Wazuh agent identity verification
This method uses SSL certificates to verify that a Wazuh agent is authorized to enroll in the Wazuh manager. The Wazuh manager and Wazuh agent verification are independent of each other. However, it is possible to use a combination of both.
Learn about Wazuh agent identity verification steps in the sections below
Prerequisites
You need a certificate authority to sign certificates for the Wazuh manager and Wazuh agents. In the absence of an already configured certificate authority, run the following command on the Wazuh server to use it as the certificate authority:
# openssl req -x509 -new -nodes -newkey rsa:4096 -keyout rootCA.key -out rootCA.pem -batch -subj "/C=US/ST=CA/O=Wazuh"
The root certificate is created and saved as the rootCA.pem file.
Wazuh agent verification options
In the prerequisite section, the CA issues an SSL certificate to the Wazuh agent host. On attempts to enroll by the Wazuh agent, the Wazuh manager verifies the certificate presented by the Wazuh agent using the root certificate. Wazuh provides two Wazuh agent verification options:
Wazuh agent verification without host validation: The certificates for the Wazuh agents are issued without specifying their hostname or IP address.
Wazuh agent verification with host validation: The certificates for the Wazuh agents are issued with their IP address or hostname specified as the common name.
The difference between these validation methods is that the certificate in the former method can be reused on multiple agents while the certificate created in the latter can only be used on the Wazuh agent whose IP address or hostname was specified during certificate generation.
Wazuh server configuration
Generate a certificate signing request (CSR) for the Wazuh agent on the Wazuh server:
Wazuh agent verification without host validation: This is done without specifying the IP address or hostname of the Wazuh agent.
# openssl req -new -nodes -newkey rsa:4096 -keyout sslagent.key -out sslagent.csr -batch
Wazuh agent verification with host validation: This is done by specifying the IP address or hostname of the Wazuh agent.
# openssl req -new -nodes -newkey rsa:4096 -keyout sslagent.key -out sslagent.csr -subj '/C=US/CN=<AGENT_IP_ADDRESS>'
Where:
sslagent.csris the CSR to be submitted to the certificate authority.sslagent.keyis the generated CSR private key.
Sign the generated agent CSR using the CA keys:
# openssl x509 -req -days 365 -in sslagent.csr -CA rootCA.pem -CAkey rootCA.key -out sslagent.cert -CAcreateserial
Where:
sslagent.csris the CSR to be submitted to the certificate authority.sslagent.certis the SSL certificate signed by the CSR.rootCA.pemis the root certificate for the CA.rootCA.keyis the root certificate private key for the CA.
Copy the signed SSL certificate and key (
sslagent.certandsslagent.keyin this case) to the Wazuh agent. You can use a tool like SCP to copy the certificate to the endpoints.Ensure that the
rootCA.pemfile is in the/var/ossec/etc/directory on the Wazuh server.Update the
/var/ossec/etc/ossec.conffile with the location of therootCA.pemfile to enable the use of certificates. Uncomment the<auth><ssl_agent_ca>section and specify the path to therootCA.pemfile on the Wazuh manager.<auth> ... <ssl_agent_ca>/var/ossec/etc/rootCA.pem</ssl_agent_ca> </auth>
Restart the Wazuh manager service to apply the changes:
# systemctl restart wazuh-manager
Linux/Unix
Follow these steps to enroll a Linux/Unix endpoint by using certificates for agent verification.
Ensure that the signed SSL certificate and key files (
sslagent.certandsslagent.key) for the Wazuh agent have been copied to the endpoint.Obtain root access, modify the Wazuh agent configuration file located at
/var/ossec/etc/ossec.conf, and include the following:The Wazuh manager IP address or FQDN (Fully Qualified Domain Name) in the
<client><server><address>section.The local path to the agent certificate and the agent key are in the
<client><enrollment>section.
<client> <server> <address><WAZUH_MANAGER_IP_ADDRESS></address> </server> <enrollment> <agent_certificate_path>/<PATH_TO>/sslagent.cert</agent_certificate_path> <agent_key_path>/<PATH_TO>/sslagent.key</agent_key_path> </enrollment> </client>
Restart the Wazuh agent to make the changes effective:
# systemctl restart wazuh-agent
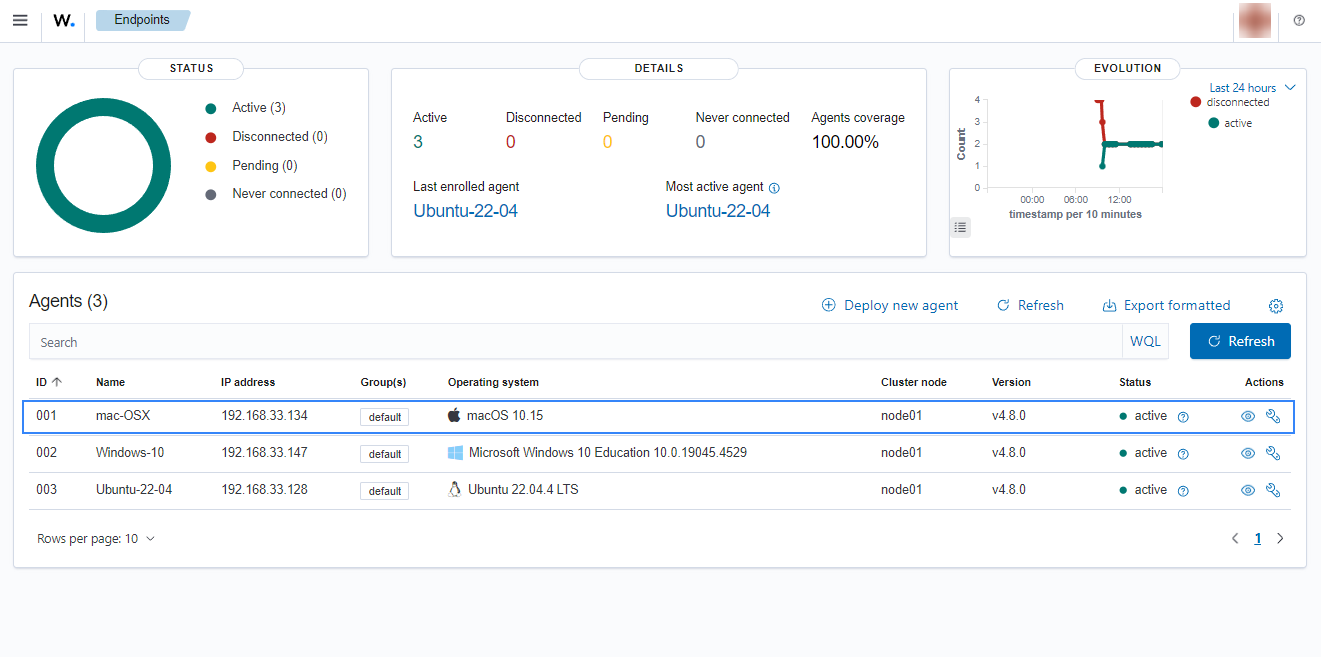
Click on the upper-left menu icon and navigate to Agents management > Summary on the Wazuh dashboard to check for the newly enrolled Wazuh agent and its connection status. If the enrollment was successful, you will have an interface similar to the image below.
Windows
Follow these steps to enroll a Windows endpoint by using certificates for the Wazuh agent verification:
The Wazuh agent installation directory depends on the architecture of the host.
C:\Program Files (x86)\ossec-agentfor 64-bit systems.C:\Program Files\ossec-agentfor 32-bit systems.
Ensure that the signed SSL certificate and key files (
sslagent.certandsslagent.key) have been copied to the endpoint.Using an administrator account, modify the Wazuh agent configuration file located at
C:\Program Files (x86)\ossec-agent\ossec.confand include the following:Wazuh manager IP address or FQDN in the
<client><server><address>section.The local path to the agent certificate and key are in the
<client><enrollment>section.
<client> <server> <address><WAZUH_MANAGER_IP_ADDRESS></address> </server> <enrollment> <agent_certificate_path>/<PATH_TO>/sslagent.cert</agent_certificate_path> <agent_key_path>/<PATH_TO>/sslagent.key</agent_key_path> </enrollment> </client>
Restart the Wazuh agent to make the changes effective.
# Restart-Service -Name wazuh# net stop wazuh # net start wazuh
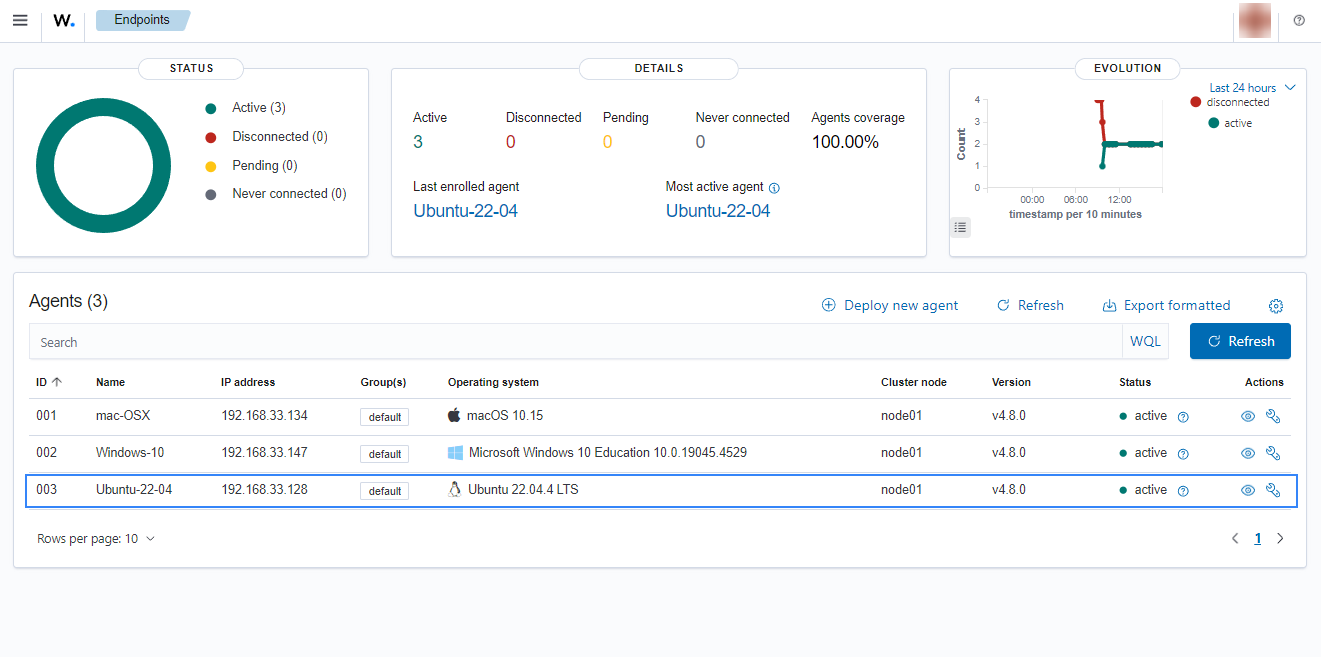
Click on the upper-left menu icon and navigate to Agents management > Summary on the Wazuh dashboard to check for the newly enrolled Wazuh agent and its connection status. If the enrollment was successful, you will have an interface similar to the image below.
macOS
Follow these steps to enroll a macOS endpoint by using certificates for Wazuh agent verification.
Ensure that the signed SSL certificate and key files (
sslagent.certandsslagent.key) for the Wazuh agent have been copied to the endpoint.Launch the terminal, obtain root access, edit the Wazuh agent configuration file located at
/Library/Ossec/etc/ossec.conf, and include the following:The Wazuh manager IP address or FQDN in the
<client><server><address>section.The local path to the agent certificate and key are in the
<client><enrollment>section.
<client> <server> <address><WAZUH_MANAGER_IP_ADDRESS></address> </server> <enrollment> <agent_certificate_path>/<PATH_TO>/sslagent.cert</agent_certificate_path> <agent_key_path>/<PATH_TO>/sslagent.key</agent_key_path> </enrollment> </client>
Restart the Wazuh agent to make the changes effective:
# /Library/Ossec/bin/wazuh-control restart
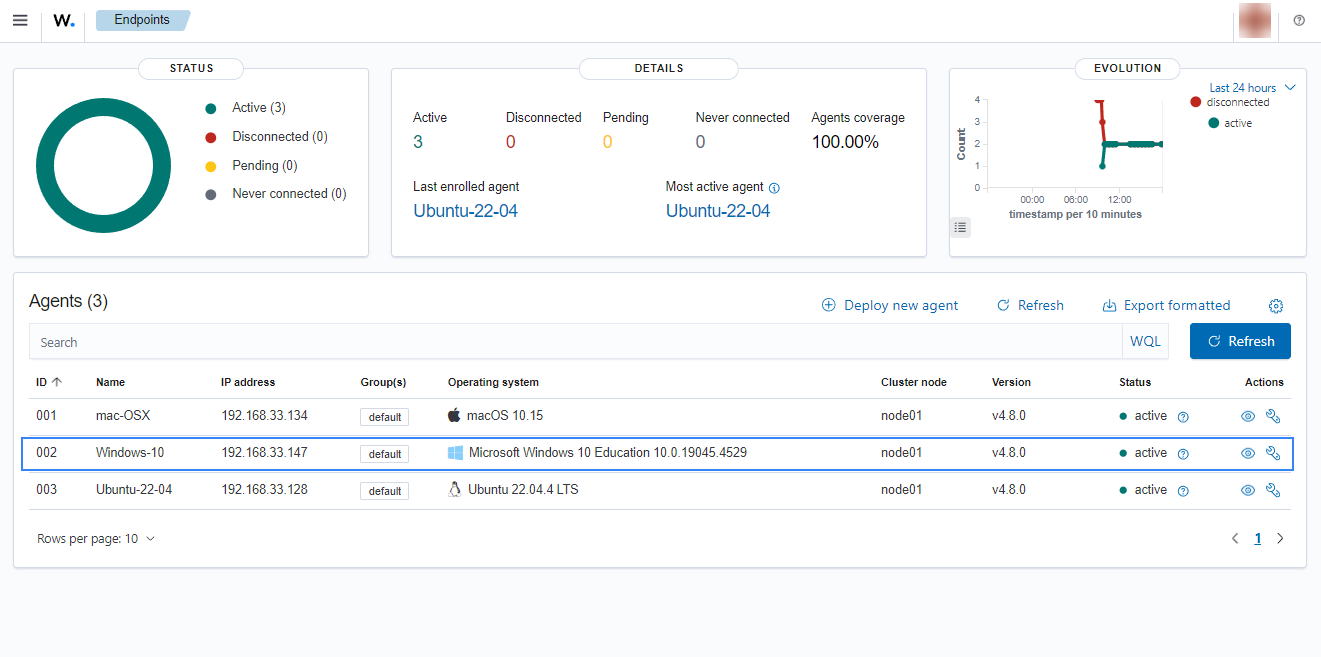
Click on the upper-left menu icon and navigate to Agents management > Summary on the Wazuh dashboard to check for the newly enrolled Wazuh agent and its connection status. If the enrollment was successful, you will have an interface similar to the image below.