Detecting malware persistence technique
Adversaries might achieve persistence if they manage to add a malicious script or program to the startup folder of a Windows endpoint. The program in this folder executes when a user logs in to the endpoint.
By monitoring the Windows startup folder with the Wazuh FIM module, you can detect any suspicious or unknown programs that users might have added. This allows you to take appropriate action to remove them before they cause harm to your endpoint.
Use case description
Endpoint |
Description |
|---|---|
Windows 11 |
The FIM module monitors the startup folder on this endpoint. |
Configuration
Wazuh monitors the startup folder automatically without requiring any user action. By default, the Wazuh configuration file at C:\Program Files (x86)\ossec-agent\ossec.conf uses the following setting to monitor the startup folder:
<syscheck> <directories realtime="yes">%PROGRAMDATA%\Microsoft\Windows\Start Menu\Programs\Startup</directories> </syscheck>
Test the configuration
Use PowerShell to download an EICAR test file to the
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startupdirectory:cd "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup" Invoke-WebRequest -Uri https://secure.eicar.org/eicar.com.txt -OutFile eicar.txt
Delete the file from the Windows endpoint:
Remove-Item eicar.txt
Visualize the alert
Navigate to File Integrity Monitoring on the Wazuh dashboard to view the alert generated when the FIM module detects changes in the Windows startup folder.
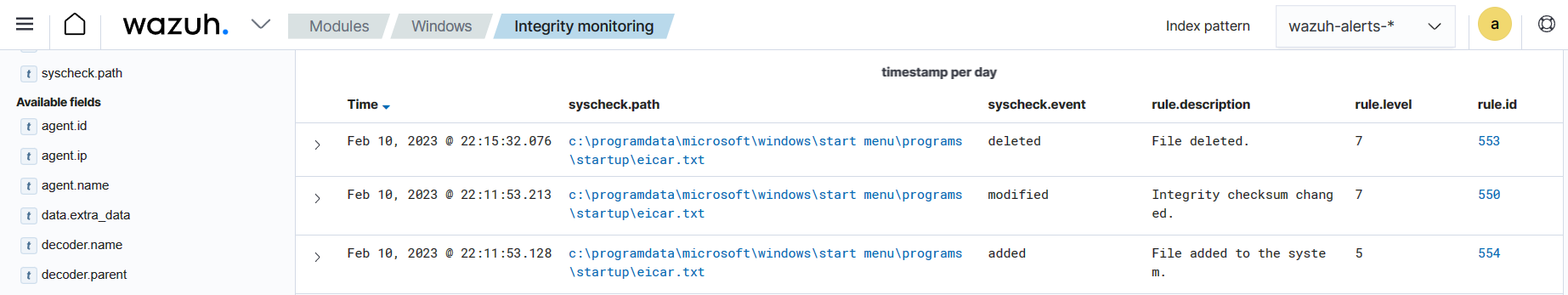
Additionally, you can integrate the Wazuh FIM module with VirusTotal to automatically remove this type of threat. You can find more information in our Proof of Concept guide.