Amazon Macie
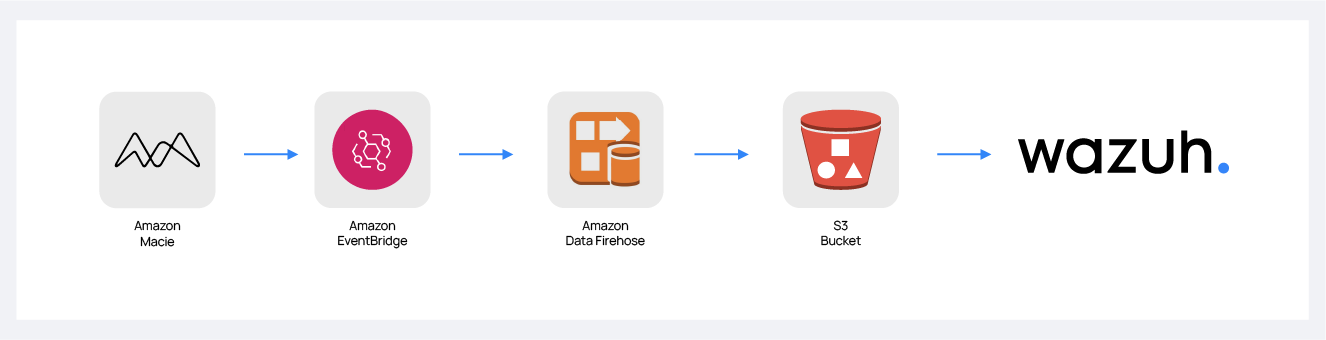
Amazon Macie is a security service that uses machine learning to automatically discover, classify, and protect sensitive data in AWS. Macie recognizes sensitive data such as personally identifiable information (PII) or intellectual property and provides you with dashboards and alerts that give visibility into how this data is being accessed or moved. The fully managed service continuously monitors data access activity for anomalies and generates detailed alerts when it detects the risk of unauthorized access or inadvertent data leaks.
AWS configuration
The following sections cover how to configure different services required to integrate AWS Macie service with Wazuh.
Amazon Data Firehose configuration
Create an Amazon Data Firehose delivery stream to store the Amazon Macie events into the desired S3 bucket so Wazuh can process them.
Create a new S3 bucket. (If you want to use an already created one, skip this step).
On your AWS console, Search for "amazon data firehose" in the search bar at the top of the page or go to Services > Analytics > Amazon Data Firehose.
Click Create Firehose stream.
Select Direct PUT and Amazon S3 as the desired Source and Destination, respectively.
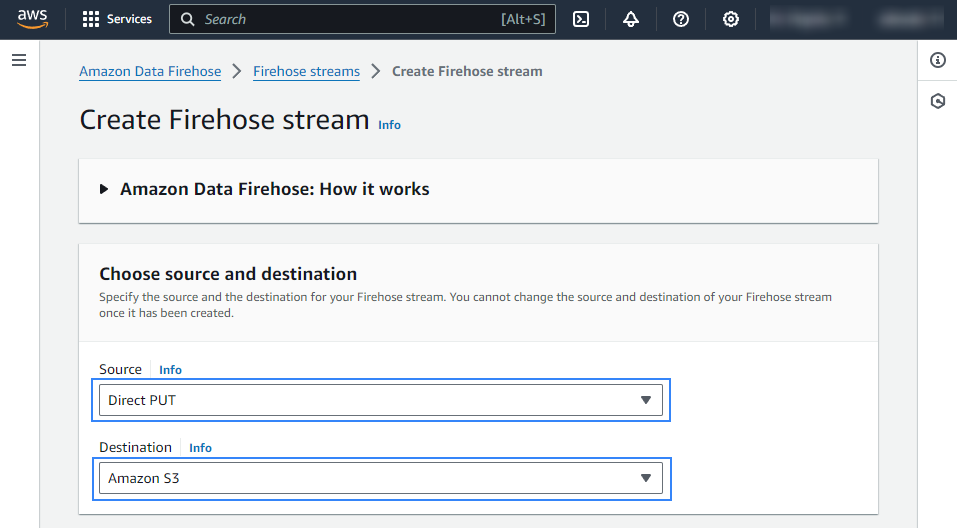
Choose an appropriate Firehose stream name.
Select the desired S3 bucket as the destination. It is possible to specify a custom prefix to alter the path where AWS stores the logs. AWS Firehose creates a file structure
YYYY/MM/DD/HH, if a prefix is used the created file structure would beprefix-name/YYYY/MM/DD/HH. If a prefix is used it must be specified under the Wazuh bucket configuration. In our case, the prefix ismacie/.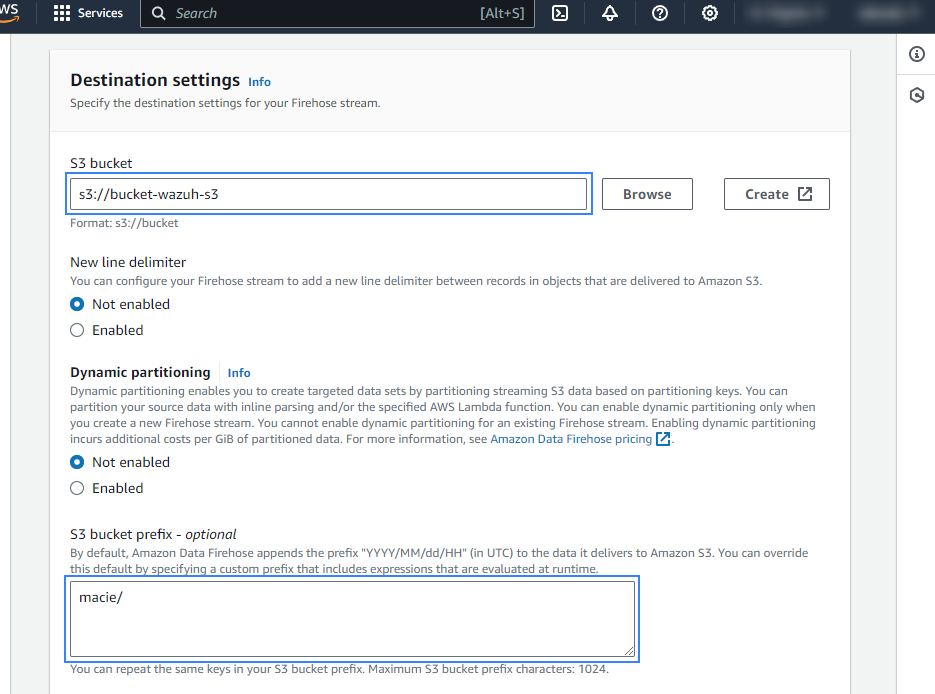
Create or choose an existing IAM role to be used by Amazon Data Firehose in the Advanced settings section.
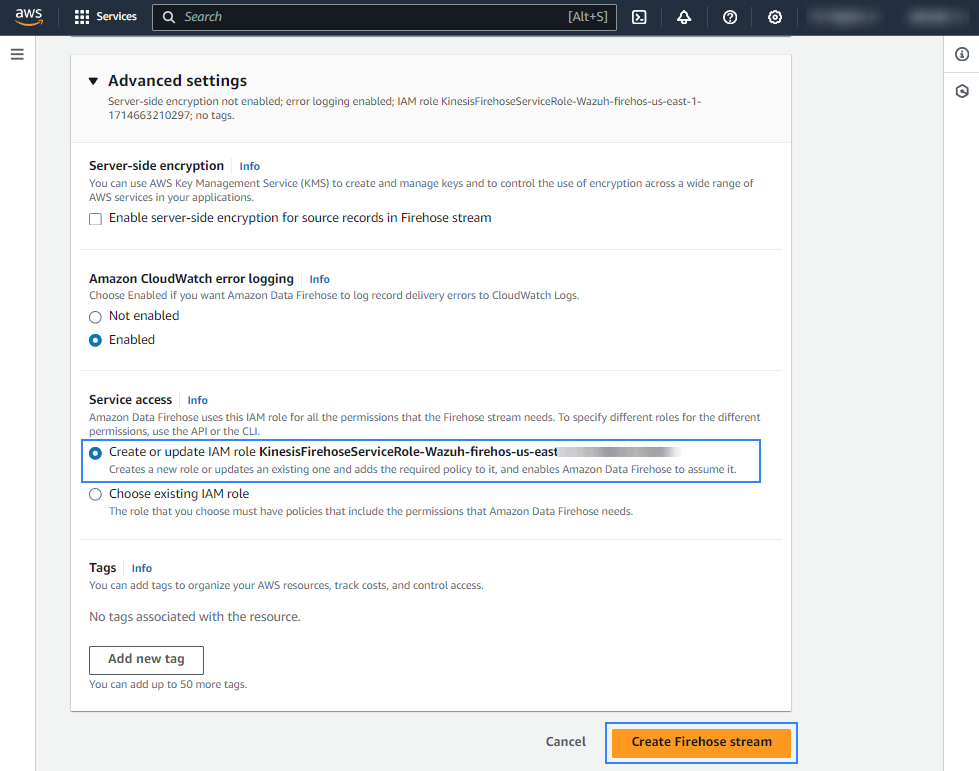
Click Create Firehose stream at the end of the page. The new delivery stream will be created and its details will be shown as follows.
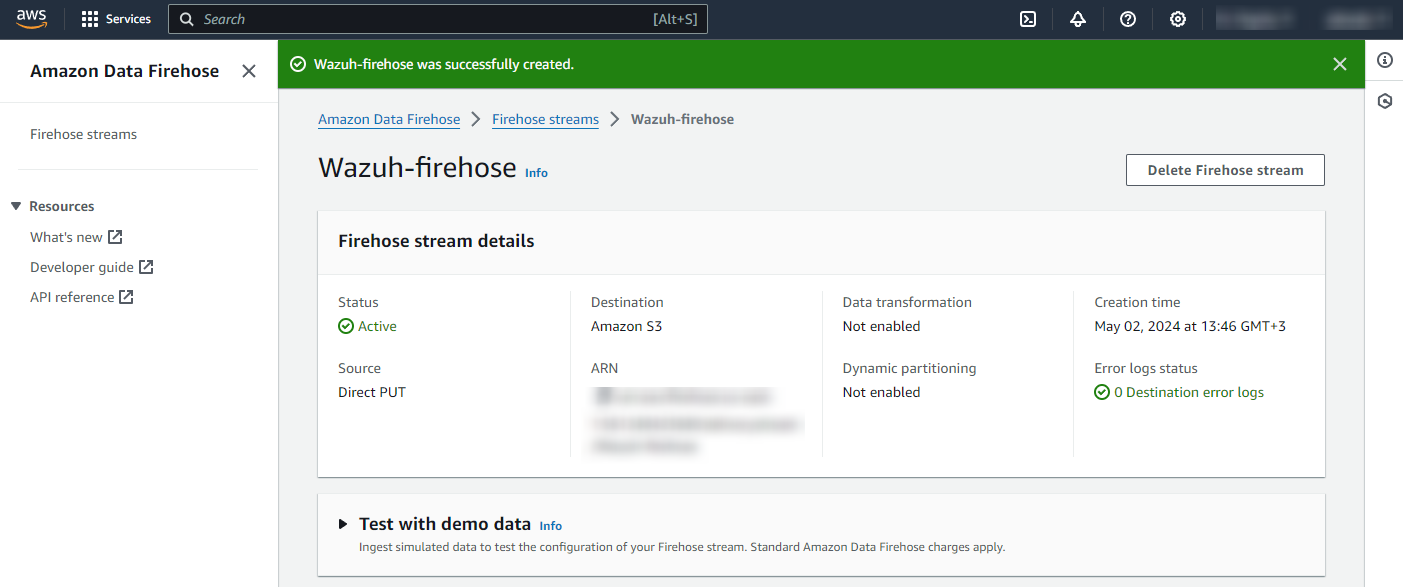
Amazon EventBridge configuration
Configure an Amazon EventBridge rule to send Macie events to the Amazon Data Firehose delivery stream created in the previous step.
On your AWS console, search for "eventbridge" in the search bar at the top of the page or navigate to Services > Application Integration > EventBridge.
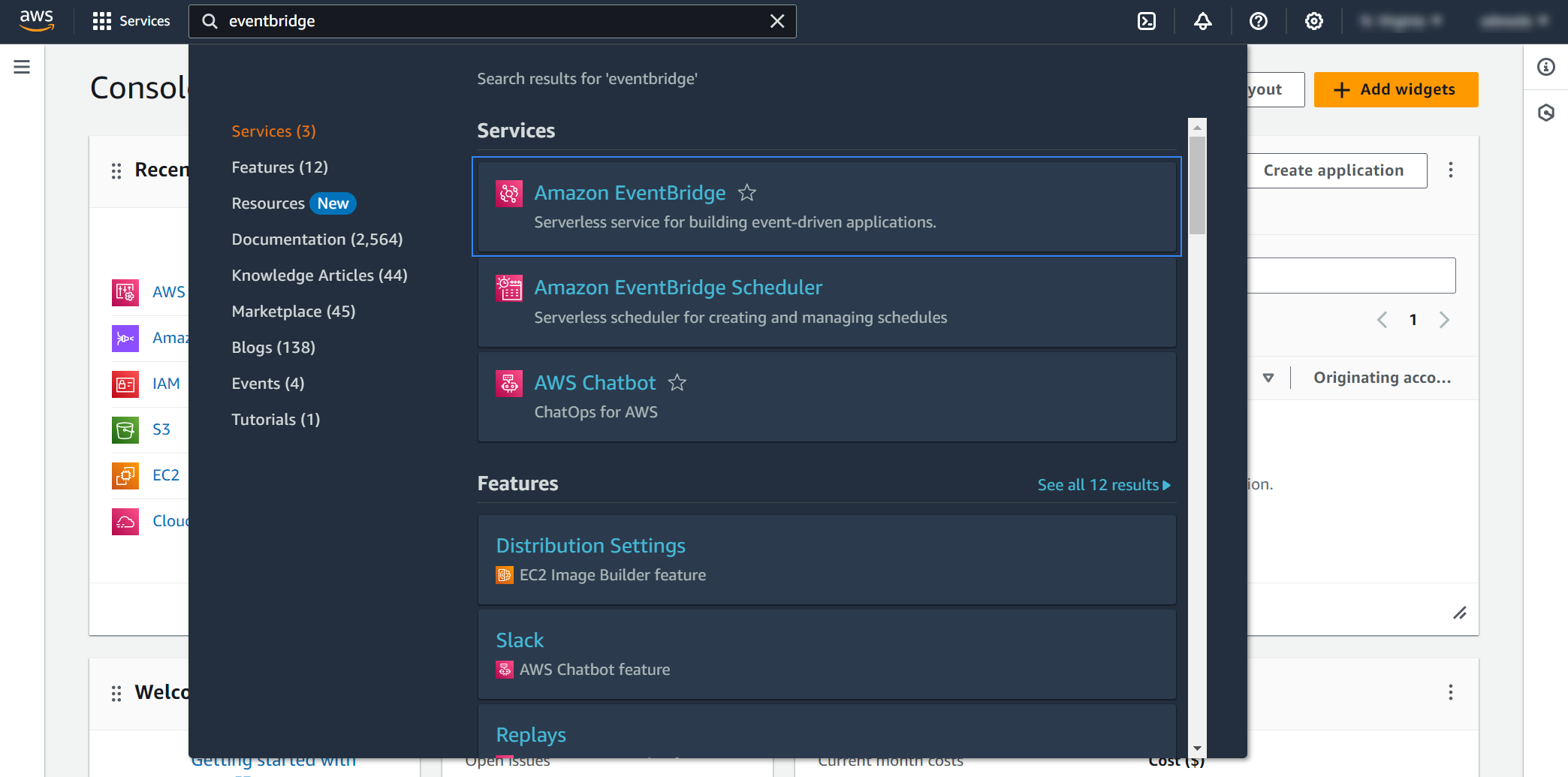
Click Create rule.
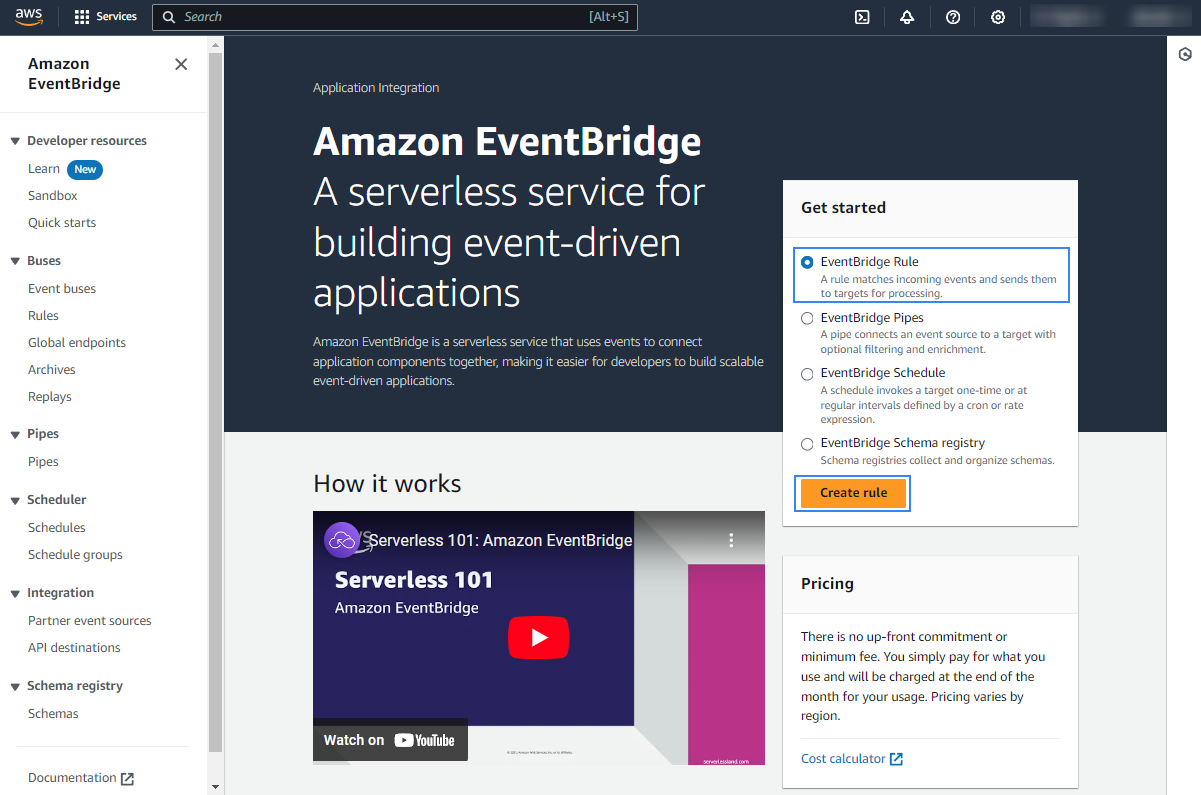
Assign a name to the rule and select the Rule with an event pattern option.
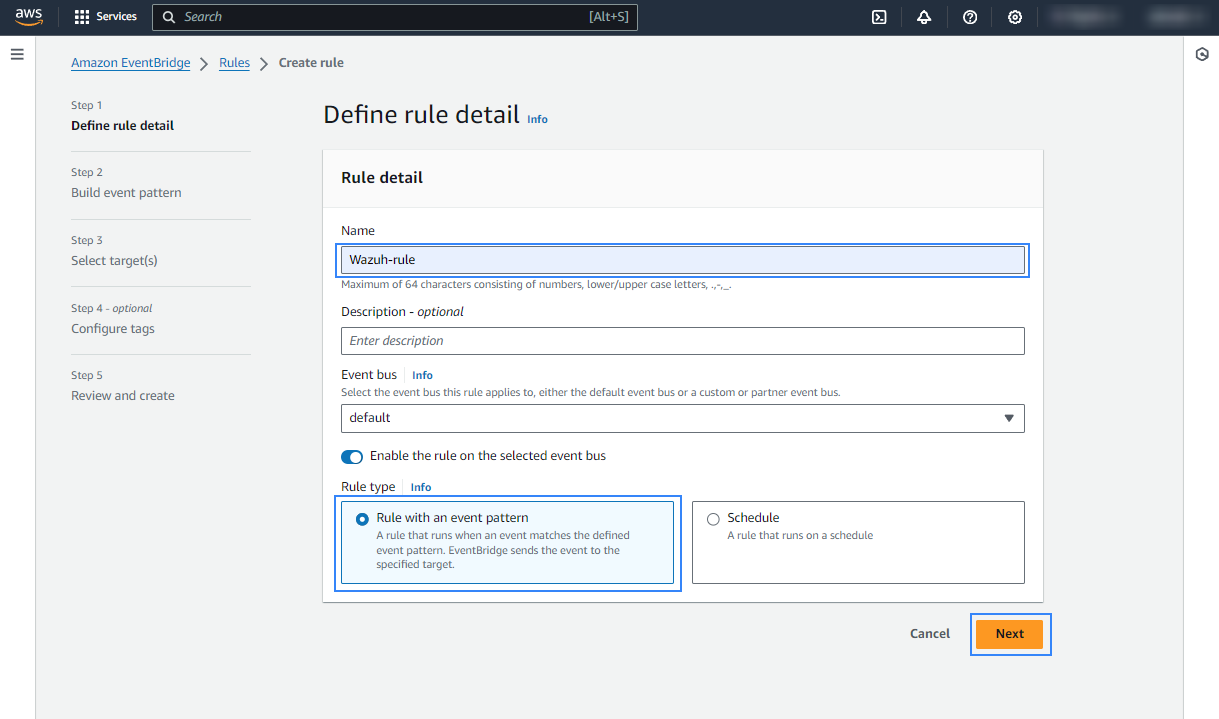
In the Build event pattern section, choose AWS events or EventBridge partner events as Event source.
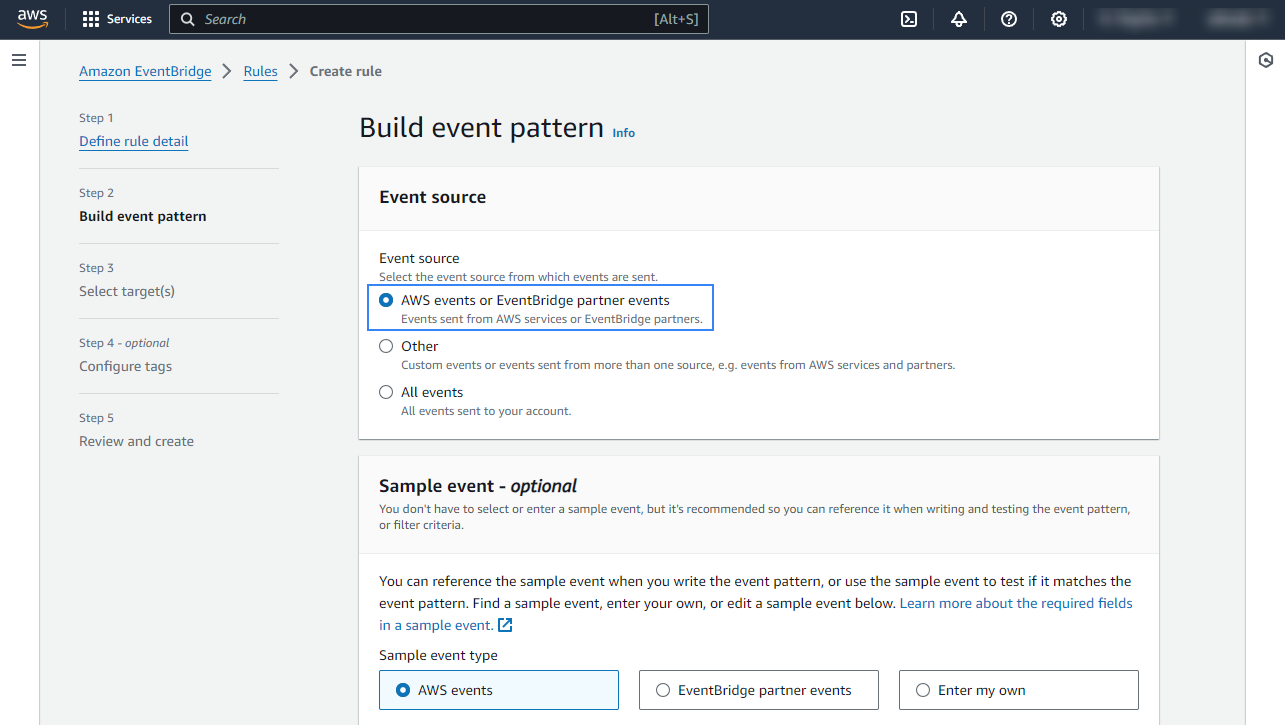
In the Event pattern section, choose AWS services as Event source, Macie as AWS service, and All Events as Event type. Click Next to apply the configuration.
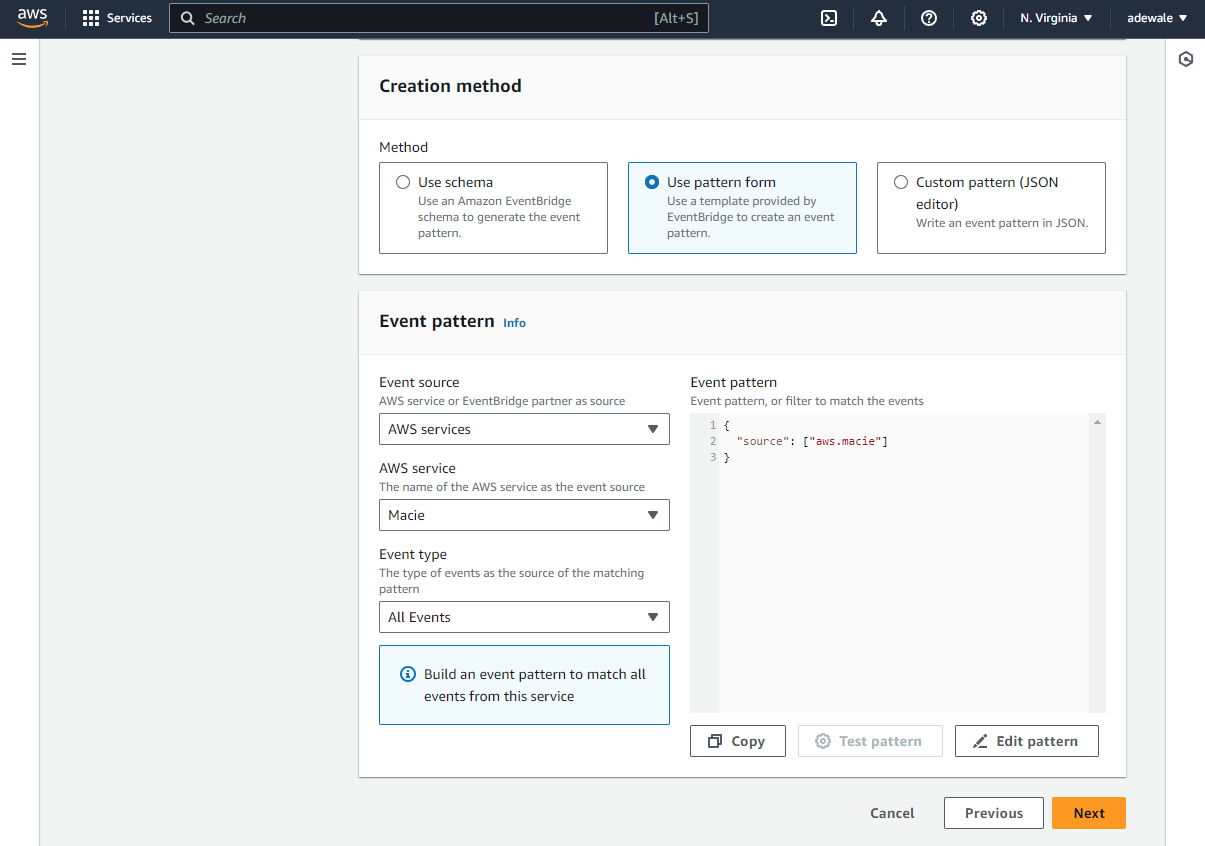
Under Select a target, choose Firehose delivery stream and select the stream created previously. Also, create a new role to access the delivery stream. Click Next to apply the configuration.
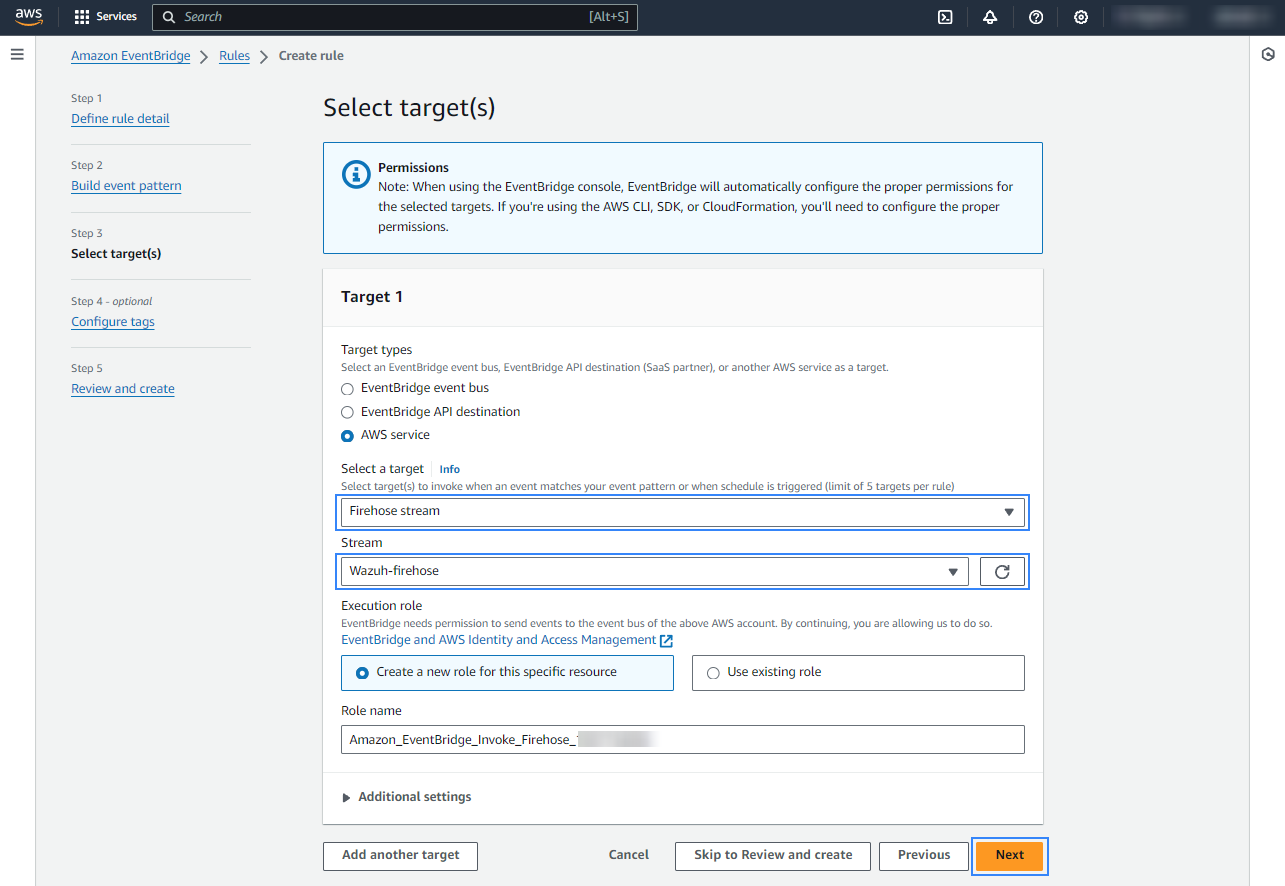
Review the configuration and click Create rule.
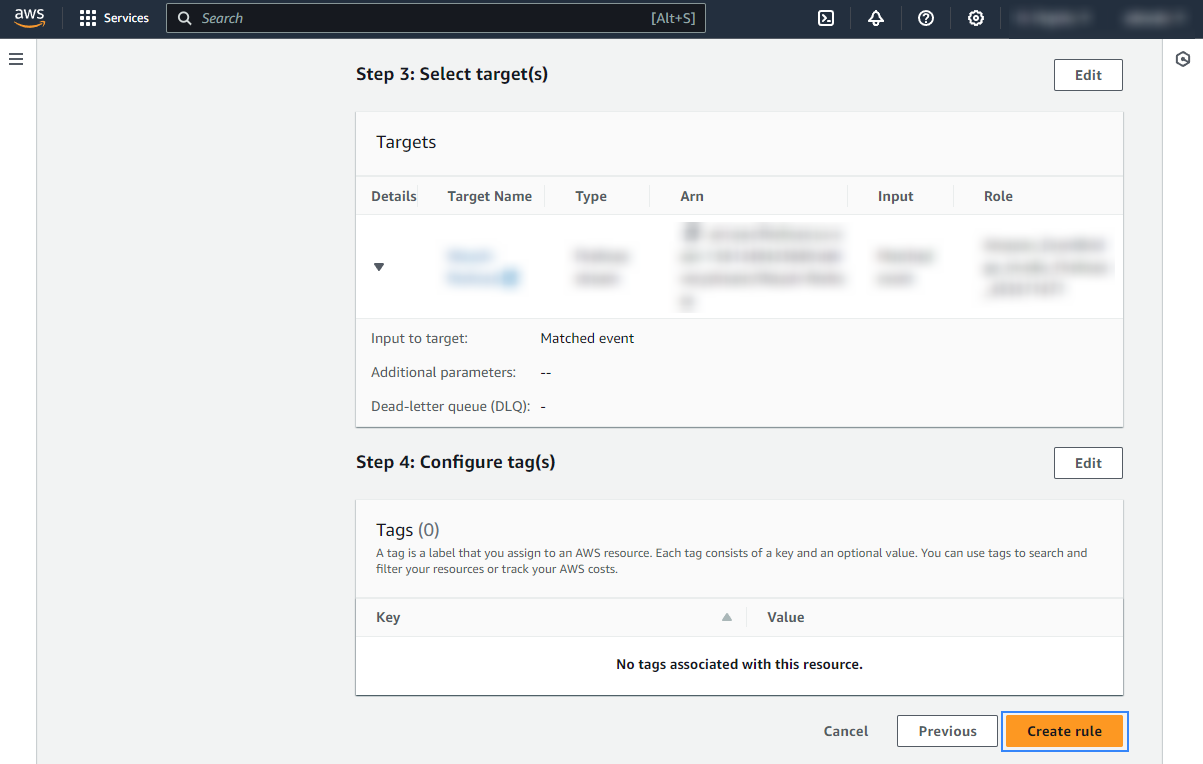
Once the rule is created, every time a Macie event is sent, it will be stored in the specified S3 bucket. Remember to first enable the Macie service, otherwise, you won't get any data.
Amazon Macie configuration
On your AWS console, search for "Amazon Macie" in the search bar and click Amazon Macie from the results.
You'll have this interface if this is the first time of setting up the service, click Get started to proceed.
Click Enable Macie to enable the service.
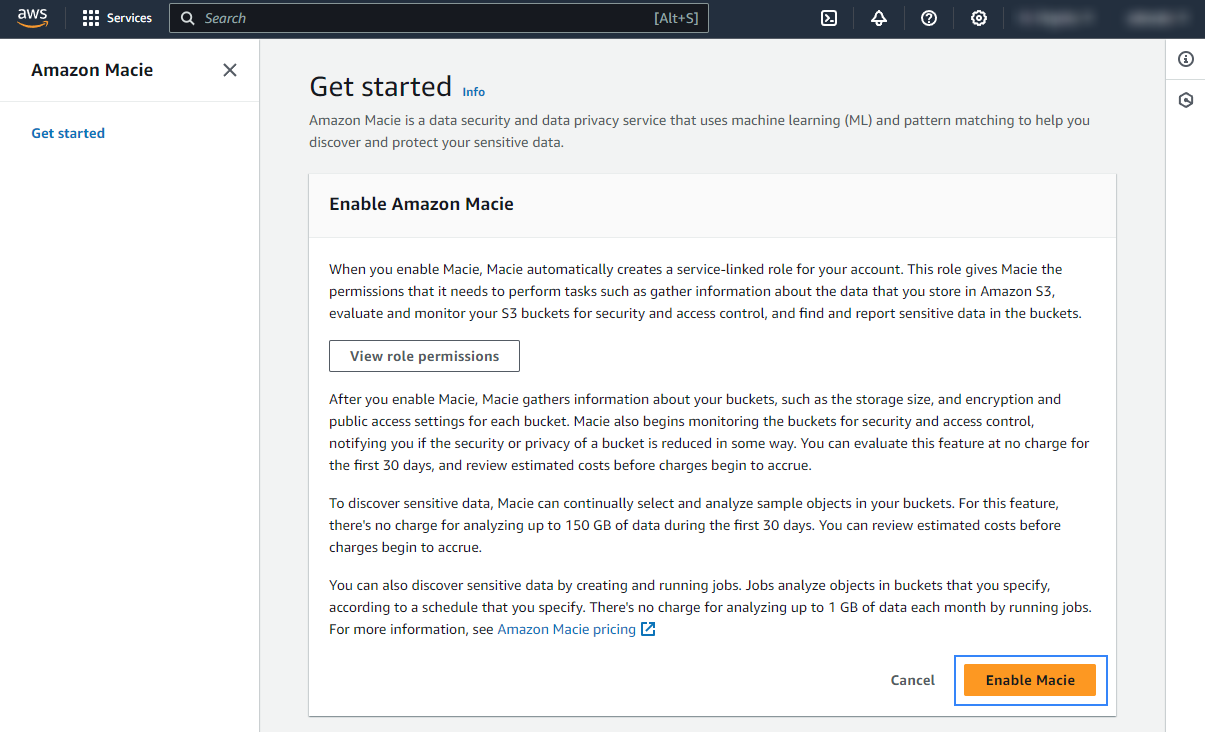
Once enabled, Macie provides visibility into data security risks and enables automated protection against those risks. Check the official AWS documentation to learn more about the service.
Policy configuration
Follow the creating an AWS policy guide to create a policy using the Amazon Web Services console.
Take into account that the policies below follow the principle of least privilege to ensure that only the minimum permissions are provided to the AWS IAM user.
To allow an AWS user to use the Wazuh module for AWS with read-only permissions, it must have a policy like the following attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::<WAZUH_AWS_BUCKET>/*",
"arn:aws:s3:::<WAZUH_AWS_BUCKET>"
]
}
]
}
If it is necessary to delete the log files once they have been collected, the associated policy would be as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::<WAZUH_AWS_BUCKET>/*",
"arn:aws:s3:::<WAZUH_AWS_BUCKET>"
]
}
]
}
Note
<WAZUH_AWS_BUCKET> is a placeholder. Replace it with the actual name of the bucket from which you want to retrieve logs.
After creating a policy, you can attach it directly to a user or to a group to which the user belongs. In attaching a policy to an IAM user group, you see how to attach a policy to a group. More information on how to use other methods is available in the AWS documentation.
Configure Wazuh to process Amazon Macie logs
Access the Wazuh configuration in Server management > Settings using the Wazuh dashboard or by manually editing the
/var/ossec/etc/ossec.conffile in the Wazuh server or agent.
Add the following Wazuh module for AWS configuration to the file, replacing
<WAZUH_AWS_BUCKET>with the name of the S3 bucket:<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>yes</run_on_start> <skip_on_error>yes</skip_on_error> <bucket type="custom"> <name><WAZUH_AWS_BUCKET></name> <path>macie</path> <aws_profile>default</aws_profile> </bucket> </wodle>
Note
Check the Wazuh module for AWS reference manual to learn more about each setting.
Restart Wazuh in order to apply the changes:
Wazuh manager:
# systemctl restart wazuh-manager
Wazuh agent:
# systemctl restart wazuh-agent
Use case
Amazon S3 (Simple Storage Service) provides secure and reliable storage capacity in the cloud. When using this service, it is highly recommended to monitor it to detect misconfigurations and sensitive data leakage.
Below is a use case for Wazuh alerts built for S3.
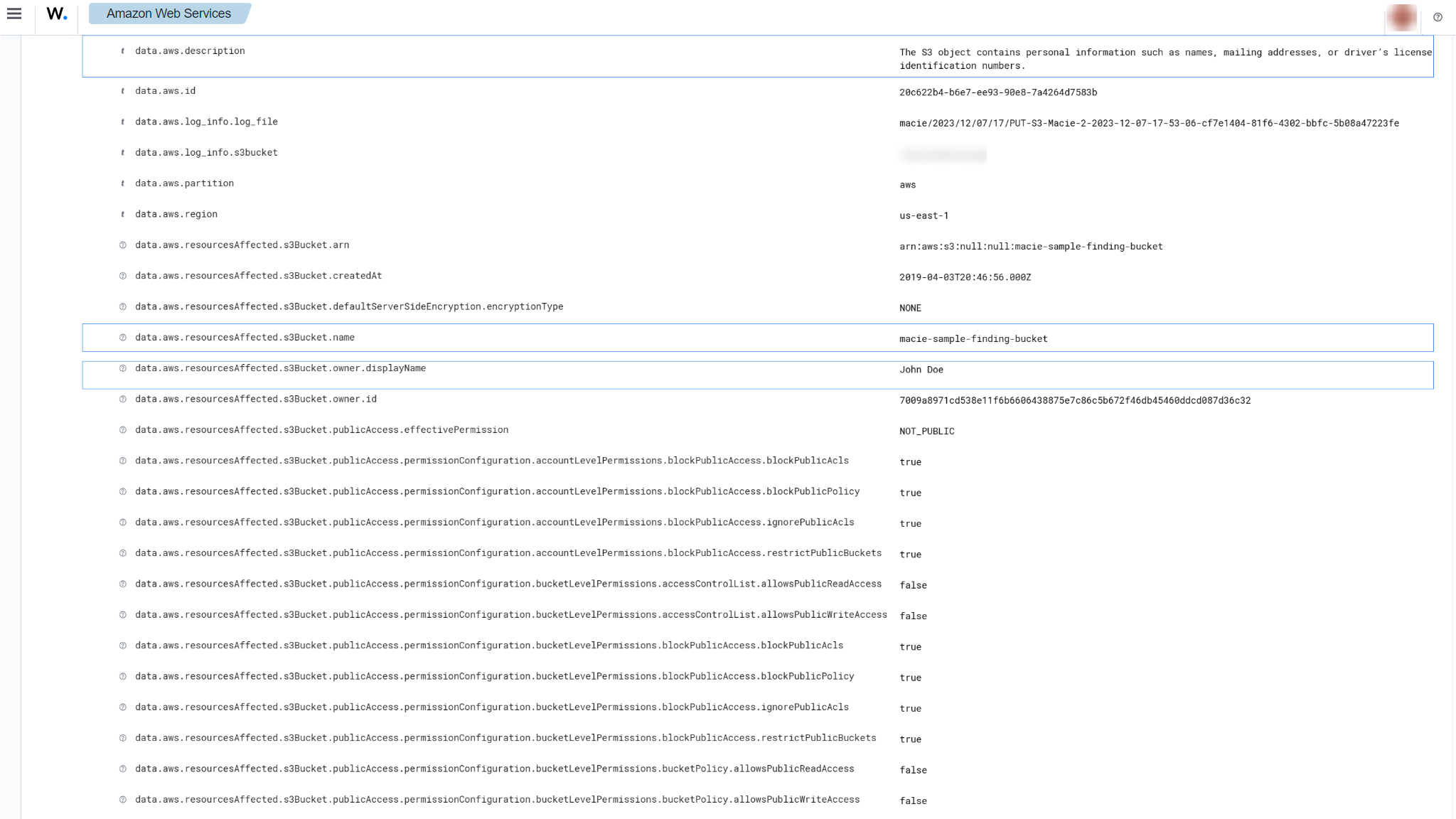
Sensitive data disclosure in S3 bucket
When sensitive data such as financial information, credentials, and personal information are found in an S3 bucket, the following alerts with rule ID 80352 and 80354 will be displayed on the Wazuh dashboard.
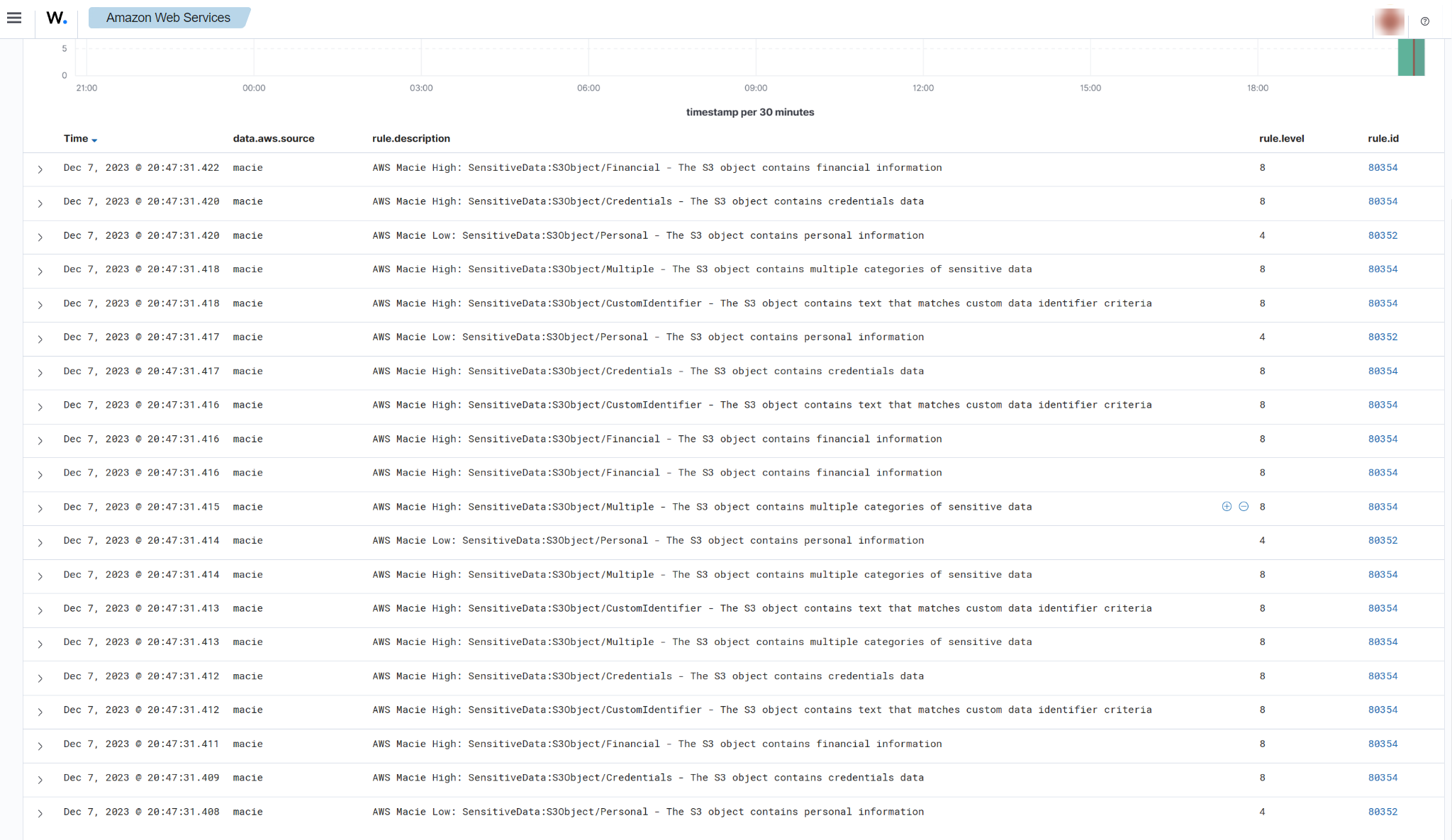
You can expand the alert to see more information such as the description of the alert, and details about the affected S3 bucket.