Amazon GuardDuty
Amazon GuardDuty is a threat detection service that continuously monitors for malicious or unauthorized behavior to help you protect your AWS accounts and workloads. It monitors for activity such as unusual API calls or potentially unauthorized deployments that indicate a possible account compromise. GuardDuty also detects potentially compromised instances or reconnaissance by attackers.
AWS configuration
The following sections cover how to configure the different services required to integrate Guard Duty into Wazuh.
Amazon GuardDuty configuration
Create a new S3 bucket. If you want to use an existing bucket, skip this step.
On your AWS console, search for "guardduty" in the search bar at the top of the page or navigate to Services > Security, Identity, & Compliance > GuardDuty.
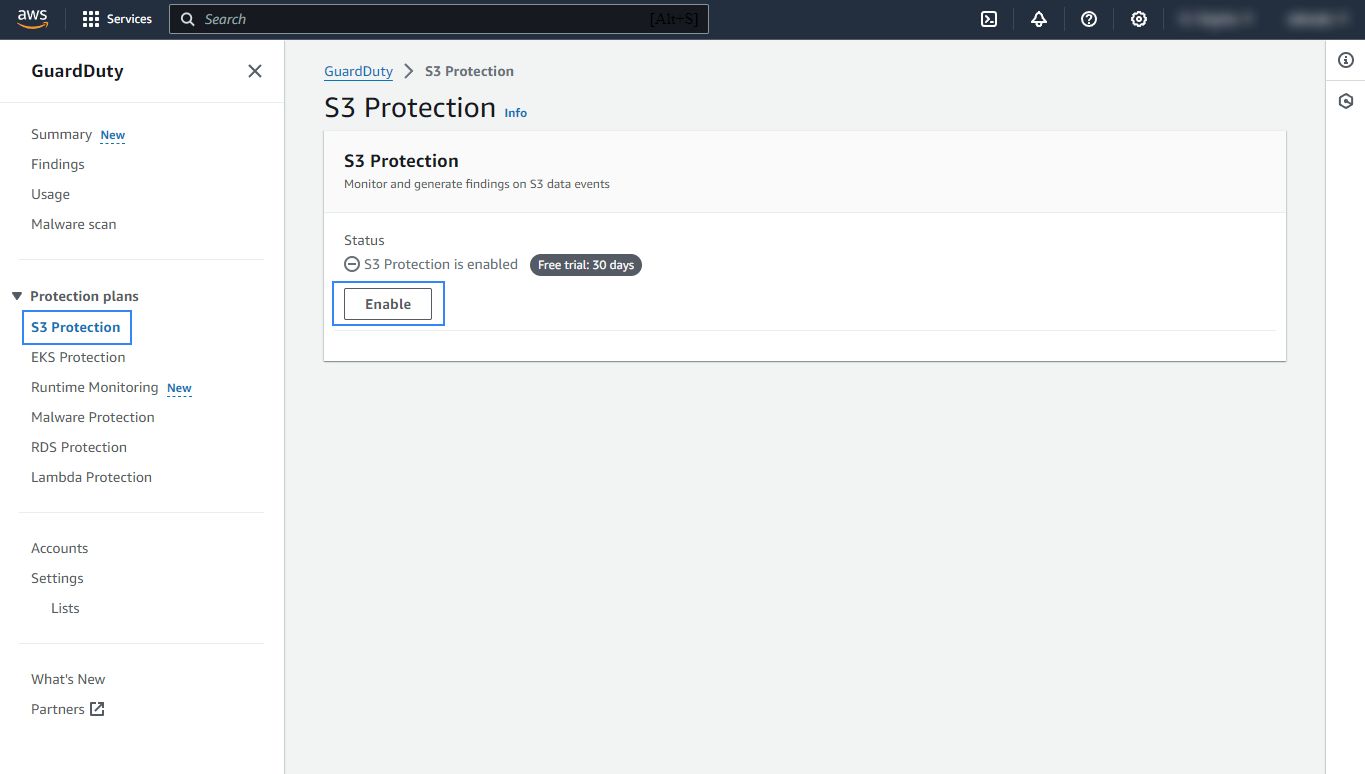
S3 Protection enables Amazon GuardDuty to monitor object-level API operations to identify potential security risks for data within your S3 buckets. In the navigation pane, under Protection plans, click S3 Protection and enable S3 protection.
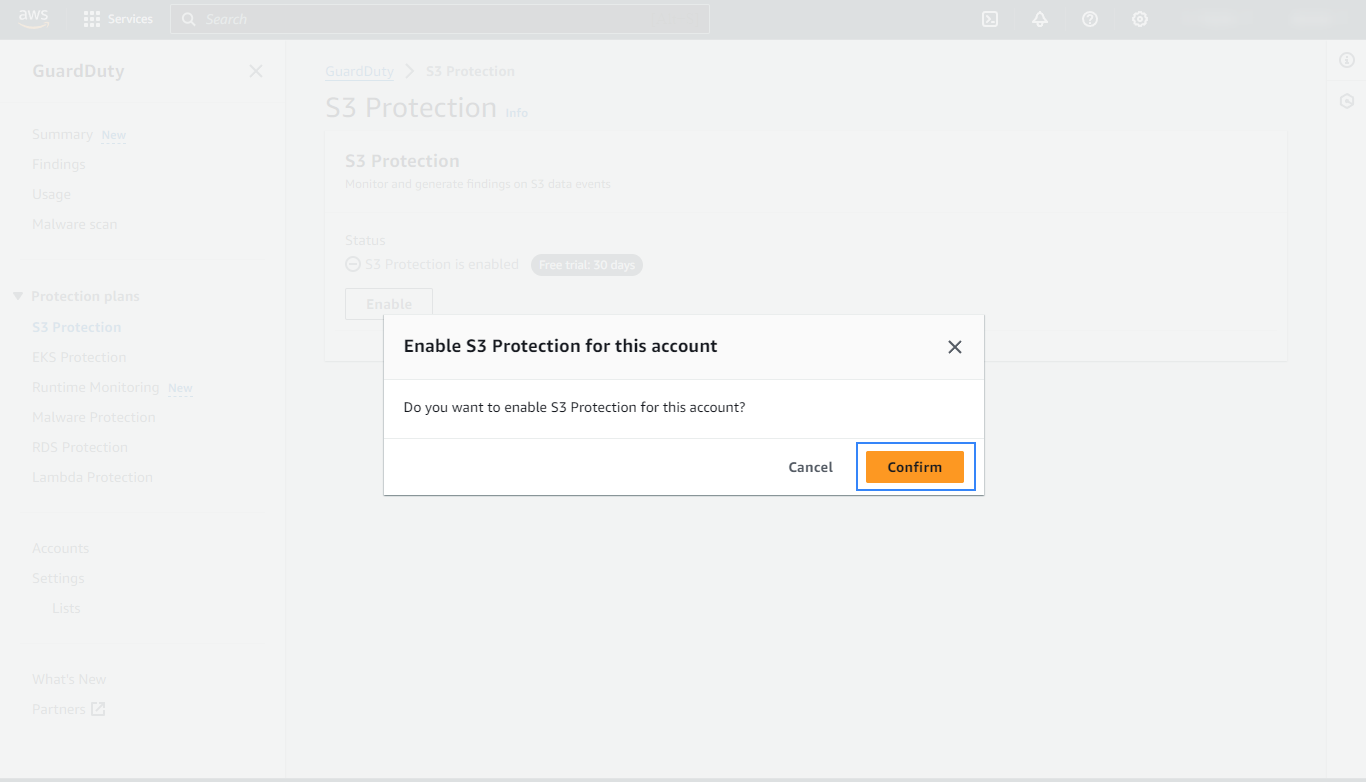
Confirm your selection.
In the navigation pane, go to Settings, scroll to Findings export options, and click Configure now to configure GuardDuty to export findings to an S3 bucket.
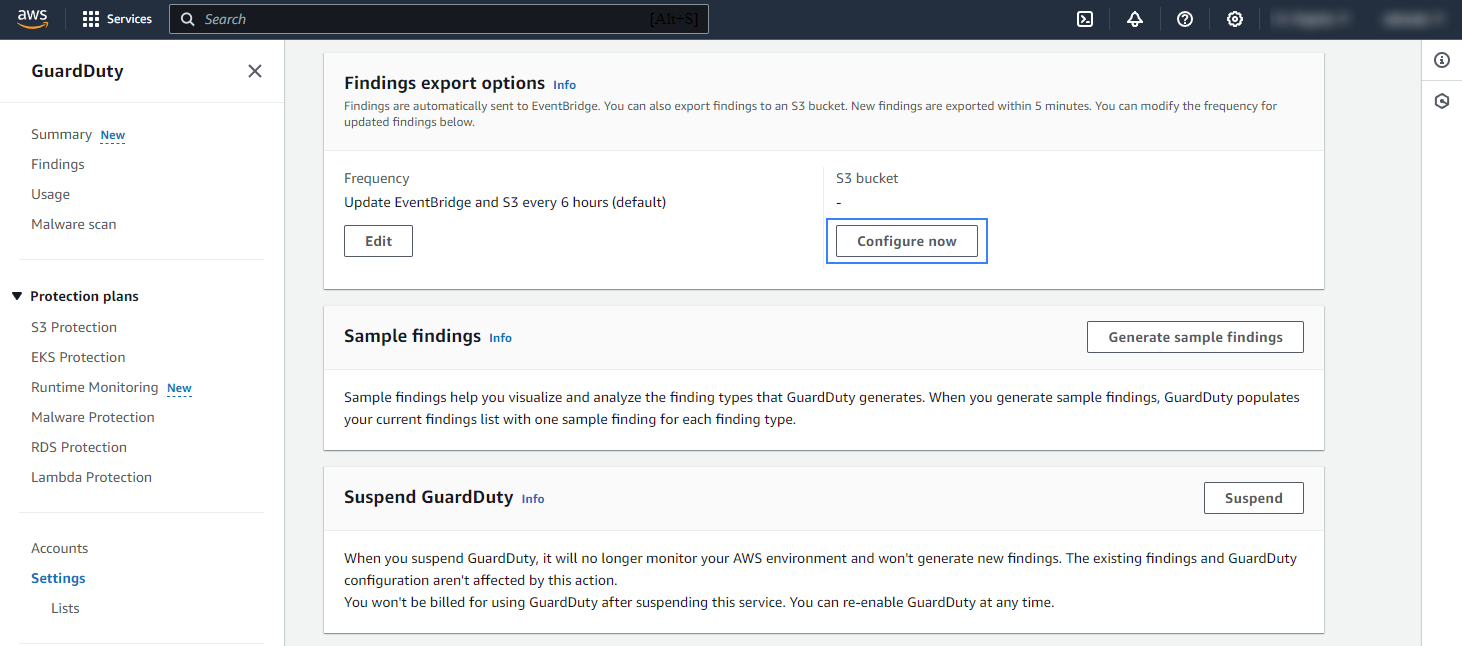
See the configuring an S3 bucket and creating symmetric encryption KMS keys guides on how to create an S3 bucket and KMS key. Copy and paste the appropriate values into the S3 bucket ARN and KMS key ARN fields.
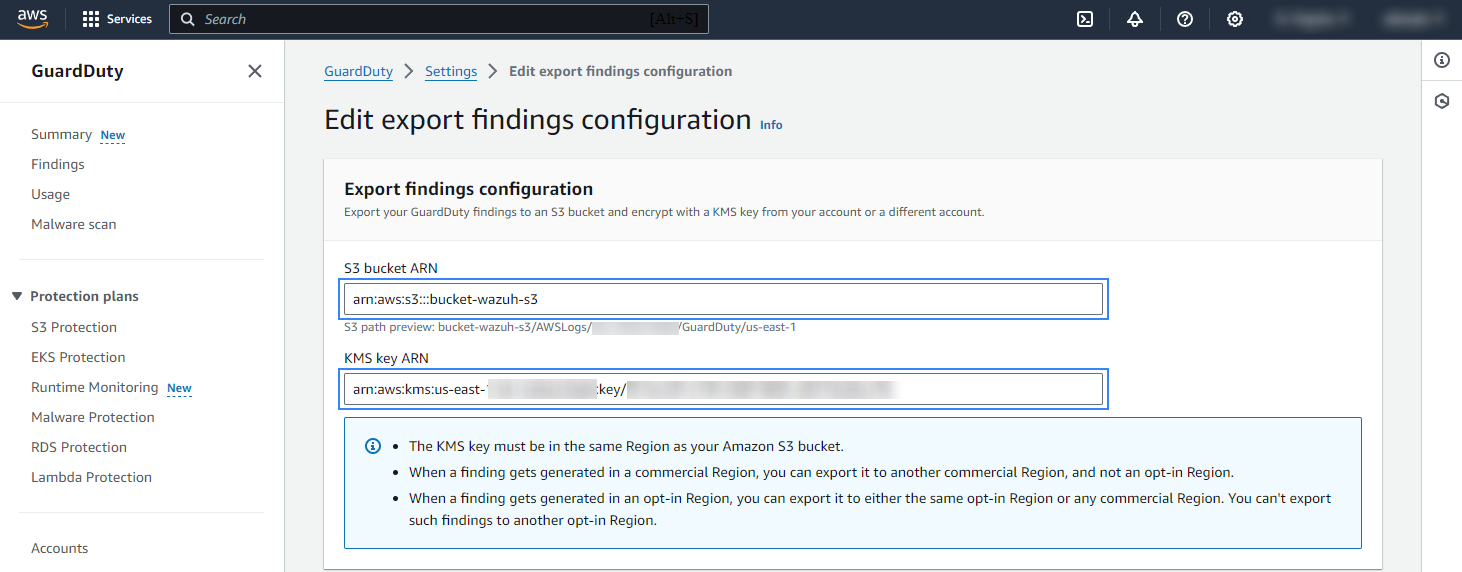
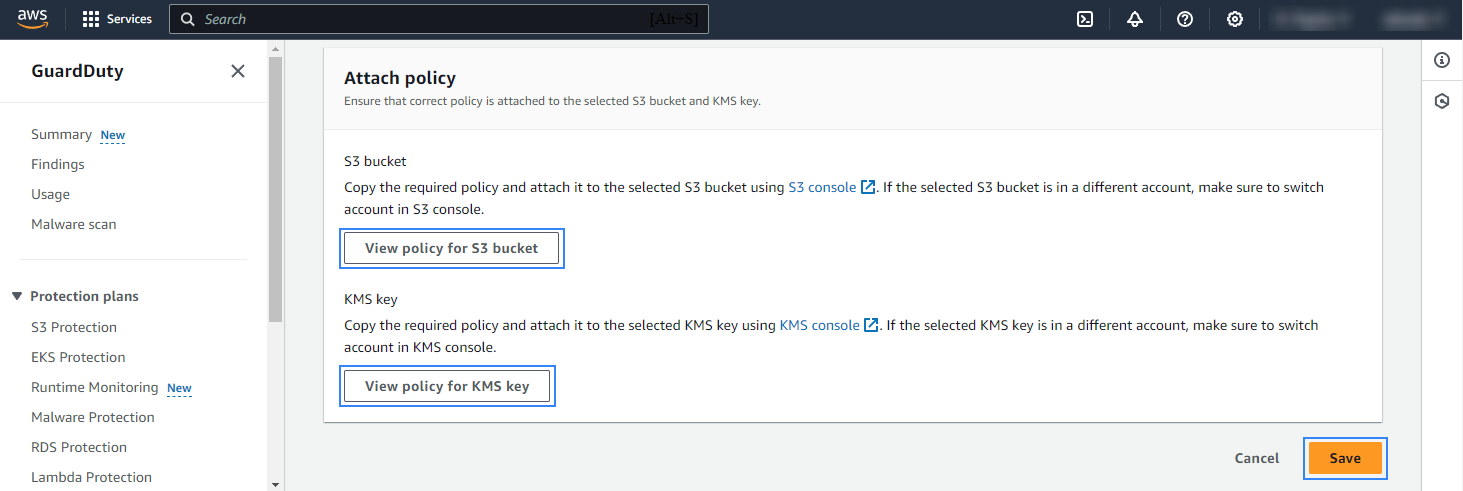
In the Attach policy section, click on View Policy for S3 bucket and View Policy for KMS key. Copy and attach the corresponding policy to the selected S3 bucket and the KMS key. Click Save to apply the configuration.
Note
For more information on how to change the S3 and KMS policies, see the adding a bucket policy by using the Amazon S3 console and changing a key policy guides.
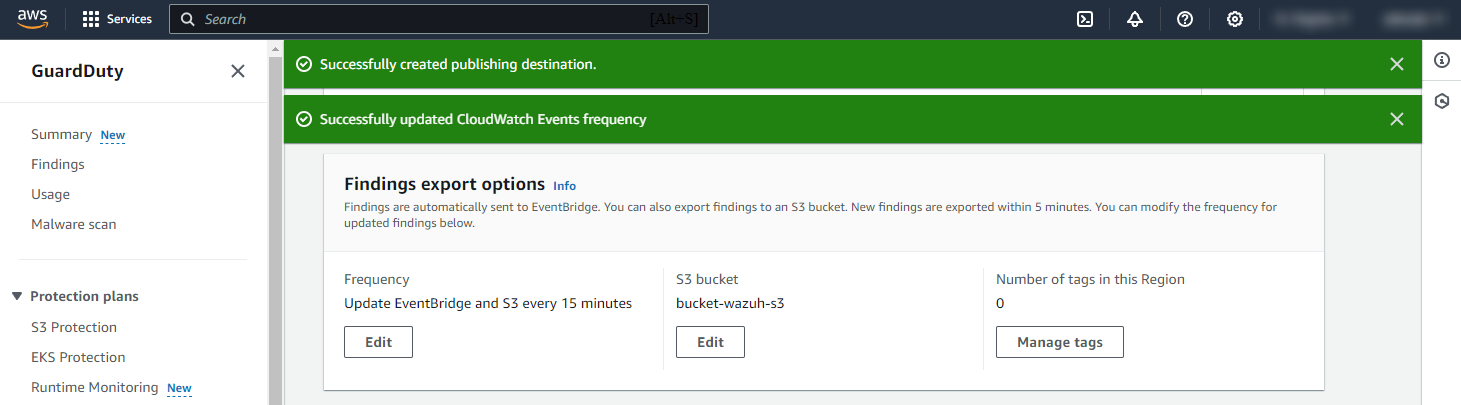
You'll have an interface similar to this, you can also set the frequency for updating the S3 bucket with the GuardDuty findings. In our case, the frequency is set to 15 minutes.
Policy configuration
Follow the creating an AWS policy guide to create a policy using the Amazon Web Services console.
Take into account that the policies below follow the principle of least privilege to ensure that only the minimum permissions are provided to the AWS IAM user.
To allow an AWS user to use the Wazuh module for AWS with read-only permissions, it must have a policy like the following attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::<WAZUH_AWS_BUCKET>/*",
"arn:aws:s3:::<WAZUH_AWS_BUCKET>"
]
}
]
}
If it is necessary to delete the log files once they have been collected, the associated policy would be as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::<WAZUH_AWS_BUCKET>/*",
"arn:aws:s3:::<WAZUH_AWS_BUCKET>"
]
}
]
}
Note
<WAZUH_AWS_BUCKET> is a placeholder. Replace it with the actual name of the bucket from which you want to retrieve logs.
After creating a policy, you can attach it directly to a user or to a group to which the user belongs. In attaching a policy to an IAM user group, you see how to attach a policy to a group. More information on how to use other methods is available in the AWS documentation.
Configure Wazuh to process Amazon GuardDuty logs
Access the Wazuh configuration in Server management > Settings using the Wazuh dashboard or by manually editing the
/var/ossec/etc/ossec.conffile in the Wazuh server or agent.
Add the following Wazuh module for AWS configuration to the file, replacing
<WAZUH_AWS_BUCKET>with the name of the S3 bucket:<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>yes</run_on_start> <skip_on_error>yes</skip_on_error> <bucket type="guardduty"> <name><WAZUH_AWS_BUCKET></name> <aws_profile>default</aws_profile> </bucket> </wodle>
Save the changes and restart Wazuh to apply the changes. The service can be manually restarted using the following command outside the Wazuh dashboard:
Wazuh manager:
# systemctl restart wazuh-manager
Wazuh agent:
# systemctl restart wazuh-agent
GuardDuty use cases
Amazon EC2 (Elastic Compute Cloud) provides scalable computing capacity in the cloud. When using this service, it is highly recommended to monitor it for intrusion attempts or other unauthorized actions performed against your cloud infrastructure.
Below are some use cases for Wazuh rules built for EC2.
Brute force attacks
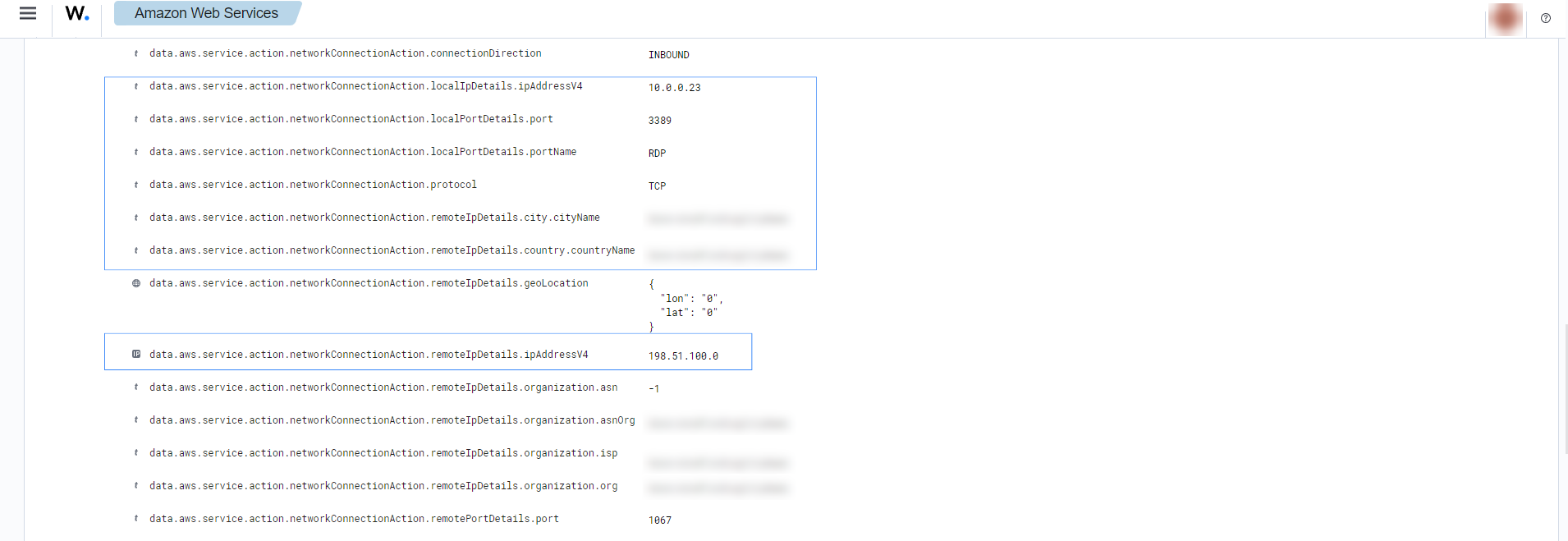
If an instance has an open port that is receiving a brute force attack, the following alerts with rule ID 80301 will be shown on the Wazuh dashboard.
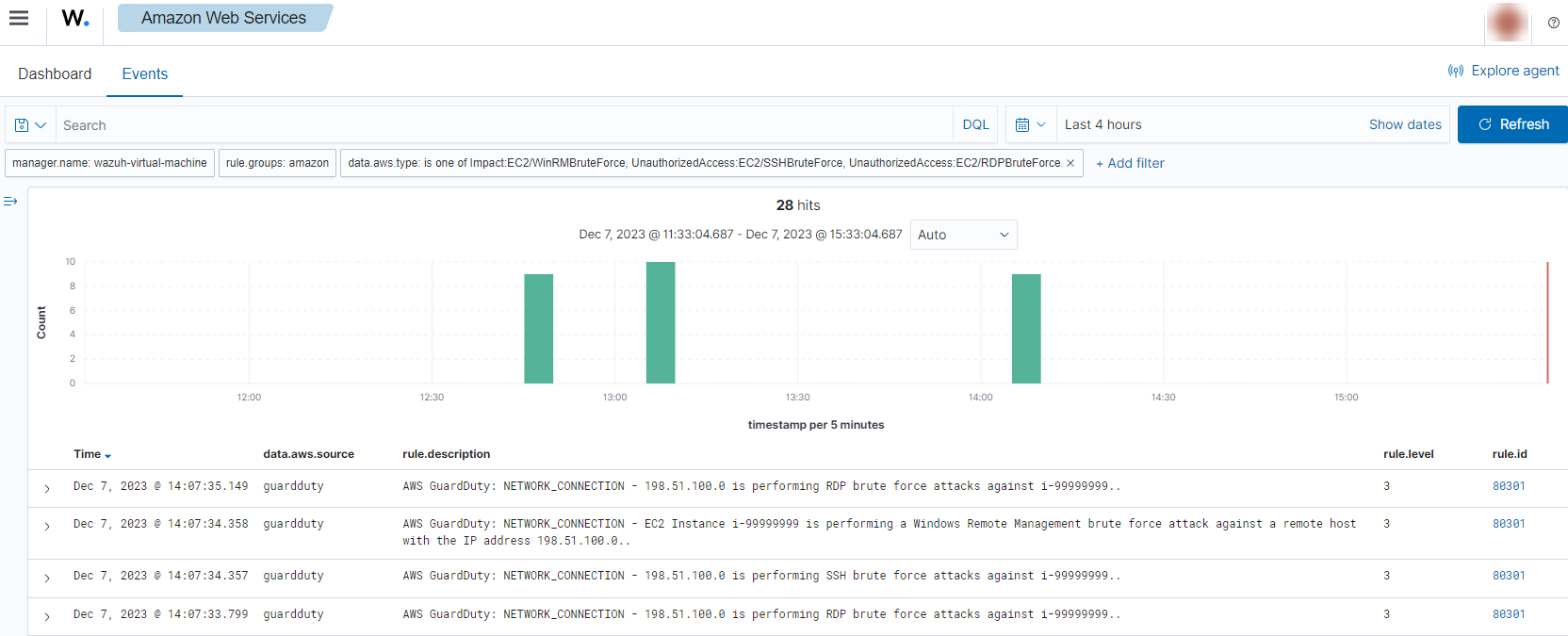
It shows information about the attacked host, the attacker, and which port is being attacked.
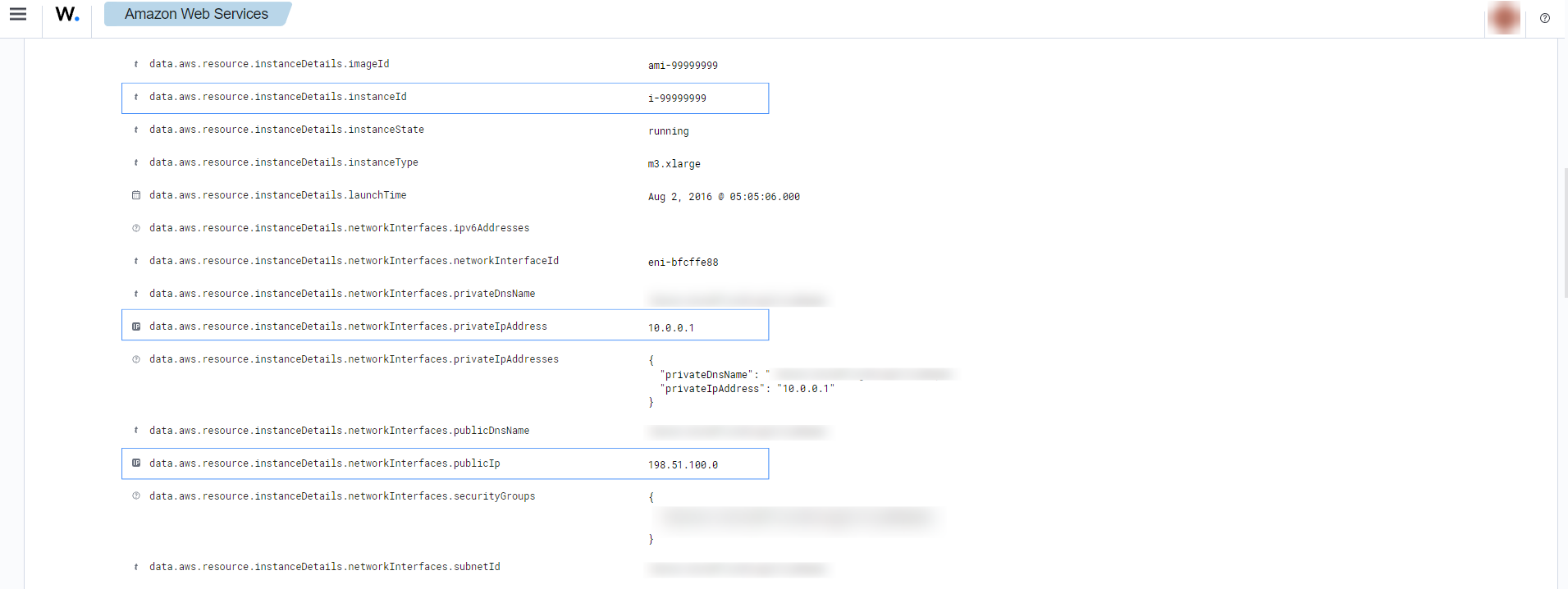
EC2 API Calls made from unusual network
If an API call is made from an unusual network, the following alerts with rule ID 80301, 80302, and 80303 will be shown on the Wazuh dashboard.
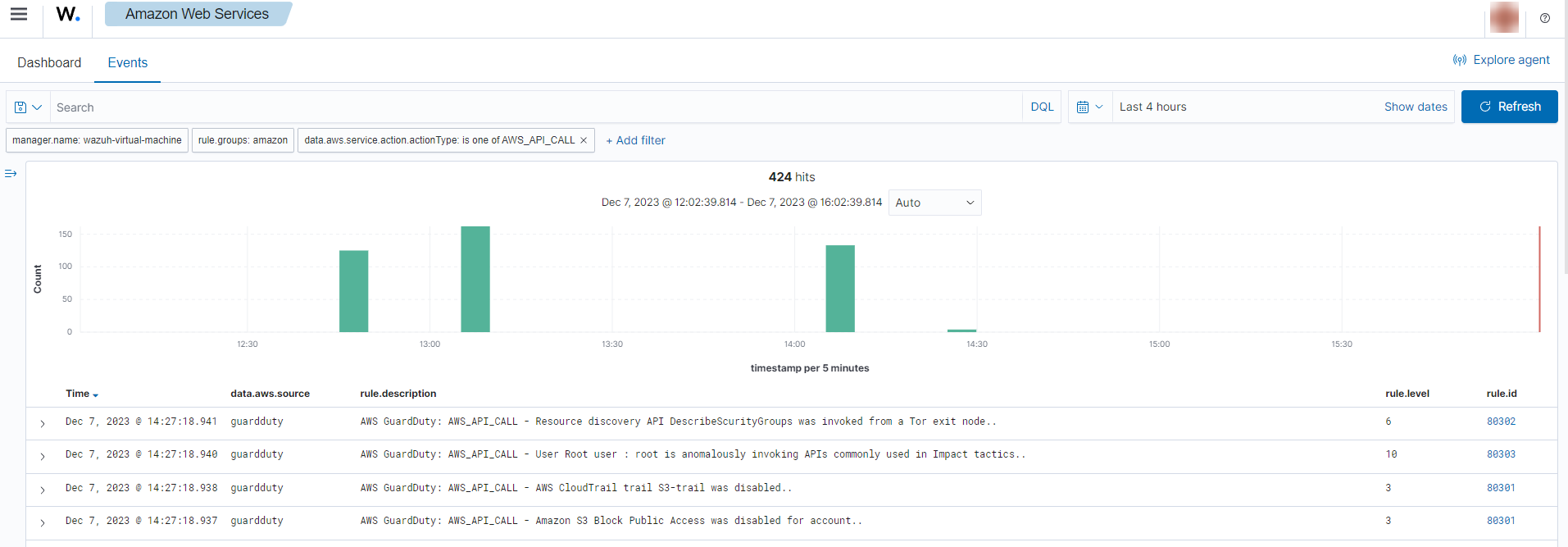
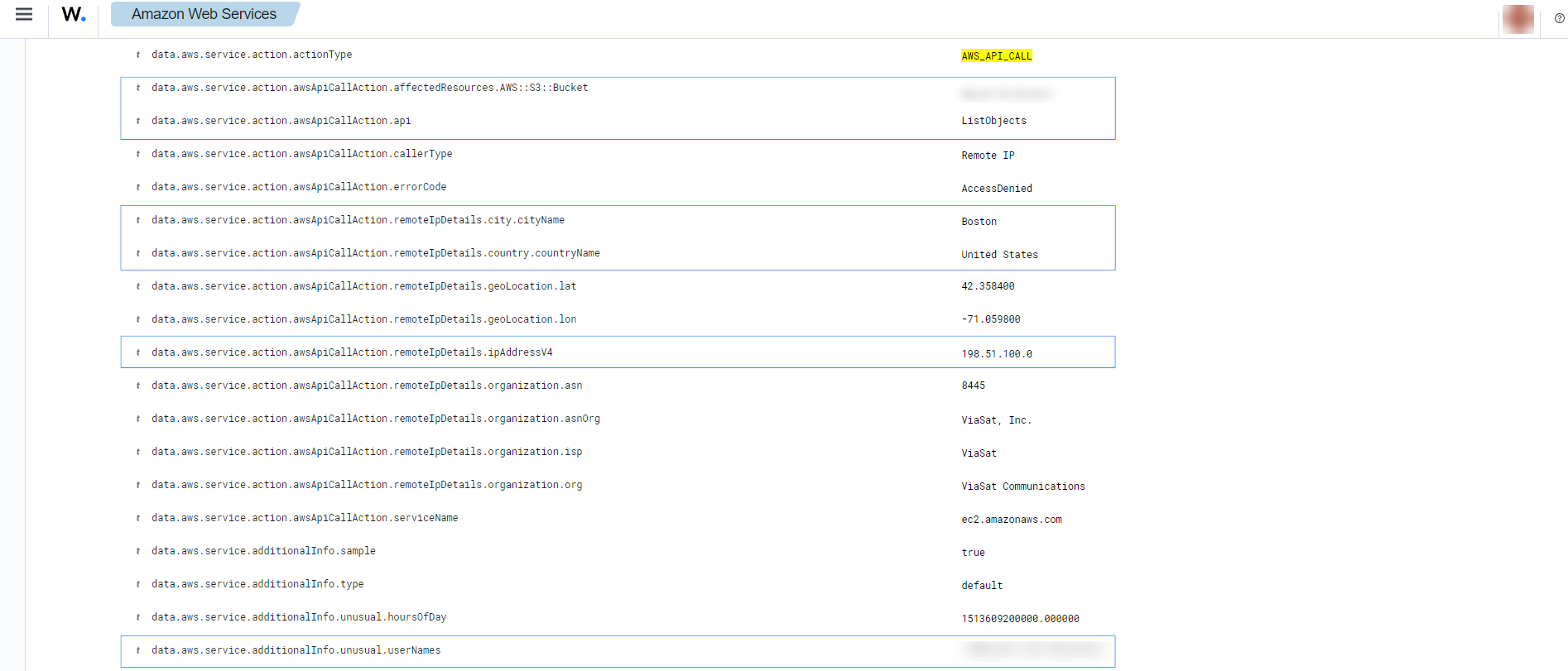
It shows the location of the unusual network, the user who made the API calls, and which API calls it made.
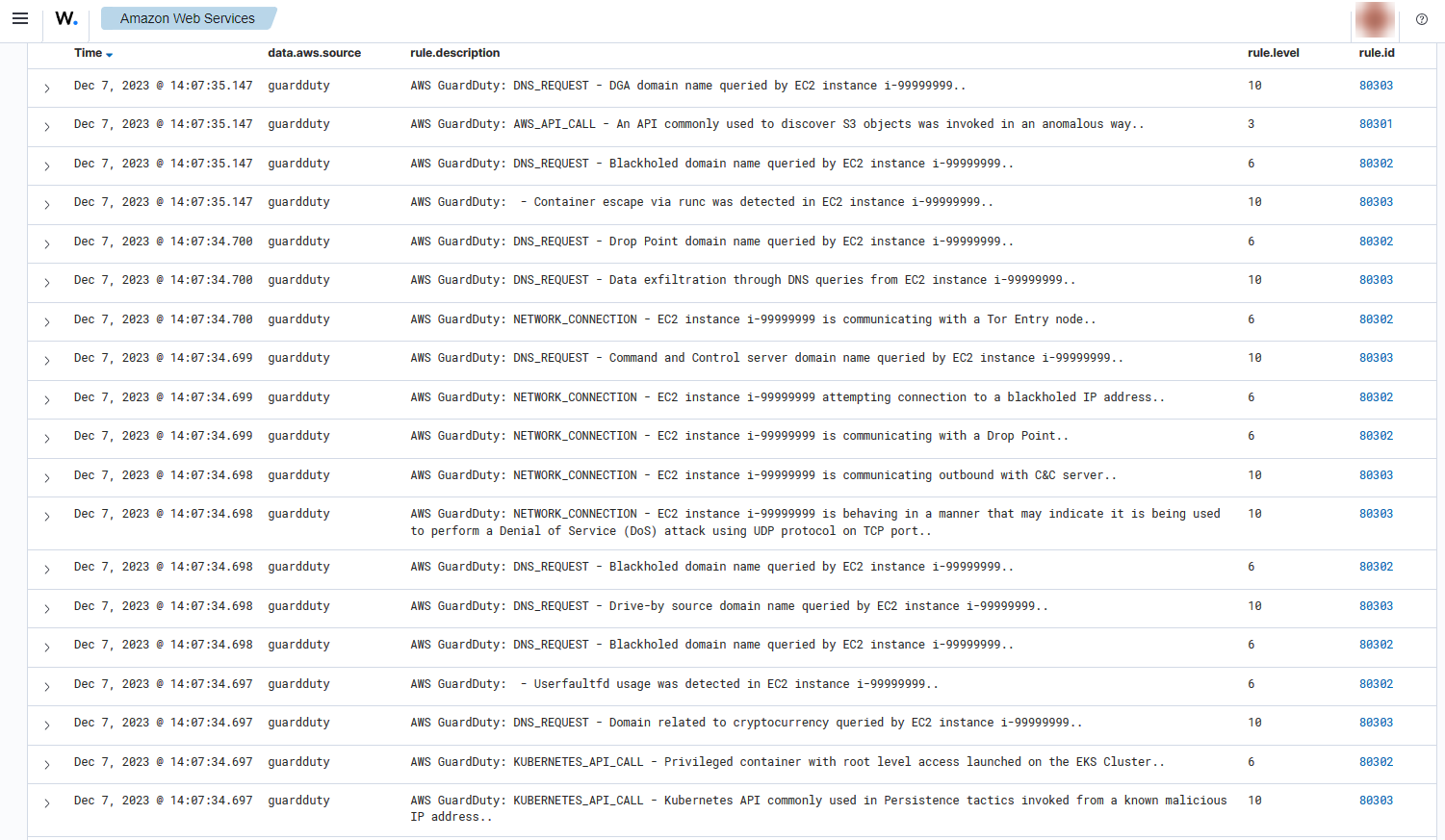
Compromised EC2 instance
If there is any indicator of a compromised EC2 instance, an alert with rule ID 80303 will be shown on the Wazuh dashboard explaining what's happening. Some examples of alerts are shown below.
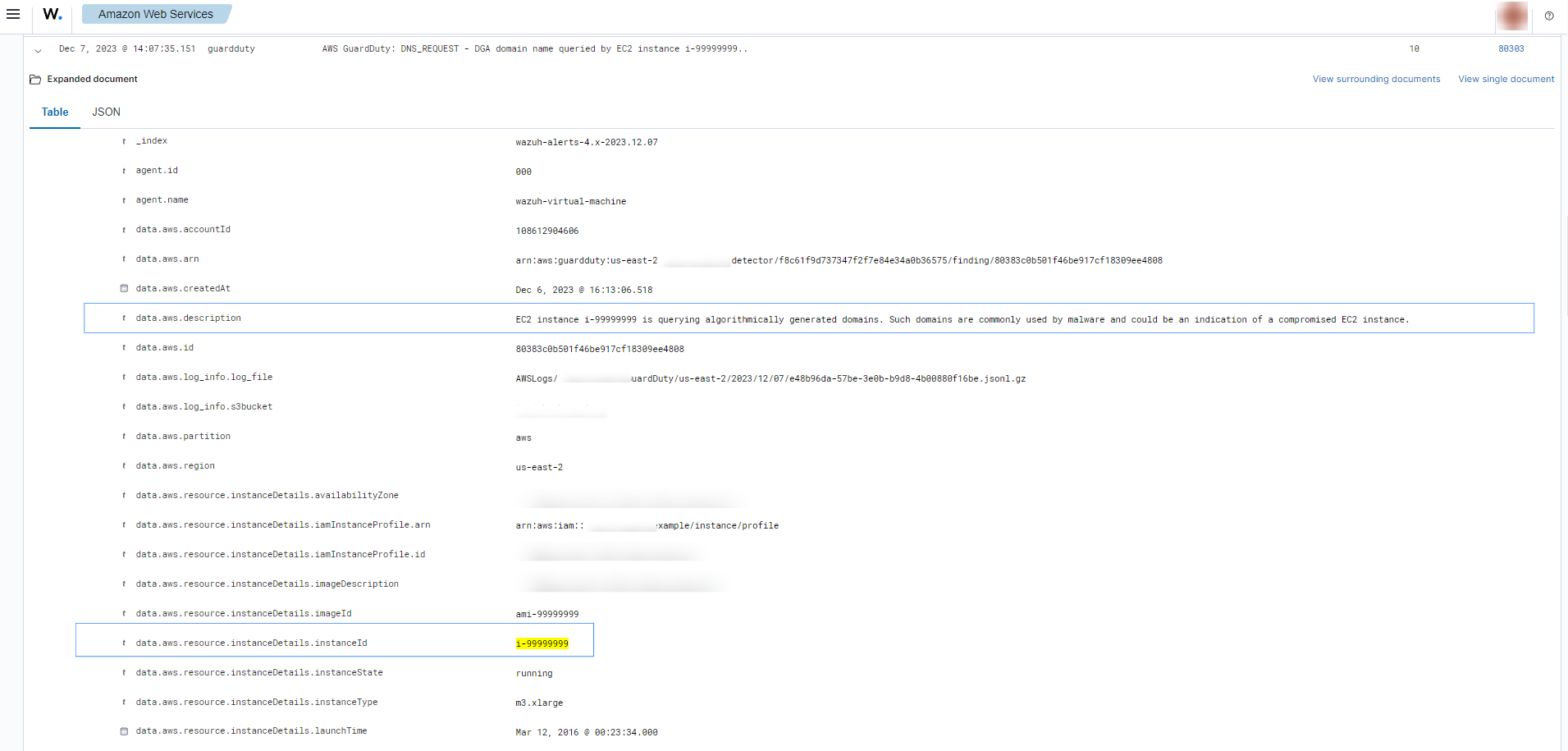
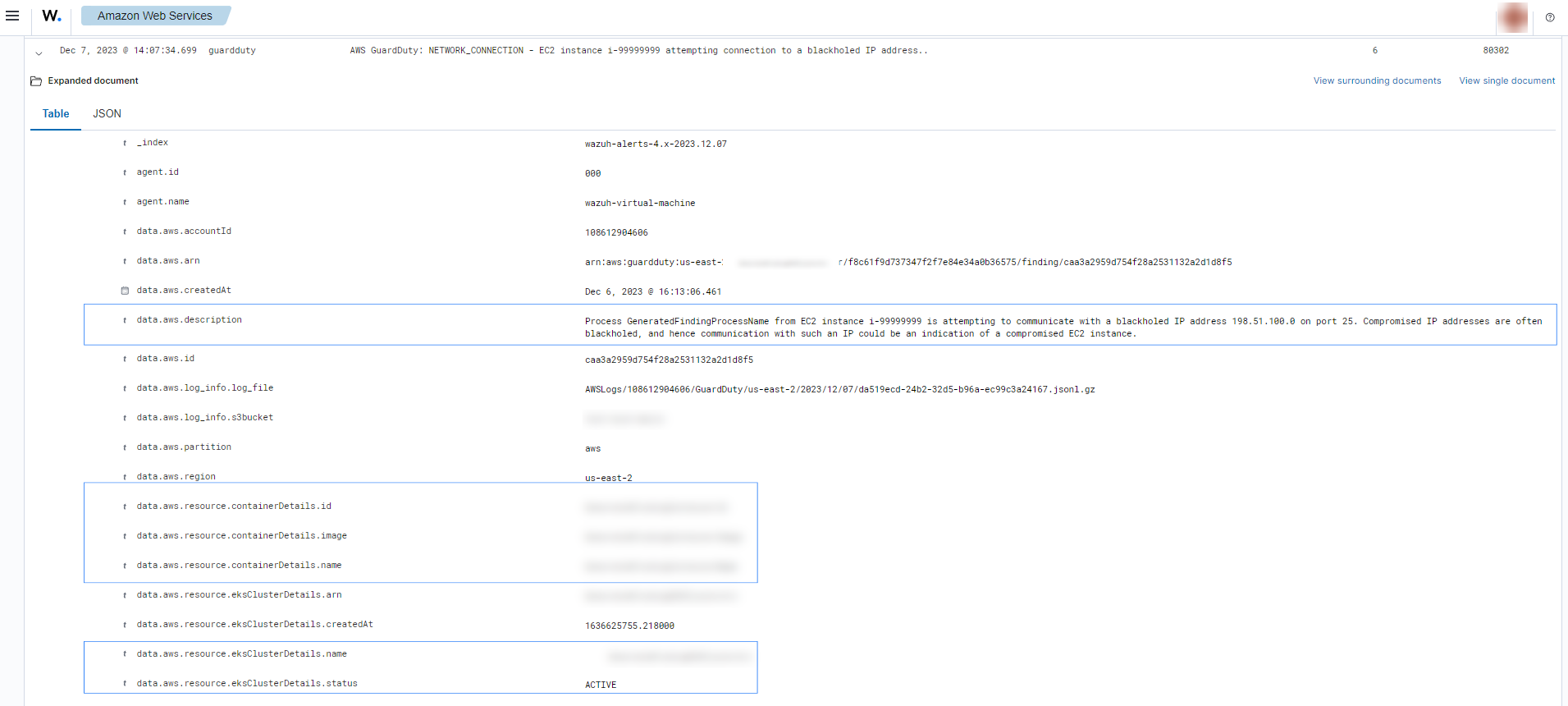
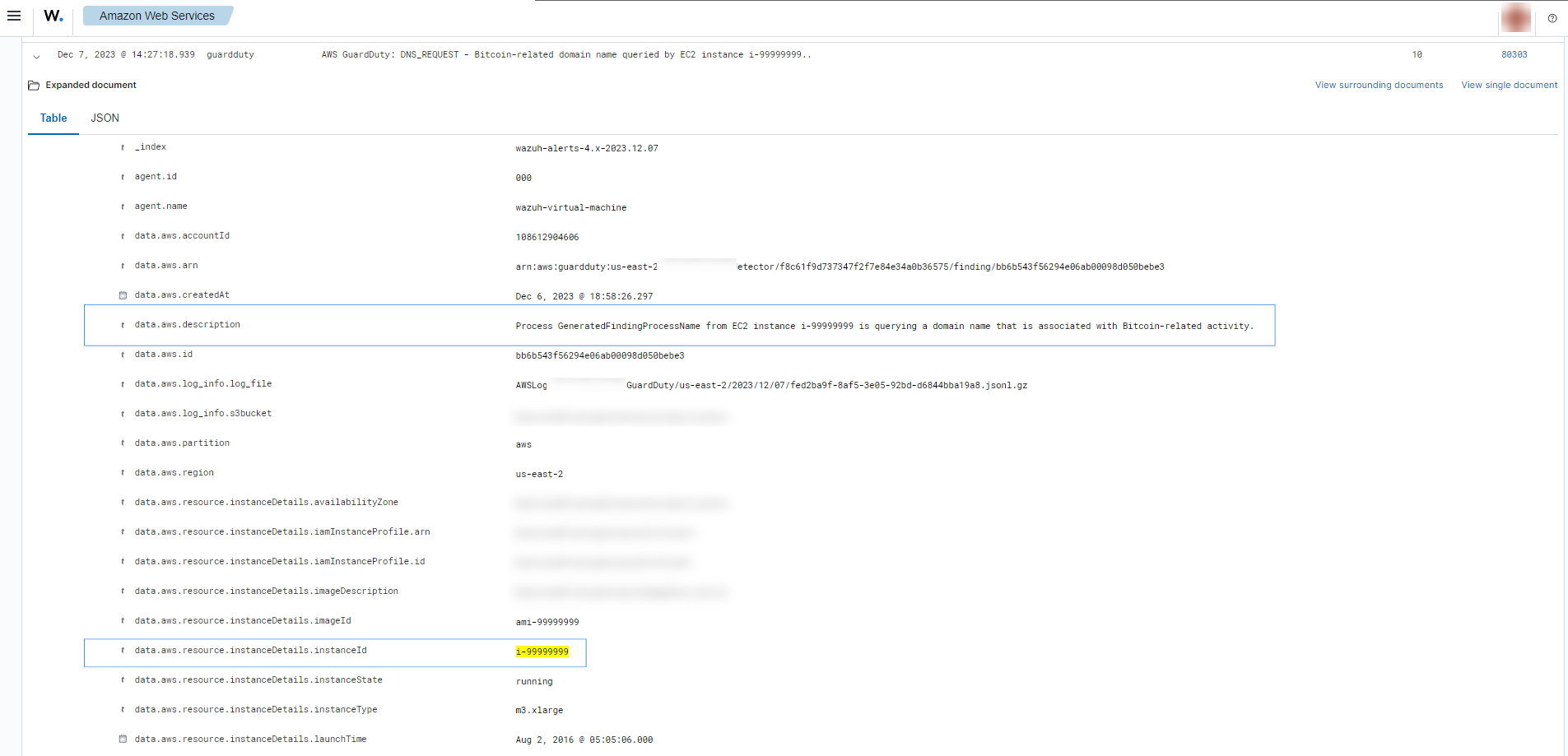
To sum up, the following screenshot shows some alerts generated for a compromised EC2 instance.