Vulnerability detection
Wazuh is able to detect vulnerabilities in the applications installed on agents using the Vulnerability Detection module. This software audit is performed by querying our Cyber Threat Intelligence (CTI) API for vulnerability content documents. We aggregate vulnerability information into the CTI repository from external vulnerability sources indexed by Canonical, Debian, Red Hat, Arch Linux, Amazon Linux Advisories Security (ALAS), Microsoft, CISA, and the National Vulnerability Database (NVD). We also maintain the integrity of our vulnerability data and the vulnerabilities repository updated, ensuring the solution checks for the latest CVEs. The Vulnerability detection module correlates this information with data from the endpoint application inventory.
The vulnerability detection module helps to meet the following PCI DSS requirements:
Requirement 6 - Develop and Maintain Secure Systems and Software: Actors with bad intentions can use security vulnerabilities to gain privileged access to systems. Many of these vulnerabilities are fixed by vendor-provided security patches, which must be installed by the entities that manage the systems. All system components must have all appropriate software patches to protect against the exploitation and compromise of account data by malicious individuals and malicious software.
The goal of this requirement is to ensure that systems and software have the appropriate security patches for discovered vulnerabilities to prevent compromise.
Requirement 11 - Test Security of Systems and Networks Regularly: Vulnerabilities are being discovered continually by malicious individuals and researchers, and being introduced by new software. System components, processes, and bespoke and custom software should be tested frequently to ensure security controls continue to reflect a changing environment.
The goal of this requirement is to ensure that systems and networks are regularly tested to confirm their security status. These tests include penetration testing and vulnerability scans.
The Wazuh vulnerability detection module helps to meet the above requirements. The Wazuh agent collects a list of installed applications and OS information and sends it periodically to the manager. The Wazuh manager compares this information with vulnerability content documents to determine what vulnerabilities exist on an endpoint. You can find more details on configuring vulnerability detection in the vulnerability detection section of the documentation.
Use cases
Below are some PCI DSS requirements use cases that can be met with the vulnerability detection module:
PCI DSS 6.3 requires to identify and address security vulnerabilities. While vulnerability detection is enabled by default, you can still check everything is properly configured. For example, you can add the following block to the shared agent configuration file
/var/ossec/etc/shared/default/agent.confto make sure to detect vulnerabilities in packages installed on Ubuntu 20.04 endpoints.<wodle name="syscollector"> <disabled>no</disabled> <interval>1h</interval> <packages>yes</packages> </wodle>
Make sure vulnerability detection is enabled by checking the
/var/ossec/etc/ossec.confmanager configuration file.<vulnerability-detection> <enabled>yes</enabled> <index-status>yes</index-status> <feed-update-interval>60m</feed-update-interval> </vulnerability-detection> <indexer> <enabled>yes</enabled> <hosts> <host>https://0.0.0.0:9200</host> </hosts> <ssl> <certificate_authorities> <ca>/etc/filebeat/certs/root-ca.pem</ca> </certificate_authorities> <certificate>/etc/filebeat/certs/filebeat.pem</certificate> <key>/etc/filebeat/certs/filebeat-key.pem</key> </ssl> </indexer>
If you made changes, restart the manager to apply them.
# systemctl restart wazuh-manager
# service wazuh-manager restart
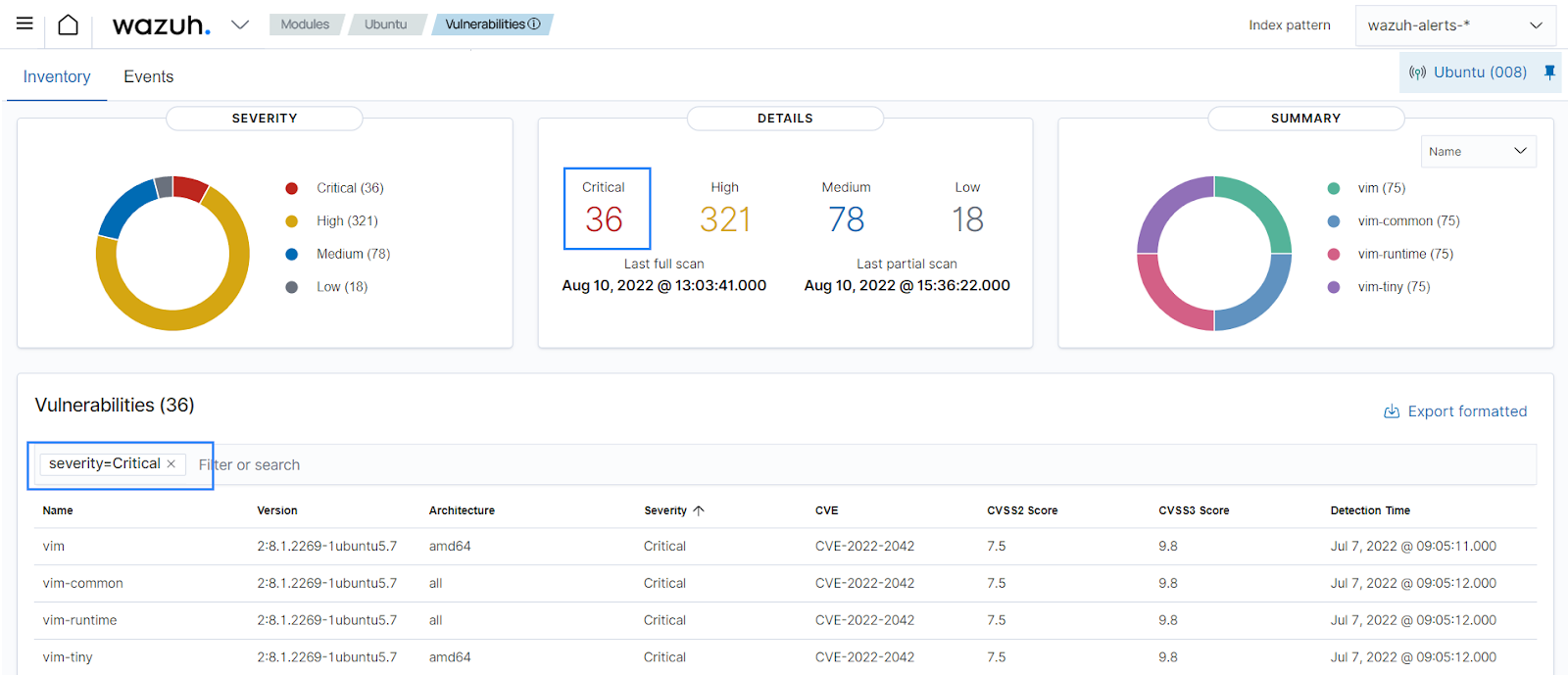
You can see the results on the Wazuh dashboard. They include details of vulnerable packages, for example, vulnerabilities in the
vimapplication. When you select a specific vulnerability detected, the Wazuh dashboard shows an overview of the issue and its status on the agent.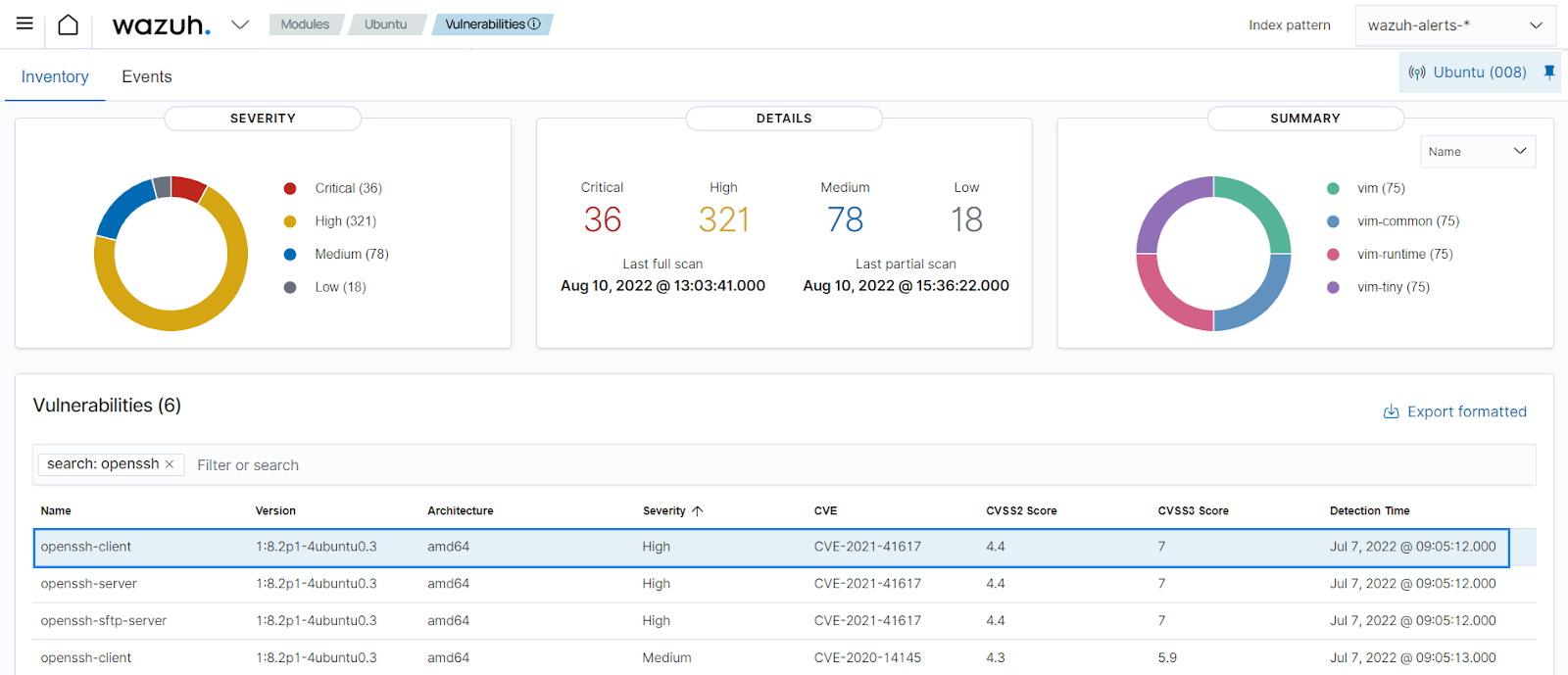
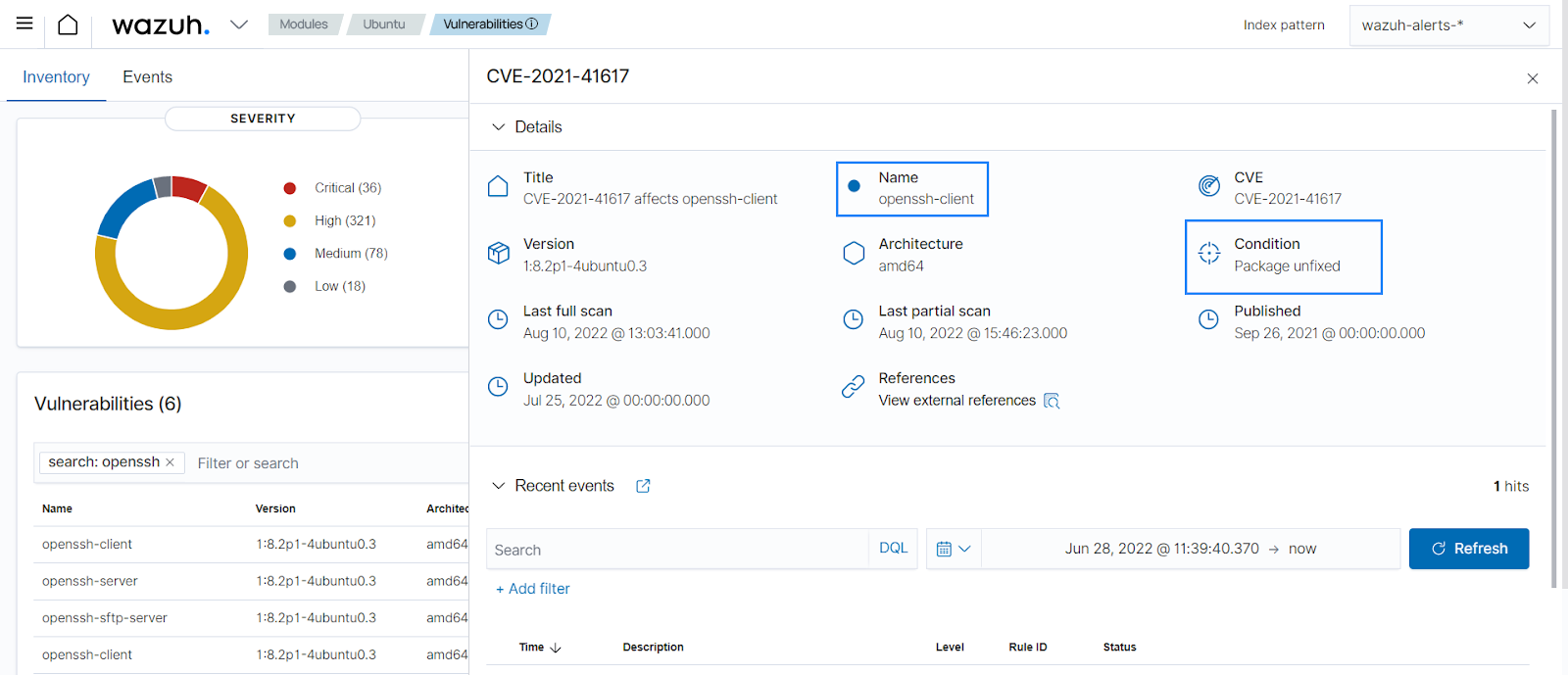
PCI DSS 11.3 requires to identify, prioritize, and address external and internal vulnerabilities regularly. The Wazuh vulnerability detection gives details on the severity rating and the CVSS scores. This helps to prioritize the vulnerabilities. From the vulnerability detection dashboard, you can filter by vulnerability severity rating to prioritize its remediation.