How it works
The Wazuh agent uses the Syscollector module to collect detailed system inventory data, including information about the operating system and installed packages or applications. The collected data is periodically sent to the Wazuh server and stored in a local SQLite database. Each agent’s inventory is maintained separately and continuously updated to reflect changes on the monitored endpoint.
The Vulnerability Detection module on the Wazuh server analyzes this inventory data by correlating it with vulnerability information from the Wazuh Cyber Threat Intelligence (CTI) platform. When the module identifies a match between a known vulnerability (identified by a CVE ID) and a software version on a monitored endpoint, it flags it as a detected vulnerability. A package is marked as vulnerable when its version falls within the affected range of a CVE. The module generates alerts to display the results; the findings are stored in a general vulnerability inventory. This inventory is filterable by agent and contains vulnerability data that can be queried to review alerts and details about vulnerabilities.
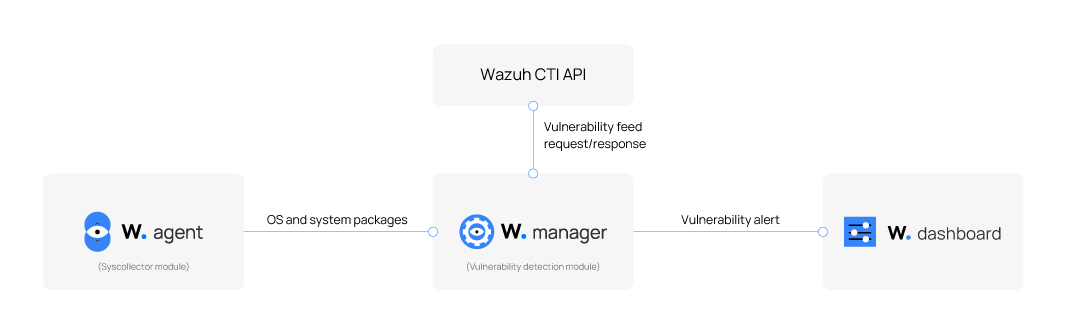
For Microsoft Windows systems and certain Microsoft products, the Vulnerability Detection module includes the hotfixes option in the Wazuh agent's Syscollector configuration. Enabling this option allows the module to detect packages that users have patched. When a patch is detected, the module uses information provided by Microsoft to verify whether the patch resolves the relevant CVEs. If it does, the module updates the status of the vulnerabilities in the inventory.
Wazuh Cyber Threat Intelligence (CTI) platform
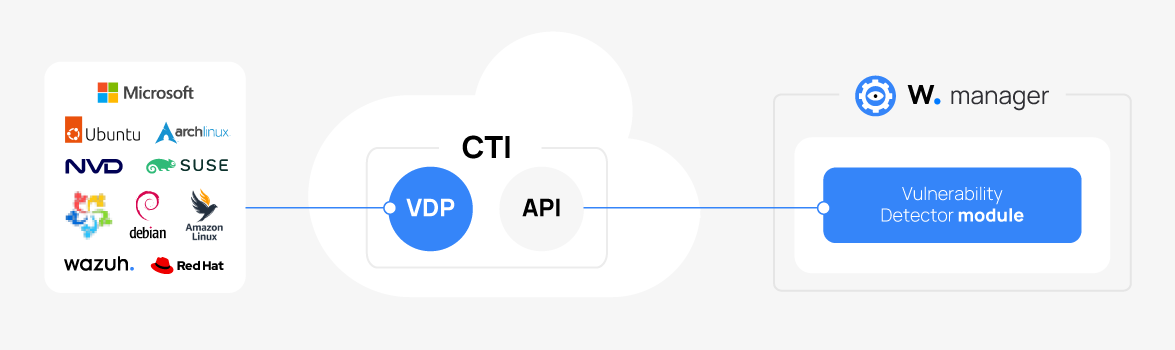
The Wazuh Cyber Threat Intelligence (CTI) platform is a publicly accessible service that collects, analyzes, and disseminates actionable information on emerging cyber threats and vulnerabilities. The Wazuh CTI platform aggregates vulnerability data from various sources, including operating system vendors and public vulnerability databases. This data is consolidated into a unified, reliable repository used by the Wazuh Vulnerability Detection module.
Vulnerability data sources
The Wazuh CTI platform gathers vulnerability data from a defined set of trusted sources, including official feeds from operating system vendors and reputable security databases. The sources include:
Operating system vendors: AlmaLinux, Amazon Linux, ArchLinux, Ubuntu (Canonical), Debian, Fedora, Oracle Linux, Red Hat Enterprise Linux (RHEL), Rocky Linux, and SUSE Linux Enterprise.
Security databases: Microsoft Security Updates (MSU), National Vulnerability Database (NVD), Open Source Vulnerabilities (OSV), Cybersecurity and Infrastructure Security Agency (CISA).
Vulnerability Detector Provider (VDP)
A core component of the CTI platform is the Vulnerability Detector Provider (VDP). The VDP organizes vulnerability data from multiple vendors into a standardized format and produces consistent, high-quality intelligence. This ensures the Vulnerability Detection module can identify vulnerabilities across various operating systems, including Windows, CentOS, Red Hat Enterprise Linux, Ubuntu, Debian, Amazon Linux, Arch Linux, SUSE, and macOS.
The VDP performs three key functions:
Content migration: This process fetches raw vulnerability data from vendors and normalizes it into a common structure using the CVE JSON v5 format. This normalization enables the consolidation of diverse vulnerability information into a reliable, centralized repository.
Data sanitization: This process enhances the normalized data by fixing inconsistencies (e.g., version mismatches and typos) and completing missing fields. This ensures the data's accuracy and reliability.
Content merging: This process combines vendor-specific content with internally maintained intelligence data. This includes product name mappings, product translations, and OS base rules. This results in a single, unique document for each CVE.
This final document is published through the CTI API, making it accessible to all Wazuh managers. The publication process includes traceability features to ensure only updated content is published. The Wazuh Vulnerability Detection module retrieves vulnerability intelligence by querying the CTI API or an offline local repository. It compares the newly fetched content with previously stored data to detect updates. This allows the module to continuously identify vulnerabilities on monitored endpoints with high accuracy and coverage.
Accessing Wazuh CTI
The Wazuh CTI API powers the public threat intelligence website and the vulnerability detection feature within the Wazuh XDR & SIEM unified platform. The Wazuh CTI platform is accessible either through the Wazuh CTI website or from the Wazuh dashboard by navigating to the Vulnerability Detection module.
Wazuh CTI Website
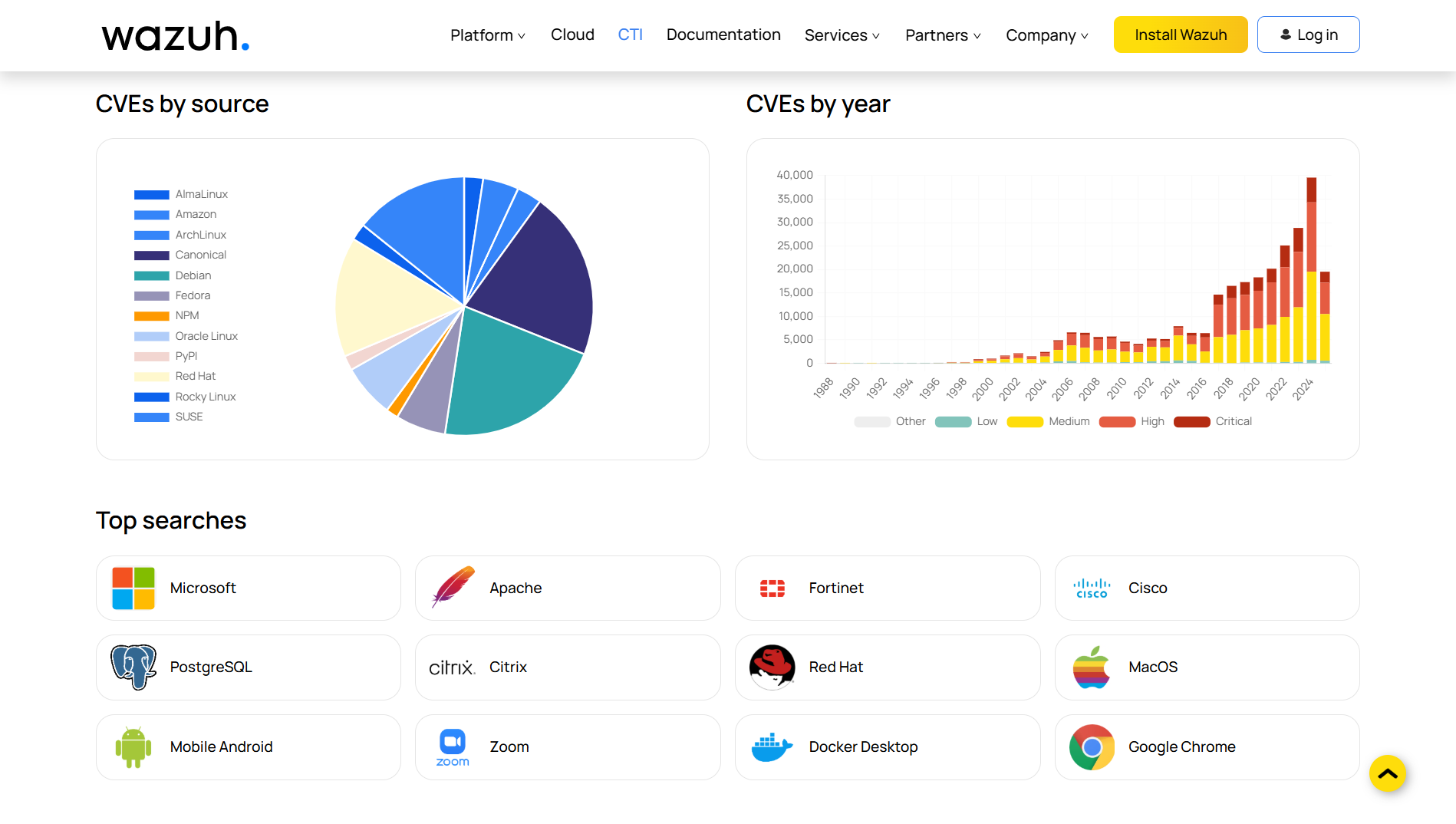
The Wazuh CTI website is open to the public and requires no registration or Wazuh installation. It features a search tool for filtering vulnerabilities by CVE ID, affected application, CVSS score, severity, and publication date, with customizable sorting.
From the Wazuh dashboard
You can access the Wazuh CTI platform directly through the vulnerability detection page in the Wazuh dashboard. Navigate to Vulnerability Detection > Inventory, then click the vulnerability ID of any listed vulnerability to open detailed threat intelligence on the Wazuh CTI website.
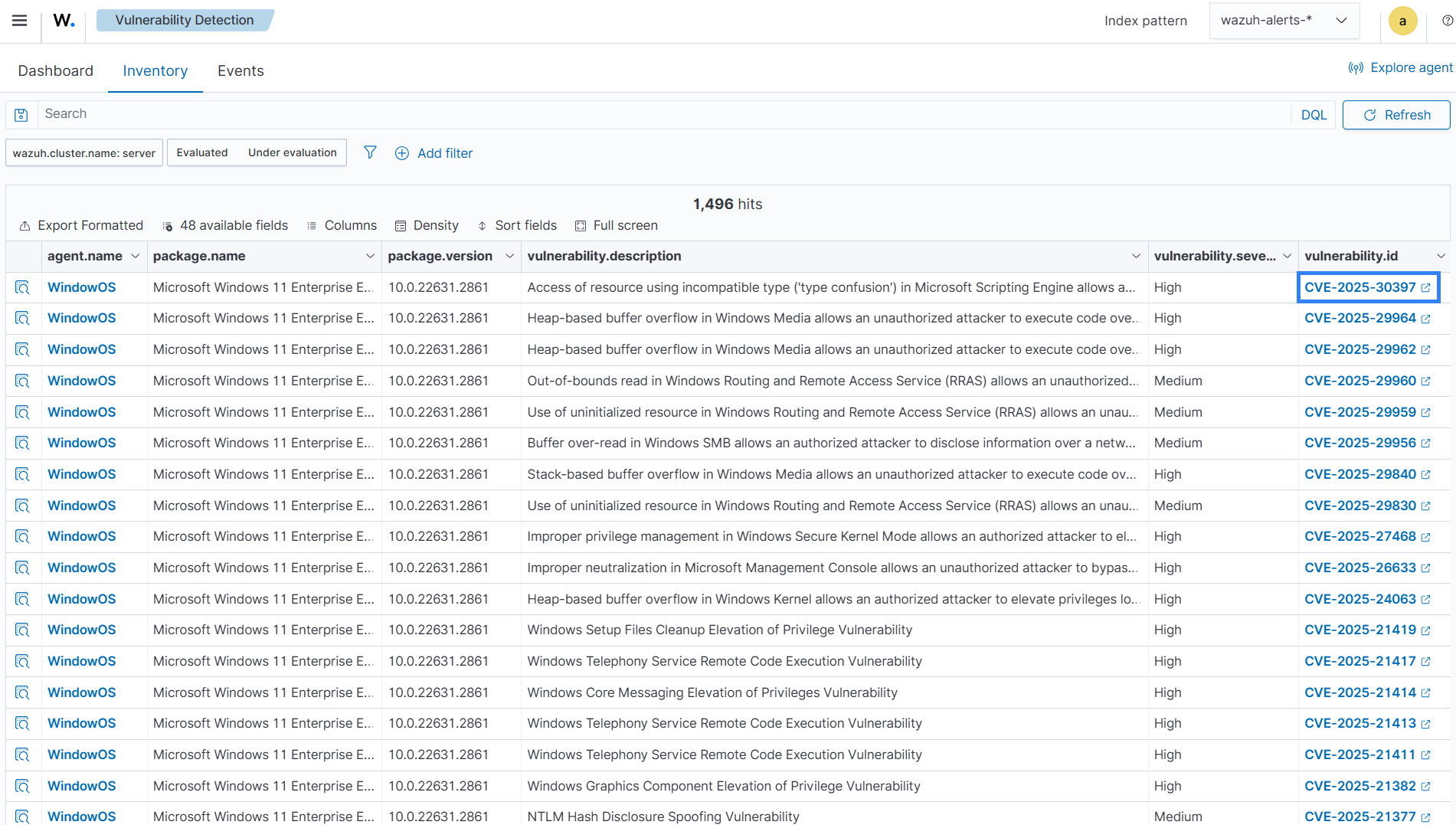
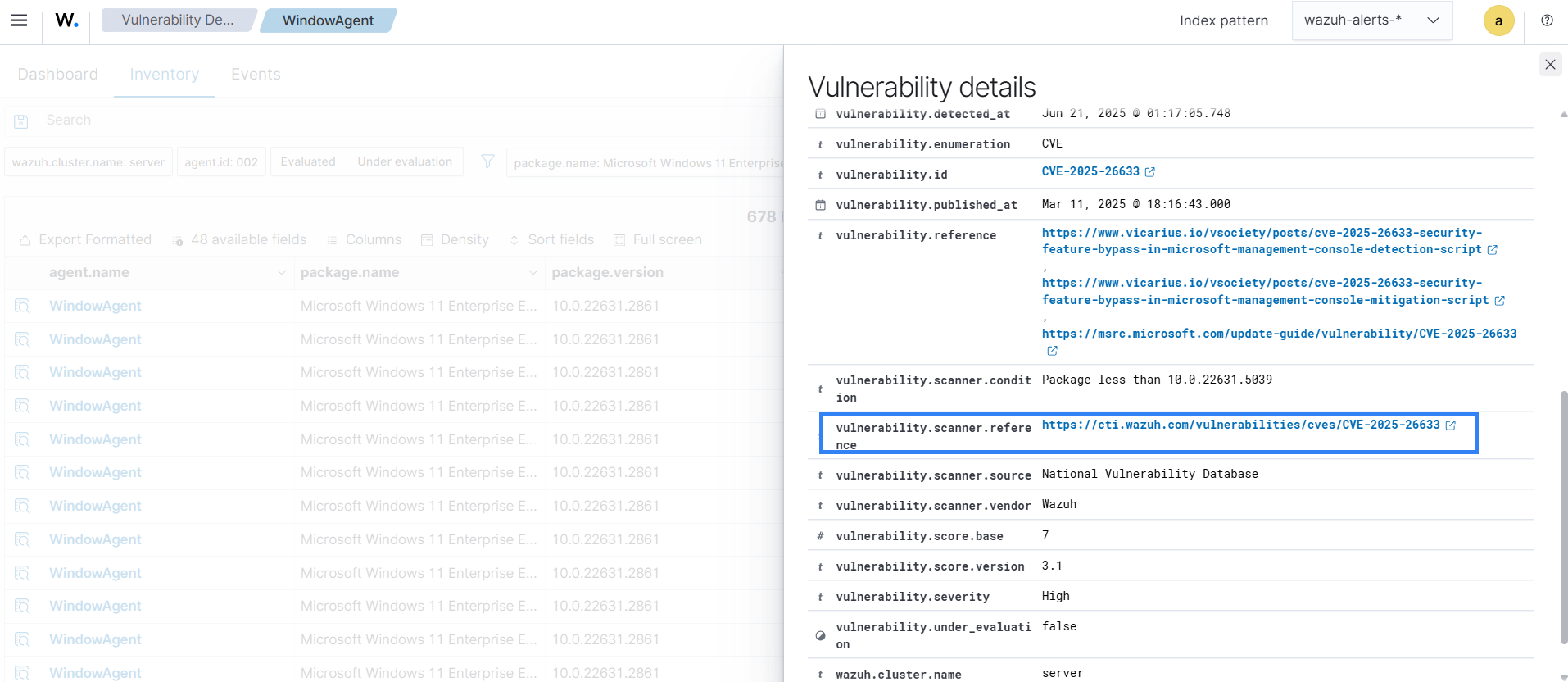
You can also access the Wazuh CTI platform by clicking the Inspect vulnerability details icon. Then, navigate to the reference section and click the provided URL to be redirected to the Wazuh CTI page, which contains detailed information about the vulnerability.
Alert generation
The Vulnerability Detection module generates alerts when new vulnerabilities are detected or existing vulnerabilities are resolved due to package updates, removals, or system upgrades. While these conditions are necessary, they are not always sufficient. Alert generation depends on specific detection scenarios.
Operating system alerts
Operating system alerts are not generated during the initial inventory scan. When a Wazuh agent syncs with the Wazuh manager for the first time, it does not recognize changes to the OS version or recent patches as new events. Alerts are only triggered in subsequent scans if a change in OS version or patch state is detected.
Packages alerts
Alerts related to package changes are triggered only when a vulnerability is added or removed from the inventory due to installing or removing a package. This requires that the event be captured during a scheduled Syscollector scan. If the changes are made to packages while the Wazuh agent is in a stopped state, no alerts will be triggered. Also, if these changes are only detected after the Wazuh agent is restarted, no alert will be triggered.
Other factors to consider regarding alert generation include:
Cluster environment: When a Wazuh agent reconnects to a different manager node in a clustered deployment, it will synchronize its inventory with the new node. However, this initial sync does not generate alerts, even if changes are present.
Content update: When the vulnerability content (CVE definitions, translations, or mapping rules) is updated on the server, all agents are re-evaluated to ensure their results remain accurate. No alerts are generated during the initial sync triggered by the vulnerability content updates.
Viewing vulnerability data
You can view the vulnerability data of each monitored endpoint from the Wazuh dashboard. To do this:
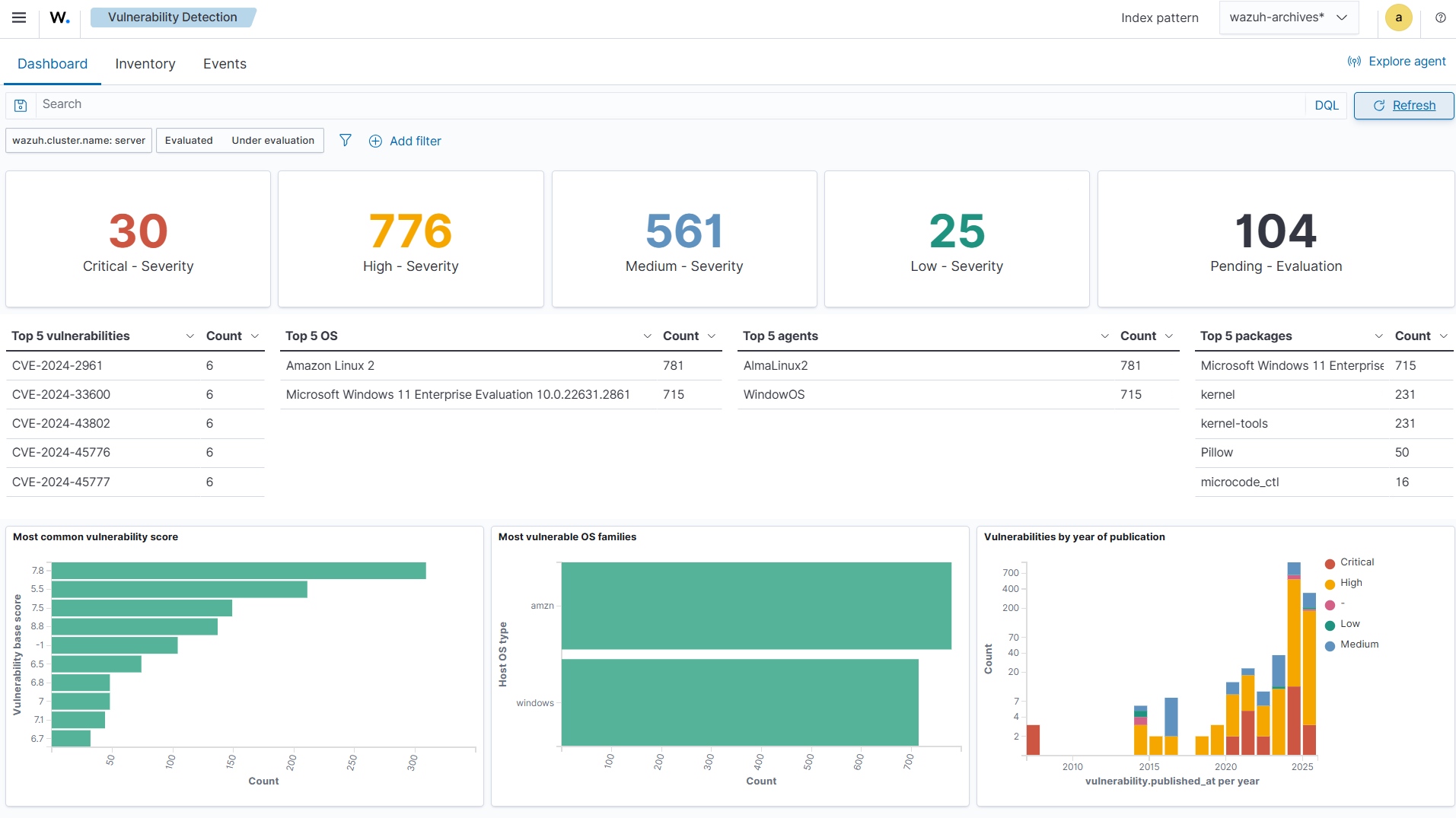
Click on Threat intelligence from the menu (☰), then select Vulnerability Detection. The Dashboard tab provides a visual summary of vulnerabilities by severity, score, and asset. It links each CVE to affected systems, with charts showing the trend over time, highlighting impacted agents.
Note
To view the vulnerability data for a specific agent, select an agent from your Wazuh dashboard and navigate to the Vulnerability detection module.
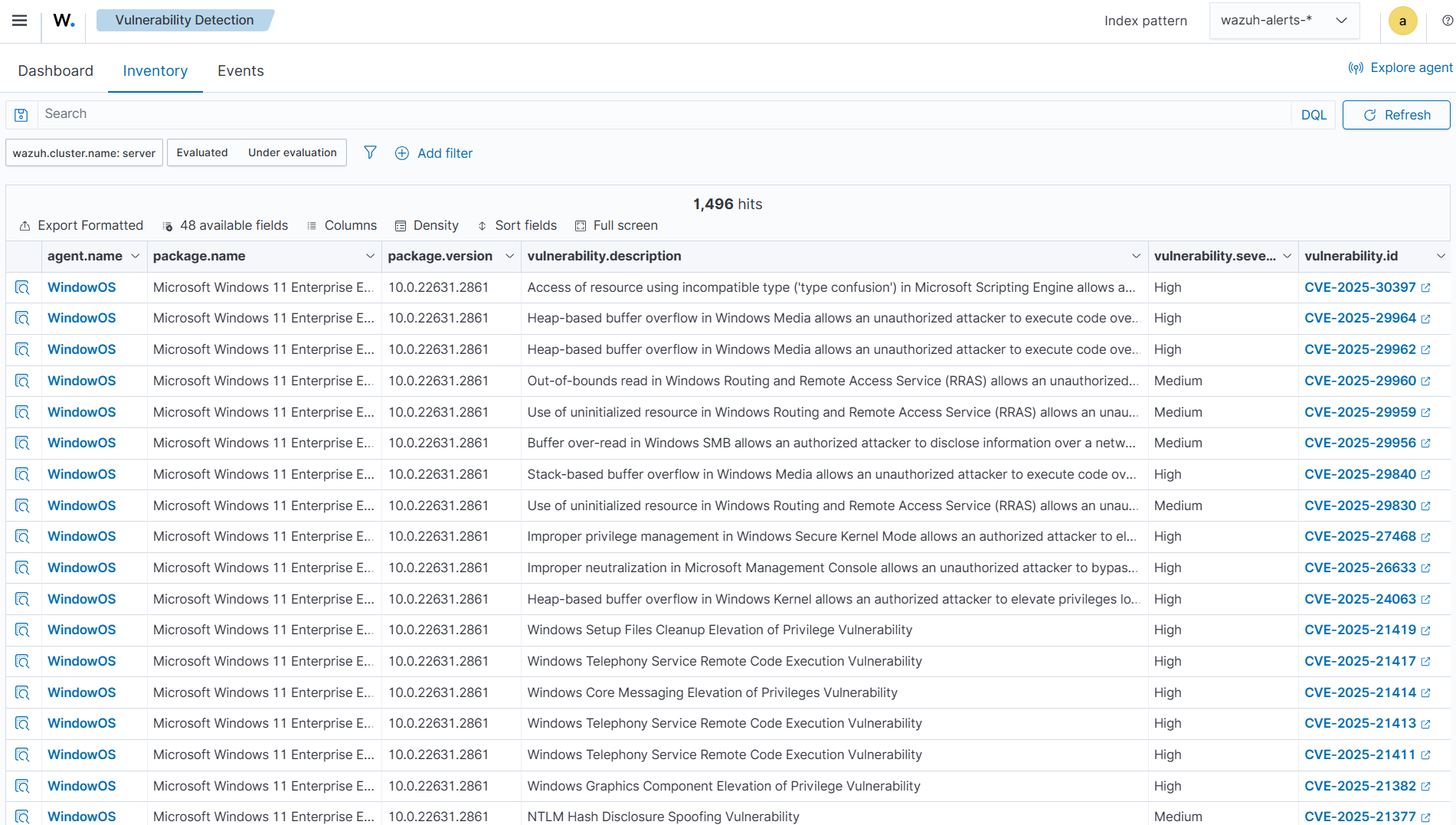
Click on the Inventory tab. This tab shows the list of all vulnerabilities detected on the Wazuh agents.
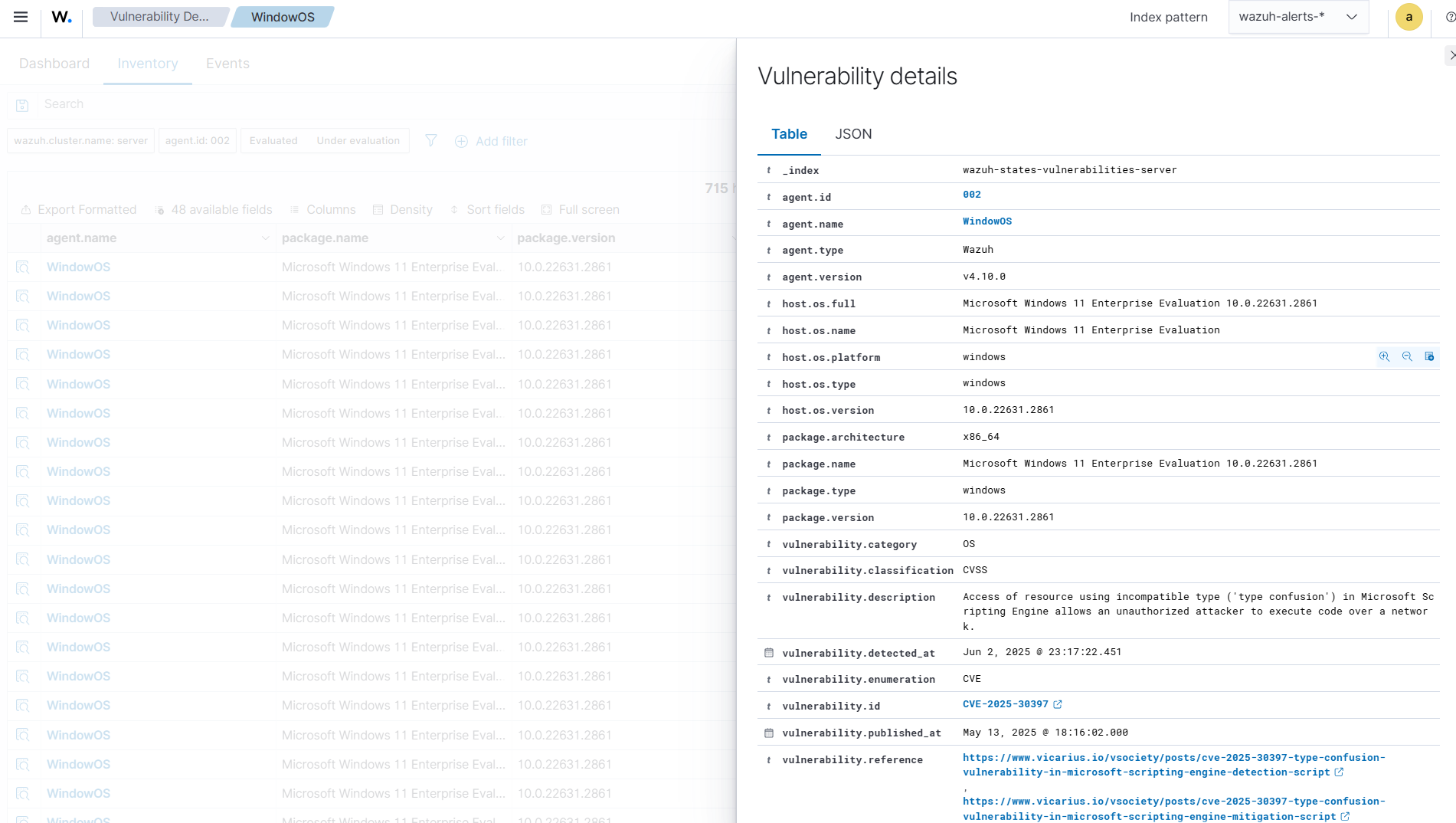
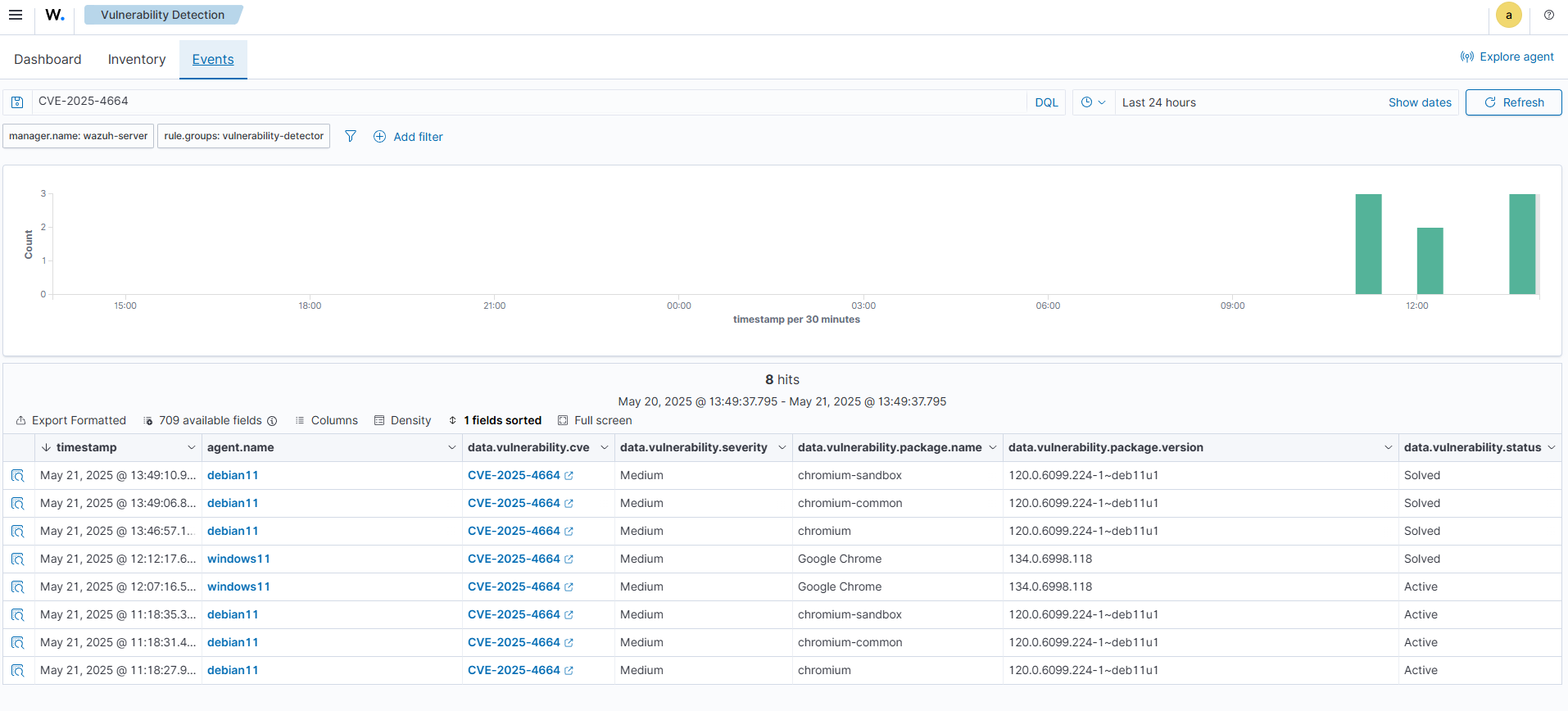
Click on the Events tab. This shows the alerts generated for vulnerabilities detected on Wazuh agents. An alert is generated when vulnerabilities are detected or remediated. It also contains key information such as detection timestamps, severity levels, package names and versions, and the current vulnerability status (e.g., Active or Solved).
Note
As mentioned earlier, alert generation depends on specific detection scenarios. For more information, refer to the Alert generation section.
Each vulnerability alert contains key fields such as:
CVE: The Common Vulnerabilities and Exposures identifier for the corresponding vulnerability.
Rule description: Short description of the impact of the vulnerability.
Description: Broad description of the vulnerability.
Severity: Impact of the vulnerability in terms of severity.
Package: Information about the affected package, including why the package is marked as vulnerable.
Status: The current status of the vulnerability (Active or Solved )
Reference: Wazuh CTI website URL, providing additional information on the vulnerability.
Sample Alert
{
"_index": "wazuh-states-vulnerabilities-server",
"_id": "002_f54fb41d71bab144a6022ca87fbad36902348cce_CVE-2025-4050",
"_score": 0,
"_source": {
"agent": {
"id": "002",
"name": "WindowOS",
"type": "Wazuh",
"version": "v4.10.0"
},
"host": {
"os": {
"full": "Microsoft Windows 11 Enterprise Evaluation 10.0.22631.2861",
"name": "Microsoft Windows 11 Enterprise Evaluation",
"platform": "windows",
"type": "windows",
"version": "10.0.22631.2861"
}
},
"package": {
"architecture": "x86_64",
"name": "Google Chrome",
"size": 0,
"type": "win",
"version": "134.0.6998.118"
},
"vulnerability": {
"category": "Packages",
"classification": "CVSS",
"description": "Out of bounds memory access in DevTools in Google Chrome prior to 136.0.7103.59 allowed a remote attacker who convinced a user to engage in specific UI gestures to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: Medium)",
"detected_at": "2025-06-03T05:35:59.947Z",
"enumeration": "CVE",
"id": "CVE-2025-4050",
"published_at": "2025-05-05T18:15:43Z",
"reference": "https://issues.chromium.org/issues/409342999, https://chromereleases.googleblog.com/2025/04/stable-channel-update-for-desktop_29.html",
"scanner": {
"condition": "Package less than 136.0.7103.59",
"reference": "https://cti.wazuh.com/vulnerabilities/cves/CVE-2025-4050",
"source": "National Vulnerability Database",
"vendor": "Wazuh"
},
"score": {
"base": 8.8,
"version": "3.1"
},
"severity": "High",
"under_evaluation": false
},
"wazuh": {
"cluster": {
"name": "server"
},
"schema": {
"version": "1.0.0"
}
}
},
"fields": {
"vulnerability.detected_at": [
"2025-06-03T05:35:59.947Z"
],
"vulnerability.published_at": [
"2025-05-05T18:15:43.000Z"
]
}
}
Compatibility matrix
Wazuh continuously expands its compatibility list to include new operating systems. The following table highlights the operating systems officially supported by the Vulnerability Detection module. While other systems are also supported, we don't guarantee full detection.
Vulnerability Information Provider |
Operating Systems and Versions |
Provider Security Website |
|---|---|---|
AlmaLinux |
|
|
Amazon Linux |
|
|
Arch Linux |
|
|
Canonical |
|
|
Debian |
|
|
Fedora Linux |
The same versions reported by the Fedora feed — generally, all versions. |
|
NPM |
- |
|
NVD |
Windows: The same versions reported by the NVD feed — generally, all versions. |
|
macOS: The same versions reported by the NVD feed — generally, all versions. |
||
Oracle Linux |
The same versions reported by the Oracle feed — generally, all versions. |
|
PyPI |
- |
|
Red Hat Enterprise Linux |
|
|
Rocky Linux |
The same versions reported by the Rocky Linux feed — generally, all versions. |
|
SUSE |
|