Processing integrity - PI1.4
The trust service criteria for additional criteria for processing integrity PI1.4 is a set of guidelines that outline the requirements for ensuring the completeness and integrity of the processed data of an entity. It states: "The entity implements policies and procedures to make available or deliver output completely, accurately, and timely in accordance with specifications to meet the entity’s objectives.". The following actions are performed to achieve this:
Protect output: Output is protected when stored or delivered, or both, to prevent theft, destruction, corruption, or deterioration that would prevent output from meeting specifications.
Distribute output only to intended parties: Output is distributed or made available only to intended parties.
Distribute output completely and accurately: Procedures are in place to provide for the completeness, accuracy, and timeliness of distributed output.
Create and maintain records of system output activities: Records of system output activities are created and maintained completely and accurately in a timely manner.
The use case below demonstrates how Wazuh assists in meeting this requirement.
Use case: Detecting file changes using the Wazuh File Integrity Monitoring module
This use case shows how Wazuh helps meet the processing integrity PI1.4 requirement by monitoring and reporting file changes using the FIM module. In this scenario, we show how you can configure the Wazuh agent on a Ubuntu 22.04 endpoint to detect changes in the critical_folder directory.
Ubuntu endpoint
Switch to the
rootuser:$ sudo su
Create the directory
critical_folderin the/rootdirectory:# mkdir /root/critical_folder
Create the file
special_data.txtin the/root/critical_folderdirectory and add some content:# touch /root/critical_folder/special_data.txt # echo "The content in this file must maintain integrity" >> /root/critical_folder/special_data.txt
Add the highlighted configuration to the
<syscheck>block of the Wazuh agent configuration file/var/ossec/etc/ossec.conf:<syscheck> <directories realtime="yes" check_all="yes" report_changes="yes">/root/critical_folder</directories> </syscheck>
Restart the Wazuh agent to apply the changes:
# systemctl restart wazuh-agent
Modify the file by changing the content of
special_data.txtfromThe content in this file must maintain integritytoA change has occurred:# echo "A change has occurred" > /root/critical_folder/special_data.txt # cat /root/critical_folder/special_data.txt
A change has occurred
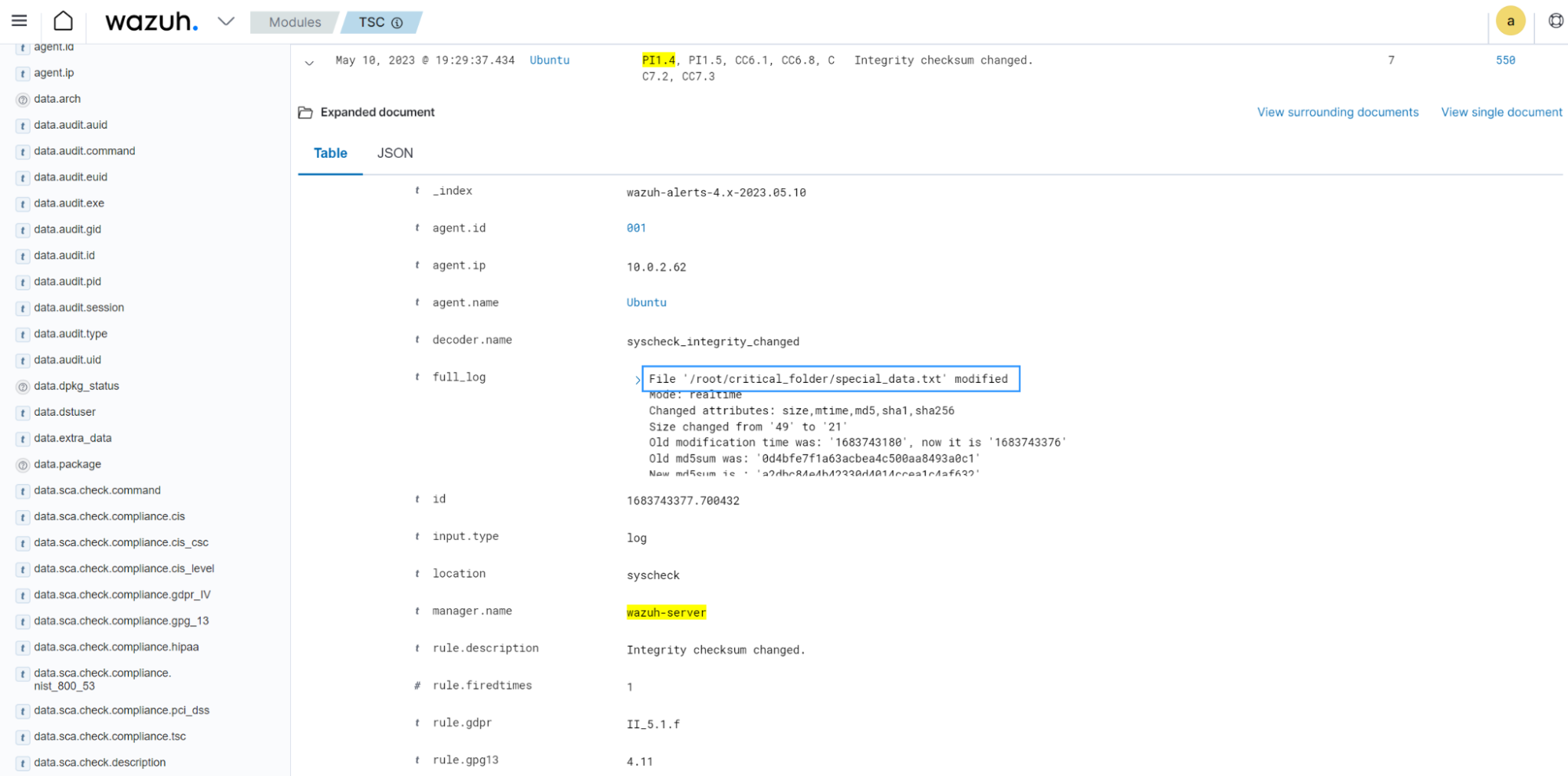
Select TSC from the Wazuh dashboard to view the alert with rule ID
550.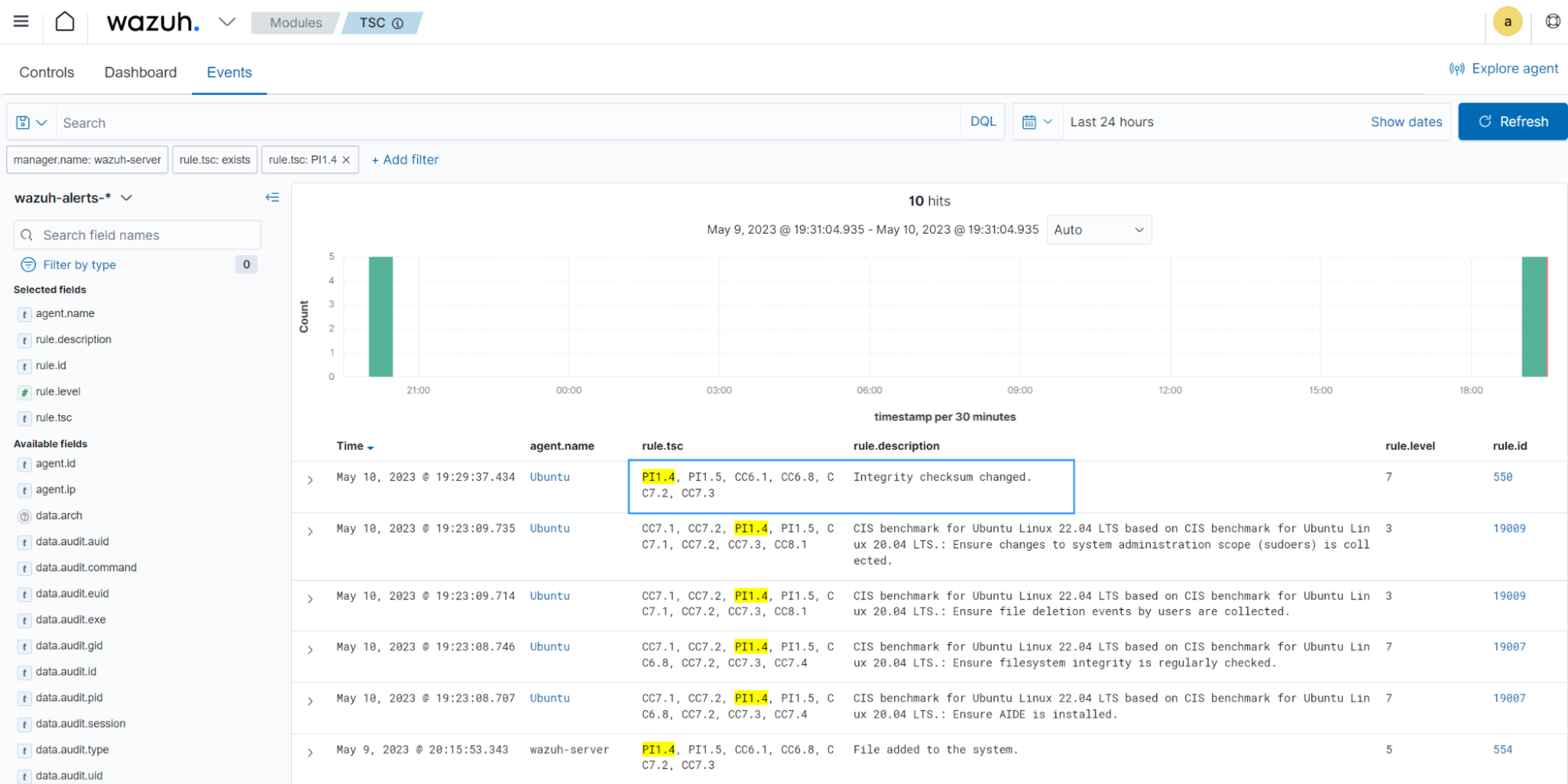
The alert is tagged with
PI1.4and other compliance tags with requirements that intersect with this use case.