Amazon S3 Server Access
Amazon S3 server access logging provides detailed records for the requests that are made to a bucket. Server access logs are useful for many applications. For example, access log information can be useful in security and access audits. It can also help you learn about your customer base and understand your Amazon S3 bill.
AWS configuration
The following sections cover how to configure the Amazon S3 Server Access service to integrate with Wazuh.
Amazon S3 server access configuration
Create a new S3 bucket to store the access logs in it. If you want to use an existing one, skip this step.
On your AWS console search for "S3" or go to Services > Storage > S3.
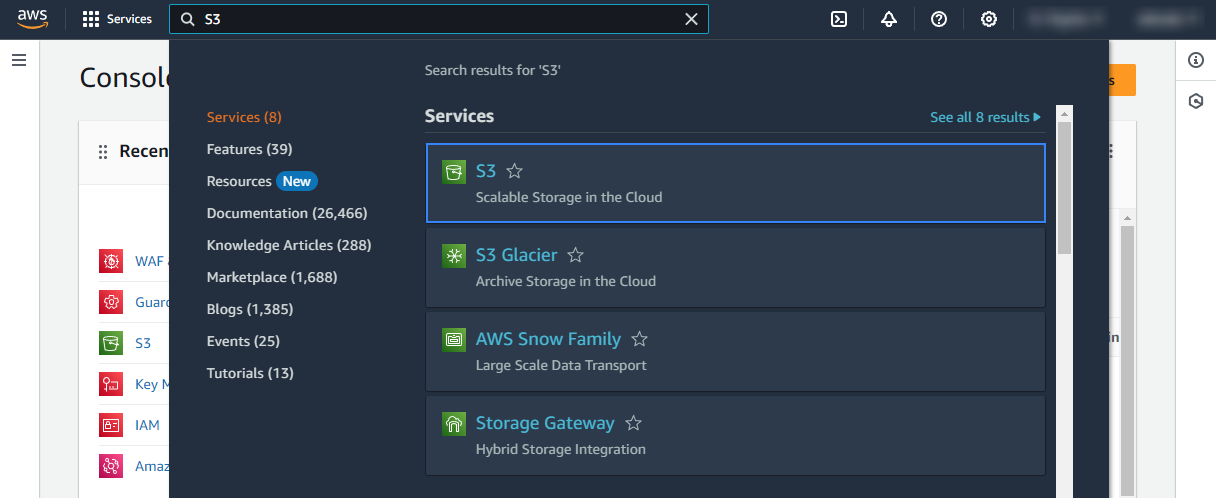
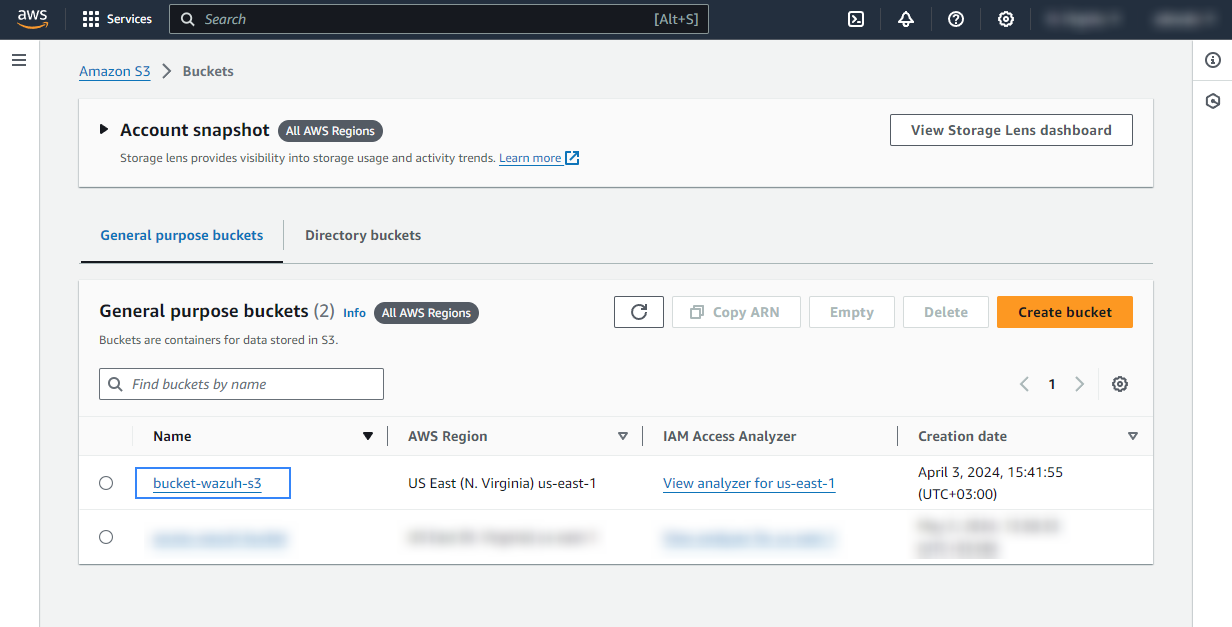
Look for the S3 bucket you want to monitor and click on its name.
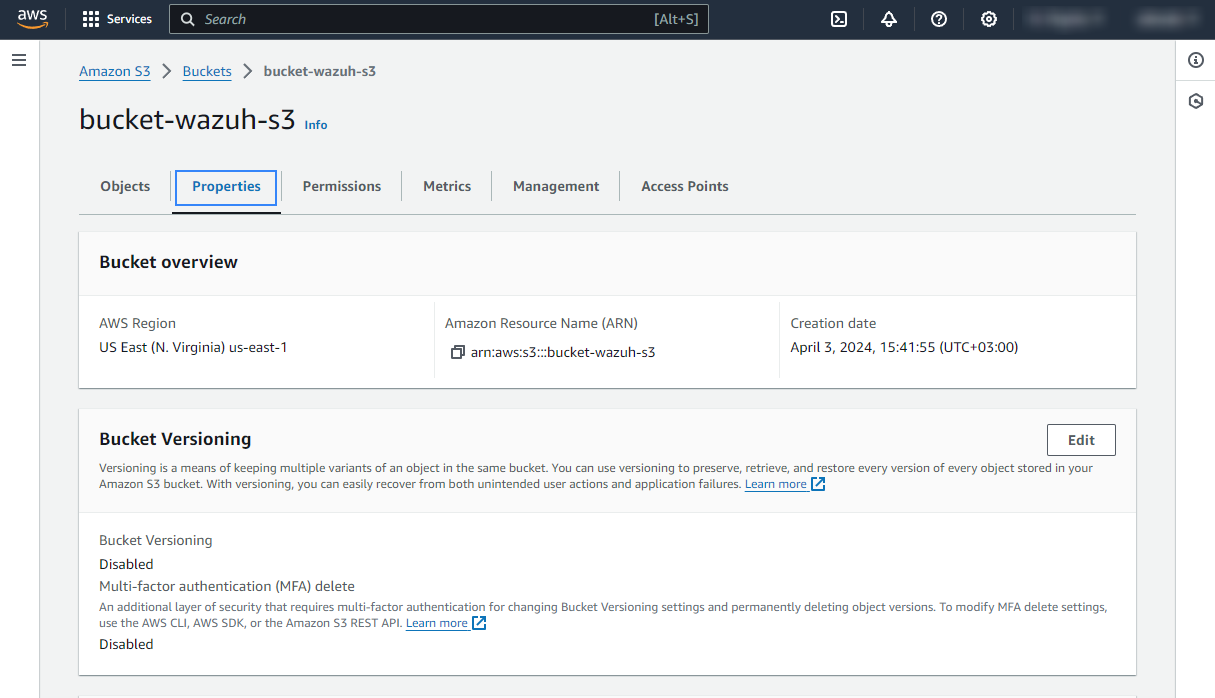
Go to the Properties tab, scroll down until you find the Server access logging, and click Edit.
Check the Enable option, and click Browse S3 to look for the bucket in which you want S3 Server Access logs to be stored. In our case, the logs are stored in the
s3-server-logs/path of the monitored S3 bucket.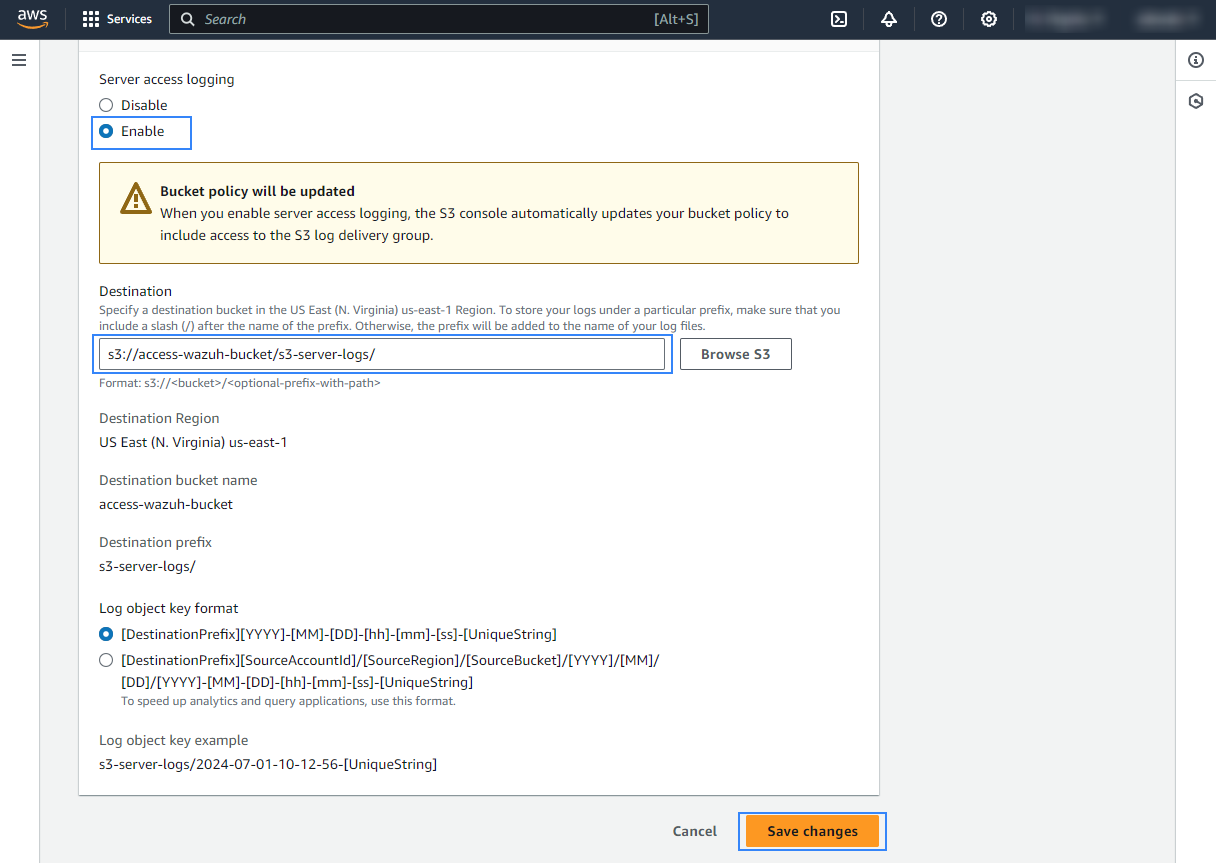
Note
It is possible to store the S3 Server Access logs in the same bucket to be monitored. It is also possible to specify a custom path inside the bucket to store the logs in it.
Finally, click on the Save changes. S3 Server Access logs will start to be stored in the specified path.
Policy configuration
Follow the creating an AWS policy guide to create a policy using the Amazon Web Services console.
Take into account that the policies below follow the principle of least privilege to ensure that only the minimum permissions are provided to the AWS IAM user.
To allow an AWS user to use the Wazuh module for AWS with read-only permissions, it must have a policy like the following attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::<WAZUH_AWS_BUCKET>/*",
"arn:aws:s3:::<WAZUH_AWS_BUCKET>"
]
}
]
}
If it is necessary to delete the log files once they have been collected, the associated policy would be as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::<WAZUH_AWS_BUCKET>/*",
"arn:aws:s3:::<WAZUH_AWS_BUCKET>"
]
}
]
}
Note
<WAZUH_AWS_BUCKET> is a placeholder. Replace it with the actual name of the bucket from which you want to retrieve logs.
After creating a policy, you can attach it directly to a user or to a group to which the user belongs. In attaching a policy to an IAM user group, you see how to attach a policy to a group. More information on how to use other methods is available in the AWS documentation.
Configure Wazuh to process Amazon S3 Server Access logs
Access the Wazuh configuration in Server management > Settings using the Wazuh dashboard or by manually editing the
/var/ossec/etc/ossec.conffile in the Wazuh server or agent.
Add the following Wazuh module for AWS configuration to the file, replacing
<WAZUH_AWS_BUCKET>with the name of the S3 bucket:<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>yes</run_on_start> <skip_on_error>yes</skip_on_error> <bucket type="server_access"> <name><WAZUH_AWS_BUCKET></name> <!-- PUT THE S3 BUCKET CHOSEN IN STEP 5 HERE --> <path>s3-server-logs</path> <!-- IF THE LOGS ARE NOT STORED IN THE BUCKET'S ROOT PATH, PUT THE PATH TO THE LOGS CHOSEN IN STEP 5 HERE --> <aws_profile>default</aws_profile> </bucket> </wodle>
Save the changes and restart Wazuh to apply the changes. The service can be manually restarted using the following command outside the Wazuh dashboard:
Wazuh manager:
# systemctl restart wazuh-manager
Wazuh agent:
# systemctl restart wazuh-agent
Use case
Amazon S3 Server Access logs provide detailed records for the requests that were made to a bucket.
Below is a use case for Wazuh alerts built for Amazon S3 Server Access logs.
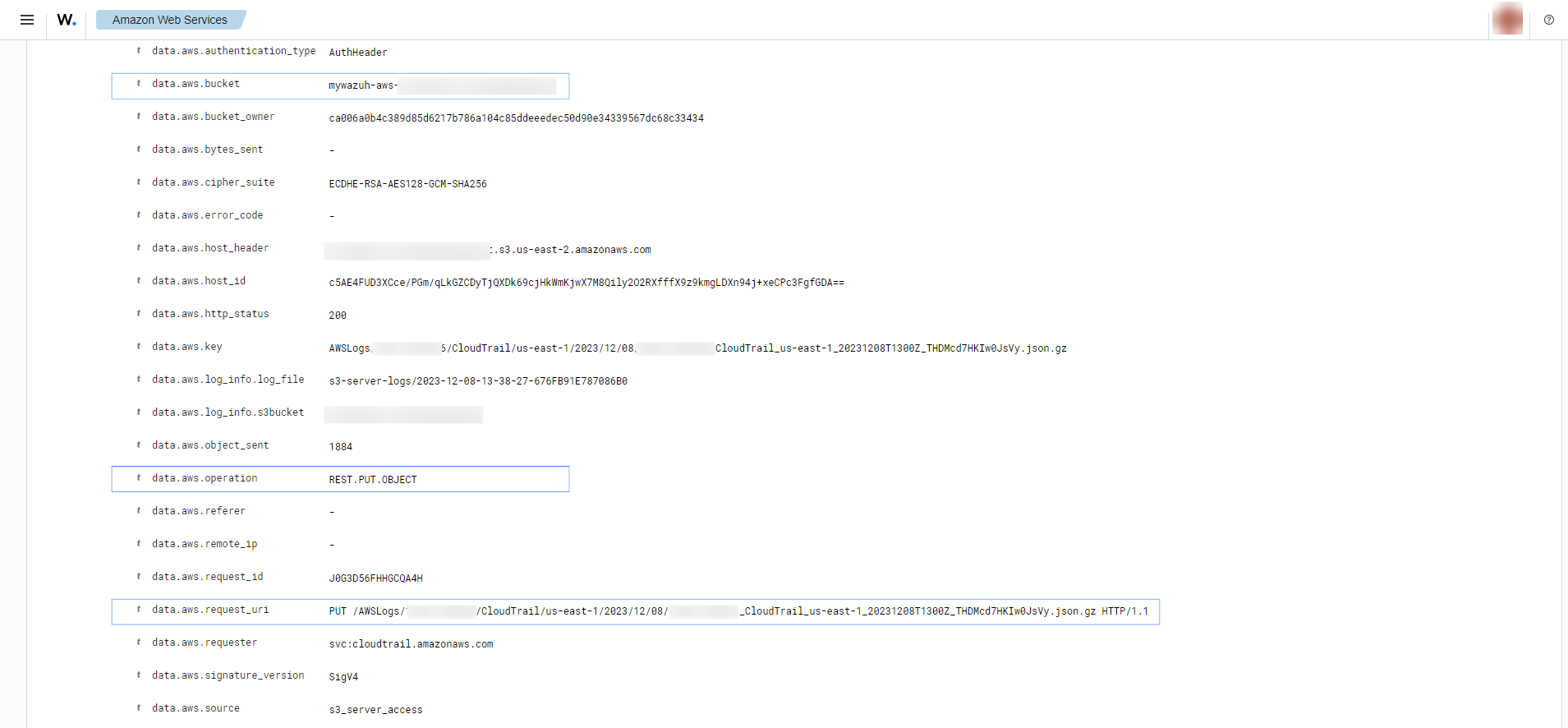
Monitoring server access logs
The following screenshots shows some alerts with rule ID 80364 and 80367 generated for requests made to a monitored S3 bucket.
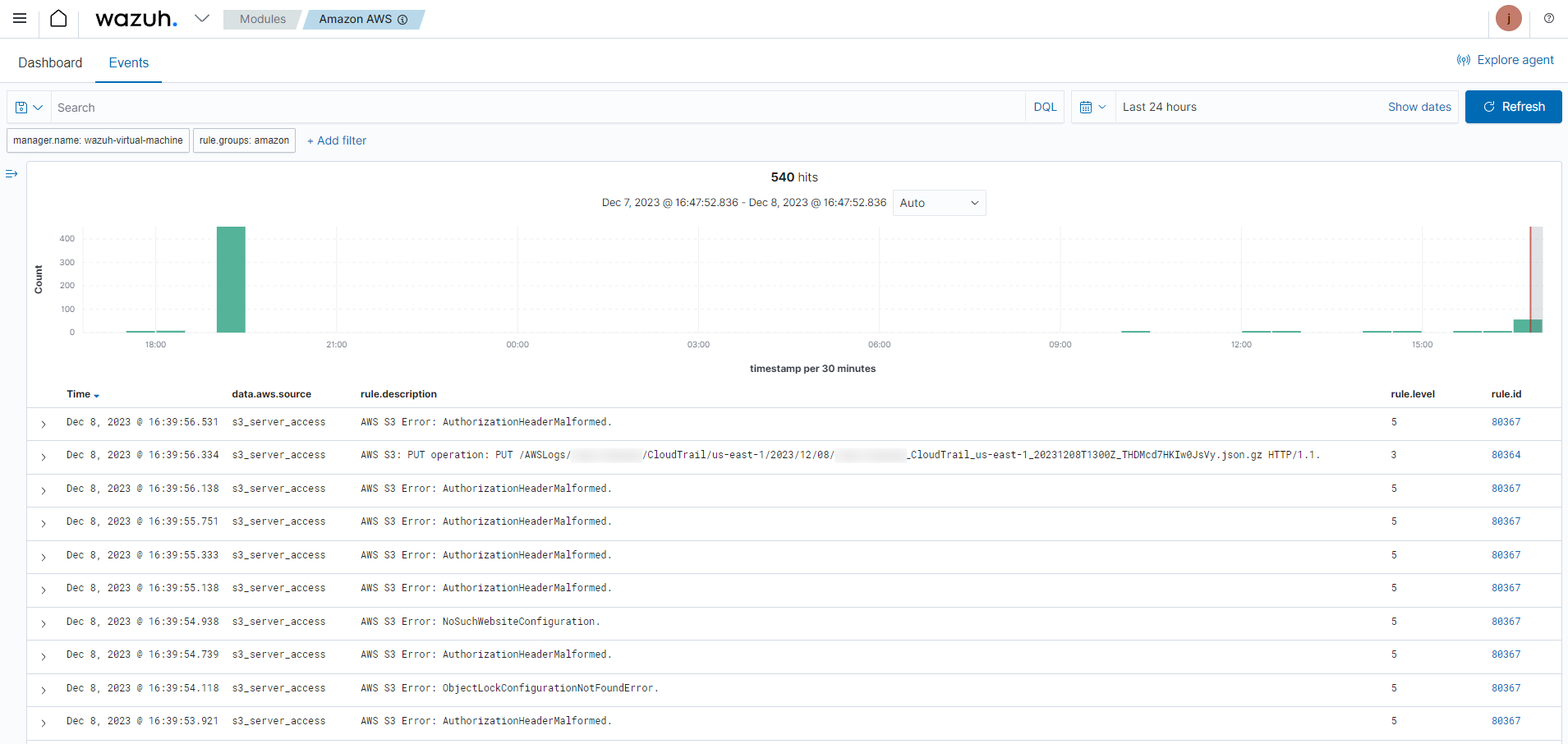
Expand an alert to find more information about the monitored S3 bucket, the operation being performed, and the request URI.