Cloud Security Posture Management
Cloud Security Posture Management (CSPM) is important in ensuring the security and compliance of cloud environments. The potential for security misconfigurations increases in cloud computing, where organizations can quickly and easily provision, configure, and modify cloud resources. These security issues can arise due to mismanagement of permissions, gaps in network configurations, and various other factors.
Cloud Security Posture Management addresses this challenge by continuously monitoring and assessing cloud workloads to identify misconfigurations, vulnerabilities, and potential risks. It also provides remediation steps to rectify potential security risks, thereby enhancing the overall security posture of the cloud environment.
Wazuh is a free, open source, enterprise-grade security monitoring platform that provides comprehensive protection for cloud, on-premises, containerized, and virtualized environments. This section demonstrates how to use Wazuh to review posture security on the Google Cloud.
Integrating Wazuh with Google Cloud
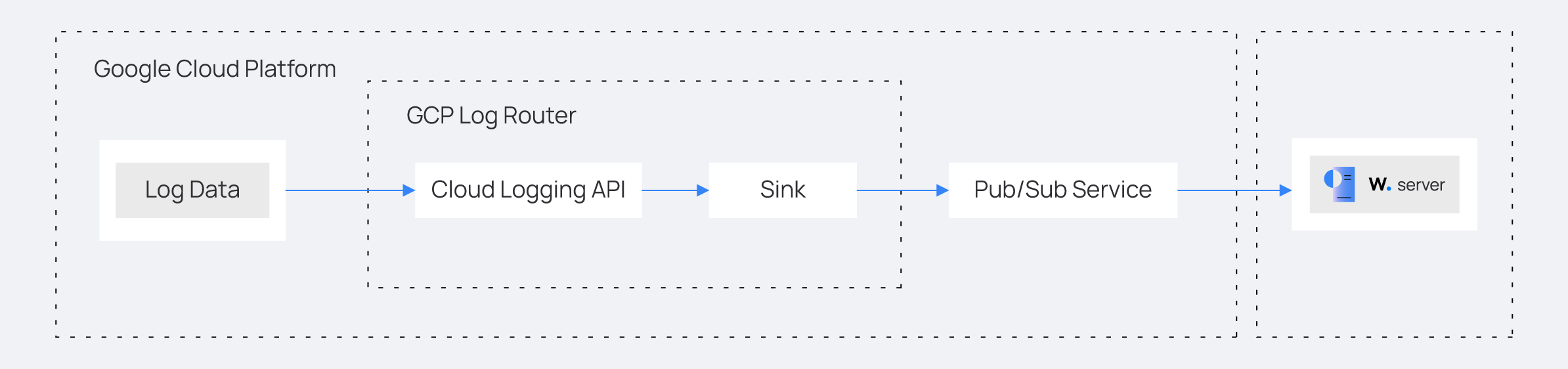
Wazuh integrates with Google Cloud using the Google Cloud publisher and subscriber service (Google Cloud Pub/Sub). Google Cloud Pub/Sub is a messaging service that helps you send and receive log data between applications. Wazuh provides an integration module for Google Cloud that fetches logs from the Pub/Sub service.
Google Cloud
Configuring the Google Cloud account
Create a new Google Cloud project and a service account that enables the Wazuh Google Cloud module to pull log data from the Google Pub/Sub service. Once this is done, configure the Pub/Sub and the Sink services. The Sink service routes cloud security posture logs from the central Google Cloud Logging service to the Pub/Sub service.
Follow the steps below to perform the configuration.
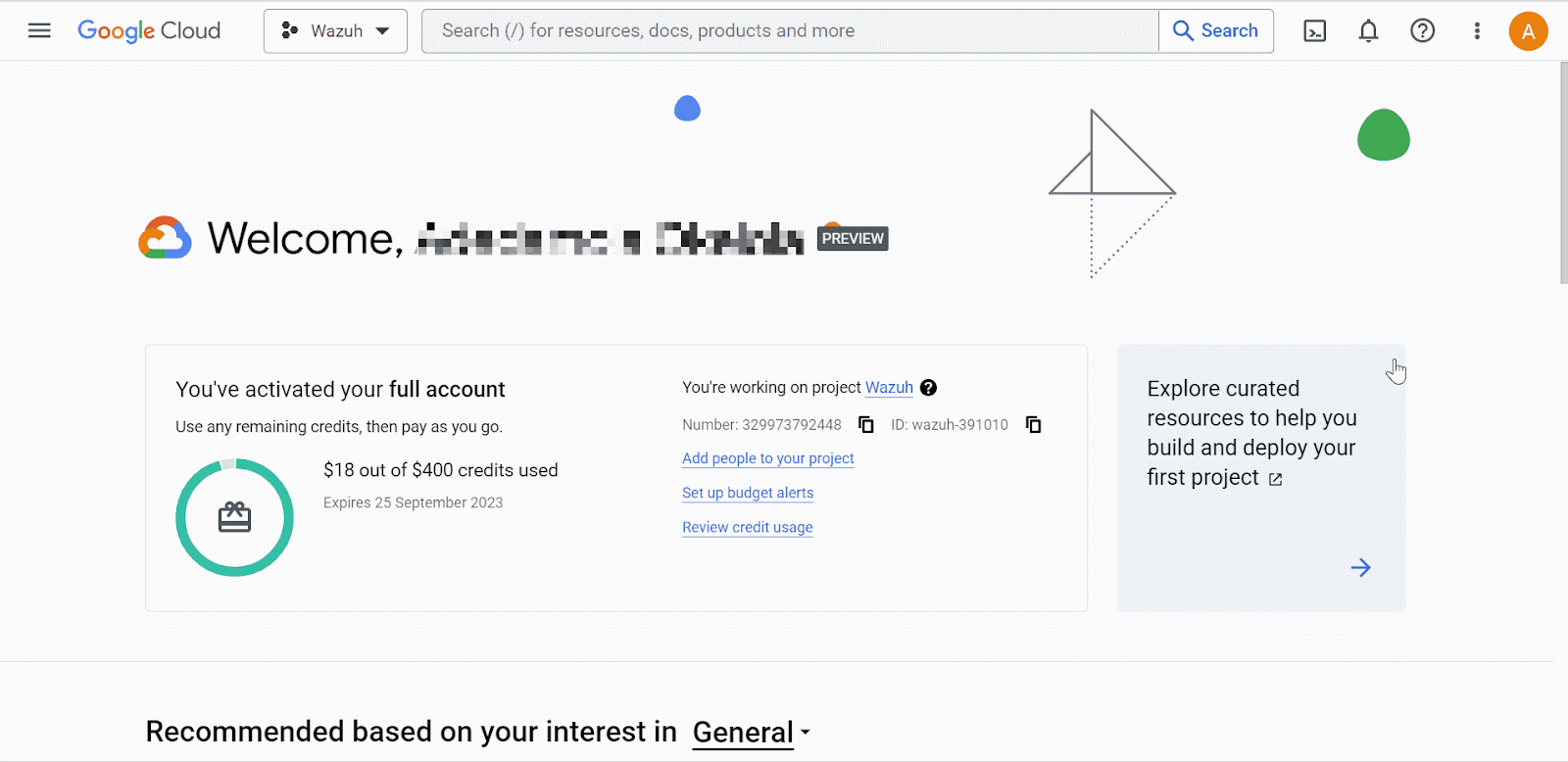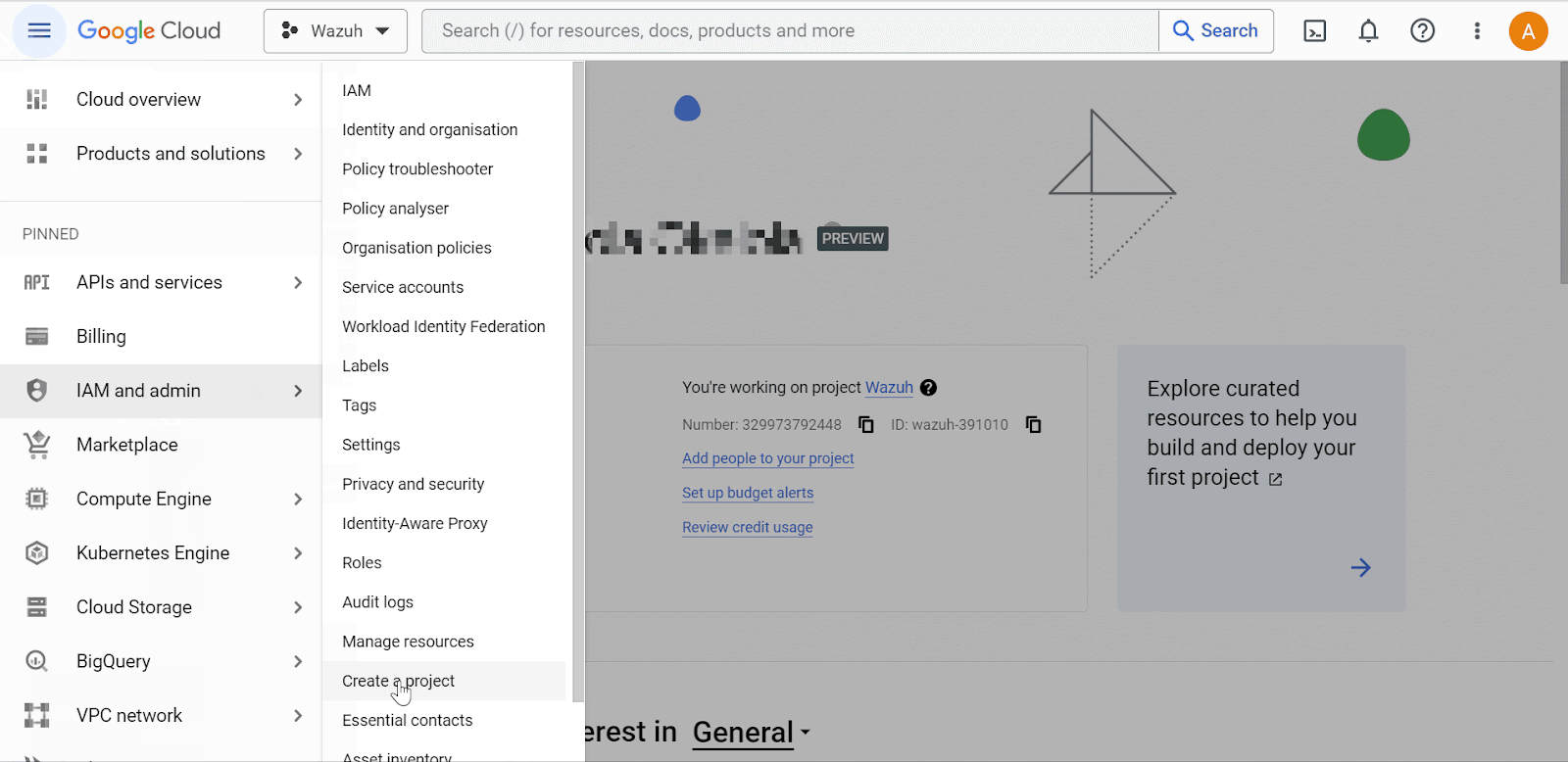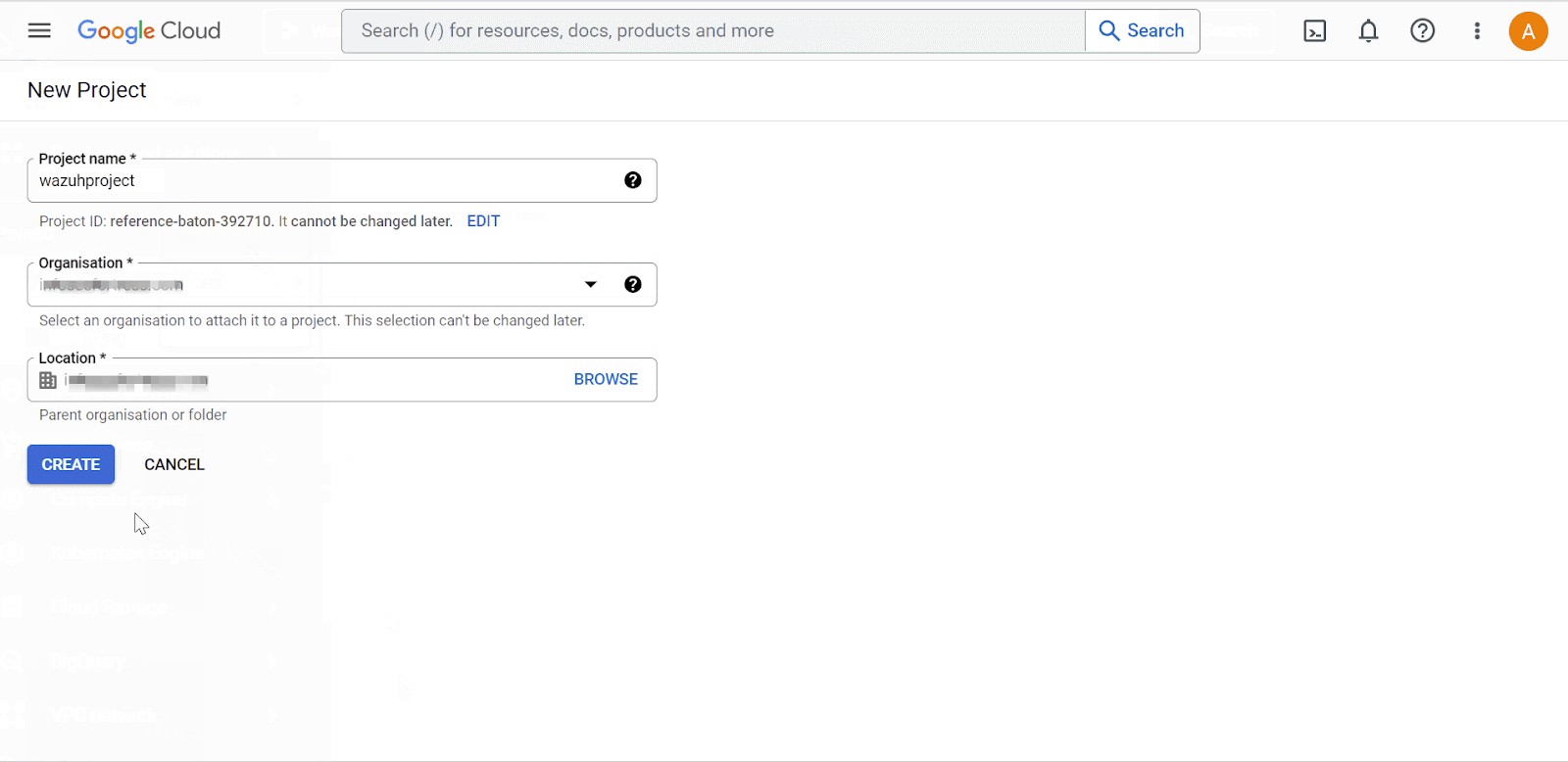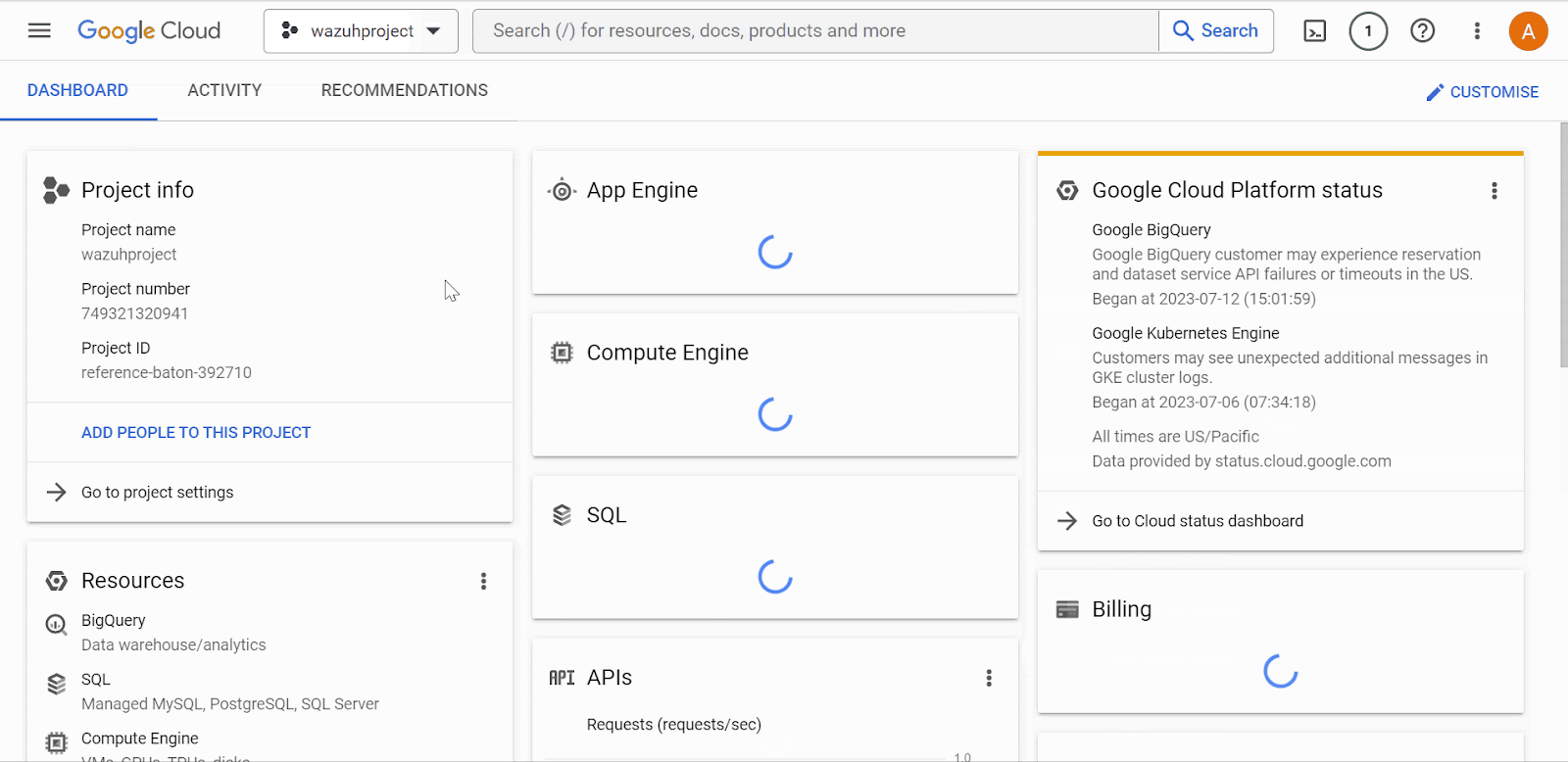
Create a new Google Cloud project. Take note of the project ID.
Where:
Project name is the name given to the project.
Organization is the name of the Google Cloud organization.
Go to the IAM and admin drop-down menu and select Service accounts to create a new service account. On the service accounts creation page, add the
Pub/Sub PublisherandPub/Sub Subscriberroles to the account.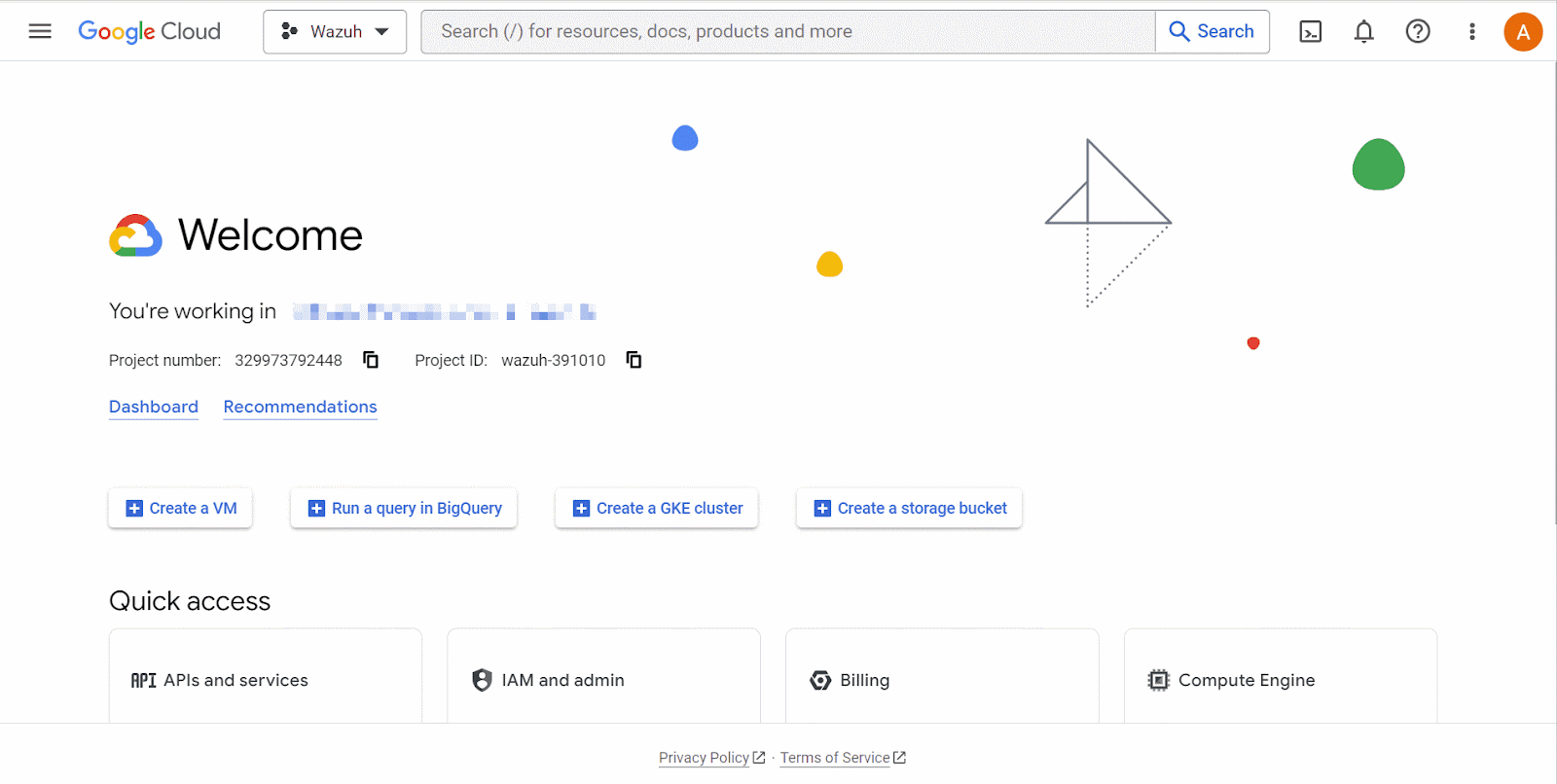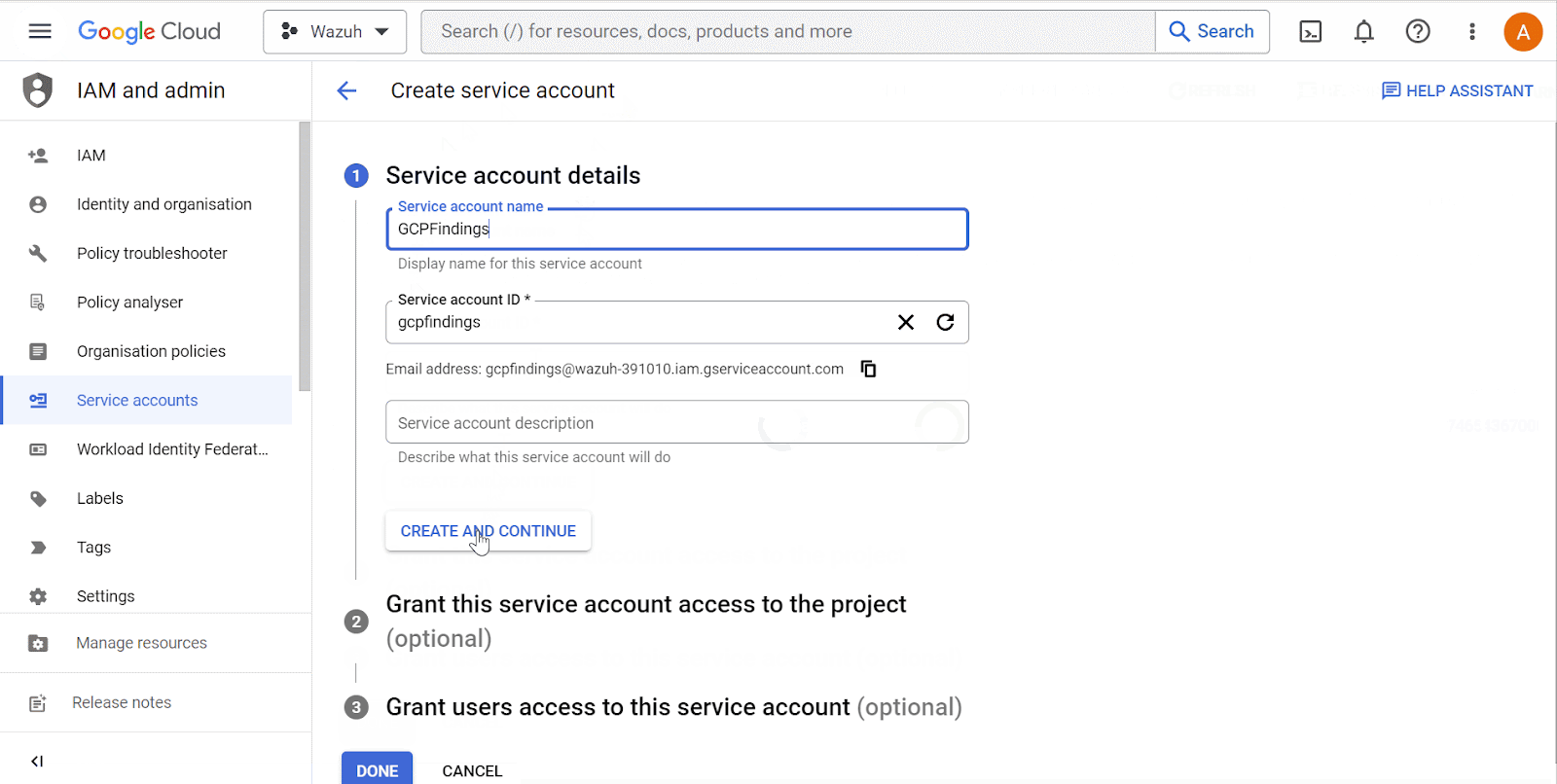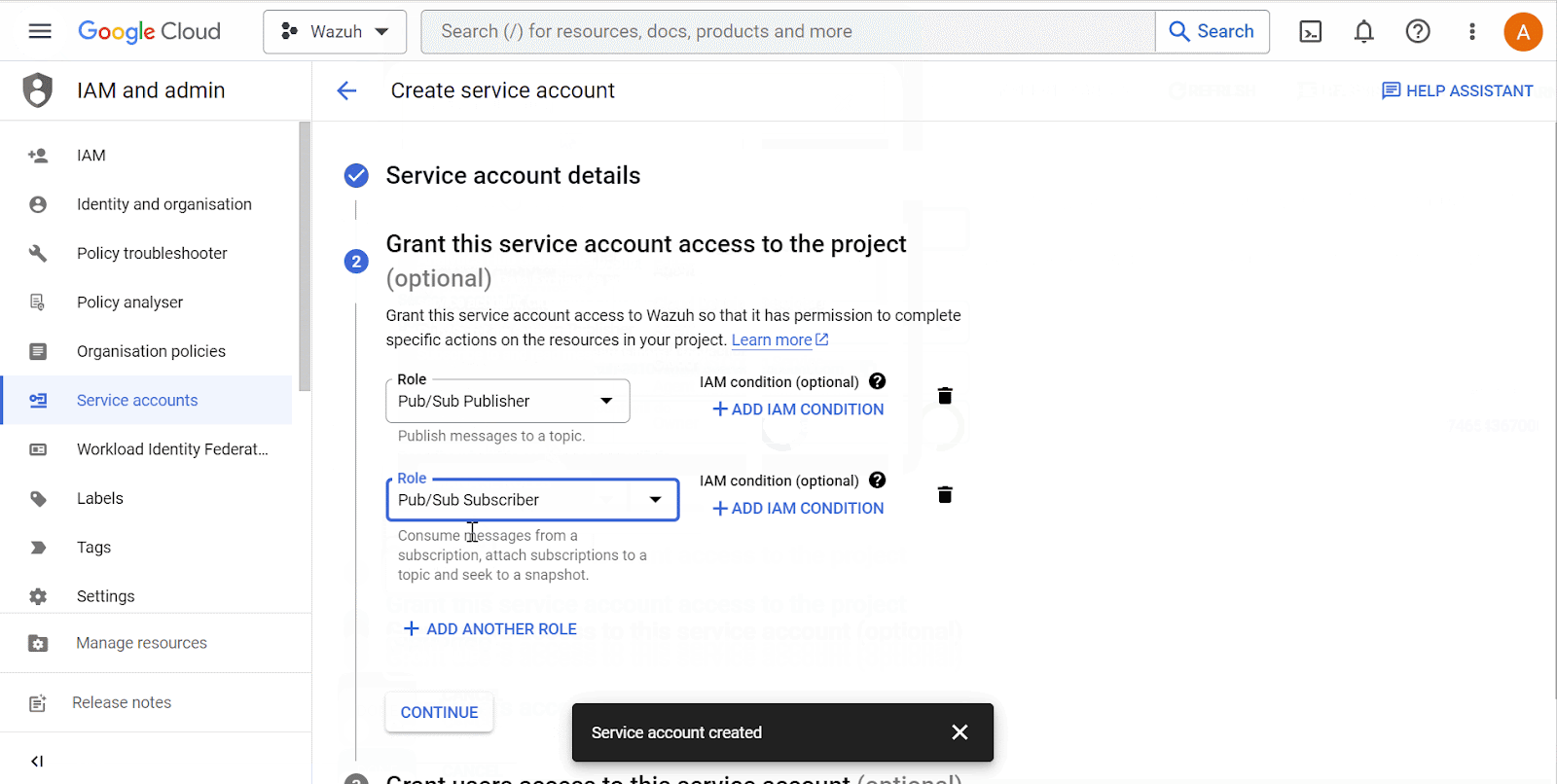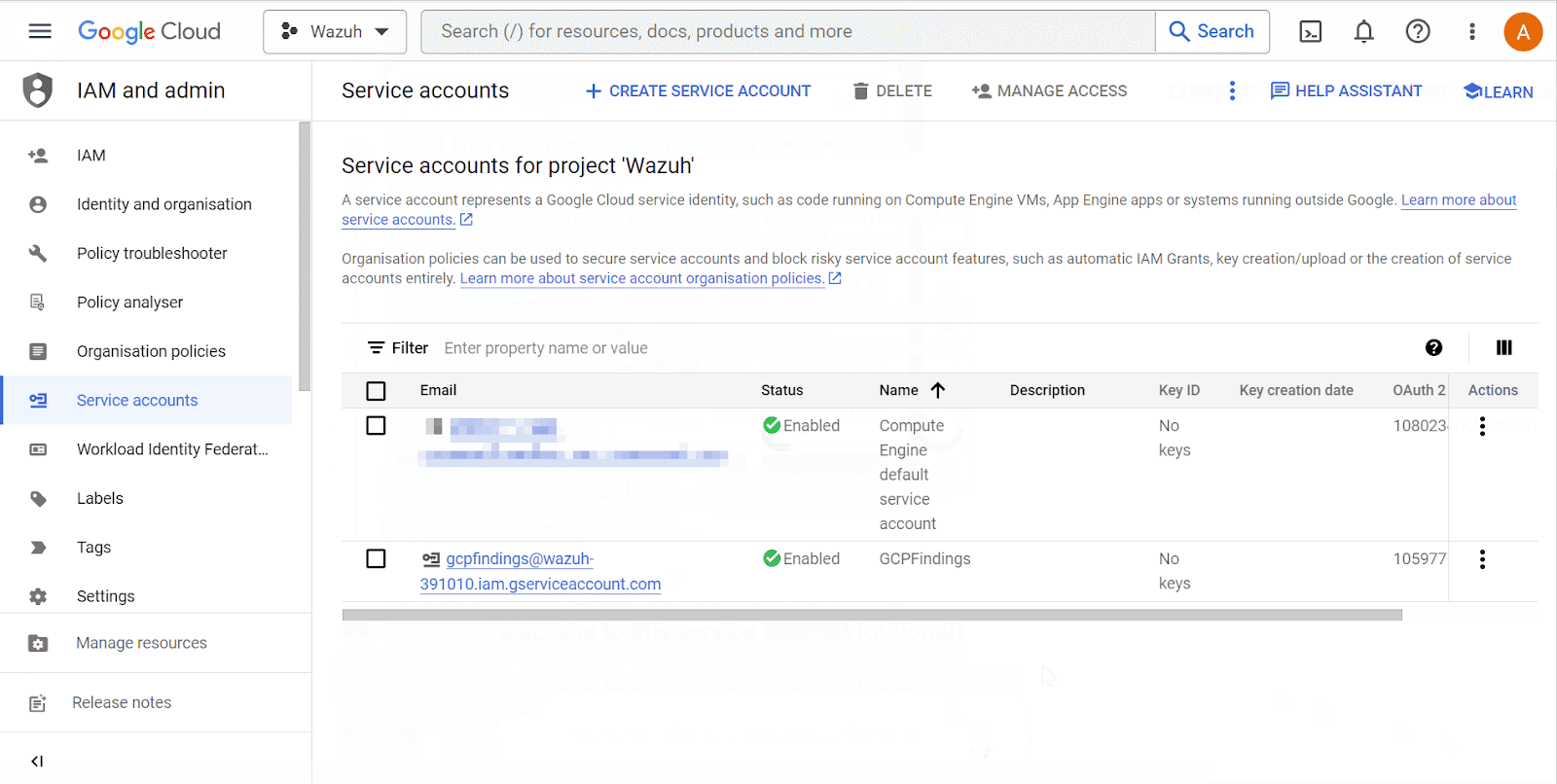
Where:
Service account name is the privileged account that Wazuh uses to connect to Google Cloud.
Roles are the rights given to the service account.
Open the newly created service account and create a private key in JSON format. Your browser automatically downloads the key. Wazuh uses the key to authenticate to your Google Cloud project.
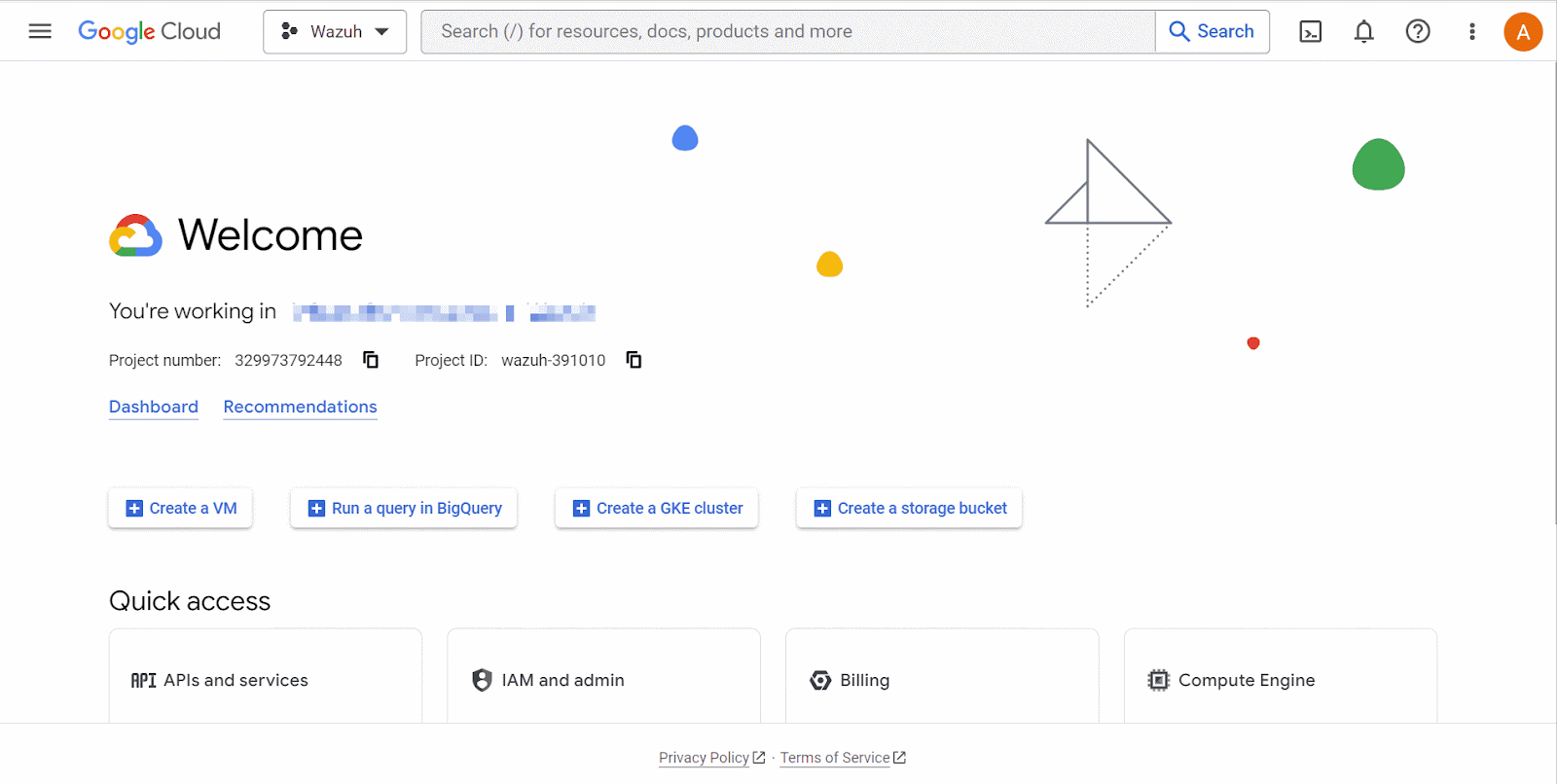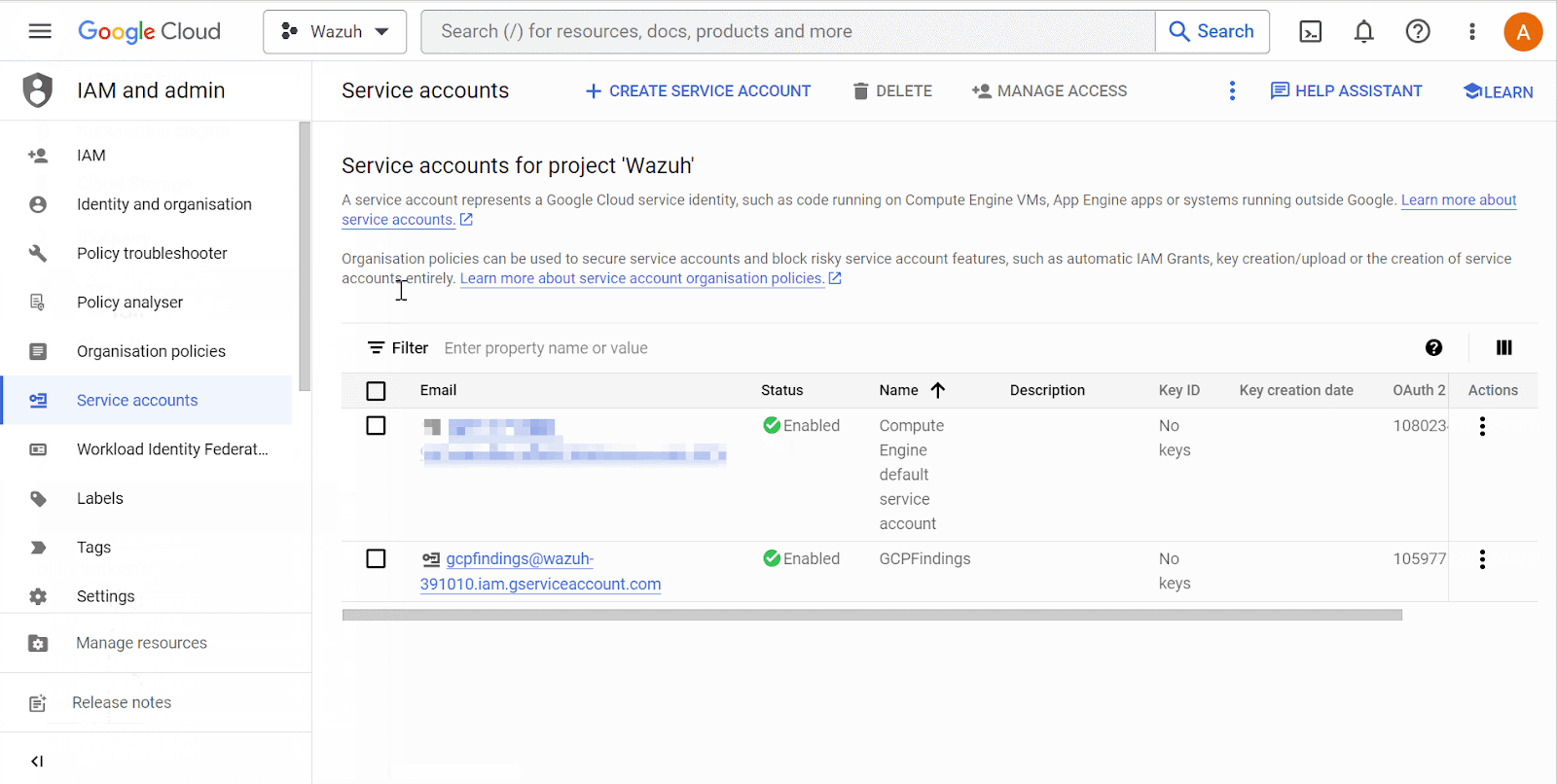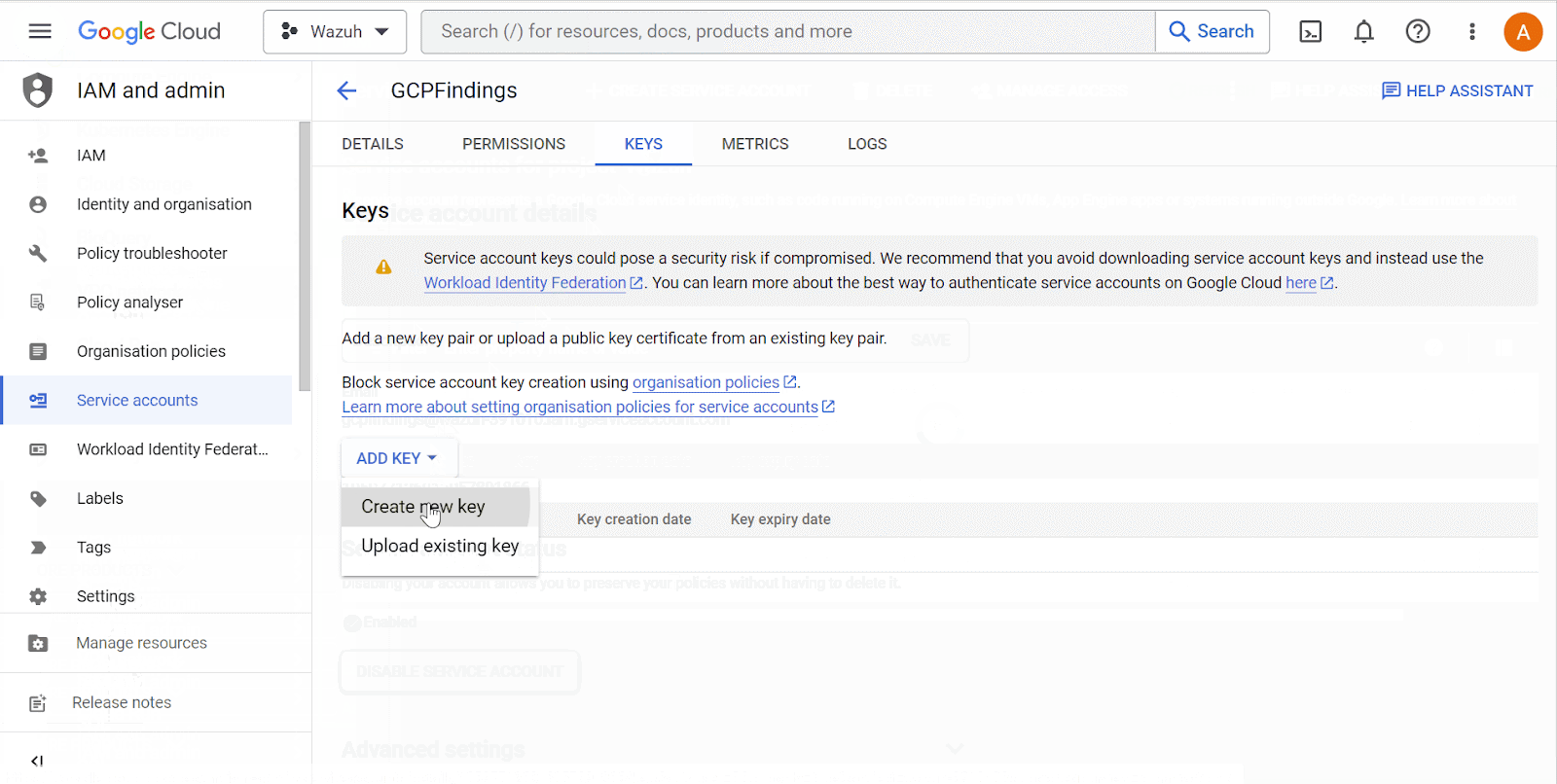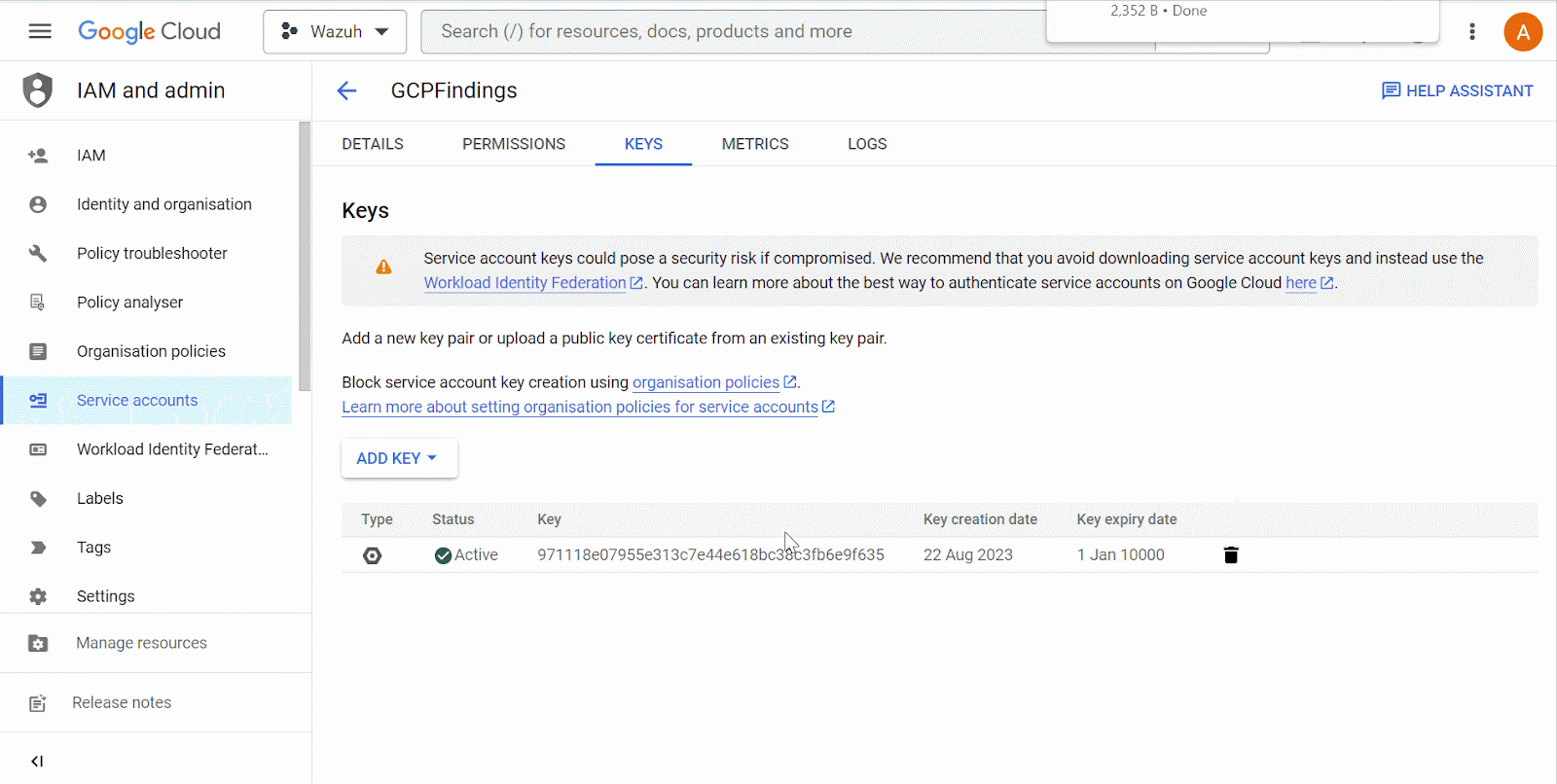
Search for
Pub/Subfrom the console search field at the top of the page and select it. Click on Create Topic. On the Create Topic page, input the Topic ID and ensure the Add a default subscription checkbox is selected. Then, click Create. Take note of the Subscription ID.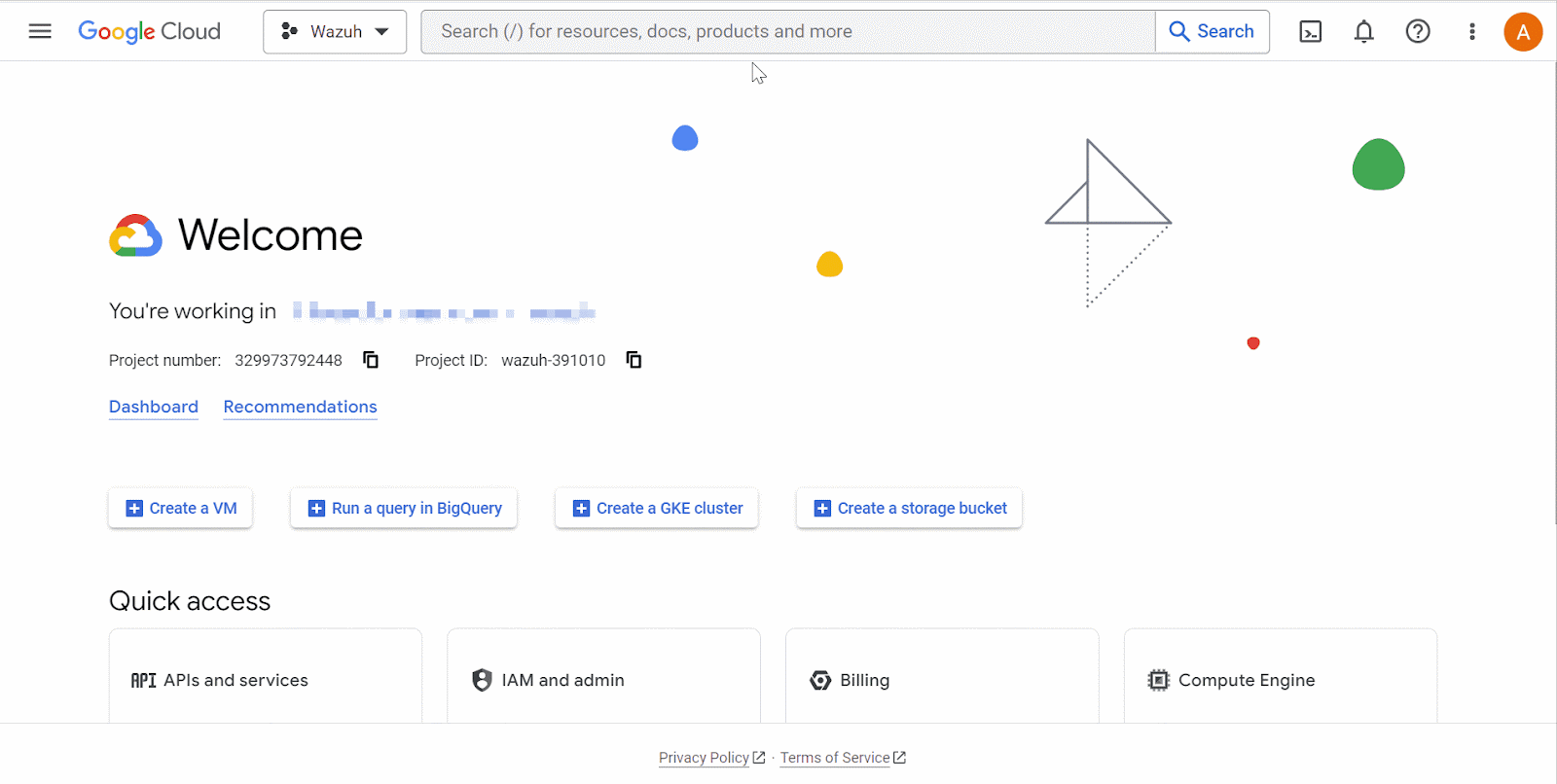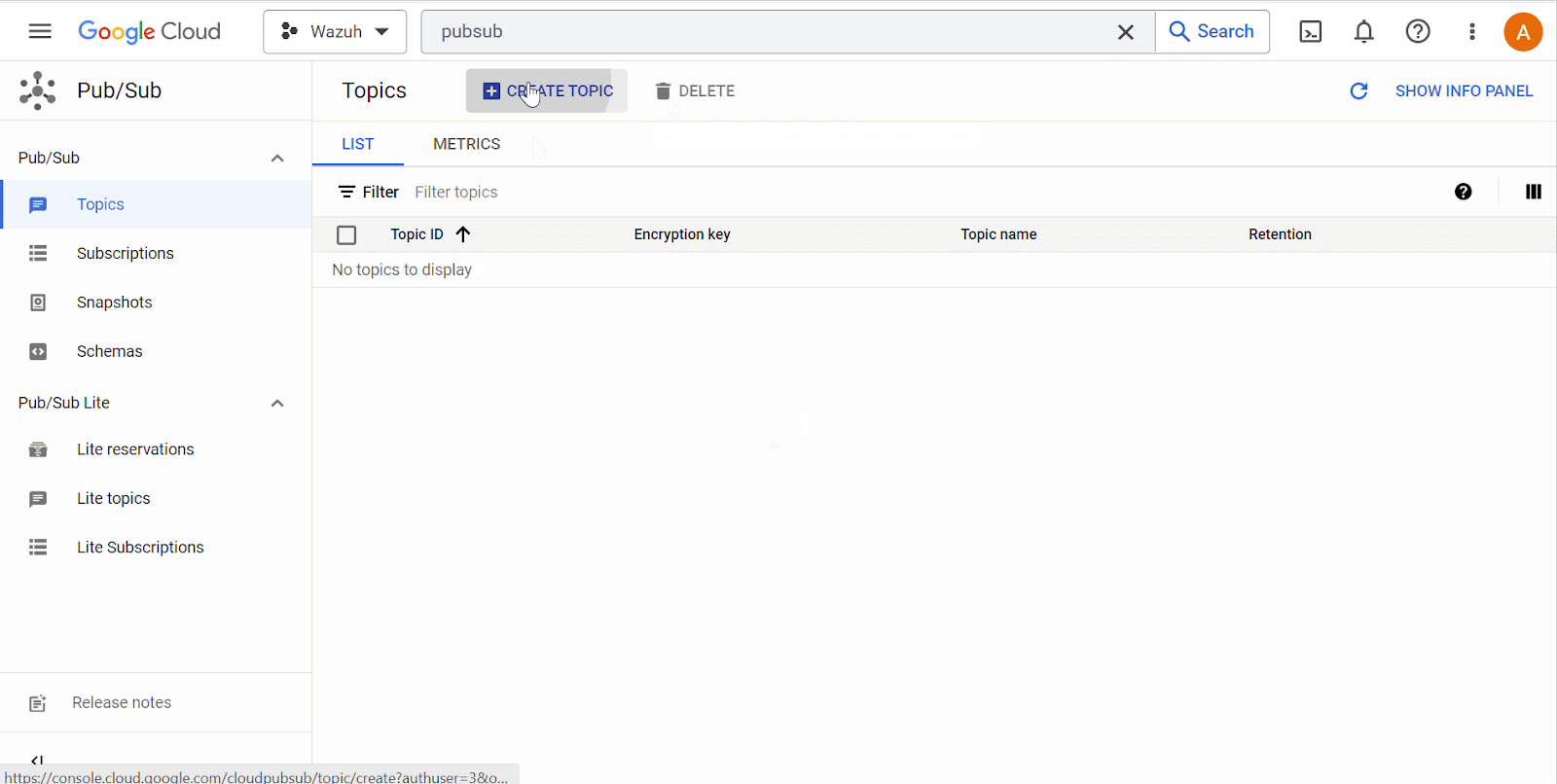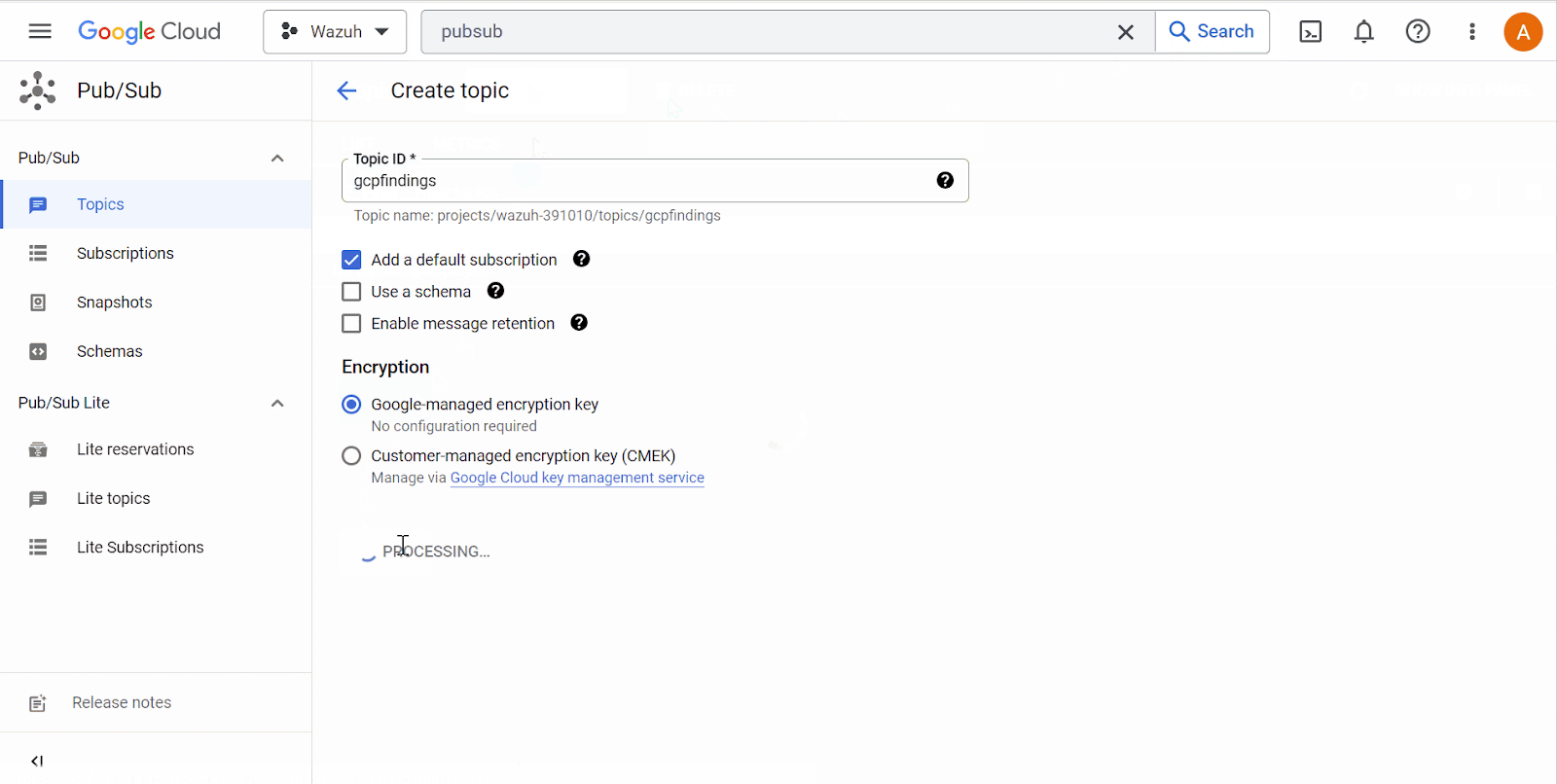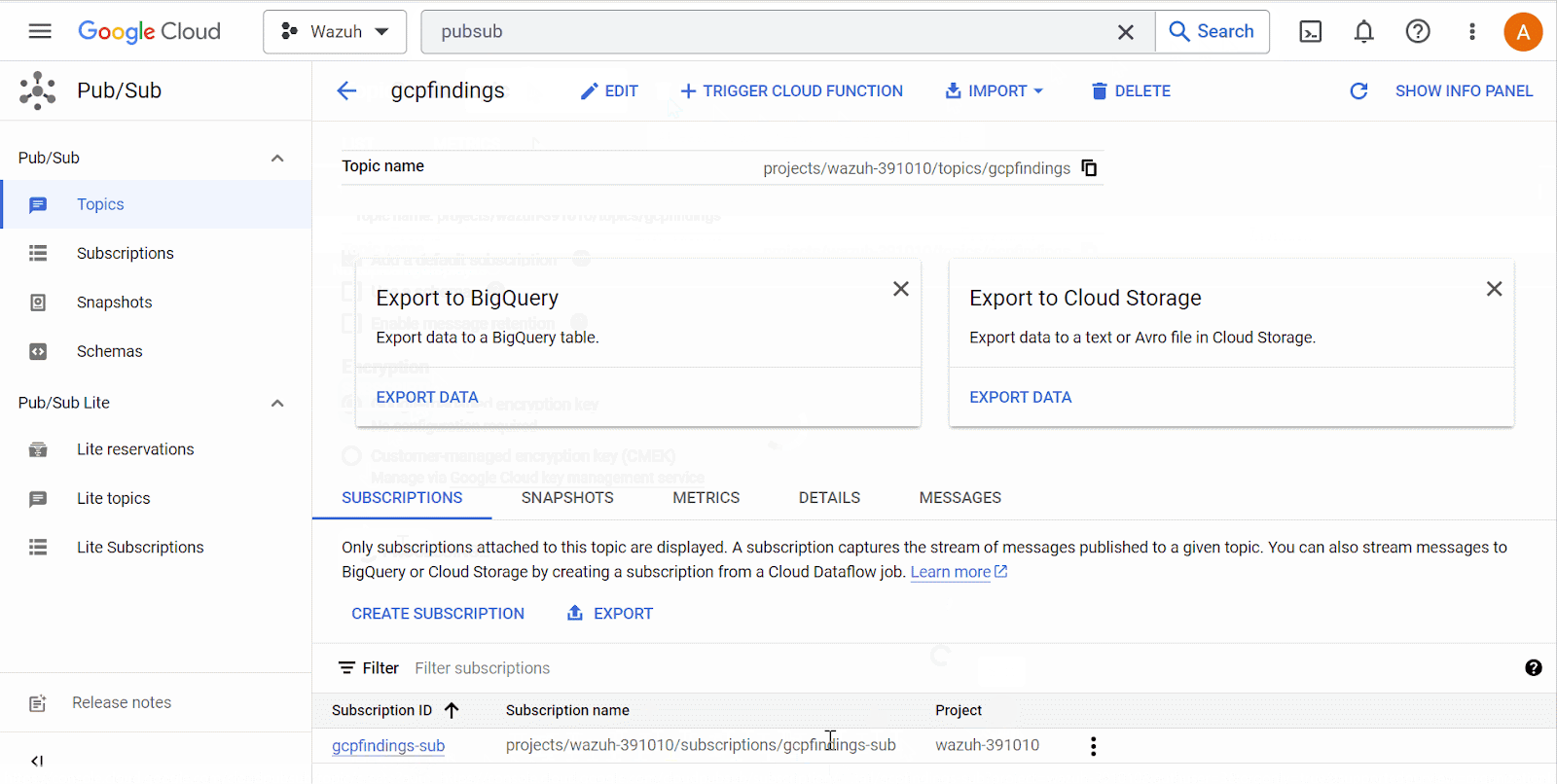
Search for Log Router in the Google Cloud console and select it. Click on Create Sink. Name the sink and click Next. On the Sink destination service, select Cloud Pub/Sub topic. Next, select the topic name created above. Click Create Sink.
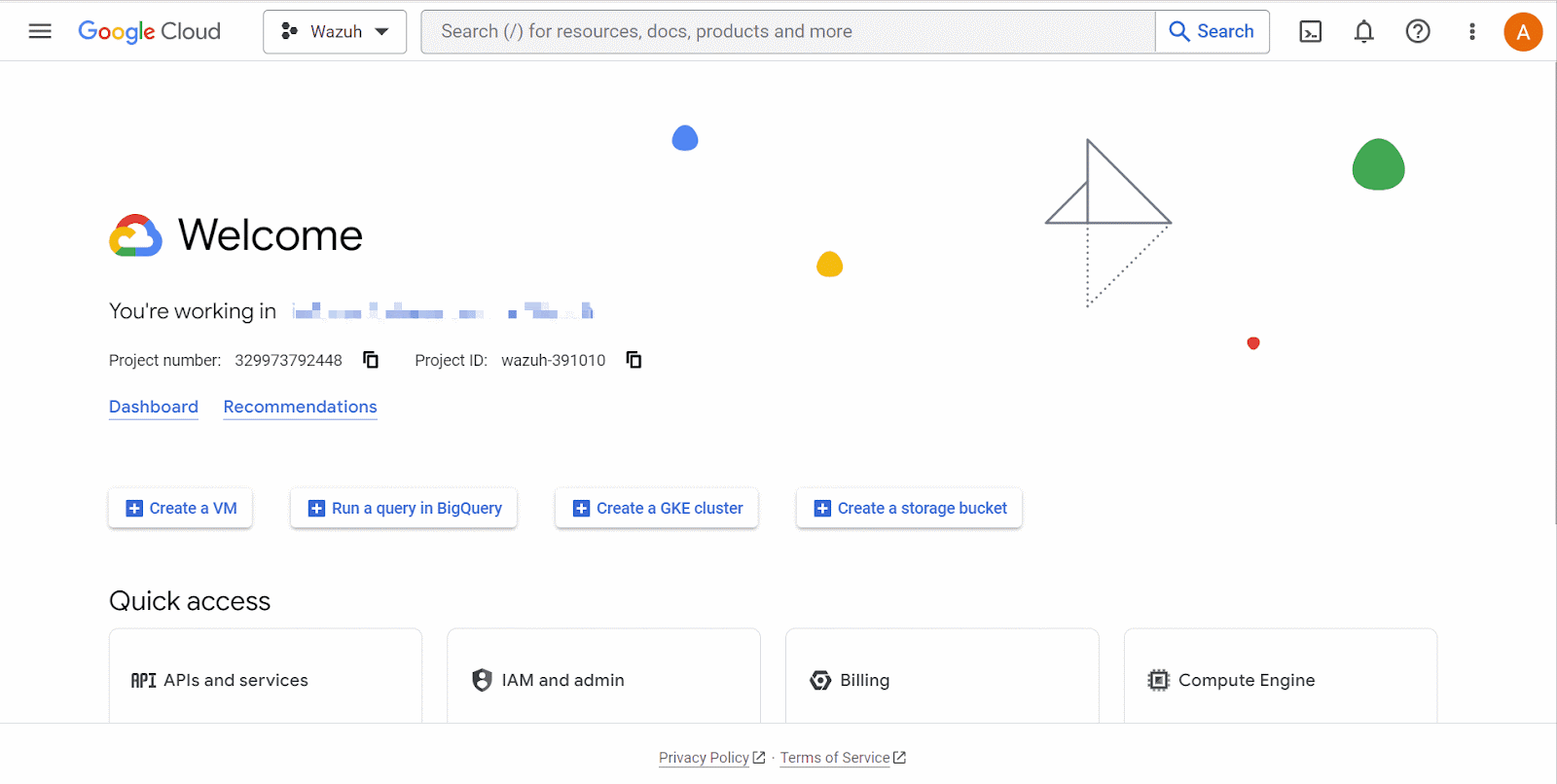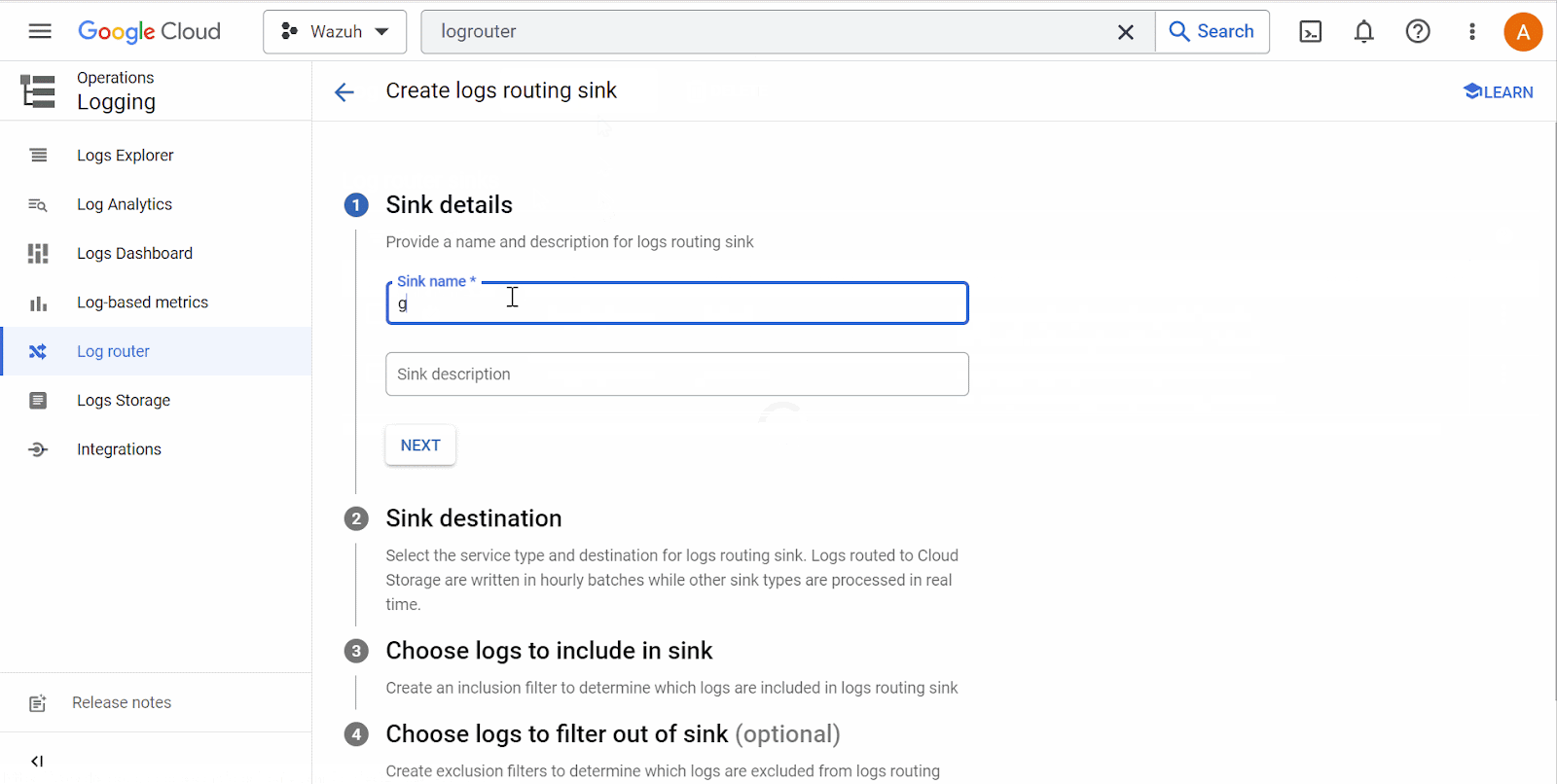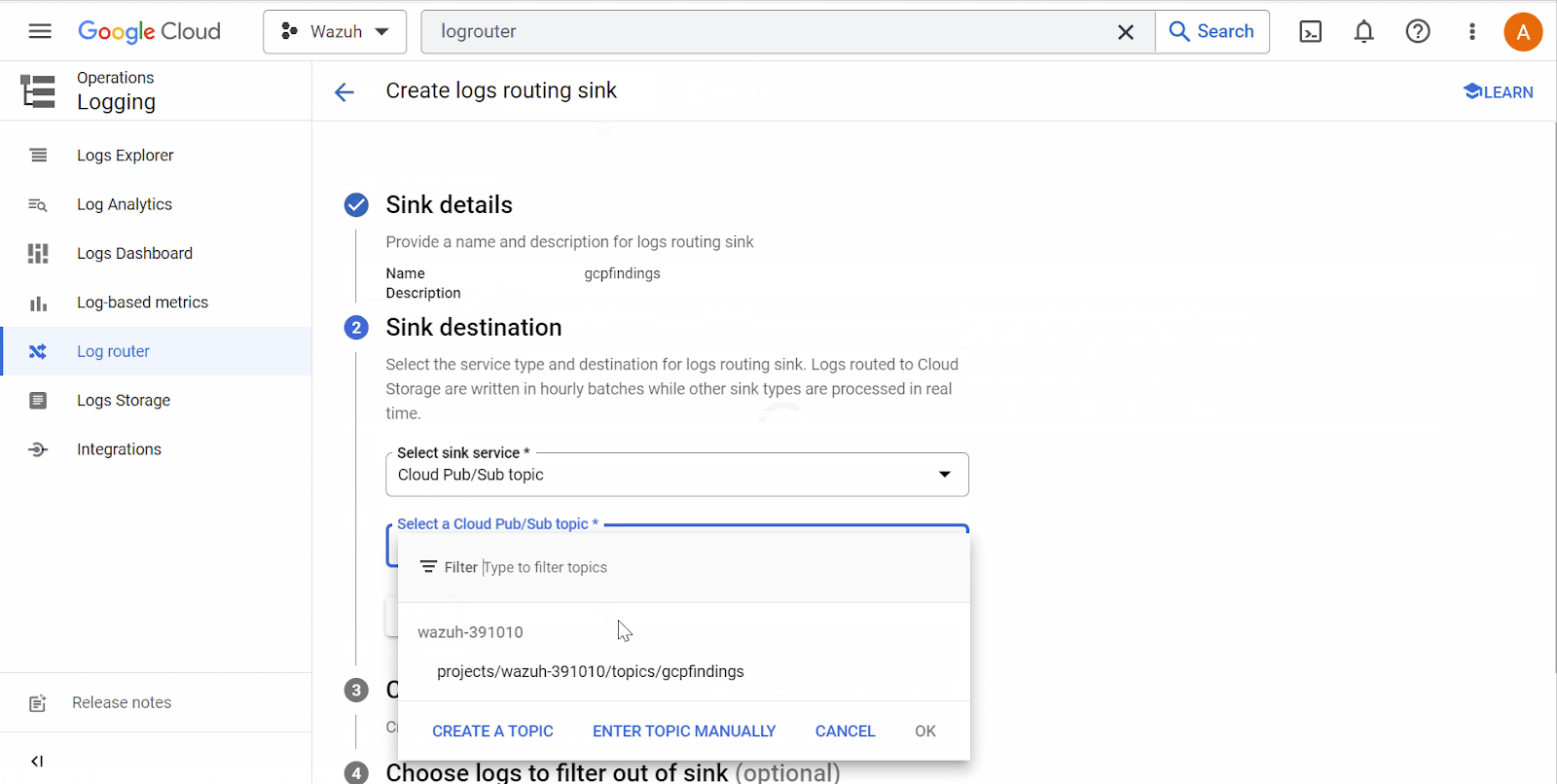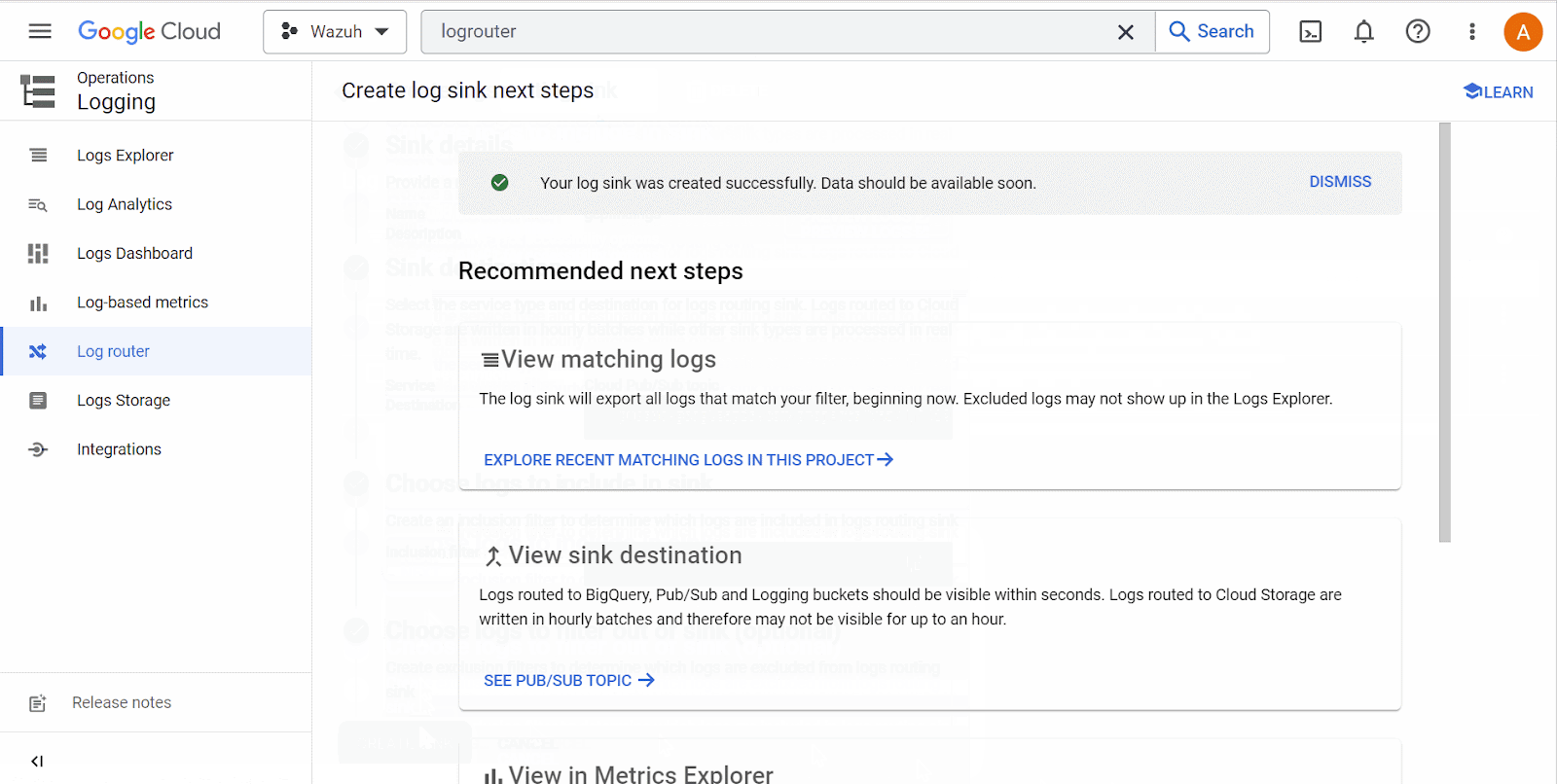
The Log Router and Sink services in a Google Cloud project are responsible for log management and log destination routing, respectively.
Configure continuous log export from the Google Cloud Findings service to the Google Cloud Pub/Sub service.
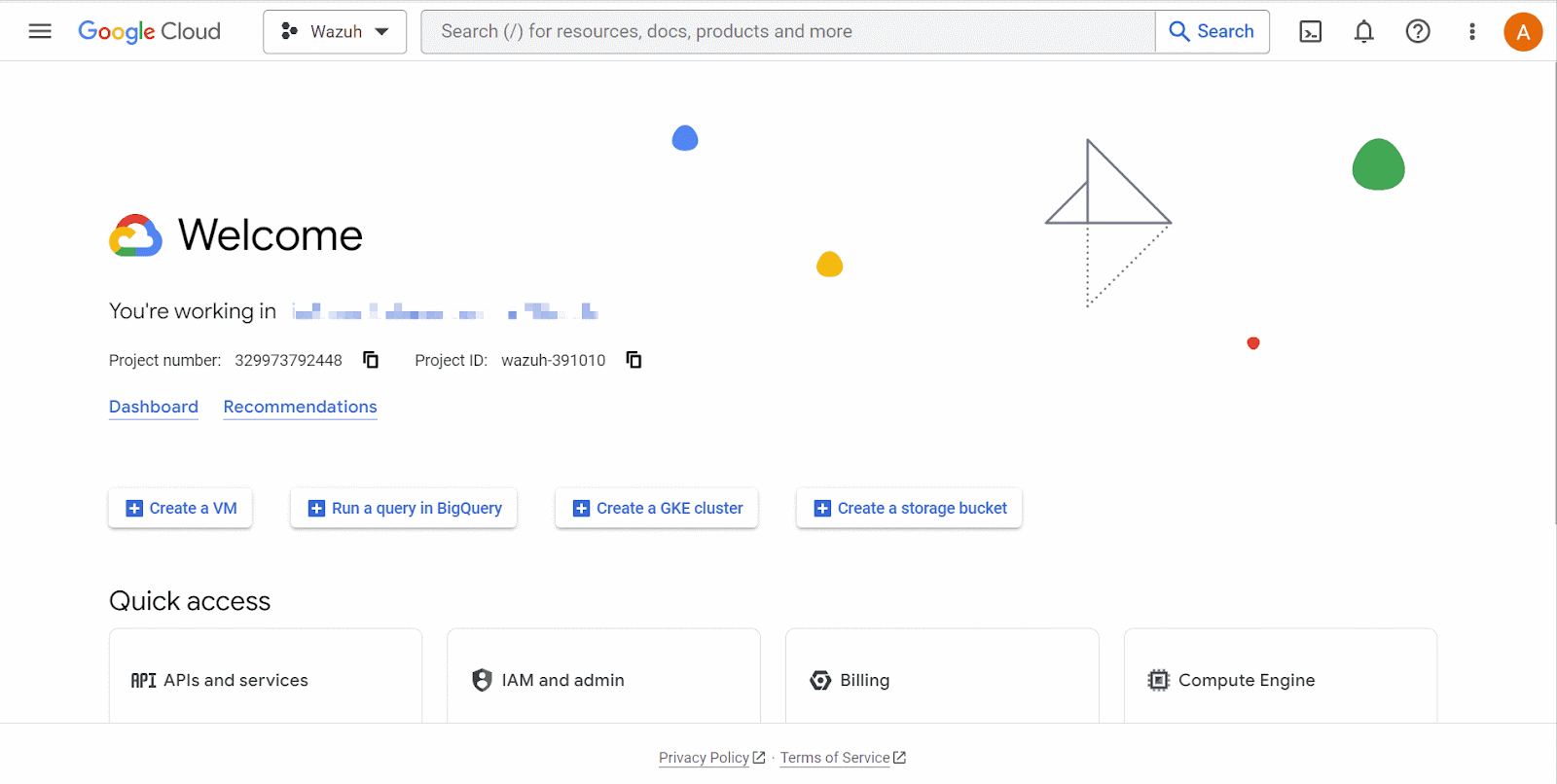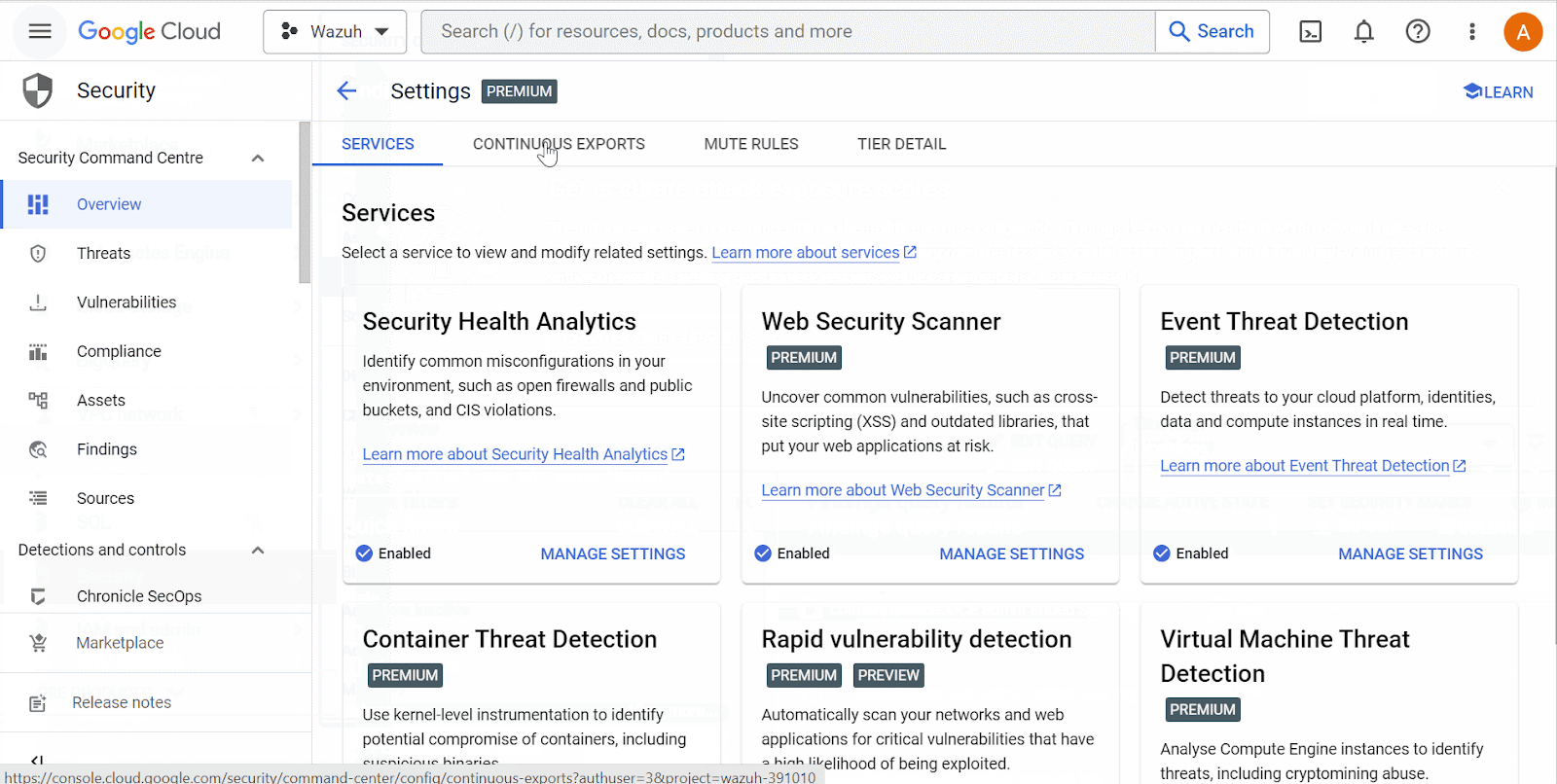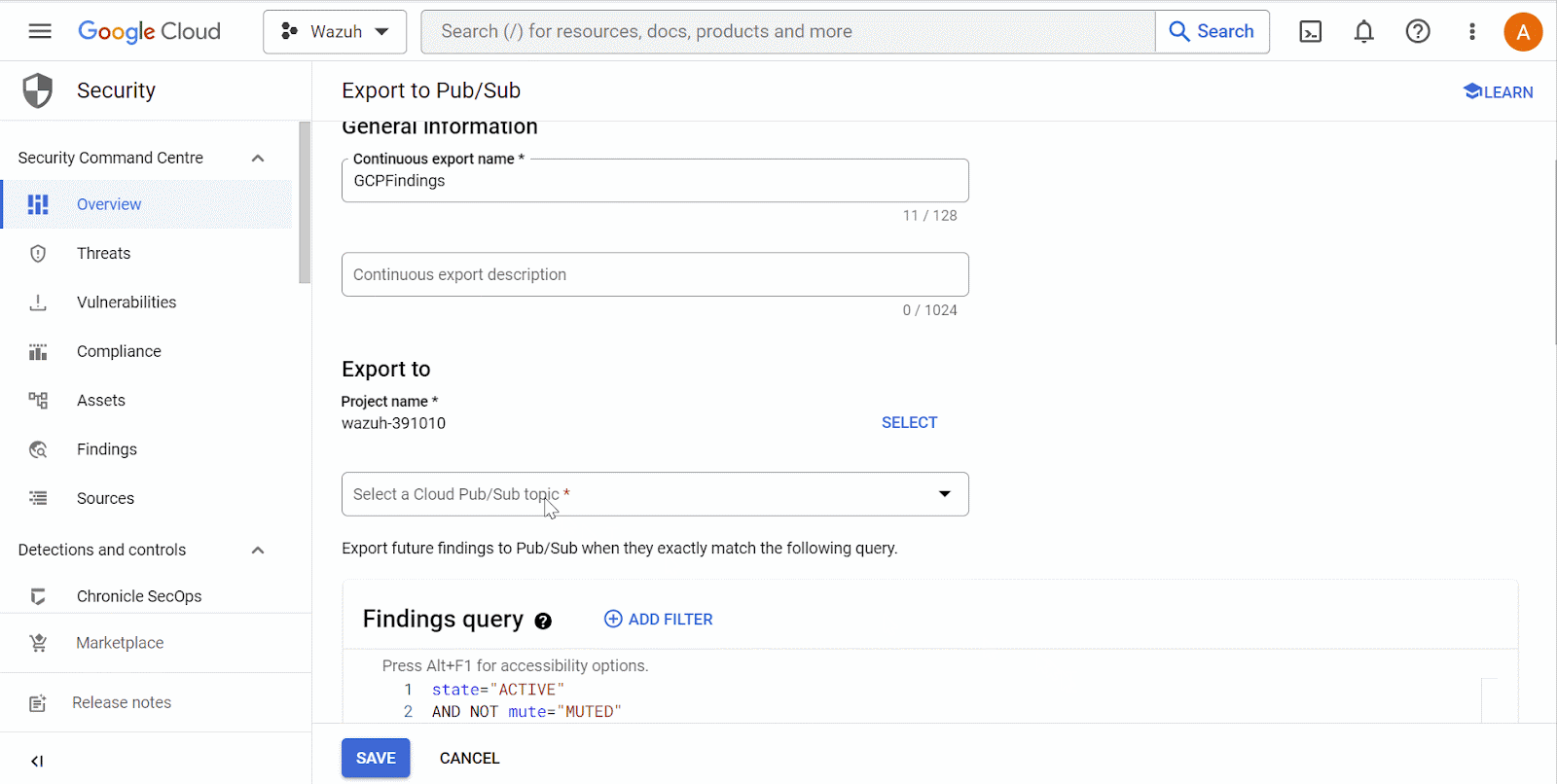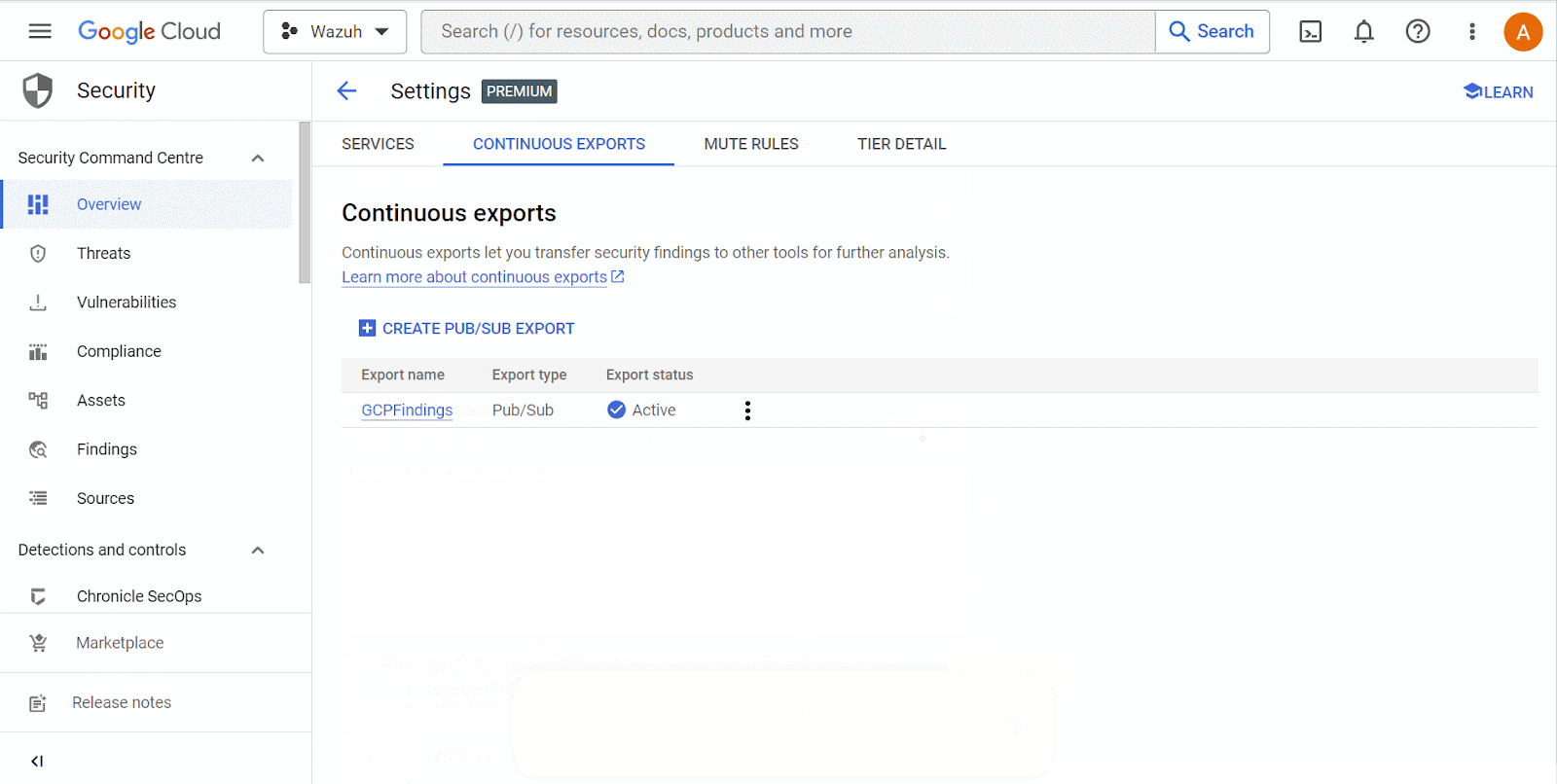
Wazuh server
Configure the Wazuh server to receive logs from Google Cloud by performing the following steps.
Note
Run the commands with root permission.
Create a
credentials.jsonfile in the/var/ossec/wodles/gcloud/directory:# touch /var/ossec/wodles/gcloud/credentials.json
Update the
/var/ossec/wodles/gcloud/credentials.jsonfile with the contents of the private key in JSON format file downloaded earlier. The Wazuh module for Google Cloud Pub/Sub uses the key file to authenticate your Google Cloud account.Append the following content to the
/var/ossec/etc/ossec.confconfiguration file. The configuration specifies how Wazuh connects to Google Cloud using the project ID, Google Cloud PubSub subscription ID, and a credential.<ossec_config> <gcp-pubsub> <pull_on_start>yes</pull_on_start> <interval>5m</interval> <project_id><PROJECT_ID></project_id> <subscription_name><SUBSCRIPTION_ID></subscription_name> <credentials_file>/var/ossec/wodles/gcloud/credentials.json</credentials_file> </gcp-pubsub> </ossec_config>
Replace the variables in the configuration with the appropriate values.
Where:
<PROJECT_ID>is the ID of the Google Cloud project created above.<SUBSCRIPTION_NAME>is the subscription ID of your Google Cloud Pub/Sub.
Create a rule file
gcp_posture.xmlin the/var/ossec/etc/rules/directory and add the following custom rules to detect Google Cloud posture findings:<group name="gcp,"> <!-- Misconfiguration detection --> <rule id="100200" level="10"> <if_sid>65000</if_sid> <field name="gcp.finding.findingClass">MISCONFIGURATION</field> <description>A $(gcp.finding.findingClass) with $(gcp.finding.severity) severity has been discovered on the GCP project $(gcp.resource.projectDisplayName). $(gcp.finding.description)</description> <mitre> <id>T1562</id> </mitre> </rule> <!-- Threat detection --> <rule id="100201" level="10"> <if_sid>65000</if_sid> <field name="gcp.finding.findingClass">THREAT</field> <description>A $(gcp.finding.findingClass) with $(gcp.finding.severity) severity has been discovered on the GCP project $(gcp.resource.projectDisplayName). $(gcp.finding.category).</description> <mitre> <id>T1562</id> </mitre> </rule> </group>
Where:
Rule ID
100200is triggered when Wazuh detects a misconfiguration in a Google Cloud account.Rule ID
100201is triggered when Google Cloud detects a threat.
Restart the Wazuh manager to apply the configuration:
# systemctl restart wazuh-manager
Cloud security posture management simulation
The Findings module is a Google Cloud Security Command Centre service that records security misconfigurations across a Google Cloud project.
Network misconfigurations
Perform the following actions on the Google Cloud console to simulate network misconfiguration.
Enable the Compute Engine API. This will enable the internal VPC firewall.
Create a firewall rule,
verybadruleon the Google Cloud network security to simulate multiple network misconfigurations. The firewall rule allows connections from all IP addresses and ports.
Delete the firewall rule
verybadrulefrom the list of rules on Google Cloud network security.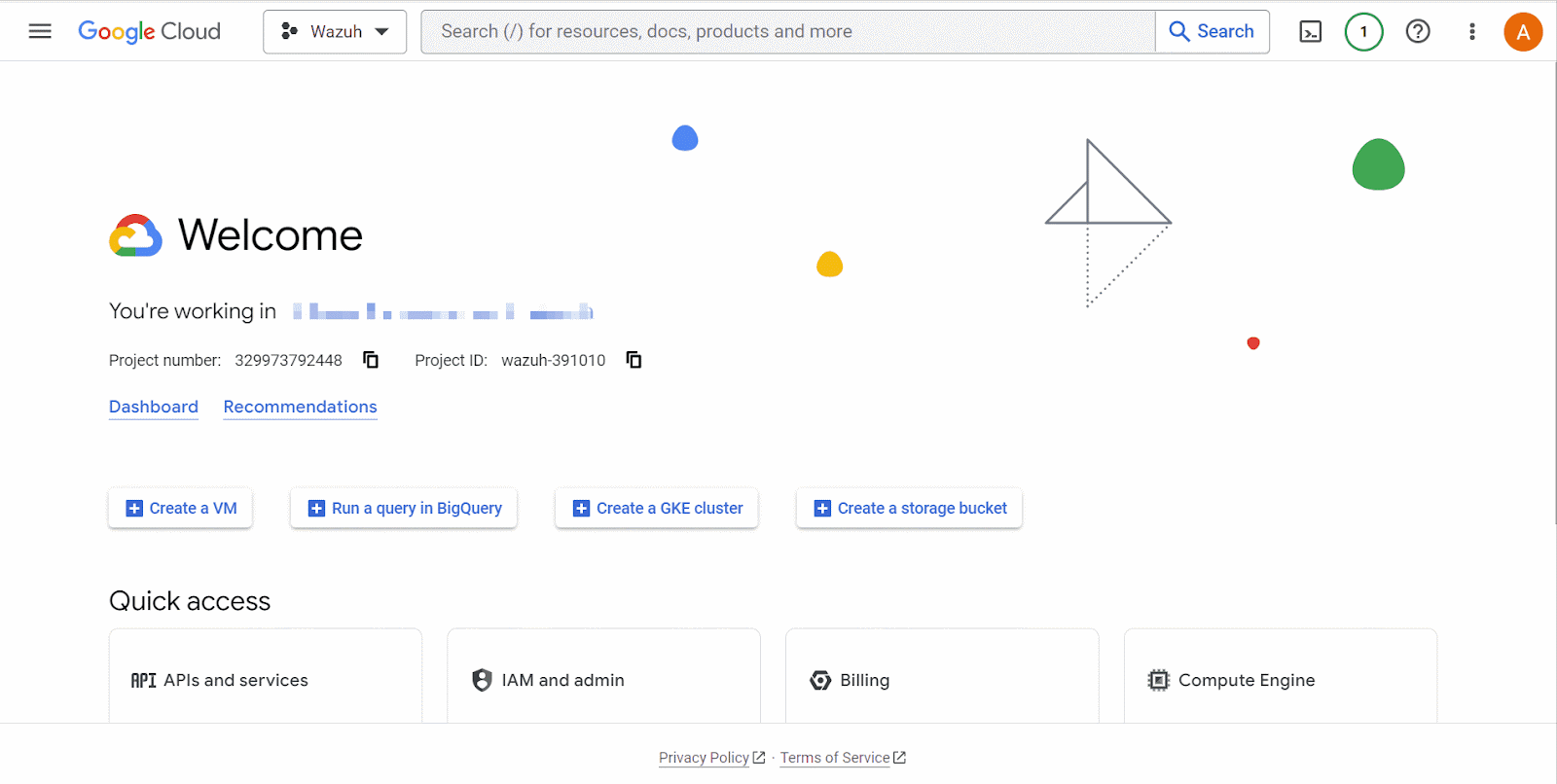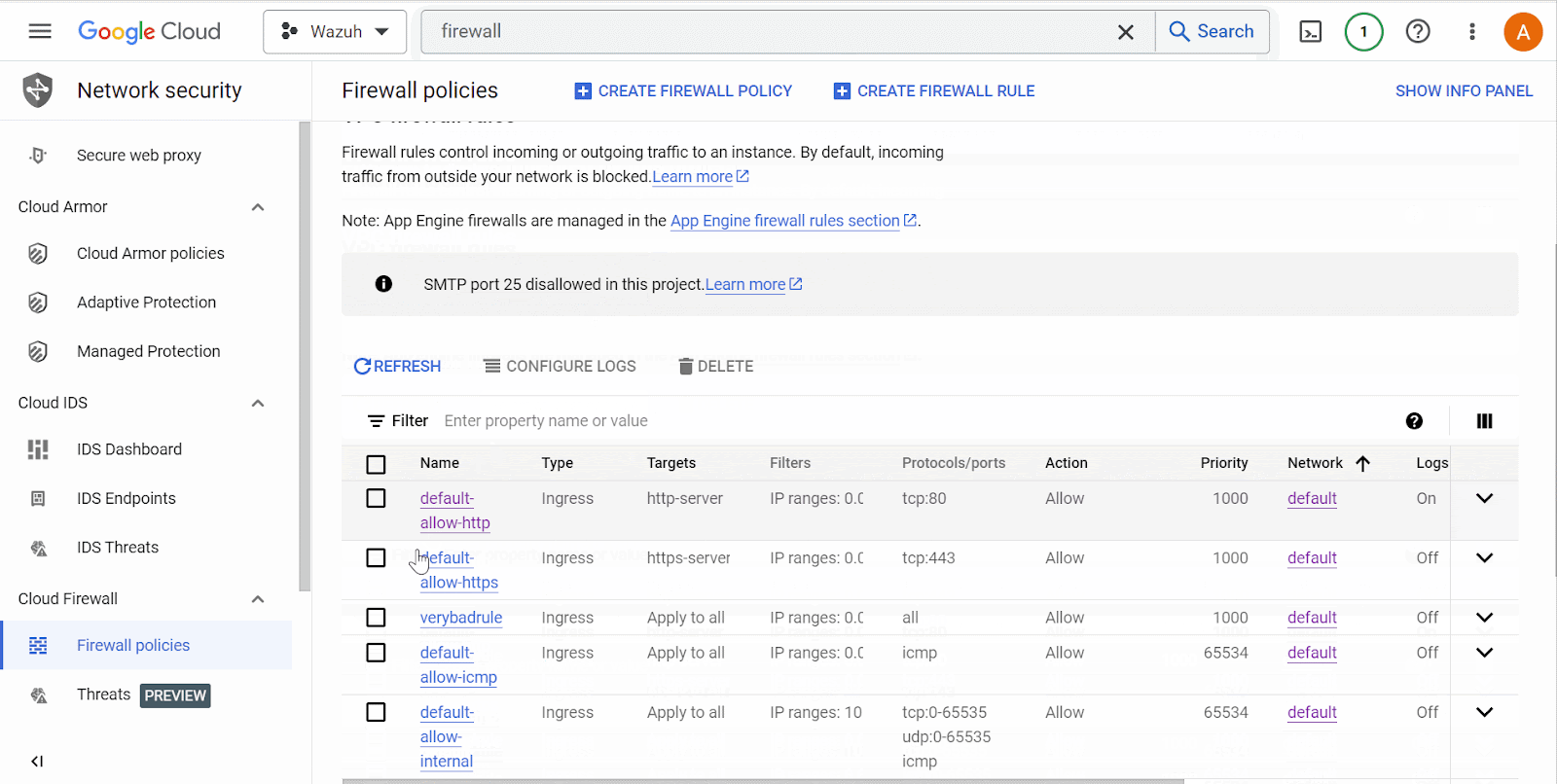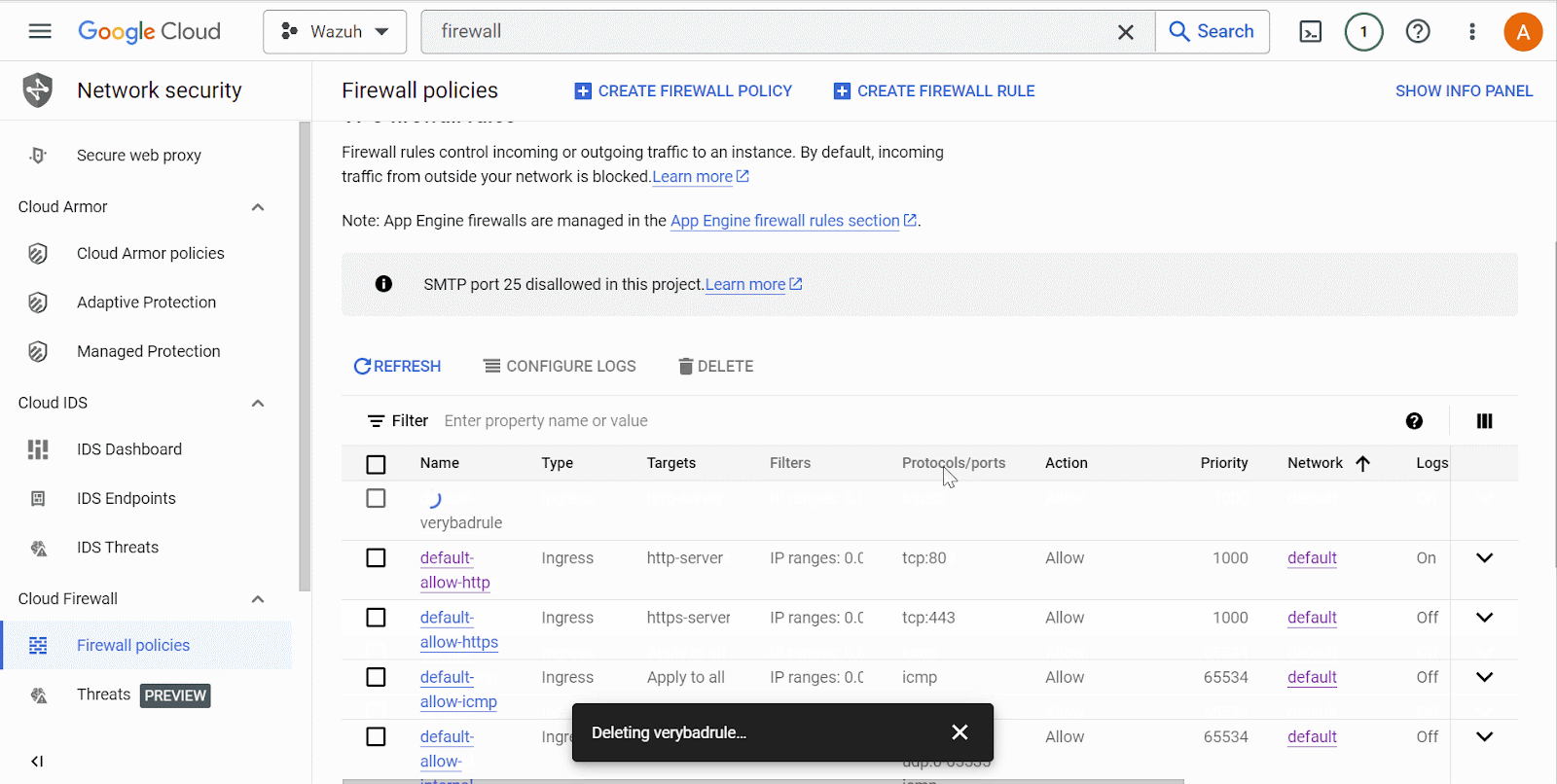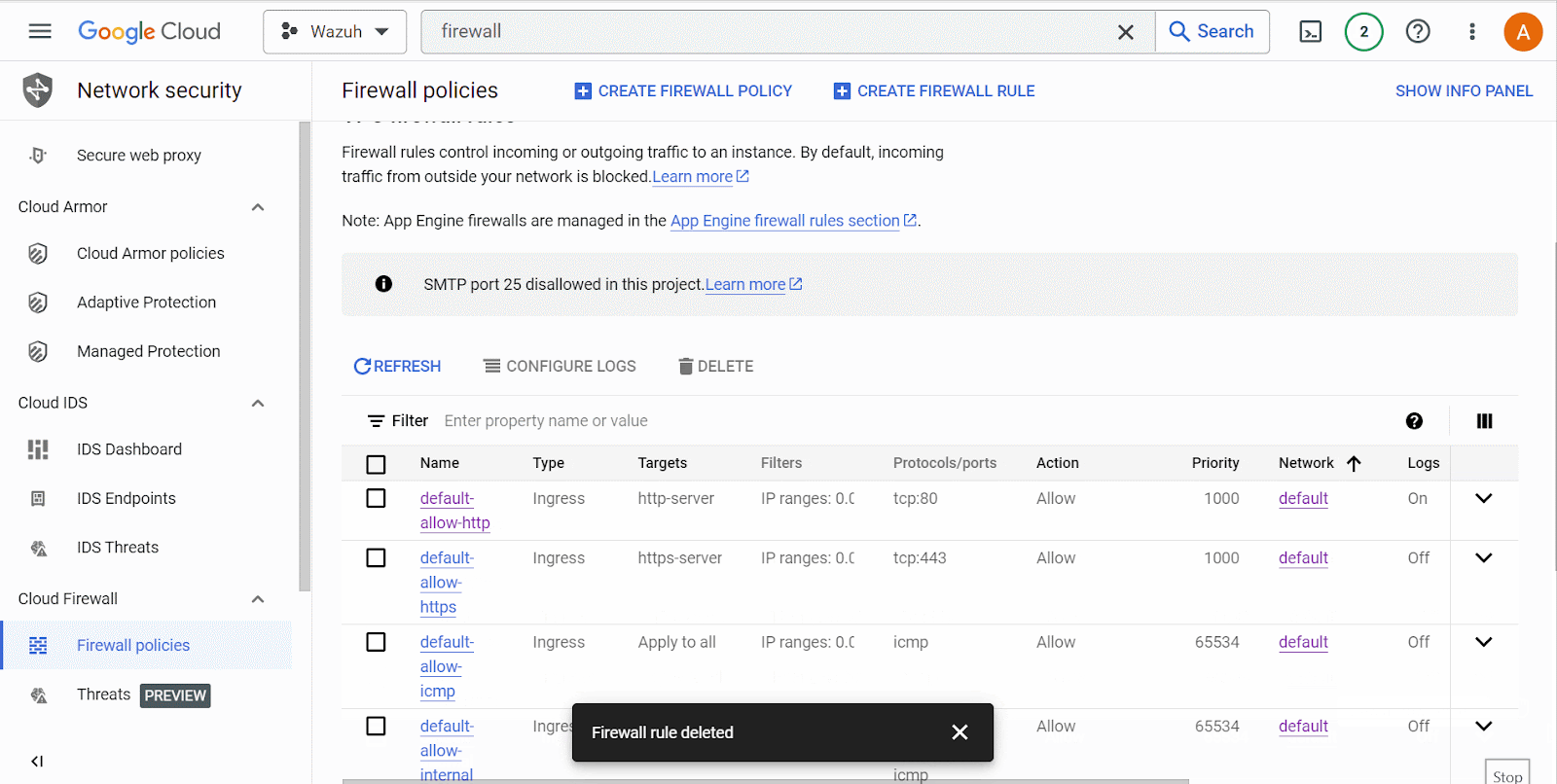
Identity and access management anomalous activity
Create a test Gmail email address if you don’t have one already.
Navigate to the IAM & Admin drop-down menu and select IAM. Click on Grant Access. On the Grant Access page, enter the test user’s Gmail address as a New principal. Next, assign the role, Project > Owner and click Save.
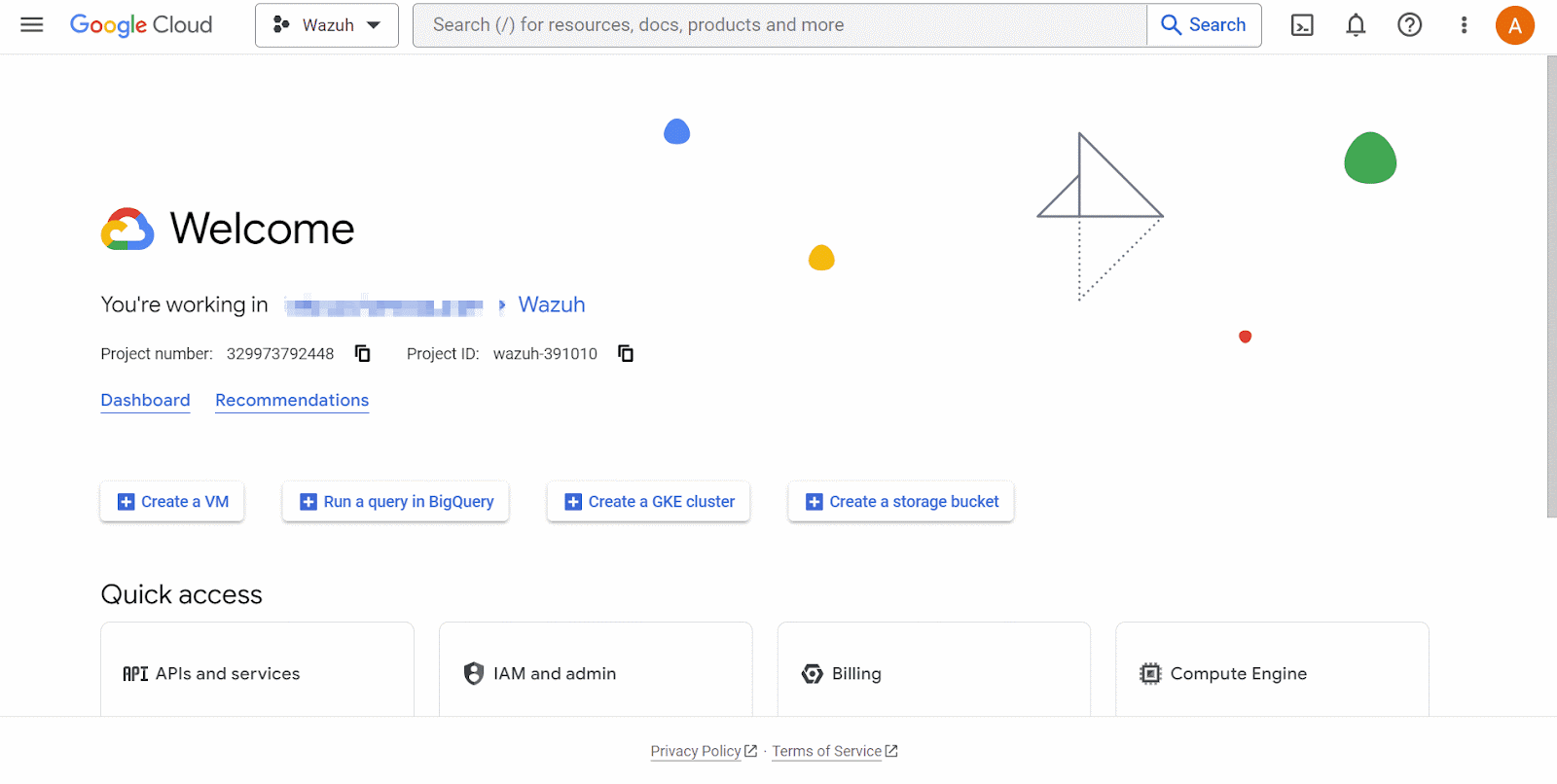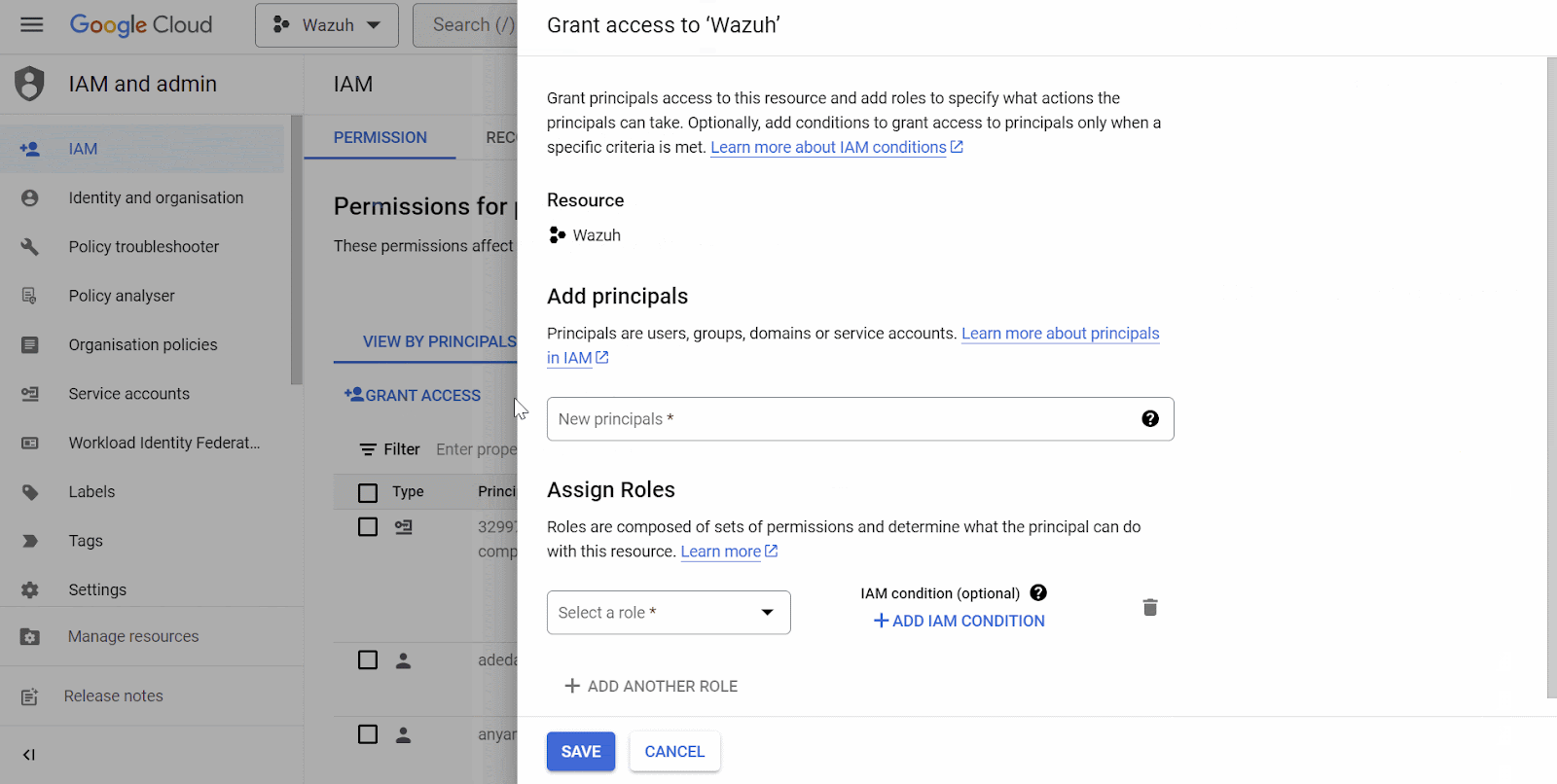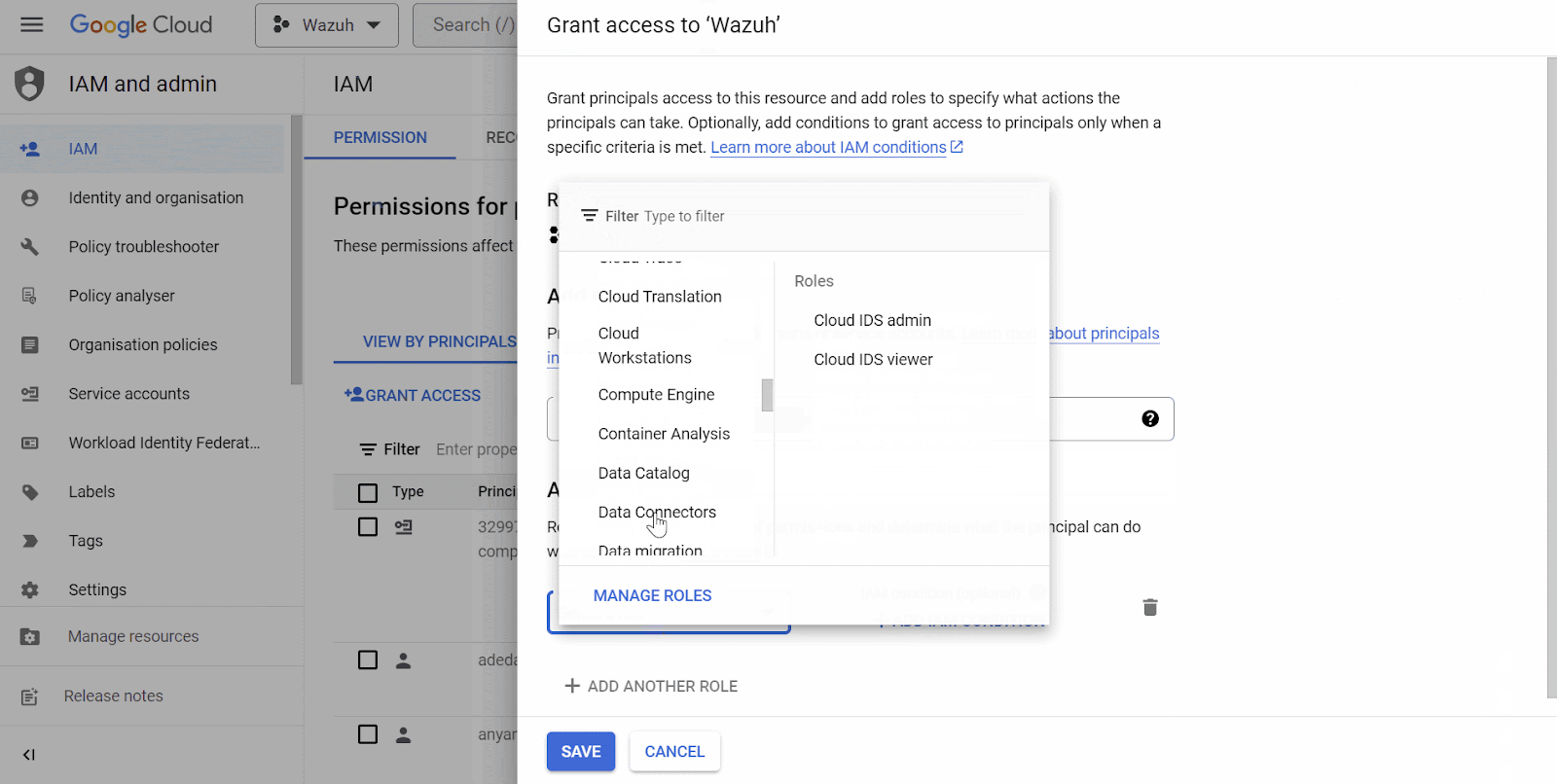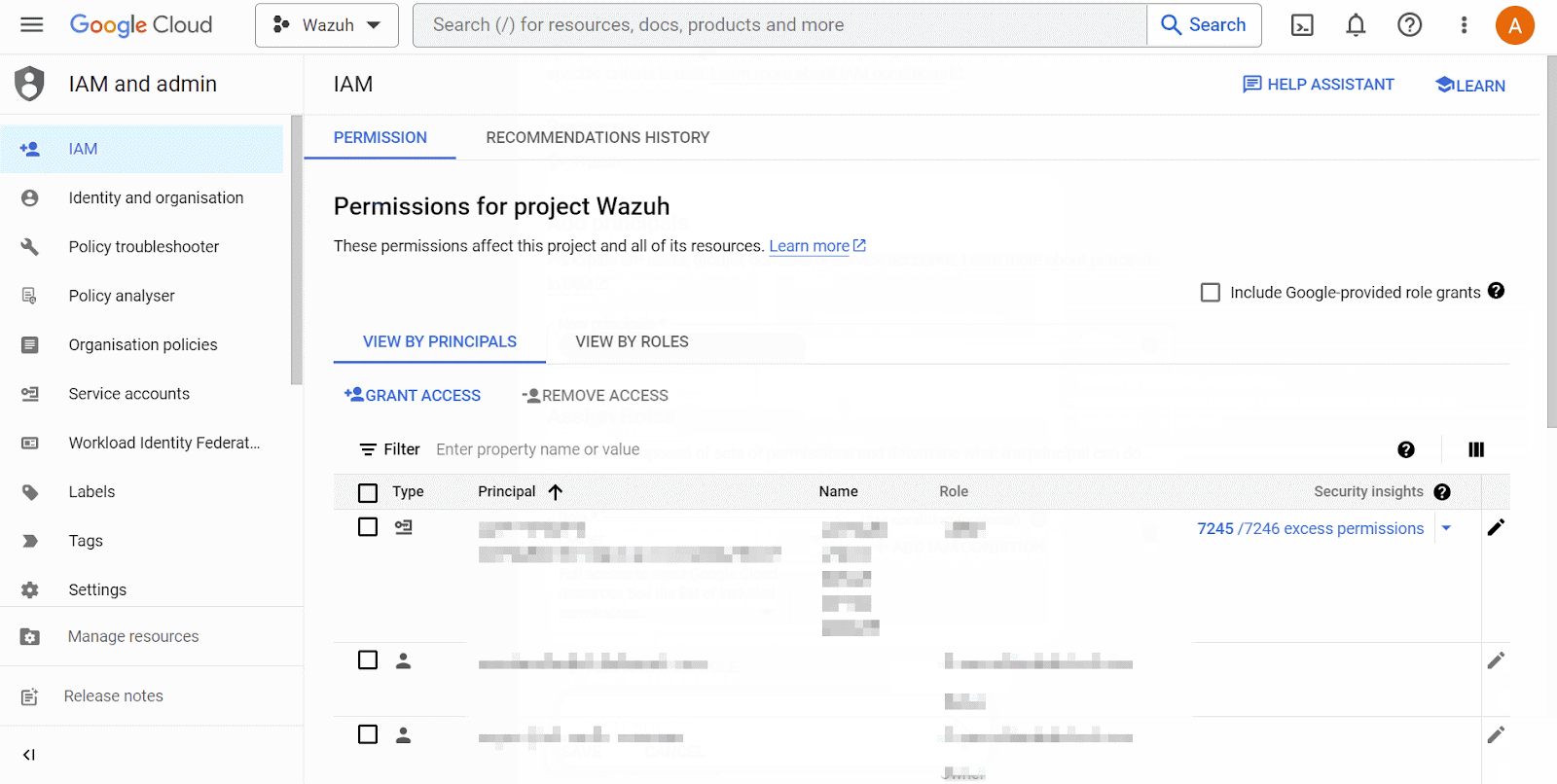
Posture management result
Visualize the Google Cloud posture management results by navigating to Threat Hunting. Filter for the rule IDs 100200 and 100201.
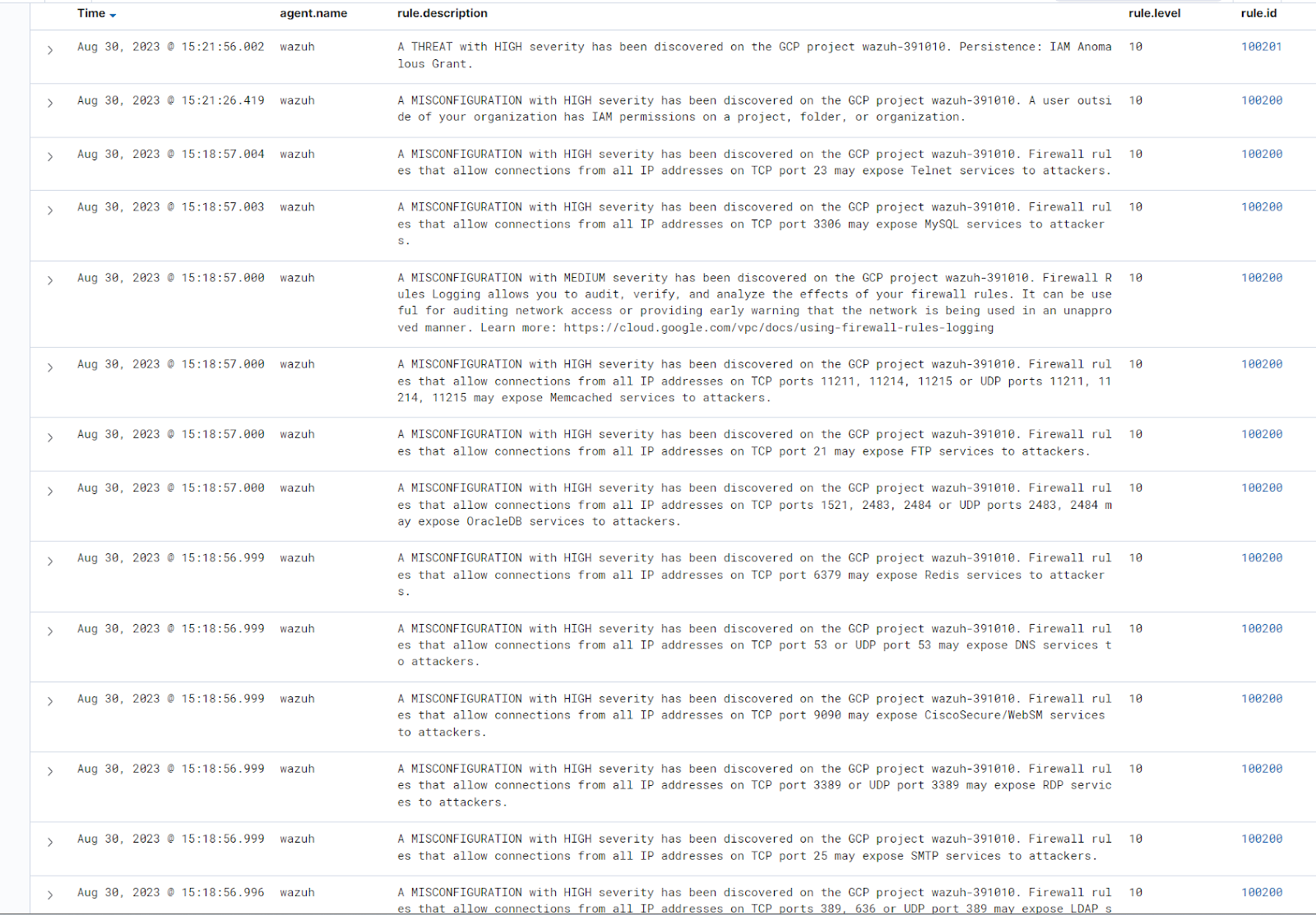
The image above shows misconfiguration and threats discovered in the Google Cloud environment.
Note
The alerts may not appear on the Wazuh dashboard immediately the first time you activate Google Cloud's security command center. This is due to the latency caused by the activation process.