File integrity monitoring and threat detection rules
Creating and modifying files on infected endpoints is typical malware behavior. File integrity monitoring enables you to check selected directories and generate alerts when there are any file changes.
Below, we show an example of an alert generated by the FIM module when it detects a change in a monitored file:
{
"timestamp":"2022-11-14T18:07:18.810+0200",
"rule":{
"level":7,
"description":"Integrity checksum changed.",
"id":"550",
"mitre":{
"id":[
"T1565.001"
],
"tactic":[
"Impact"
],
"technique":[
"Stored Data Manipulation"
]
},
"firedtimes":1,
"mail":false,
"groups":[
"ossec",
"syscheck",
"syscheck_entry_modified",
"syscheck_file"
],
"pci_dss":[
"11.5"
],
"gpg13":[
"4.11"
],
"gdpr":[
"II_5.1.f"
],
"hipaa":[
"164.312.c.1",
"164.312.c.2"
],
"nist_800_53":[
"SI.7"
],
"tsc":[
"PI1.4",
"PI1.5",
"CC6.1",
"CC6.8",
"CC7.2",
"CC7.3"
]
},
"agent":{
"id":"010",
"name":"Ubuntu",
"ip":"10.0.2.15"
},
"manager":{
"name":"localhost.localdomain"
},
"id":"1668442038.4872352",
"full_log":"File '/test/hello' modified\nMode: realtime\nChanged attributes: size,mtime,md5,sha1,sha256\nSize changed from '0' to '8'\nOld modification time was: '1668441994', now it is '1668442038'\nOld md5sum was: 'd41d8cd98f00b204e9800998ecf8427e'\nNew md5sum is : '99472f8d2f760bcc394e80d09275150a'\nOld sha1sum was: 'da39a3ee5e6b4b0d3255bfef95601890afd80709'\nNew sha1sum is : '75fdf620d8a1c7e6ea7f4c24ba5ff991fbb82e86'\nOld sha256sum was: 'e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855'\nNew sha256sum is : 'a96db6890367a8bc049841501ba1b0ab38bbdca062885d94f0130b17d162dea9'\n",
"syscheck":{
"path":"/test/hello",
"mode":"realtime",
"size_before":"0",
"size_after":"8",
"perm_after":"rw-r--r--",
"uid_after":"0",
"gid_after":"0",
"md5_before":"d41d8cd98f00b204e9800998ecf8427e",
"md5_after":"99472f8d2f760bcc394e80d09275150a",
"sha1_before":"da39a3ee5e6b4b0d3255bfef95601890afd80709",
"sha1_after":"75fdf620d8a1c7e6ea7f4c24ba5ff991fbb82e86",
"sha256_before":"e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"sha256_after":"a96db6890367a8bc049841501ba1b0ab38bbdca062885d94f0130b17d162dea9",
"uname_after":"root",
"gname_after":"root",
"mtime_before":"2022-11-14T18:06:34",
"mtime_after":"2022-11-14T18:07:18",
"inode_after":3014658,
"changed_attributes":[
"size",
"mtime",
"md5",
"sha1",
"sha256"
],
"event":"modified"
},
"decoder":{
"name":"syscheck_integrity_changed"
},
"location":"syscheck"
}
Furthermore, you can write rules based on file creation and modification events to detect specific malware. For example, the following rules detect when web shells create or modify files on web servers.
<group name="linux, webshell, windows,">
<!-- This rule detects file creation. -->
<rule id="100500" level="12">
<if_sid>554</if_sid>
<field name="file" type="pcre2">(?i).php$|.phtml$|.php3$|.php4$|.php5$|.phps$|.phar$|.asp$|.aspx$|.jsp$|.cshtml$|.vbhtml$</field>
<description>[File creation]: Possible web shell scripting file ($(file)) created</description>
<mitre>
<id>T1105</id>
<id>T1505</id>
</mitre>
</rule>
<!-- This rule detects file modification. -->
<rule id="100501" level="12">
<if_sid>550</if_sid>
<field name="file" type="pcre2">(?i).php$|.phtml$|.php3$|.php4$|.php5$|.phps$|.phar$|.asp$|.aspx$|.jsp$|.cshtml$|.vbhtml$</field>
<description>[File modification]: Possible web shell content added in $(file)</description>
<mitre>
<id>T1105</id>
<id>T1505</id>
</mitre>
</rule>
<!-- This rule detects files modified with PHP web shell signatures. -->
<rule id="100502" level="15">
<if_sid>100501</if_sid>
<field name="changed_content" type="pcre2">(?i)passthru|exec|eval|shell_exec|assert|str_rot13|system|phpinfo|base64_decode|chmod|mkdir|fopen|fclose|readfile|show_source|proc_open|pcntl_exec|execute|WScript.Shell|WScript.Network|FileSystemObject|Adodb.stream</field>
<description>[File Modification]: File $(file) contains a web shell</description>
<mitre>
<id>T1105</id>
<id>T1505.003</id>
</mitre>
</rule>
</group>
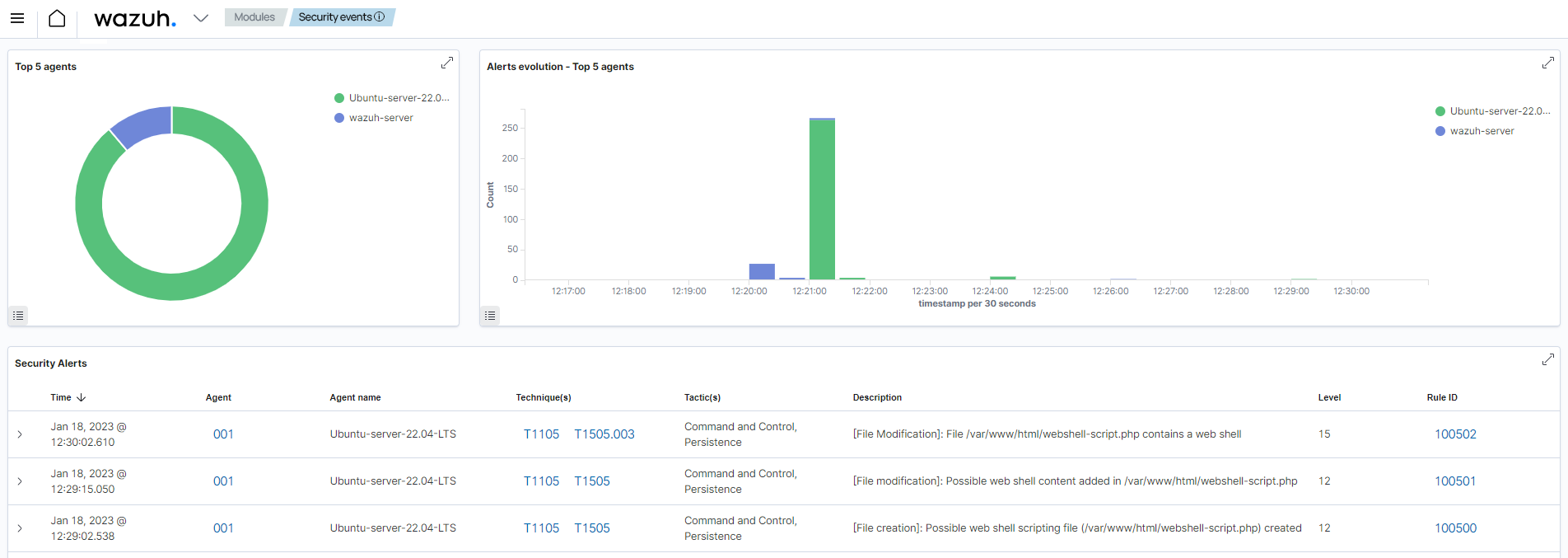
Below you can see a screenshot showing the alerts displayed on the Wazuh dashboard.