LDAP integration
Lightweight Directory Access Protocol (LDAP) is often used for centralizing user authentication and authorization data. It is also used to store structured data such as employee records, contact information, and more. LDAP can handle both authentication and authorization of users accessing the Wazuh dashboard.
Authentication is the process of verifying the identity of users or systems to ensure that they provide valid credentials, such as username and password. Authorization, on the other hand, is granting access to a user or system based on their identity. It retrieves the backend roles for the user and determines what actions they are allowed to perform on the Wazuh dashboard.
In this section, we outline the required configuration to integrate LDAP with the Wazuh platform. The guide assumes you already have an LDAP server or Microsoft Active Directory.
LDAP server configuration
Depending on your LDAP server configuration, you need to create users and groups or use existing ones. You also have to obtain some information from your AD/LDAP server:
Create an OU for the Users (or use an already created OU). Get the DN of the OU, in our example:
ou=people,dc=example,dc=org.Create an OU for the Group(s) (or use an already created OU). Get the DN of the OU, in our example:
ou=Groups,dc=example,dc=org.Create a user with sufficient privileges to bind to the service. Get the DN of the user, in our example, this is
cn=admin,dc=example,dc=org.Create a group where the users with access to Wazuh will be placed, in our example this is the
Administratorandreadonlygroups.Get the FQDN of the LDAP server or Domain Controller.
Map LDAP role to Wazuh dashboard
LDAP can be used for authorization by retrieving the backend roles associated with a user. This backend role can be used to determine the access privileges of a user on the Wazuh dashboard. In this section, we map the LDAP roles to the administrator and read-only roles on the Wazuh dashboard.
Setup administrator role
Follow these steps to create a new role mapping and grant administrator permissions to the backend role.
Configure the
roles_mapping.ymlfile to map the role (CN) we have in our LDAP server to the appropriate Wazuh indexer role. In our case, we map users in theAdministratorgroup in LDAP to theall_accessrole on Wazuh indexer.Edit the
/etc/wazuh-indexer/opensearch-security/roles_mapping.ymlfile and change the following values:all_access: reserved: false hidden: false backend_roles: - "admin" - "Administrator" description: "Maps admin to all_access"
Run the
securityadminscript to load the configuration changes made in theroles_mapping.ymlfile:# export JAVA_HOME=/usr/share/wazuh-indexer/jdk/ && bash /usr/share/wazuh-indexer/plugins/opensearch-security/tools/securityadmin.sh -f /etc/wazuh-indexer/opensearch-security/roles_mapping.yml -icl -key /etc/wazuh-indexer/certs/admin-key.pem -cert /etc/wazuh-indexer/certs/admin.pem -cacert /etc/wazuh-indexer/certs/root-ca.pem -h 127.0.0.1 -nhnv
The
-hflag specifies the hostname or the IP address of the Wazuh indexer node. Note that this command uses 127.0.0.1, set your Wazuh indexer address if necessary.The command output must be similar to the following:
Security Admin v7 Will connect to 127.0.0.1:9200 ... done Connected as "CN=admin,OU=Wazuh,O=Wazuh,L=California,C=US" OpenSearch Version: 2.6.0 Contacting opensearch cluster 'opensearch' and wait for YELLOW clusterstate ... Clustername: wazuh-cluster Clusterstate: GREEN Number of nodes: 1 Number of data nodes: 1 .opendistro_security index already exists, so we do not need to create one. Populate config from /etc/wazuh-indexer/opensearch-security Will update '/rolesmapping' with /etc/wazuh-indexer/opensearch-security/roles_mapping.yml SUCC: Configuration for 'rolesmapping' created or updated Done with success SUCC: Expected 1 config types for node {"updated_config_types":["rolesmapping"],"updated_config_size":1,"message":null} is 1 (["rolesmapping"]) due to: null
Check the value of
run_asin the/usr/share/wazuh-dashboard/data/wazuh/config/wazuh.ymlconfiguration file. Ifrun_asis set tofalse, proceed to the next step.hosts: - default: url: https://127.0.0.1 port: 55000 username: wazuh-wui password: "<WAZUH_WUI_PASSWORD>" run_as: false
If
run_asis set totrue, you need to add a role mapping on the Wazuh dashboard. To map the backend role to Wazuh, follow these steps:Click ☰ to open the menu on the Wazuh dashboard, go to Server management > Security, and then Roles mapping to open the page.
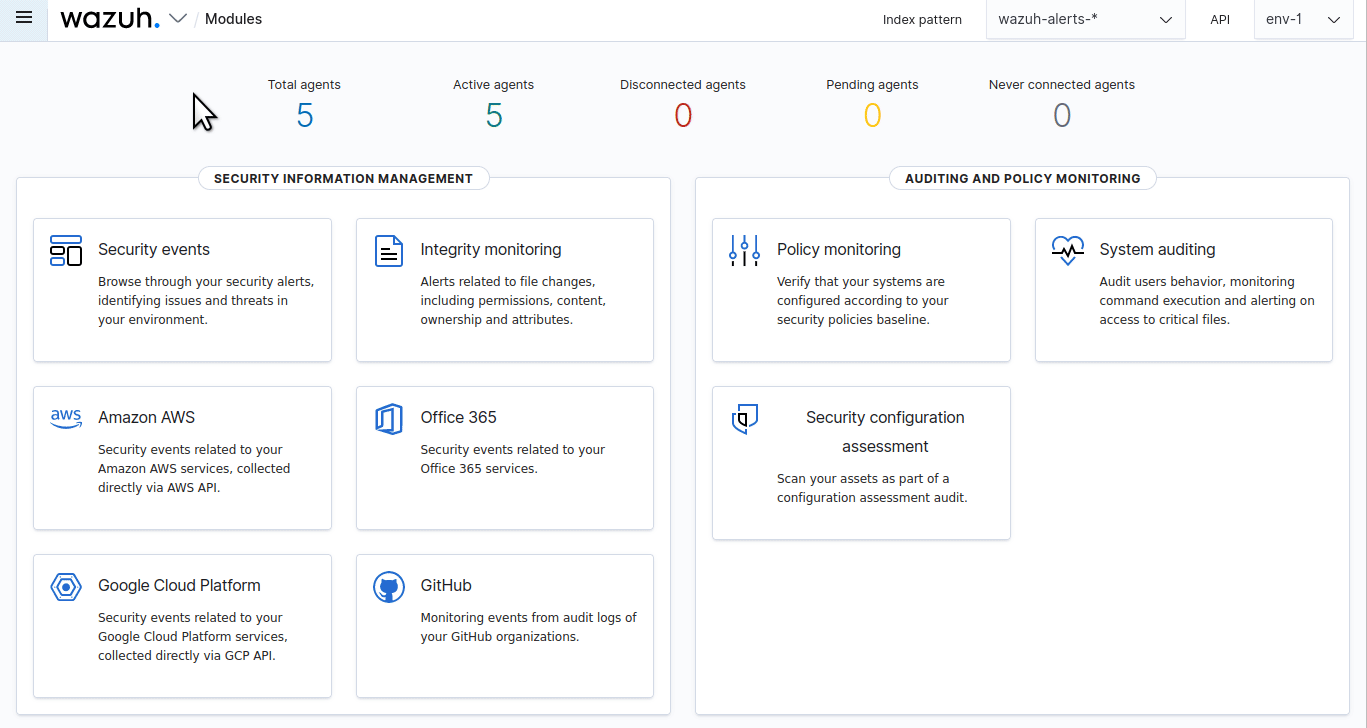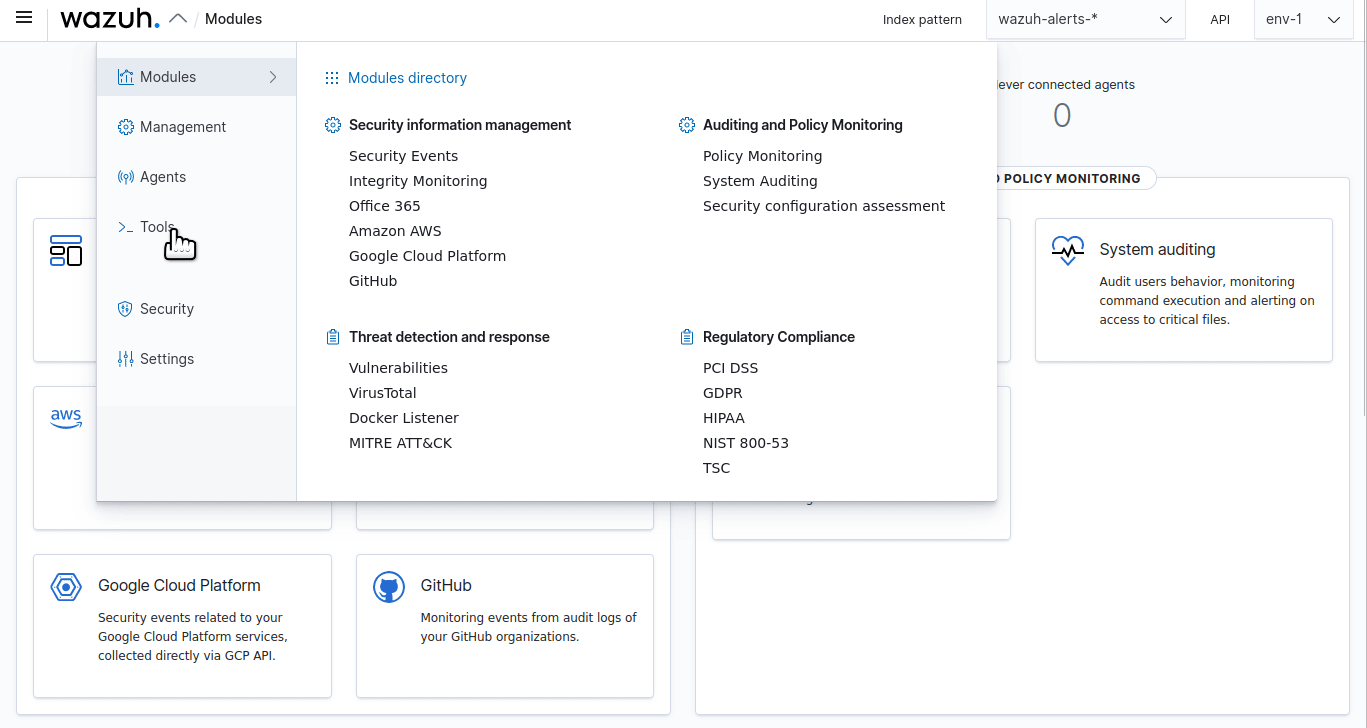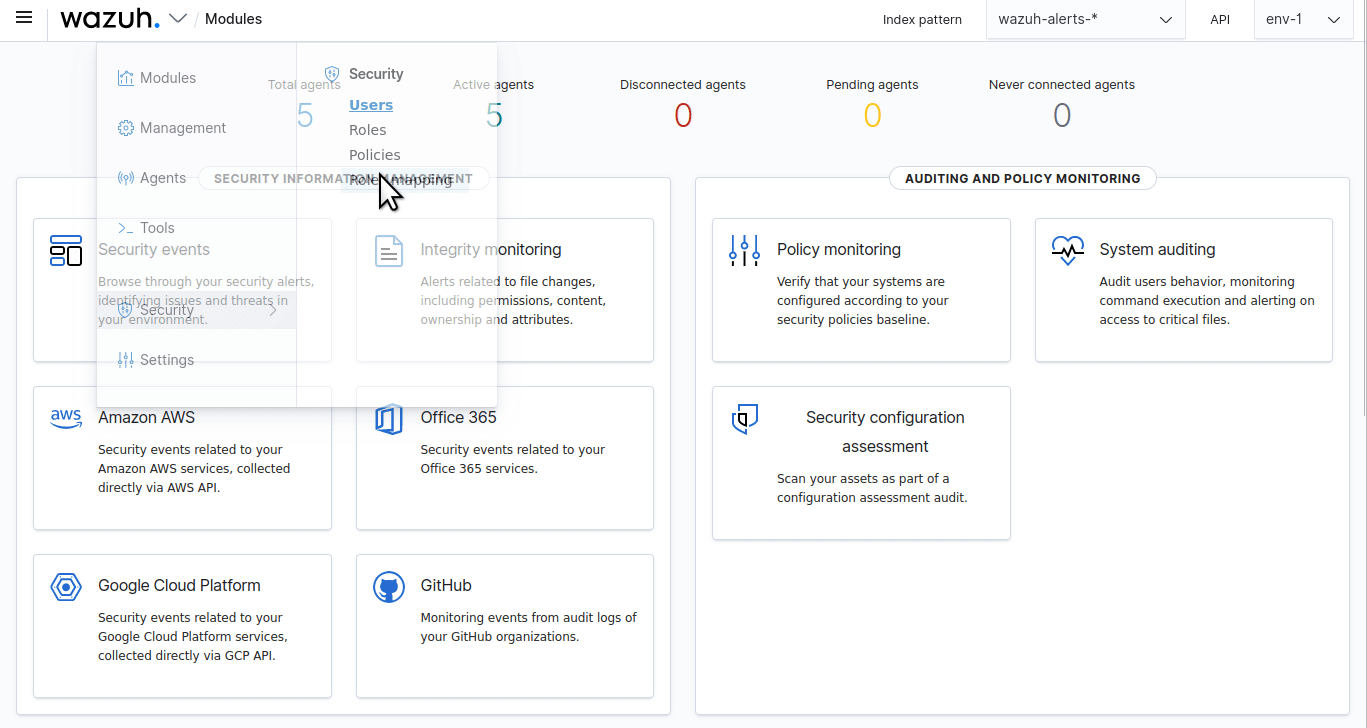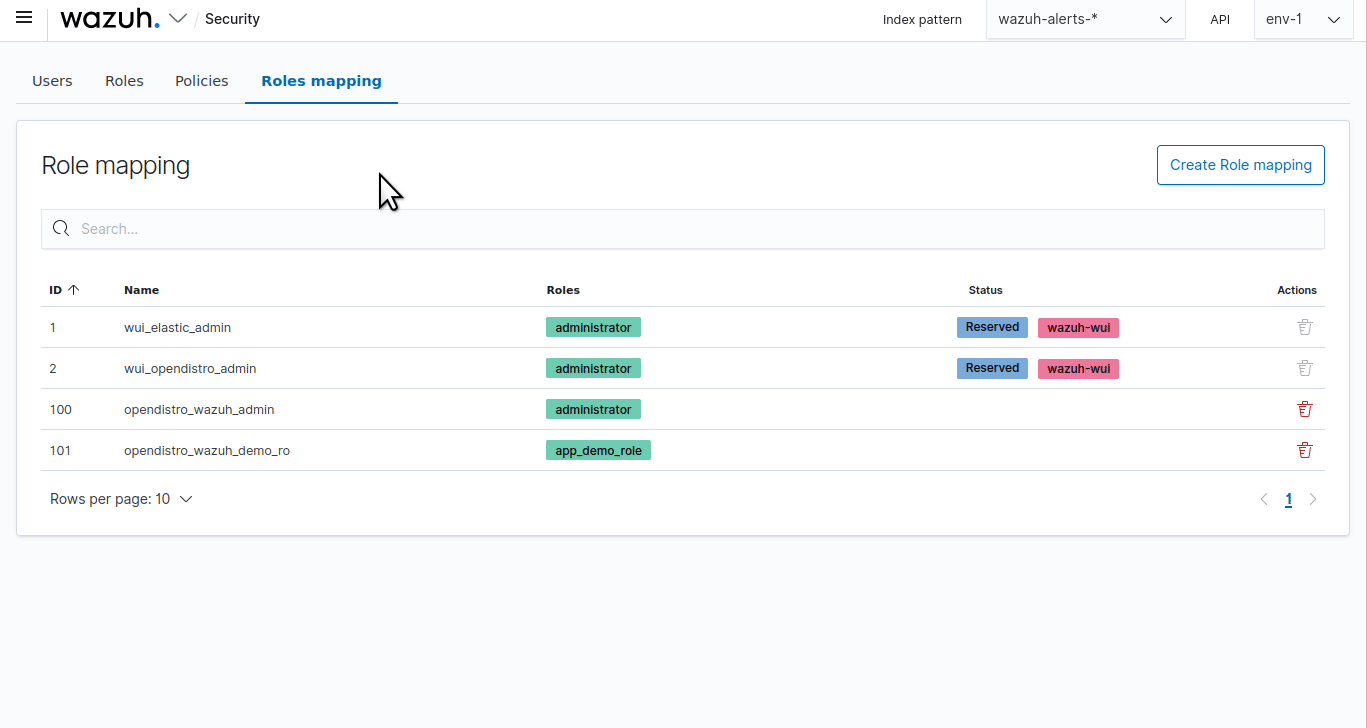
Click Create Role mapping and complete the empty fields with the following parameters:
Role mapping name: Assign a name to the role mapping.
Roles: Select
administrator.Custom rules: Click Add new rule to expand this field.
User field:
backend_roles.Search operation:
FIND.Value: Assign the name of your backend role in your LDAP server. In our case, this is a group named
Administratorwhich contains users with administrator roles
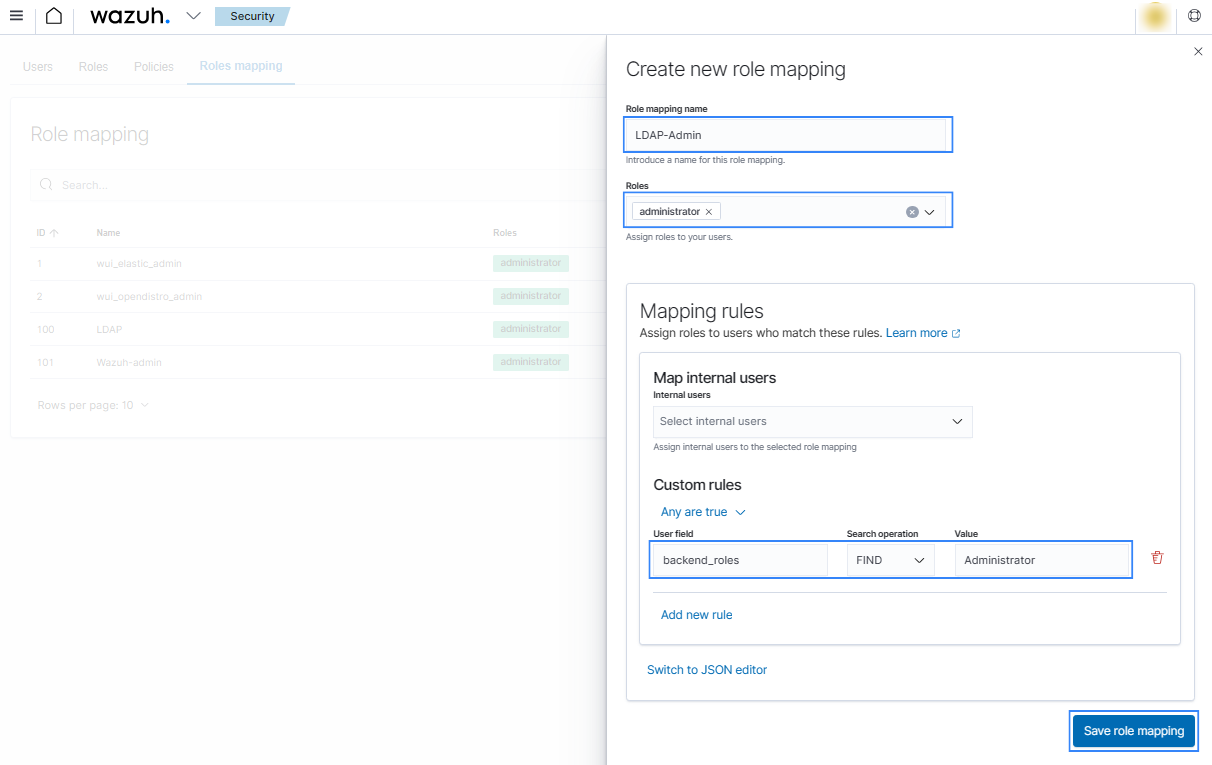
Click Save role mapping to save and map the backend role with Wazuh as administrator.
Restart the Wazuh dashboard service using this command:
# systemctl restart wazuh-dashboard
Test the configuration. To test the configuration, go to your Wazuh dashboard URL and log in with your LDAP details.
Setup read-only role
Follow these steps to create a new role mapping and grant read-only permissions to the backend role.
Log into the Wazuh dashboard as administrator.
Click the upper-left menu icon ☰ to open the options, go to Indexer management > Security, and then Roles to open the roles page.
Click Create role, complete the empty fields with the following parameters, and then click Create to complete the task.
Name: Assign a name to the role.
Cluster permissions: cluster_composite_ops_ro
Index: *
Index permissions: read
Tenant permissions: global_tenant and select the Read only option.
Select the newly created role.
Select the Mapped users tab and click Manage mapping.
Under Backend roles, assign the name of the read-only role you have in your LDAP server and click on Map to confirm the action. In our case, the backend role (CN) is
readonly.
Check the value of
run_asin the/usr/share/wazuh-dashboard/data/wazuh/config/wazuh.ymlconfiguration file. Ifrun_asis set tofalse, proceed to the next step.hosts: - default: url: https://127.0.0.1 port: 55000 username: wazuh-wui password: "<WAZUH_WUI_PASSWORD>" run_as: false
If
run_asis set totrue, you need to add a role mapping on the Wazuh dashboard. To map the backend role to Wazuh, follow these steps:Click the upper-left menu icon ☰ to open the menu on the Wazuh dashboard, go to Server management > Security, and then Roles mapping to open the page.

Click Create Role mapping and complete the empty fields with the following parameters:
Role mapping name: Assign a name to the role mapping.
Roles: Select
readonly.Custom rules: Click Add new rule to expand this field.
User field:
backend_roles.Search operation:
FIND.Value: Assign the name of your backend role in your LDAP server. In our case, this is a group named
readonlywhich contains users with read only roles.
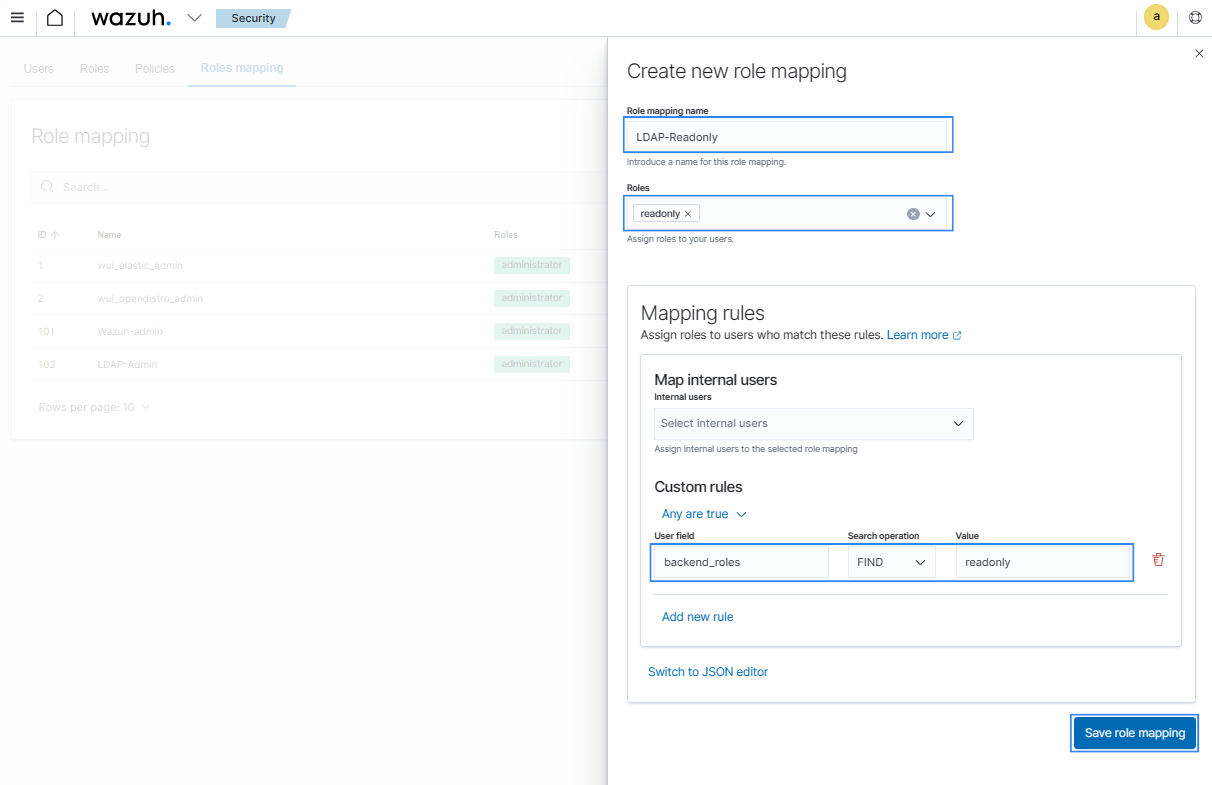
Click Save role mapping to save and map the backend role with Wazuh as read-only.
Restart the Wazuh dashboard service using this command:
# systemctl restart wazuh-dashboard
Test the configuration. To test the configuration, go to your Wazuh dashboard URL and log in with your LDAP details.