Amazon ECR Image scanning
Amazon ECR image scanning uses the Common Vulnerabilities and Exposures (CVEs) database from the open source Clair project to detect software vulnerabilities in container images and provide a list of scan findings, which can be easily integrated into Wazuh thanks to the Amazon CloudWatch Logs integration.
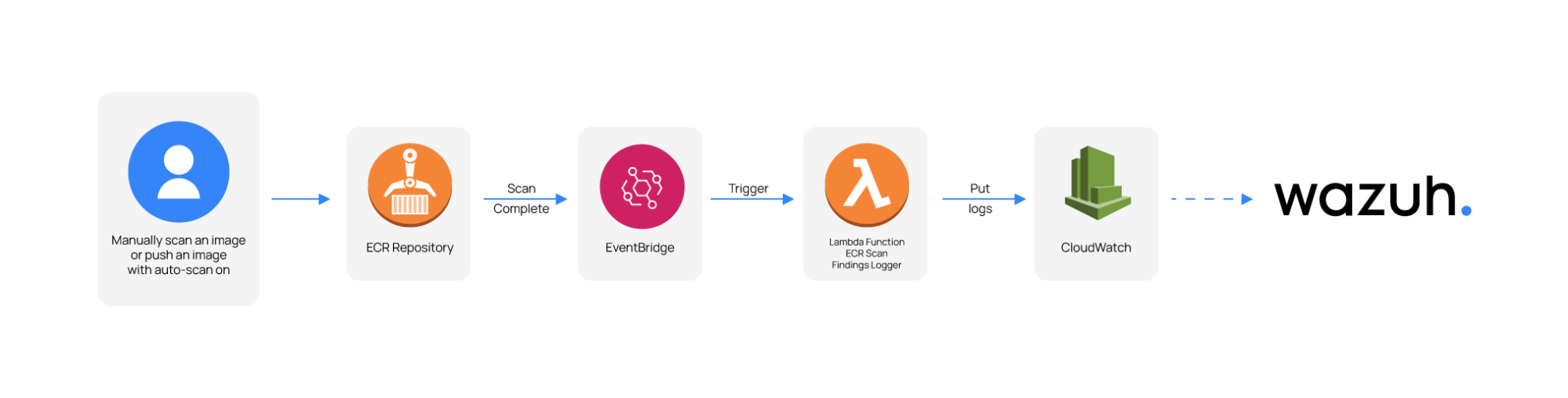
Amazon ECR sends an event to Amazon EventBridge when an image scan is completed. The event itself is only a summary and does not contain the details of the scan findings. However, it is possible to configure a Lambda function to request the scan findings details and store them in CloudWatch Logs. Here is a quick summary of what the workflow looks like:
An image scan is triggered.
Once the scan is completed Amazon ECR sends an event to EventBridge.
The "Scan completed" event triggers a Lambda function.
The lambda function takes the data from the "Scan completed" event and requests the scan details.
The Lambda function creates a log group and a log stream in CloudWatch Logs to store the response received.
Wazuh pulls the logs from the CloudWatch log groups using the CloudWatch Logs integration.
AWS configuration
The following sections cover how to configure AWS to store the scan findings in CloudWatch Logs and how to ingest them into Wazuh.
Amazon ECR Image scan configuration
AWS provides a template that logs to CloudWatch the findings of Amazon ECR scans of images. The template uses an AWS Lambda function to accomplish this.
Uploading the template and creating a stack, uploading the images to Amazon ECR, scanning the images, and using the logger all require specific permissions. Because of this, you need to create a custom policy granting these permissions.
Take into account that the policies below follow the principle of least privilege to ensure that only the minimum permissions are provided to the AWS IAM user.
Policy configuration
Follow the creating an AWS policy guide to create a policy using the Amazon Web Services console.
You need the permissions listed below inside the sections for RoleCreator and PassRole to create and delete the stack based on the template.
Note
These permissions must be bound to the specific resources due to overly permissive actions.
{
"Sid": "RoleCreator",
"Effect": "Allow",
"Action": [
"iam:CreateRole",
"iam:PutRolePolicy",
"iam:AttachRolePolicy",
"iam:DeleteRolePolicy",
"iam:DeleteRole",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:PassRole"
],
"Resource": "arn:aws:iam::<ACCOUNT_ID>:role/*"
},
{
"Sid": "PassRole",
"Effect": "Allow",
"Action": "iam:PassRole",
"Resource": "arn:aws:iam::<ACCOUNT_ID>:role/*-LambdaExecutionRole*"
}
CloudFormation stack permissions
A CloudFormation stack is a collection of AWS resources that can be managed as a single unit, including creation, update, or deletion. You need the following permissions to create and delete any template-based CloudFormation stack.
{
"Sid": "CloudFormationStackCreation",
"Effect": "Allow",
"Action": [
"cloudformation:CreateStack",
"cloudformation:ValidateTemplate",
"cloudformation:CreateUploadBucket",
"cloudformation:GetTemplateSummary",
"cloudformation:DescribeStackEvents",
"cloudformation:DescribeStackResources",
"cloudformation:ListStacks",
"cloudformation:DeleteStack",
"s3:PutObject",
"s3:ListBucket",
"s3:GetObject",
"s3:CreateBucket"
],
"Resource": "*"
}
ECR registry and repository permissions
This Amazon ECR permission allows calls to the API through an IAM policy.
Note
Before authenticating to a registry and pushing or pulling any images from any Amazon ECR repository, you need ecr:GetAuthorizationToken.
{
"Sid": "ECRUtilities",
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken",
"ecr:DescribeRepositories"
],
"Resource": "*"
}
Image pushing and scanning permissions
You need the following Amazon ECR permissions to push images. They are scoped down to a specific repository. The steps to push Docker images are described in the Amazon ECR - pushing a docker image documentation.
{
"Sid": "ScanPushImage",
"Effect": "Allow",
"Action": [
"ecr:CompleteLayerUpload",
"ecr:UploadLayerPart",
"ecr:InitiateLayerUpload",
"ecr:BatchCheckLayerAvailability",
"ecr:PutImage",
"ecr:ListImages",
"ecr:DescribeImages",
"ecr:DescribeImageScanFindings",
"ecr:StartImageScan"
],
"Resource": "arn:aws:ecr:<REGION>:<ACCOUNT_ID>:repository/<REPOSITORY_NAME>"
}
Amazon Lambda and Amazon EventBridge permissions
You need the following permissions to create and delete the resources handled by the Scan Findings Logger template.
{
"Sid": "TemplateRequired0",
"Effect": "Allow",
"Action": [
"lambda:RemovePermission",
"lambda:DeleteFunction",
"lambda:GetFunction",
"lambda:CreateFunction",
"lambda:AddPermission"
],
"Resource": "arn:aws:lambda:<REGION>:<ACCOUNT_ID>:*"
},
{
"Sid": "TemplateRequired1",
"Effect": "Allow",
"Action": [
"events:RemoveTargets",
"events:DeleteRule",
"events:PutRule",
"events:DescribeRule",
"events:PutTargets"
],
"Resource": "arn:aws:events:<REGION>:<ACCOUNT_ID>:*"
}
How to create the CloudFormation Stack
Download the ECR Image Scan findings logger template from the official aws-samples GitHub repository.
Access CloudFormation and click on Create stack.
Create a new stack using the template from step 1.
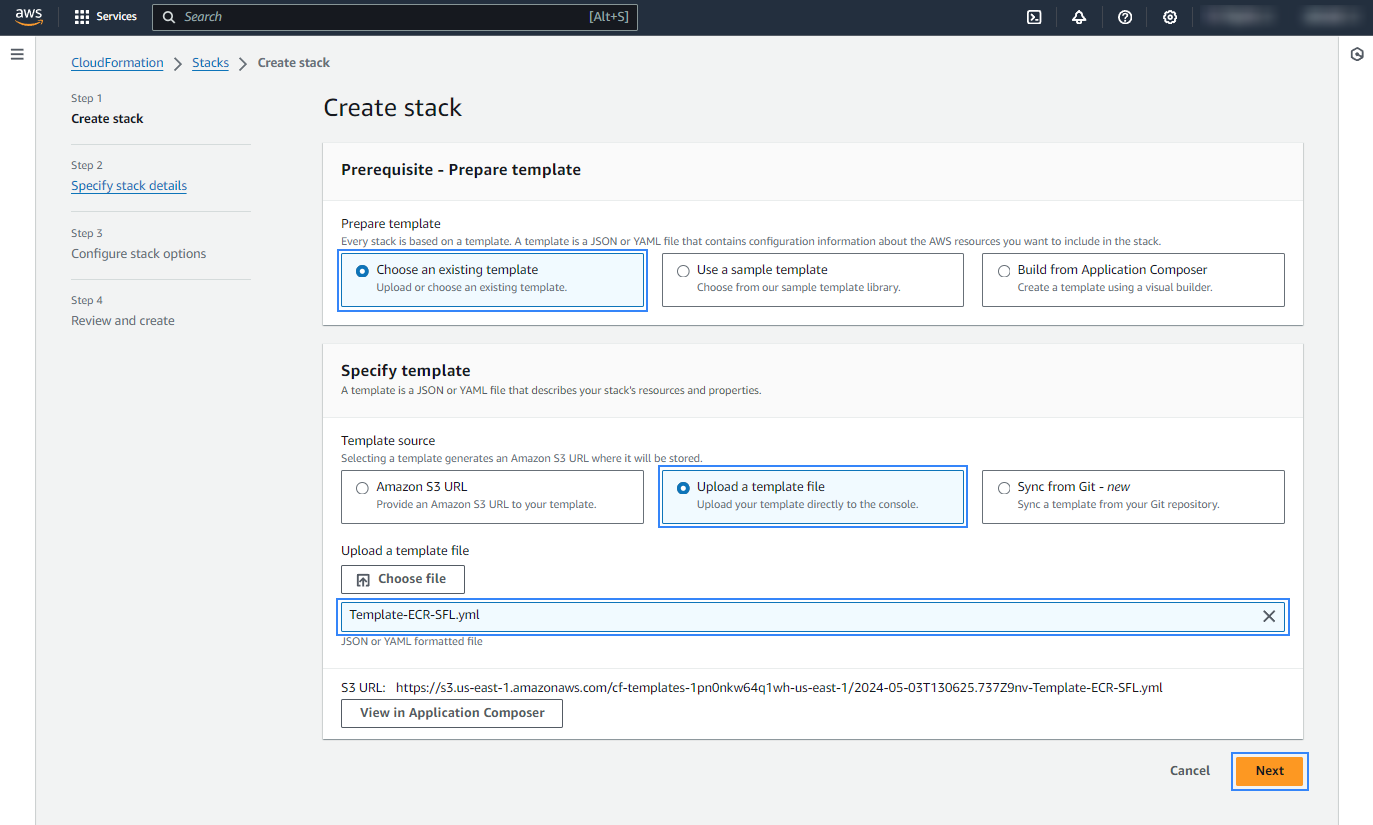
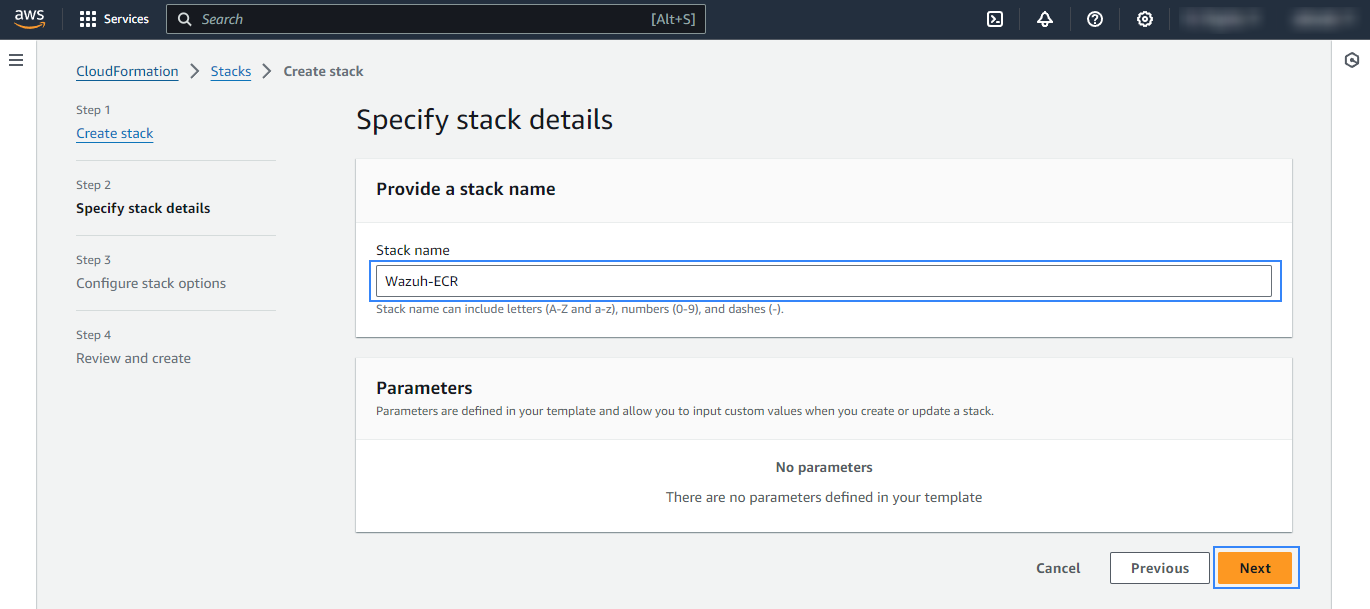
Choose a name for the stack and finish the creation process. No additional configuration is required.
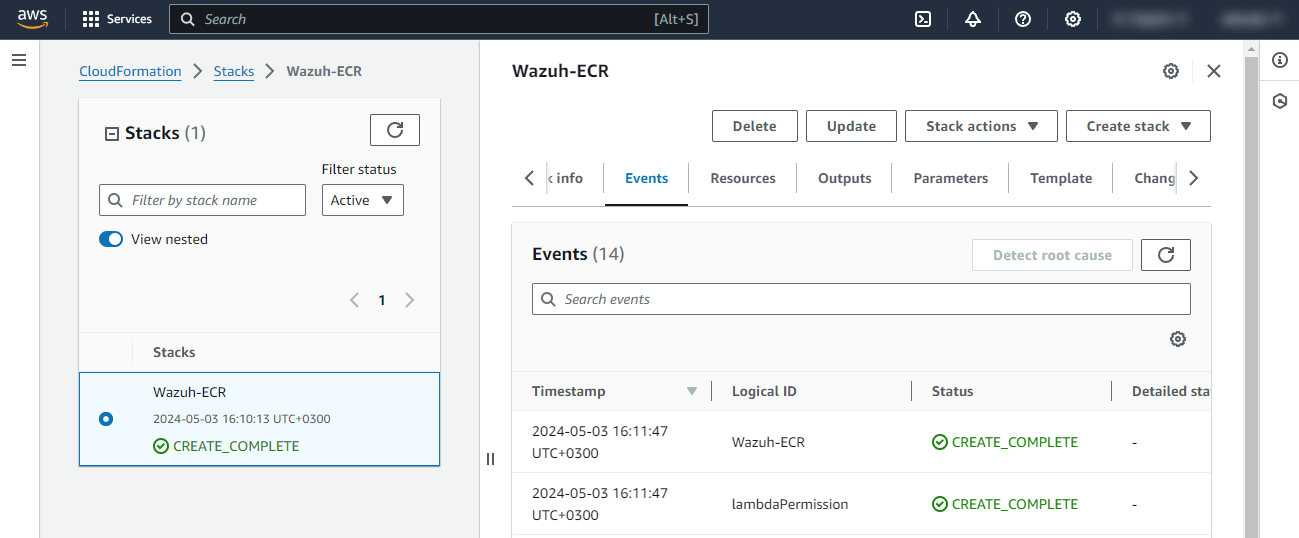
Wait until CREATE_COMPLETE status is reached. The stack containing the AWS Lambda is now ready to be used.
Once the stack configuration is completed, the Lambda can be tested by manually triggering an image scan of a container in Amazon ECR private registry. The scan results in the creation of a CloudWatch log group called /aws/ecr/image-scan-findings/<NAME_OF_ECR_REPOSITORY> containing the scan results. For every new scan, the corresponding log streams are created inside the log group.
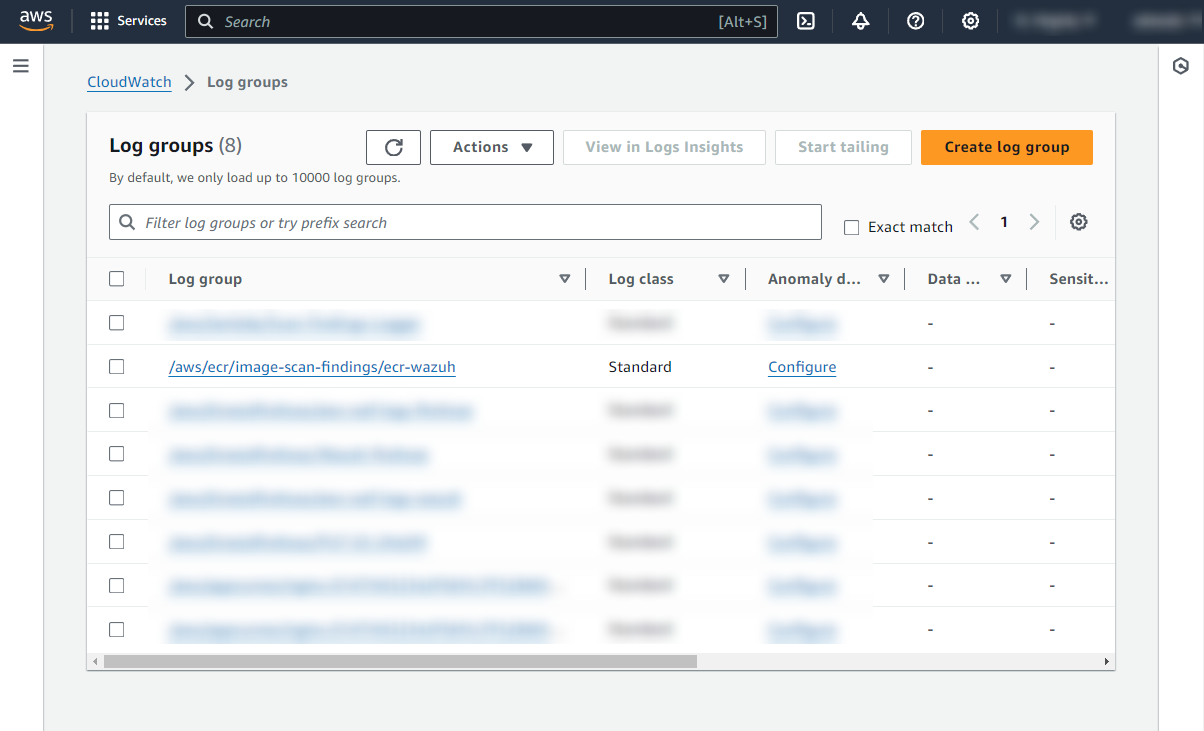
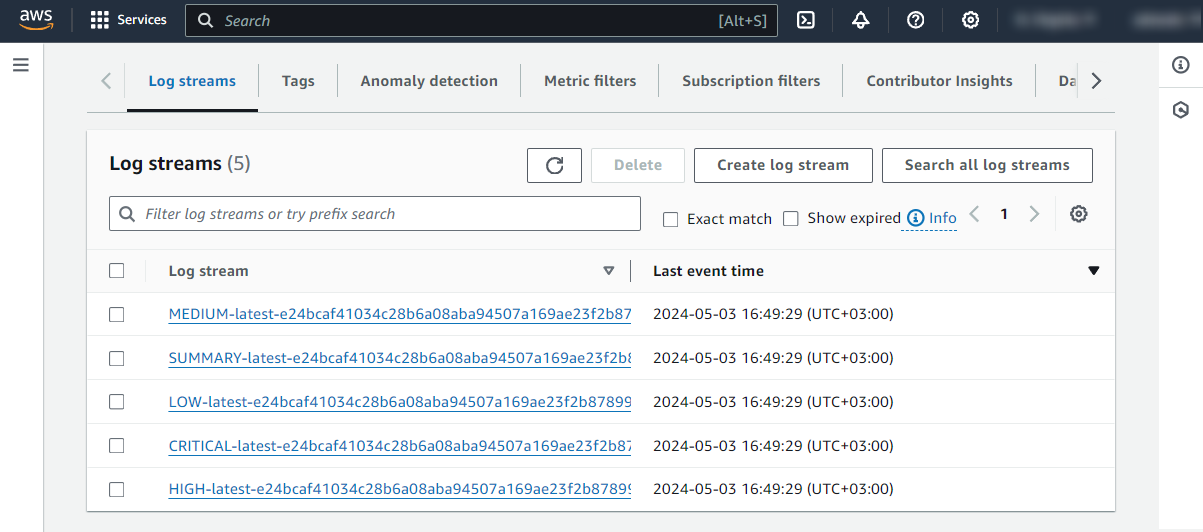
Configure Wazuh to process Amazon ECR image scanning logs
Access the Wazuh configuration in Server management > Settings using the Wazuh dashboard or by manually editing the
/var/ossec/etc/ossec.conffile in the Wazuh server or agent.
Add the following Wazuh module for AWS configuration block to enable the integration with Amazon ECR Image scanning. Replace
<NAME_OF_ECR_REPOSITORY>with the name of the Amazon ECR repository:<wodle name="aws-s3"> <disabled>no</disabled> <interval>5m</interval> <run_on_start>yes</run_on_start> <service type="cloudwatchlogs"> <aws_profile>default</aws_profile> <aws_log_groups>/aws/ecr/<NAME_OF_ECR_REPOSITORY></aws_log_groups> </service> </wodle>
Note
Check the AWS CloudWatch Logs integration to learn more about how the CloudWatch Logs integration works.
Save the changes and restart Wazuh to apply the changes. The service can be manually restarted using the following command outside the Wazuh dashboard:
Wazuh manager:
# systemctl restart wazuh-manager
Wazuh agent:
# systemctl restart wazuh-agent
Use case
Amazon ECR provides an image scanning feature that uses the Common Vulnerabilities and Exposure (CVEs) database from the open source Clair project to detect vulnerabilities in container images. Wazuh polls and detects these vulnerabilities from AWS CloudWatch.
Detecting vulnerabilities in container images
Check the Detecting vulnerabilities in container images using Amazon ECR blog to learn how to detect vulnerabilities in container images using Wazuh and Amazon ECR integration.