Vulnerability detection
Wazuh uses the Vulnerability Detection module to identify vulnerabilities in applications and operating systems running on monitored endpoints.
This use case shows how Wazuh detects unpatched Common Vulnerabilities and Exposures (CVEs) in the monitored endpoint.
For more information on this capability, check the Vulnerability detection section of the Wazuh documentation.
Infrastructure
Endpoint |
Description |
|---|---|
Red Hat Enterprise Linux 7 |
The Wazuh Vulnerability Detection module scans this Linux endpoint for vulnerabilities in the operating system and installed applications. |
Note
Vulnerabilities tagged with the description unimportant will not appear on the Wazuh dashboard. Visit the Wazuh CTI page for more information. The Compatibility matrix shows the operating systems officially supported by the Vulnerability Detection module.
Configuration
The Wazuh Vulnerability Detection module is enabled by default and it generates alerts when new vulnerabilities are detected or when existing vulnerabilities are resolved through package updates, removal, or system upgrades.
Wazuh Server
Perform the following steps on the Wazuh server to confirm that the Wazuh Vulnerability Detection module is enabled and properly configured.
Open the Wazuh configuration
/var/ossec/etc/ossec.confand check the following settings.Vulnerability detection is enabled:
<vulnerability-detection> <enabled>yes</enabled> <index-status>yes</index-status> <feed-update-interval>60m</feed-update-interval> </vulnerability-detection>
The Wazuh indexer connection is properly configured.
By default, the indexer settings have one host configured. It's set to
0.0.0.0as highlighted below.<indexer> <enabled>yes</enabled> <hosts> <host>https://0.0.0.0:9200</host> </hosts> <ssl> <certificate_authorities> <ca>/etc/filebeat/certs/root-ca.pem</ca> </certificate_authorities> <certificate>/etc/filebeat/certs/filebeat.pem</certificate> <key>/etc/filebeat/certs/filebeat-key.pem</key> </ssl> </indexer>
Replace
0.0.0.0with your Wazuh indexer node IP address or hostname. You can find this value in the Filebeat config file/etc/filebeat/filebeat.yml.Ensure the Filebeat certificate and key name match the certificate files in
/etc/filebeat/certs.
If you are running a Wazuh indexer cluster infrastructure, add a
<host>entry for each one of your nodes. For example, in a two-node configuration:<hosts> <host>https://10.0.0.1:9200</host> <host>https://10.0.0.2:9200</host> </hosts>
The Wazuh server prioritizes reporting to the first Wazuh indexer node in the list. It switches to the next node in case it is not available.
Restart the Wazuh manager if you made changes to the configuration:
$ sudo systemctl restart wazuh-manager
Test the configuration
Note
The time it takes to detect vulnerabilities depends on the <interval> value in the Syscollector module, configured in the /var/ossec/etc/ossec.conf file on the Wazuh agent. For this test, we reduce the Syscollector module interval time from 1h to 10m. Refer to System inventory capability configuration for more information.
Install Vim version
2:7.4.629-8which is known to be vulnerable, on the RHEL 7 endpoint. Wait approximately 10 minutes (or the duration set in your Syscollector<interval>) for a new scan to run and the vulnerability to be detected.Remove the Vim package to fix the vulnerability. Wait 10 minutes for the syscollector to run a new scan to confirm the vulnerability has been cleared.
Visualize the vulnerabilities
You can visualize the detected vulnerabilities on the Wazuh dashboard. To see a list of active vulnerabilities, perform the following on the Wazuh dashboard:
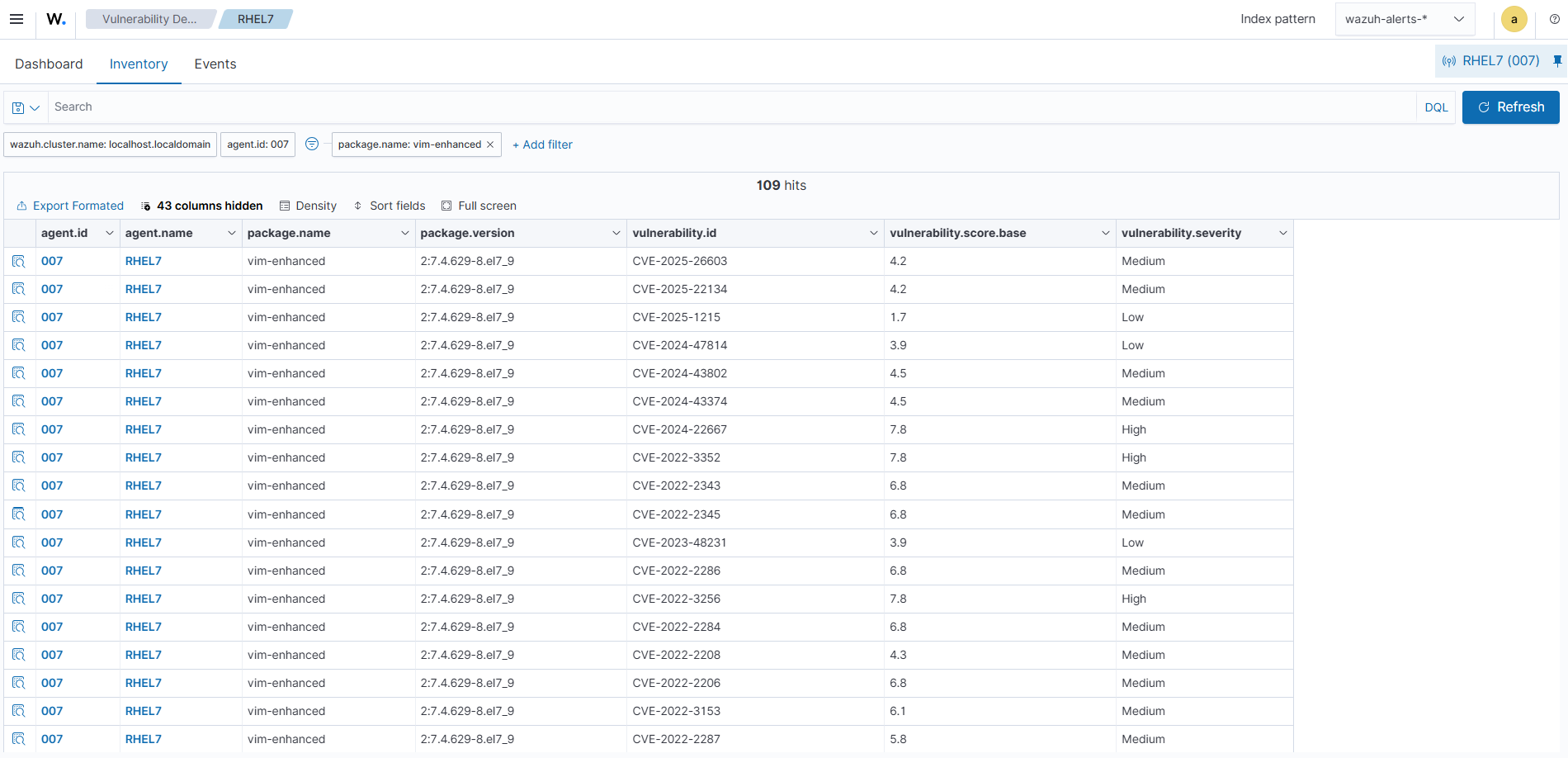
Go to Vulnerability Detection and select Inventory.
Click + Add filter. Then filter by
package.name.In the Operator field, select
is.Search and select
vimin the Values field.
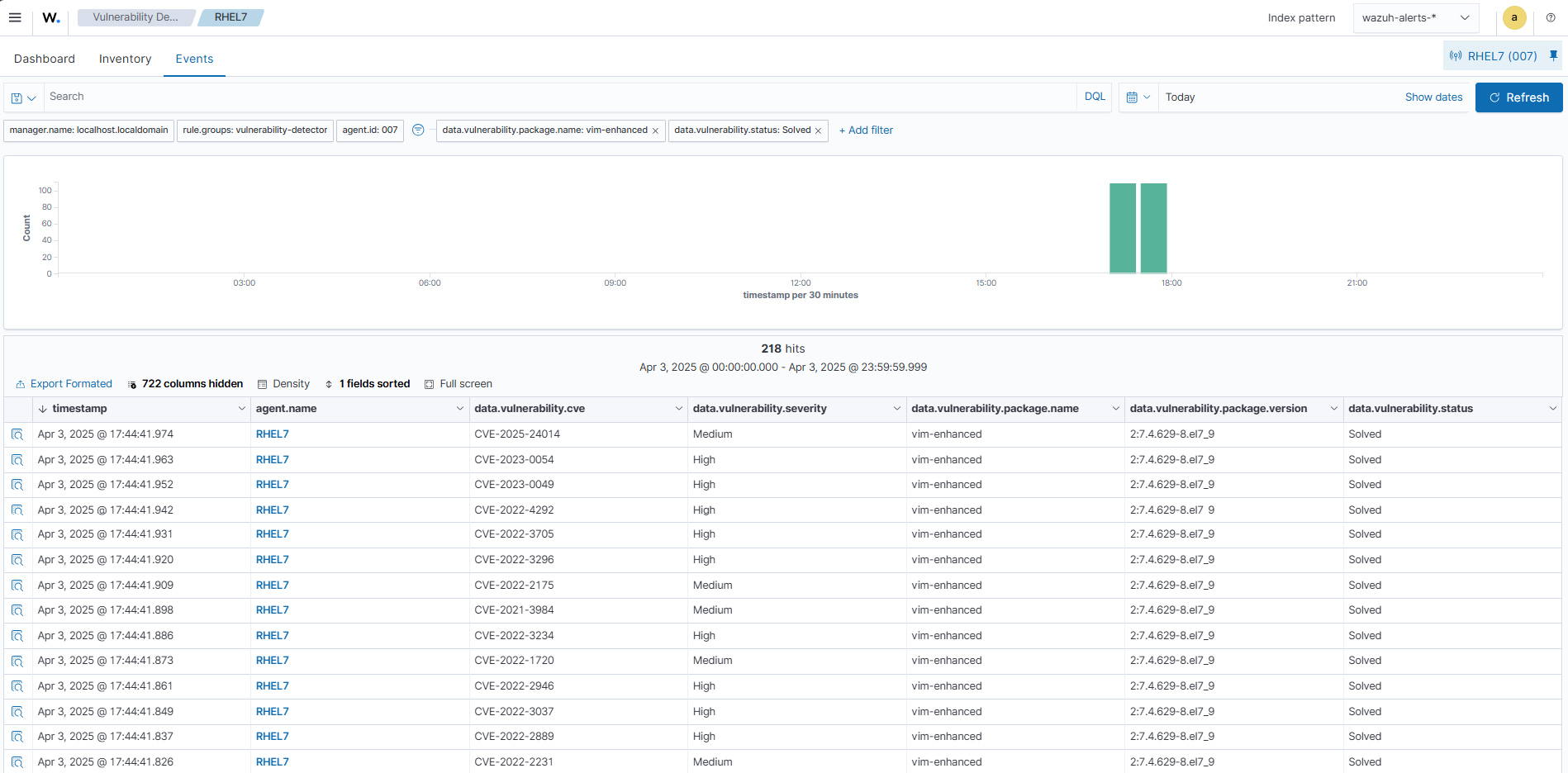
To see vulnerability alerts from the last system inventory scan, switch to the Events tab. Add filters in the search bar to query vulnerability alerts for Vim.
Note
Not all vulnerabilities added to or removed from the inventory generate alerts. This depends on the event source. See Alert generation for more details.
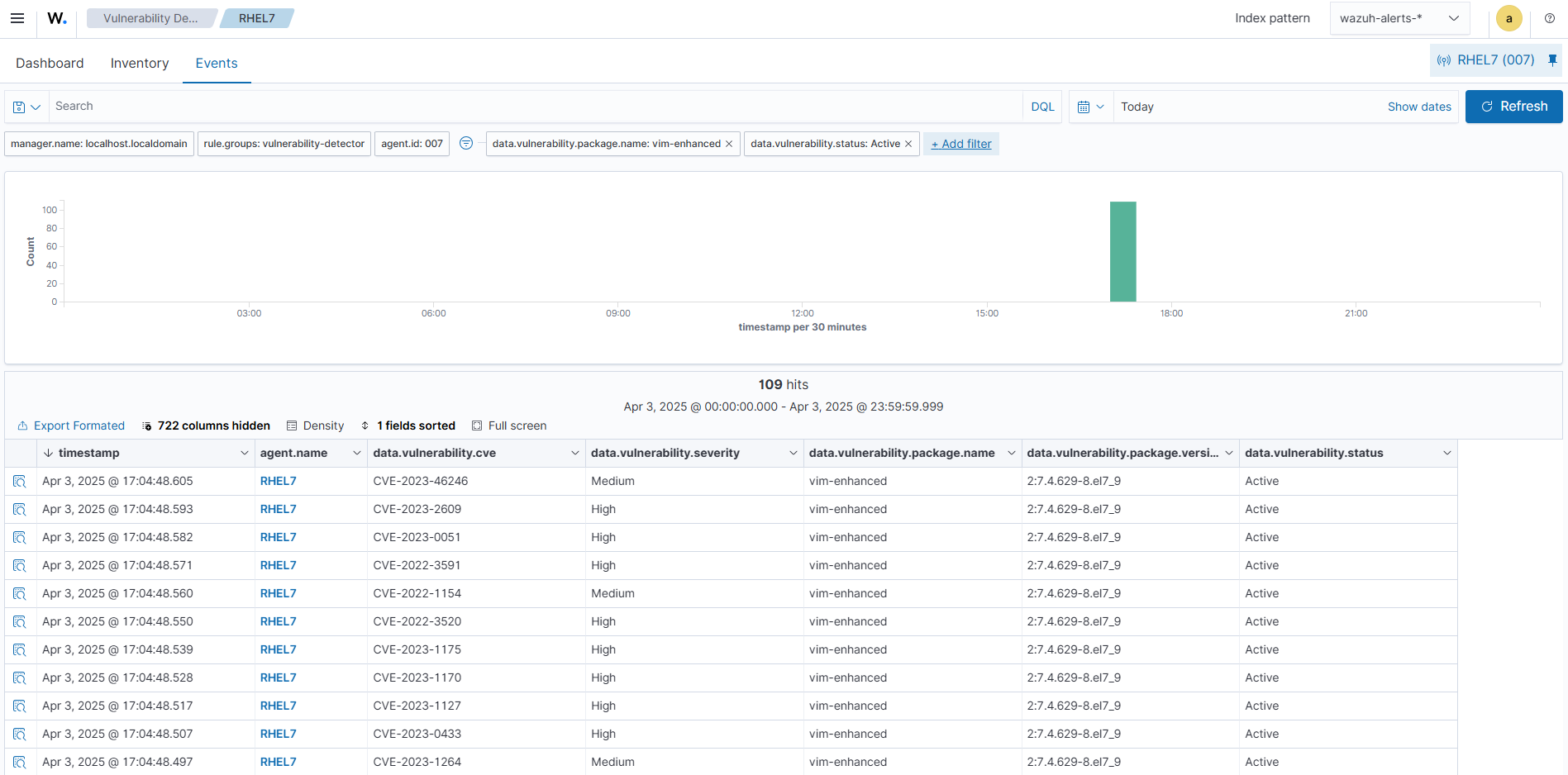
Upon installation of the vulnerable Vim package, the active vulnerability alerts can be seen on the Wazuh dashboard by changing the filter to data.vulnerability.package.name: vim AND data.vulnerability.status:Active
After removing the vulnerable package from the endpoint, to view the resolved vulnerability alerts, simply change the filter values to data.vulnerability.package.name: vim AND data.vulnerability.status:Solved