Log data analysis
The logs generated from devices, systems, and applications are useful for detecting security incidents and system errors. The Wazuh log data analysis module collects and analyzes logs from various sources such as applications, endpoints, network devices, cloud workloads, and other security solutions. The data collected and analyzed by the log data analysis module helps in threat detection, prevention, and active response. Refer to the ruleset section for more information.
The Wazuh log data analysis module can help comply with the following HIPAA sections:
Audit Controls §164.312(b): “A covered entity or business associate must, in accordance with § 164.306 implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information.”
This section of the HIPAA standard requires that tools be in place to log activities on all systems containing health data. The activities logged may include: authentication, system or application failure, and file read, write, or modification events.
Security Incident Procedures §164.308(a)(6)(i) - Response and reporting: “Identify and respond to suspected or known security incidents; mitigate, to the extent practicable, harmful effects of security incidents that are known to the covered entity or business associate; and document security incidents and their outcomes.”
This section of the HIPAA standard requires you to identify and mitigate security incidents and threats. The log data analysis module helps identify these incidents by analysis of endpoint activities.
Person or Entity Authentication §164.312(d): “A covered entity or business associate must, in accordance with § 164.306 implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.”
This section of the HIPAA standard requires you to log and review user authentication activities. The analysis of these activities helps determine if they are legitimate. The Wazuh log data analysis module analyzes logs to generate alerts when suspicious activities are detected.
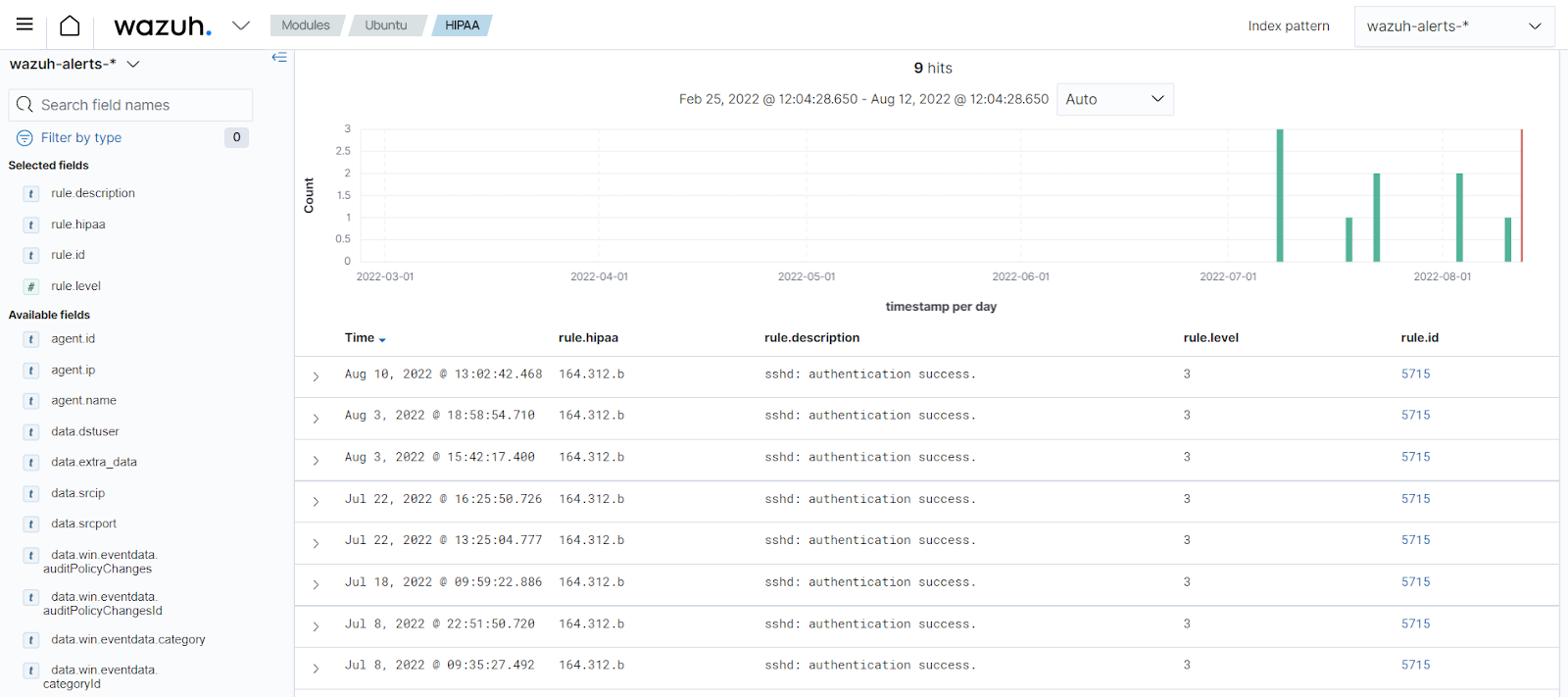
Use case: SSH authentication
In this use case, the Wazuh server receives SSH authentication logs from an Ubuntu 22.04 endpoint. The log data analysis module subsequently decodes and evaluates these logs against Wazuh rules to find if they match the behavior of interest. For example, successful authentication.
Below is a rule to detect and alert on a successful SSH authentication:
Rule 5715 - sshd: authentication success: When a user successfully logs into an endpoint via SSH, this rule generates an alert. The alert includes the username, timestamp, and authentication status (success, or failure). The image below shows the alerts generated on the Wazuh dashboard for successful SSH authentications: