Malware detection
Wazuh offers several capabilities that support malware detection. The Malware detection module uses the following integrations and methods to detect malicious activities on a monitored endpoint:
File integrity monitoring and threat detection rules.
Rootkit behavior detection rules.
CDB lists and threat intelligence to detect and remove malicious files.
VirusTotal integration for malware detection.
File integrity monitoring and YARA scans for malware detection.
Custom rules to detect malware IOC.
ClamAV logs collection.
Windows Defender logs collection.
These Malware detection components of Wazuh help you comply with the following NIST 800-53 controls:
SI-3 Malicious code protection: “Malicious code protection mechanisms include both signature and non-signature-based technologies. Non-signature-based detection mechanisms include artificial intelligence techniques that use heuristics to detect, analyze, and describe the characteristics or behavior of malicious code and to provide controls against such code for which signatures do not yet exist or for which existing signatures may not be effective. Such malicious code includes polymorphic malicious code (i.e., code that changes signatures when it replicates). Non-signature-based mechanisms also include reputation-based technologies. In addition to the above technologies, pervasive configuration management, comprehensive software integrity controls, and anti-exploitation software may be effective in preventing the execution of unauthorized code. Malicious code may be present in commercial off-the-shelf software as well as custom-built software and could include logic bombs, backdoors, and other types of attacks that could affect organizational mission and business functions.”
SI-7 Software, firmware, and information integrity: “Unauthorized changes to software, firmware, and information can occur due to errors or malicious activity. Software includes operating systems (with key internal components, such as kernels or drivers), middleware, and applications. Firmware interfaces include Unified Extensible Firmware Interface (UEFI) and Basic Input/Output System (BIOS). Information includes personally identifiable information and metadata that contains security and privacy attributes associated with information. Integrity-checking mechanisms-including parity checks, cyclic redundancy checks, cryptographic hashes, and associated tools-can automatically monitor the integrity of systems and hosted applications.”
The NIST 800-53 controls above require users to have tools and processes to detect malicious code and modified software and firmware. Wazuh supports the detection of suspicious system binaries, malware, and suspicious processes using out-of-the-box rules, VirusTotal and YARA integrations, and CDB lists. In addition, Wazuh also includes a File Integrity Monitoring module that allows users to continuously monitor specific files and paths that malware might use.
Use case: Detecting suspicious binaries
This use case shows how Wazuh meets the SI-3 Malicious code protection requirement by detecting a malicious binary on a monitored endpoint. In this scenario, the Wazuh rootcheck module is used to detect a trojan system binary on a Ubuntu 22.04 endpoint.
The Wazuh rootcheck module is enabled by default on the Wazuh agent configuration file. The rootcheck section explains the options in the rootcheck module.
Create a copy of the original system binary:
$ sudo cp -p /usr/bin/w /usr/bin/w.copy
Replace the original system binary /usr/bin/w with the following shell script:
$ sudo tee /usr/bin/w << EOF #!/bin/bash echo "`date` this is evil" > /tmp/trojan_created_file echo 'test for /usr/bin/w trojaned file' >> /tmp/trojan_created_file # Now running original binary /usr/bin/w.copy EOF
Restart the Wazuh agent to see the relevant alert:
$ sudo systemctl restart wazuh-agent
Navigate to the Threat Hunting dashboard. Search for the event with rule ID
510.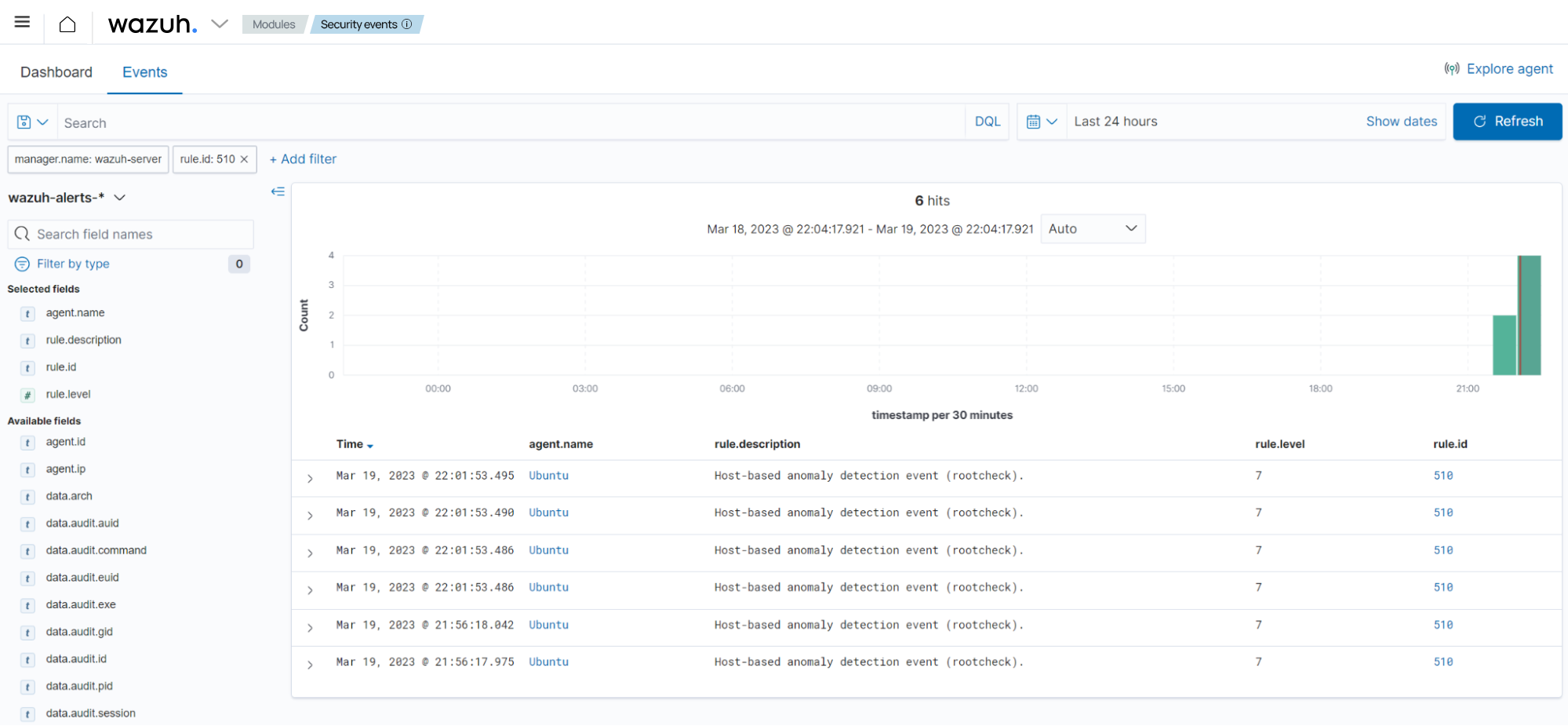
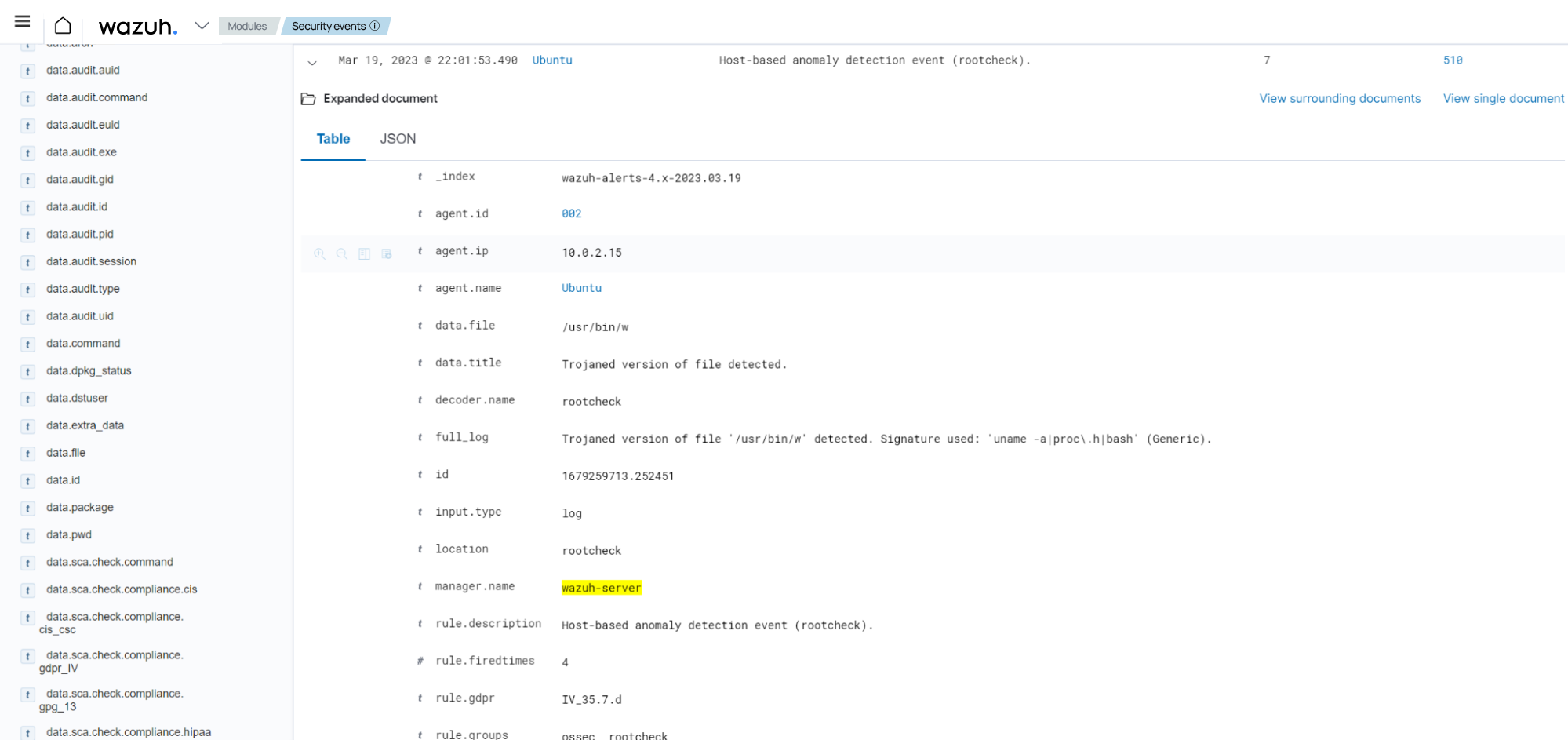
The image above shows an example of a suspicious binary file detected on a monitored endpoint.