CDB lists and threat intelligence
Wazuh detects malicious files by checking the presence of their signatures in a CDB list. This CDB list must contain known malware threat intelligence indicators. A CDB list is a text file you can use to save a list of users, file hashes, IP addresses, and domain names. You can add entries to a CDB list in key:value pairs or key: only. CDB lists can act as either allow or deny lists. You can learn more about CDB lists in the documentation.
How it works
Wazuh checks if field values, such as IP address, file hashes, and others, extracted from security events during decoding are in a CDB list to hunt and detect malware. To detect malware, you can use CDB lists with the file integrity monitoring (FIM) module. We describe how it works below:
The Wazuh FIM module scans monitored directories on endpoints to detect changes such as file creation and modifications. The FIM module stores the checksums and attributes of the monitored files.
When the FIM module generates an alert, the Wazuh analysis engine compares the file attributes, for example, the file hash, to the keys in a predefined CDB list.
If the Wazuh analysis engine finds a match, it generates or suppresses an alert based on how you configure your rule.
Use case: Detecting malware using file hashes in a CDB list
In this use case, we show how you can detect malware using file hashes that you have added to a CDB list. You can use this use case to detect malicious files on a Linux endpoint on which you have installed a Wazuh agent.
Wazuh server
Create a CDB list
malware-hashesof known malware hashes and save it to the/var/ossec/etc/listsdirectory on the Wazuh server.# vi /var/ossec/etc/lists/malware-hashes
Add the known malware hashes to the file as
key:valuepairs. In this case, you can use the known MD5 hashes of the Mirai and Xbash malware as shown below.e0ec2cd43f71c80d42cd7b0f17802c73:mirai 55142f1d393c5ba7405239f232a6c059:Xbash
Add a reference to the CDB list in the Wazuh manager configuration file
/var/ossec/etc/ossec.conf. You can do this by specifying the path to the list within the<ruleset>block:... <ruleset> <!-- Default ruleset --> <decoder_dir>ruleset/decoders</decoder_dir> <rule_dir>ruleset/rules</rule_dir> <rule_exclude>0215-policy_rules.xml</rule_exclude> <list>etc/lists/audit-keys</list> <list>etc/lists/amazon/aws-eventnames</list> <list>etc/lists/security-eventchannel</list> <list>etc/lists/malware-hashes</list> <ruleset> ...
Create a custom rule in the
/var/ossec/etc/rules/local_rules.xmlfile on the Wazuh server. The rule generates alerts when the Wazuh analysis engine matches the MD5 hash of a new or modified file to a hash in the CDB list. Rules 554 and 550 must previously match indicating a recently created or modified file.<group name="malware,"> <rule id="110002" level="13"> <!-- The if_sid tag references the built-in FIM rules --> <if_sid>554, 550</if_sid> <list field="md5" lookup="match_key">etc/lists/malware-hashes</list> <description>File with known malware hash detected: $(file)</description> <mitre> <id>T1204.002</id> </mitre> </rule> </group>
Restart the Wazuh manager to apply changes.
# systemctl restart wazuh-manager
Linux endpoint
Configure directory monitoring by adding the
<directories>block specifying the folders you want to monitor in the agent configuration file or using the centralized configuration option.<ossec_config> <syscheck> <disabled>no</disabled> <directories check_all="yes" realtime="yes"><PATH_TO_MONITORED_DIRECTORY></directories> </syscheck> </ossec_config>
Note
The
check_alloption ensures Wazuh checks all file attributes including the file size, permissions, owner, last modification date, inode, and the hash sums.Apply the changes if you edited the local configuration file:
# systemctl restart wazuh-agent
If you used centralized configuration, no manual restart is required. The agent reloads automatically after receiving the update.
Test the configuration
To test that everything works correctly, download the Mirai and Xbash malware samples to the directory the FIM module is monitoring.
Warning
These malicious files are dangerous, so use them for testing purposes only. Do not install them in production environments.
Download the malware samples. Replace
<PATH_TO_MONITORED_DIRECTORY>with the path of the monitored directory.$ sudo curl https://raw.githubusercontent.com/wazuh/wazuh-documentation/refs/heads/4.14/resources/samples/mirai --output <PATH_TO_MONITORED_DIRECTORY>/mirai $ sudo curl https://raw.githubusercontent.com/wazuh/wazuh-documentation/refs/heads/4.14/resources/samples/xbash --output <PATH_TO_MONITORED_DIRECTORY>/Xbash
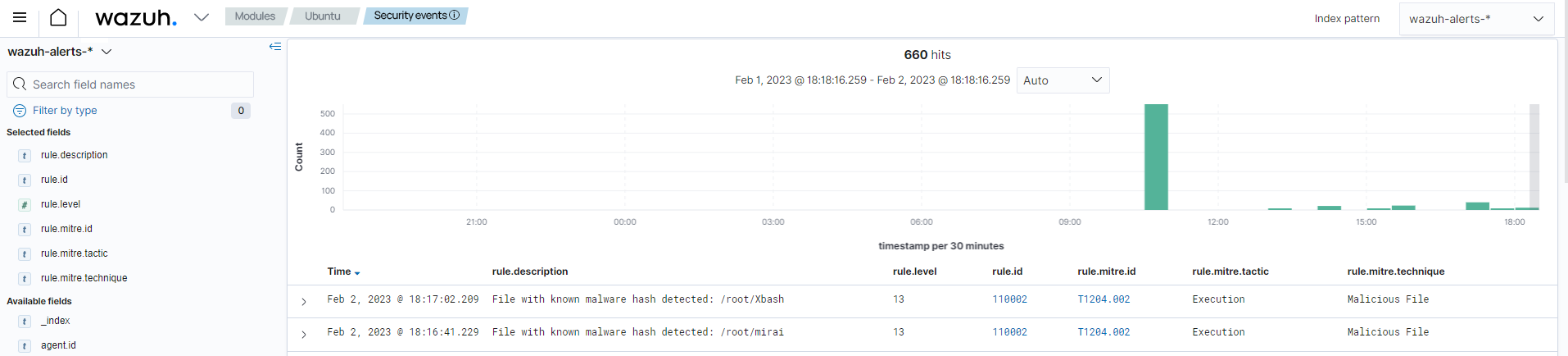
Visualize the alerts
You can see these alerts on the Wazuh dashboard. To do this, go to the Threat Hunting module of the Wazuh dashboard to view the alerts.