Vulnerability detection
Wazuh detects vulnerabilities in the applications installed on monitored endpoints using the Vulnerability Detection module. It performs a software audit by querying our Cyber Threat Intelligence (CTI) API for vulnerability content documents. We aggregate vulnerability information into the CTI repository from external vulnerability sources indexed by Canonical, Debian, Red Hat, Arch Linux, Amazon Linux Advisories Security (ALAS), Microsoft, CISA, and the National Vulnerability Database (NVD). We also maintain the integrity of our vulnerability data and the vulnerabilities repository updated, ensuring the solution checks for the latest CVEs. The Vulnerability detection module correlates this information with data from the endpoint application inventory.
The Vulnerability Detection module helps to implement the following HIPAA section:
Security Management Process §164.308(a)(1) - Risk Analysis: “Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity or business associate.”
This section of the HIPAA standard requires identifying risks and vulnerabilities affecting systems containing healthcare information.
The Wazuh Vulnerability Detection module assists in meeting aspects of this HIPAA section. The Vulnerability Detection module checks for vulnerable applications/packages and missing OS updates in an endpoint. Refer to the vulnerability detection section of our documentation for more details on configuring vulnerability detection.
Use case: Detect vulnerabilities
In this use case, you configure Wazuh to detect vulnerabilities on a Debian endpoint with the following steps:
Edit the Wazuh server configuration file
/var/ossec/etc/ossec.conf. Make sure the module is enabled.<vulnerability-detection> <enabled>yes</enabled> <index-status>yes</index-status> <feed-update-interval>60m</feed-update-interval> </vulnerability-detection> <indexer> <enabled>yes</enabled> <hosts> <host>https://0.0.0.0:9200</host> </hosts> <ssl> <certificate_authorities> <ca>/etc/filebeat/certs/root-ca.pem</ca> </certificate_authorities> <certificate>/etc/filebeat/certs/filebeat.pem</certificate> <key>/etc/filebeat/certs/filebeat-key.pem</key> </ssl> </indexer>
If you made changes, restart the Wazuh manager to apply them.
# systemctl restart wazuh-manager
# service wazuh-manager restart
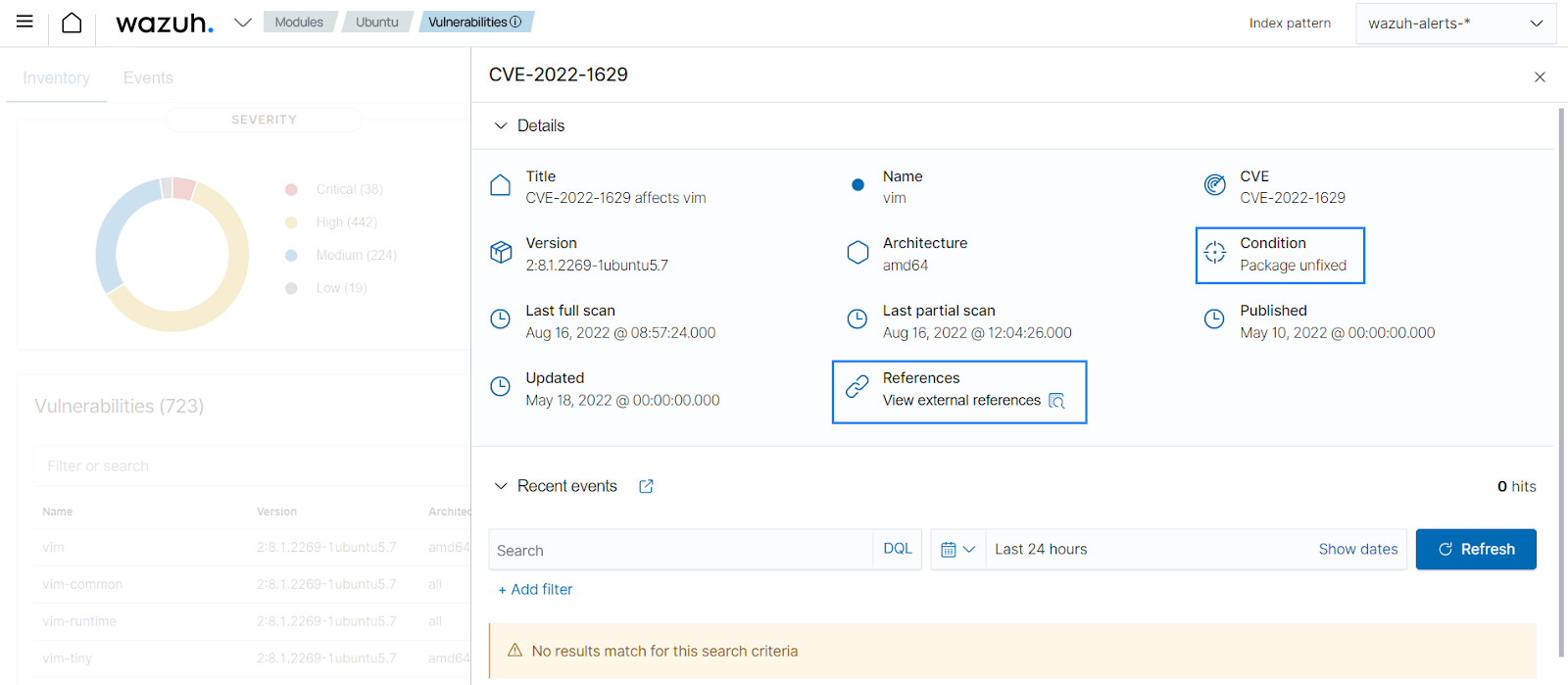
You can view the results on the Wazuh dashboard, which includes information about vulnerable packages on the monitored endpoint. In this case, the vim software installed on the endpoint has vulnerabilities.
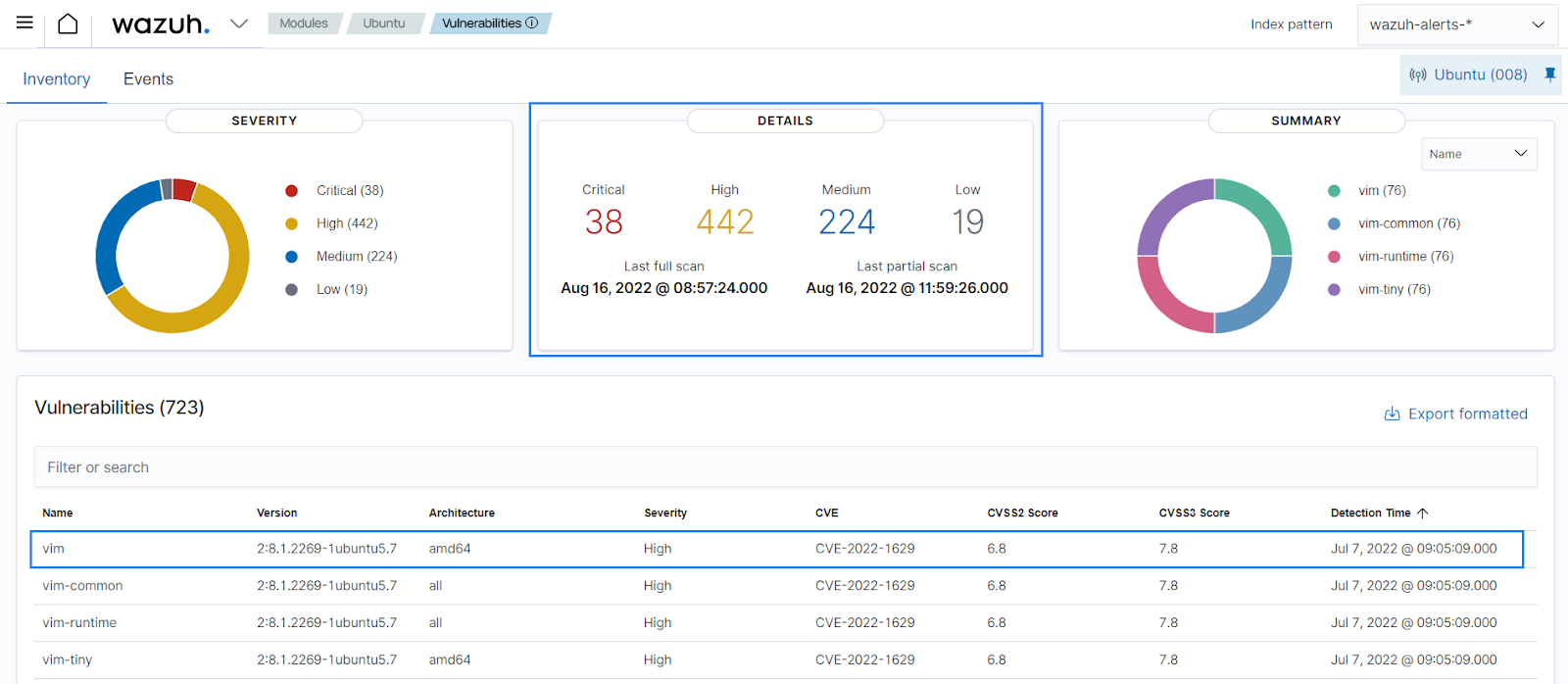
When you select any of the vulnerabilities, the dashboard shows an overview of the issues detected.