File integrity monitoring
File integrity monitoring compares the cryptographic checksum and other attributes of a known file against the checksum and attributes of that file after it has been modified.
First, the Wazuh agent scans the system periodically at a specified interval, then it sends the checksums of the monitored files and registry keys (for Windows systems) to the Wazuh server. The server stores the checksums and looks for modifications by comparing the newly received checksums against the historical checksum values for those files and/or registry keys. An alert is generated if the checksum (or another file attribute) changes. Wazuh also supports near real-time file integrity monitoring.
The file integrity monitoring module is used to meet some sub-requirements of PCI DSS requirement 11 which requires testing the security of systems and networks regularly. This requirement aims to ensure that system components, processes, and bespoke and custom software are tested frequently to ensure security controls continue to reflect a changing environment. Some of the changes in the environment may include the modification and deletion of critical files. This module helps to monitor these file changes and assist in achieving PCI DSS compliance.
Use cases
PCI DSS 11.5.2 requires the deployment of a change-detection mechanism (for example, file integrity monitoring tools) to alert personnel of unauthorized modification (including changes, additions, and deletions) of critical system files, configuration files, or content files; and to configure the software to perform critical file comparisons at least weekly.
In the following sections, we look at configuring Wazuh to do the following:
Detect changes in a file
Perform critical file comparisons at specified intervals
Detect file deletion
Detect changes in a file
For this use case, we configure Wazuh to detect when changes are made to a file in the directory /root/credit_cards and the details of the user that made the changes.
On the agent
Firstly we need to check if the Audit daemon is installed in our system.
In RedHat based systems, Auditd is commonly installed by default. If it's not installed, we need to install it using the following command:
# yum install audit
For Debian based systems, use the following:
# apt install auditd
Check the full file path for the file or directory to be monitored. In this case, the module monitors the directory
/root/credit_cardsfor changes:# ls -l /root/credit_cards/
total 4 -rw-r--r--. 1 root root 14 May 16 14:53 cardholder_data.txt
# cat /root/credit_cards/cardholder_data.txt
User1 = card4
Add the following configuration to the syscheck block of the agent configuration file (
/var/ossec/etc/ossec.conf). This enables real-time monitoring of the directory. It also ensures that Wazuh generates an alert when a file in the directory is modified. This alert has the details of the user who made the changes on the monitored files and the program name or process used to carry them out:<syscheck> <directories check_all="yes" whodata="yes">/root/credit_cards</directories> </syscheck>
Restart the Wazuh agent to apply the changes:
# systemctl restart wazuh-agent
# service wazuh-agent restart
Execute the following command to check if the Audit rule for monitoring the selected folder is applied:
auditctl -l | grep wazuh_fimCheck in the command output that the rule was added:
auditctl -w /root/credit_cards -p wa -k wazuh_fimEdit the file and add new content:
nano credit_cards/cardholder_data.txtYou can see an alert generated to show that a file in the monitored directory was modified.
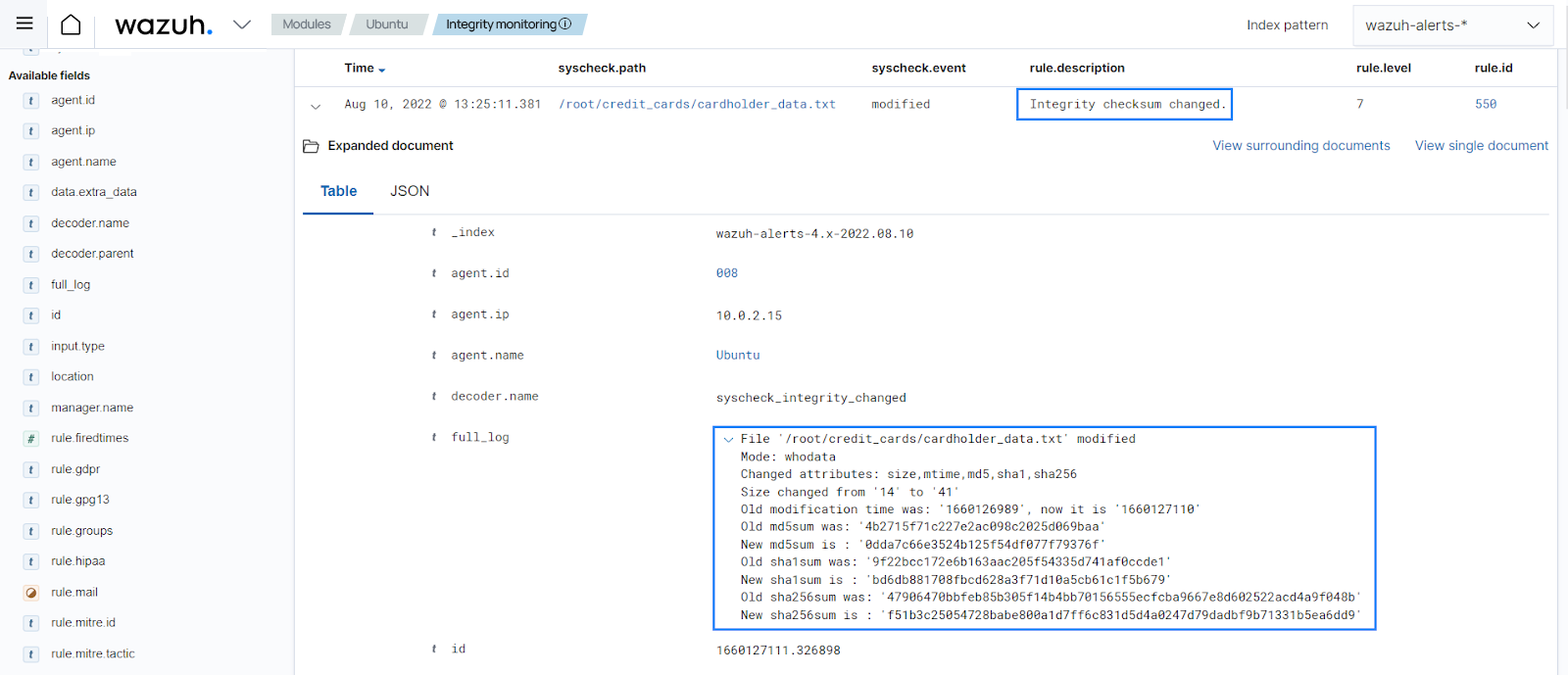
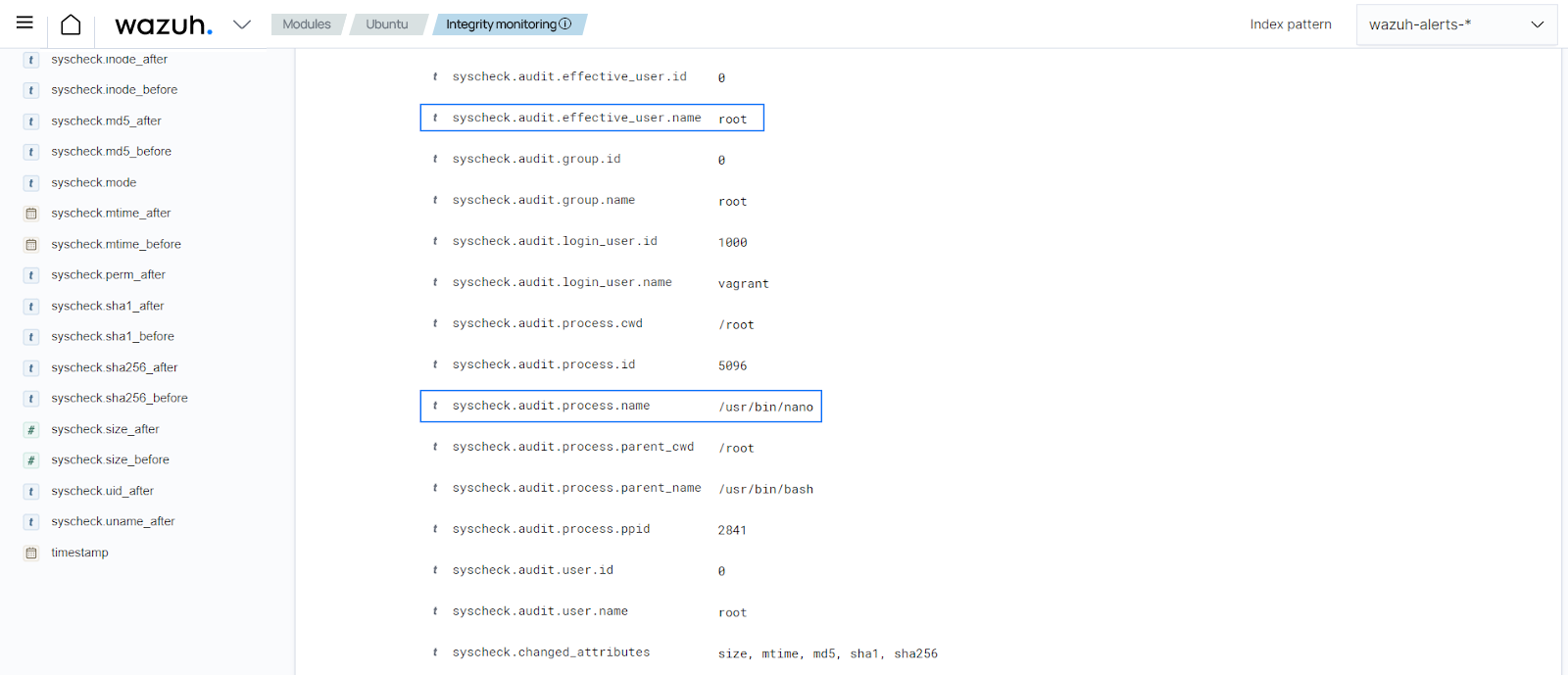
In the alert details, you can see the PCI DSS requirement met, the differences in the file checksum, the file modified, the modification time, the
whodatashowing the process and user that made the modification, and other details.
Perform critical file comparisons at specified intervals
In this use case, we configure Syscheck to detect when changes have been made to monitored files over specific time intervals and show the differences in the file between the last check and the present check. To illustrate this, in the steps below, we configure syscheck to perform a scan every 1 hour and generate an alert for every file change detected.
Note
Syscheck runs scans every 12 hours by default. The scan frequency set is for all monitored files/directories except directories with real-time monitoring enabled.
Depending on the number of files/directories configured for scans, and the frequency of syscheck scans, you may observe increased CPU and memory usage. Please use the frequency option carefully.
On the agent
Determine the full file path for the file to be monitored. In this case, we are monitoring the file
/root/credit_cards/cardholder_data.txtfor changes.Note
Showing the changes made in a file is limited to only text files at this time.
Update the frequency option of the
syscheckblock in the/var/ossec/etc/ossec.confagent configuration file. Set a scan interval in seconds. For example, every 3600 seconds:<frequency>3600</frequency>Add the following configuration to the
syscheckblock of the/var/ossec/etc/ossec.confagent configuration file. This enables monitoring of the file. It also ensures that Wazuh generates an alert with the differences when the file is modified.<syscheck> <directories check_all="yes" report_changes="yes" >/root/credit_cards/cardholder_data.txt</directories> </syscheck>
Note
If you prefer that the changes are monitored in real-time, you can use the configuration below to monitor the directory where the file is saved and disregard making the frequency modification.
<syscheck> <directories check_all="yes" report_changes="yes" realtime="yes" >/root/credit_cards</directories> </syscheck>
Restart the Wazuh agent to apply the changes.
# systemctl restart wazuh-agent
# service wazuh-agent restart
Proceed to modify the file. In this case, we removed some content. An alert is generated on the next Syscheck scan about the modified file.
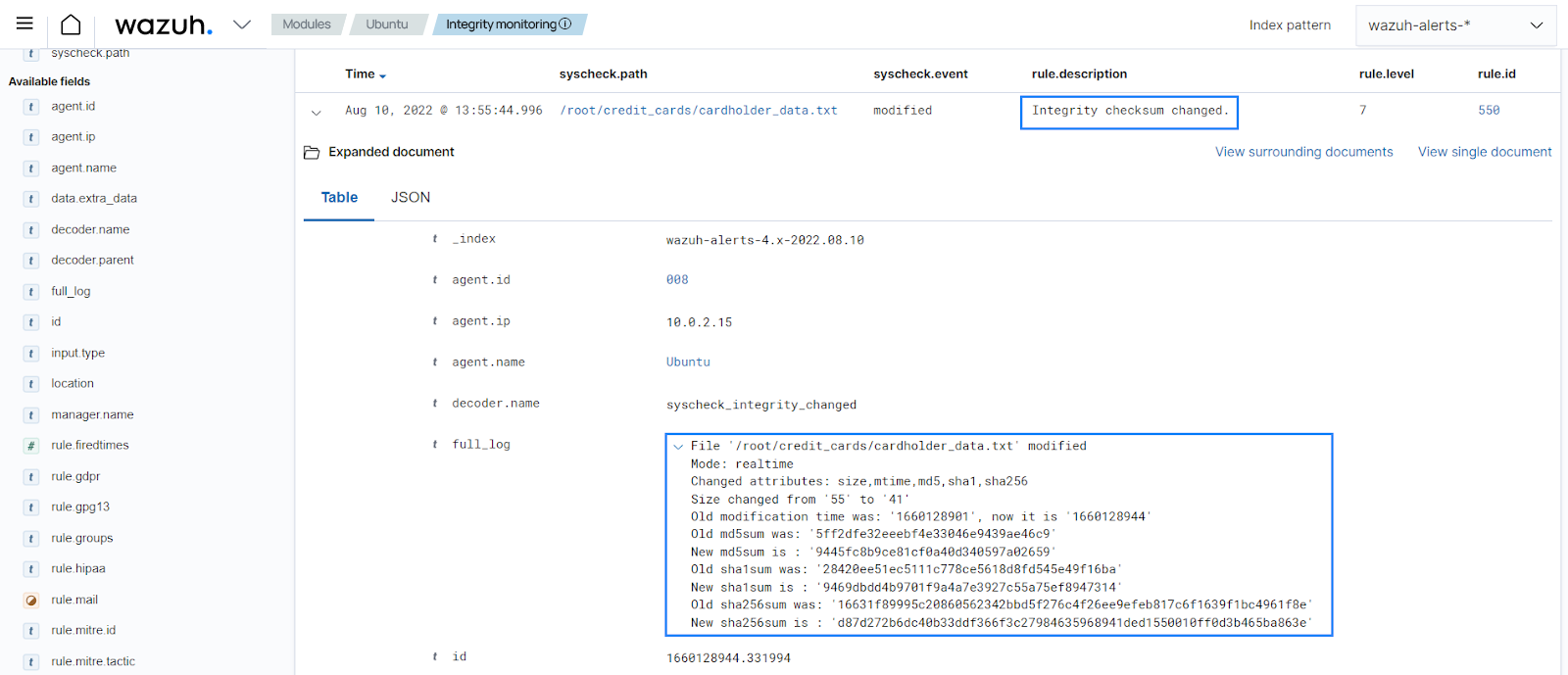
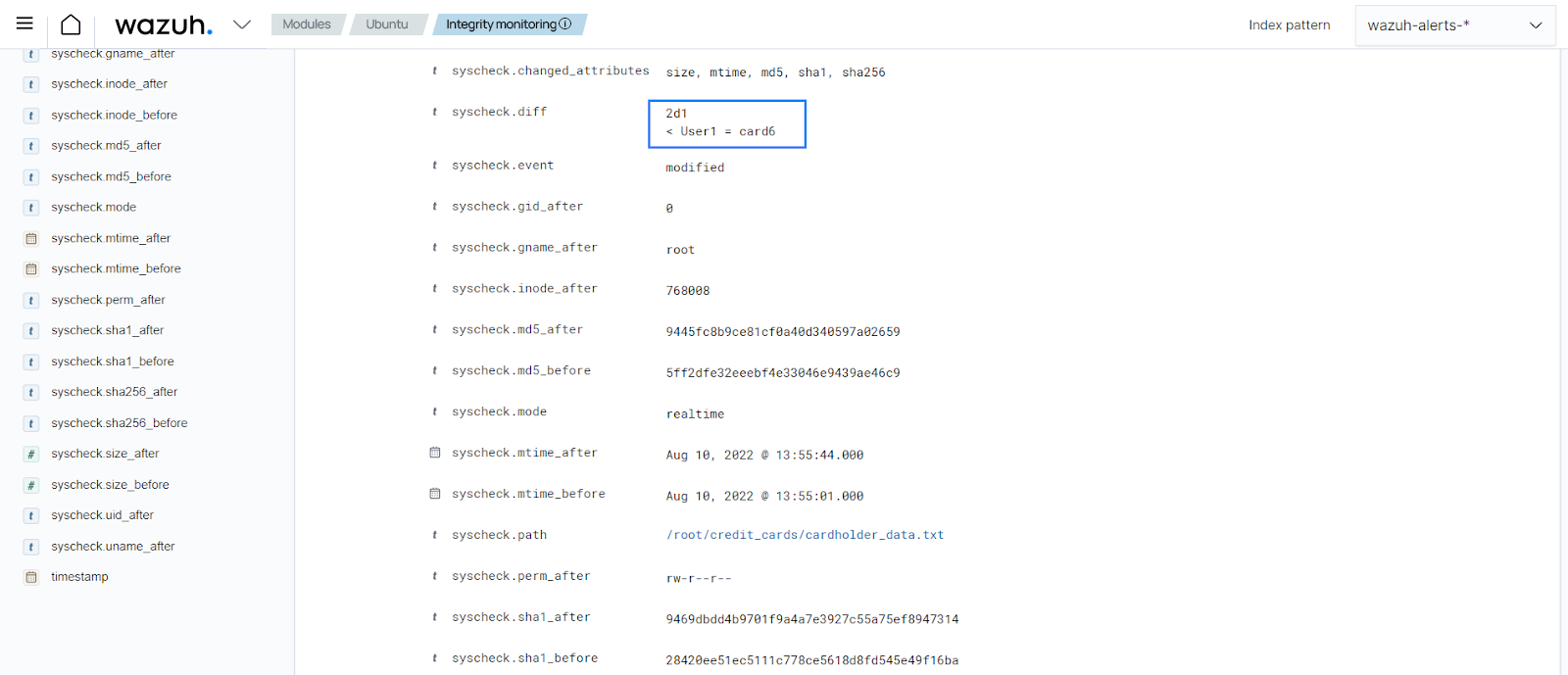
In the alert details, you can see the changes made in
syscheck.diff, the file modified, the PCI DSS requirement met, the differences in the file checksum, the modification time, and other details.
Detect file deletion
In this scenario, Syscheck detects when a file in a monitored directory is deleted. To illustrate this, in the steps below, Syscheck is configured to monitor the /root/credit_cards/ directory for changes.
On the agent
Determine the full file path for the file or directory to be monitored. In this case, we are monitoring the directory
/root/credit_cards.Add the following configuration to the syscheck block of the
/var/ossec/etc/ossec.confagent configuration file. This enables monitoring of the file. It also ensures that Wazuh generates an alert if the file is deleted.<syscheck> <directories check_all="yes" realtime="yes" >/root/credit_cards</directories> </syscheck>
Restart the Wazuh agent to apply the changes.
# systemctl restart wazuh-agent
# service wazuh-agent restart
Delete a file from the directory. For example,
cardholder_data.txt. You can see an alert generated for the file deleted.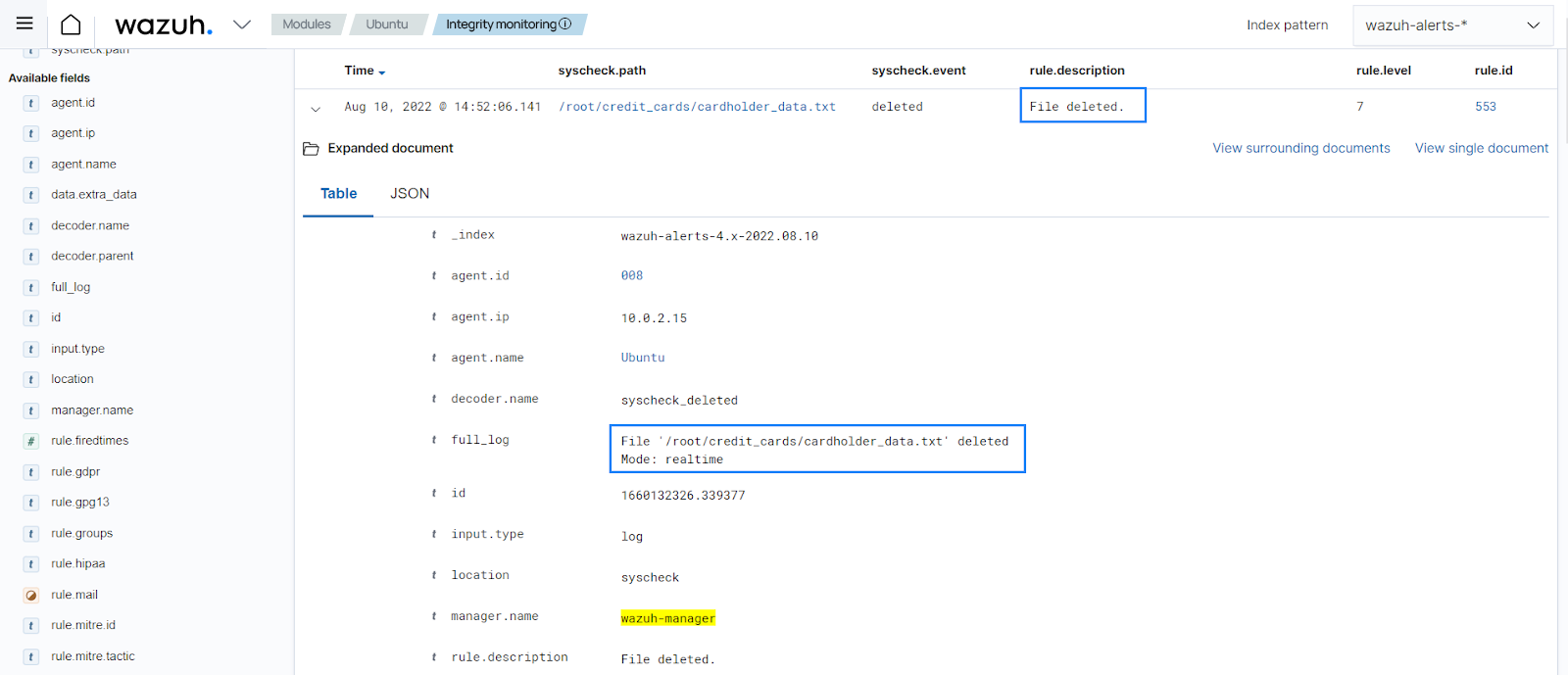
In the alert details, you can see the file deleted, the PCI DSS requirement met, the deletion time, and other details.
You can track these activities from the PCI DSS module dashboard. The dashboard shows all activities that trigger a PCI DSS requirement including FIM changes.