The blank screen in Kibana 7.10.2 is fixed. |
|
Related decoders file link errors when users click on it are fixed. |
|
Flyouts in Kibana 7.14.2 are fixed. |
|
The bug of index patterns in health-check due to a bad copy of a PR is fixed. |
|
Styles and behavior of button filter in the flyout of |
|
The height of the |
|
The clearing of the query filter that doesn't update the data in Office 365 and GitHub Panel tab is updated. |
|
Wrong daemons in the filter list are fixed. |
|
A bug when creating a filename with spaces that throws a bad error is fixed. |
|
A bug in security User flyout nonexistent unsubmitted changes warning is fixed. |
|
The redirect to a new tab when clicking on a link is fixed. |
|
Missing settings in |
|
The |
|
The regex lookahead and lookbehind for safari are fixed. |
|
Vulnerabilities Inventory flyout details filters are fixed. |
|
Removed API selector toggle from Settings menu since it performed no useful function. |
|
Dashboard PDF report error when switching pinned agent state is fixed. |
|
The rendering of the command to deploy a new Windows agent not working in some Kibana versions now works correctly. |
|
Action buttons no longer overlay with the request text in Tools/API Console. |
|
A bug in Rule ID value in reporting tables related to top results is now fixed. |
|
An issue with github/office365 multi-select filters suggested values is now fixed. |
|
We fixed an issue related to updating the aggregation data of the Panel section when changing the time filter |
|
We removed the button to remove an agent for a group in the agents' table when it is the default group. |
|
Adding a single agent to a group is fixed. |
|
The implicit filters from the search bar can be removable. |
|
Office365/Github module the side panel tab are fixed. |
|
No wrap text in MITRE ATT&CK intelligence table is fixed. |
|
The visualization tooltip position is fixed. |
|
github/office365 multi-select filters suggested values is fixed. |
|
The styles on the evolution card are fixed. |
|
Internal user no longer needs permission to make x-pack detection request. |
|
Agents details card style is fixed. |
|
Agents evolutions card is fixed. |
|
Routing redirection in events documents discovers links are fixed. |
|
Health-check is fixed. |
|
The table of Vulnerabilities/Inventory doesn't reload when changing the selected agent is fixed. |
|
The issue with the table in Modules/Vulnerabilities/Inventory that doesn't refresh when changing the selected agent is fixed. |
|
An asynchronism issue when multiple fields are missing in the Events view rows details is solved. |
|
A rendering problem in the map visualizations is fixed. |
|
Parse error when using # character not at the beginning of the line. |
|
The rule.mitre.id cell enhancement that doesn't support values with sub techniques is solved. |
|
An error when changing the selected time in some flyouts is fixed. |
|
An issue related to the user can log out when the Kibana server has a basepath configurated is solved. |
|
A fatal cron-job error when Wazuh API is down is fixed. |
Wazuh Splunk app
Reference |
Description |
|---|---|
Long agent names no longer overflow in the overview page. |
|
An issue that occurred when saving rules or decoders files is now fixed. |
|
An issue with unnecessary table requests when resizing the browser window is fixed. |
|
Agent counters are now centered correctly. |
|
Users can no longer add new agents without the right "create" permissions. |
|
The navigation bar for Security options no longer overlaps with the background header. |
|
An error when the agents view is re-initialized is now fixed. |
|
This issue is fixed and you can now see actions after adding the first API. |
|
The Agent status chart data is shown correctly. |
|
The Agent status graph is fixed to show the correct amount of agents. |
|
The sorting on the Groups table columns is fixed. |
|
Non-sortable columns are fixed on the Security section tables. |
|
Group report disabled configuration parameter error is fixed. |
|
Import CDB list file is fixed. |
|
Header menu height style issue is fixed. |
|
An error is fixed on the search string used on the Alerts Summary table in the Overview > Vulnerability section, causing the table to show no data. |
Others
Reference |
Description |
|---|---|
Error detection in the CURL helper library is fixed. |
|
External Berkeley DB library support for GCC 11 is fixed. |
|
An installation error due to missing OS minor version on CentOS Stream is fixed. |
|
An installation error due to a missing command hostname on OpenSUSE Tumbleweed is fixed. |
Changelogs
More details about these changes are provided in the changelog of each component: