AWS CloudTrail
AWS CloudTrail is a service that enables auditing of your AWS account. With CloudTrail, you can log, monitor, and retain account activity related to actions across your AWS infrastructure. This service provides the event history of your AWS account activity, such as actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services.
AWS configuration
The following sections cover how to configure the Amazon CloudTrail service to integrate with Wazuh.
Amazon CloudTrail configuration
Create a new S3 bucket. If you want to use an already existing one, skip this step.
On your AWS console, search for “cloudtrail” in the search bar at the top of the page or go to Management & Governance > CloudTrail.
Click Create trail to create a new trail.
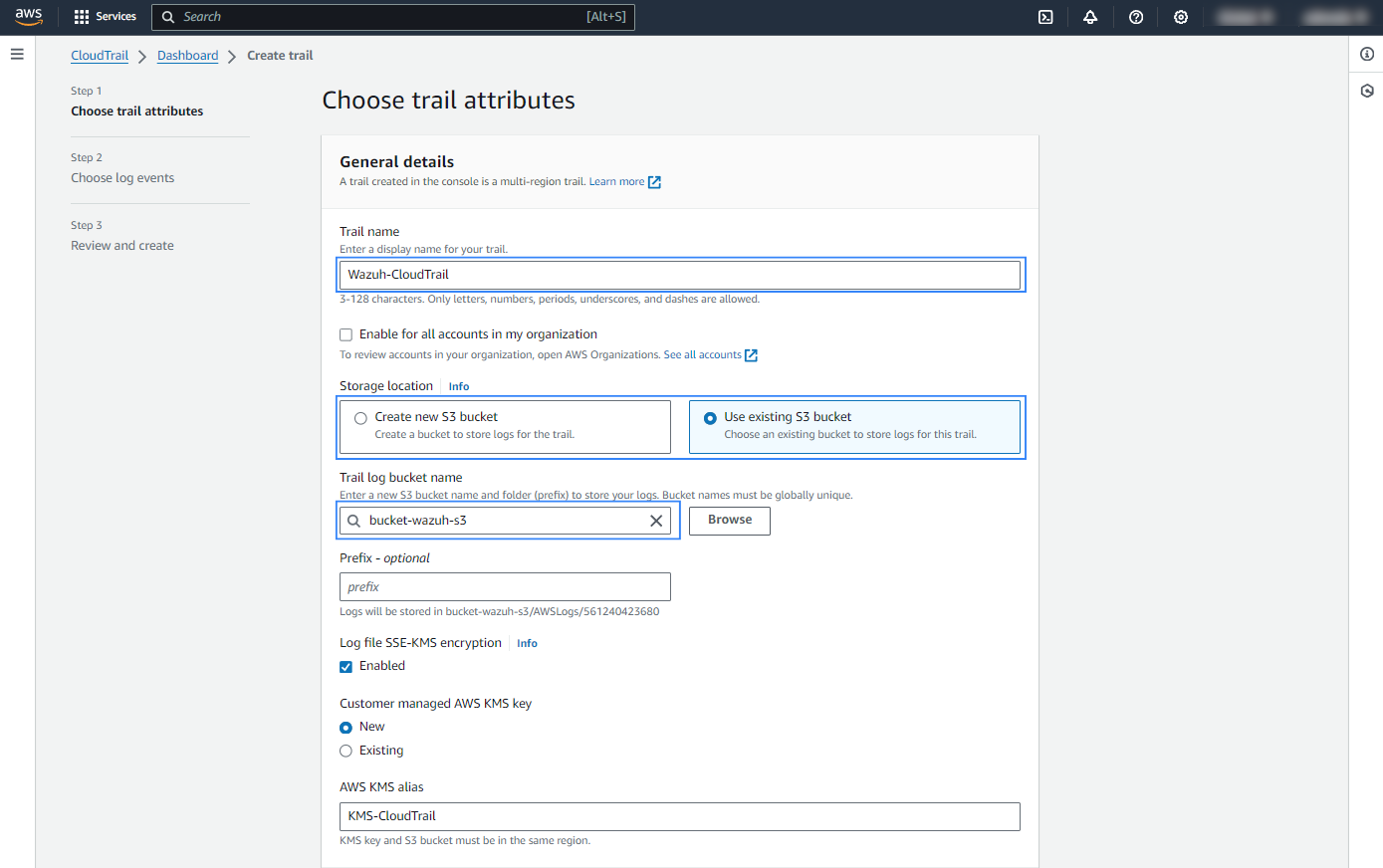
Assign a Trail Name and choose the S3 bucket that will store the CloudTrail logs (remember the name you provide here, you’ll need to reference it the Wazuh module for AWS configuration). If Log file SSE-KMS encryption is enabled, assign a name for a new AWS KMS alias or choose an existing one:
Note
The standard file system AWS CloudTrail will create has this structure:
<WAZUH_AWS_BUCKET>/<PREFIX>/AWSLogs/<ACCOUNT_ID>/CloudTrail/<REGION>/<YEAR>/<MONTH>/<DAY>
The structure may change depending on the different configurations of the services, or changing of the
<WAZUH_AWS_BUCKET>and<PREFIX>values by the user.Choose log events to be recorded and click Next.
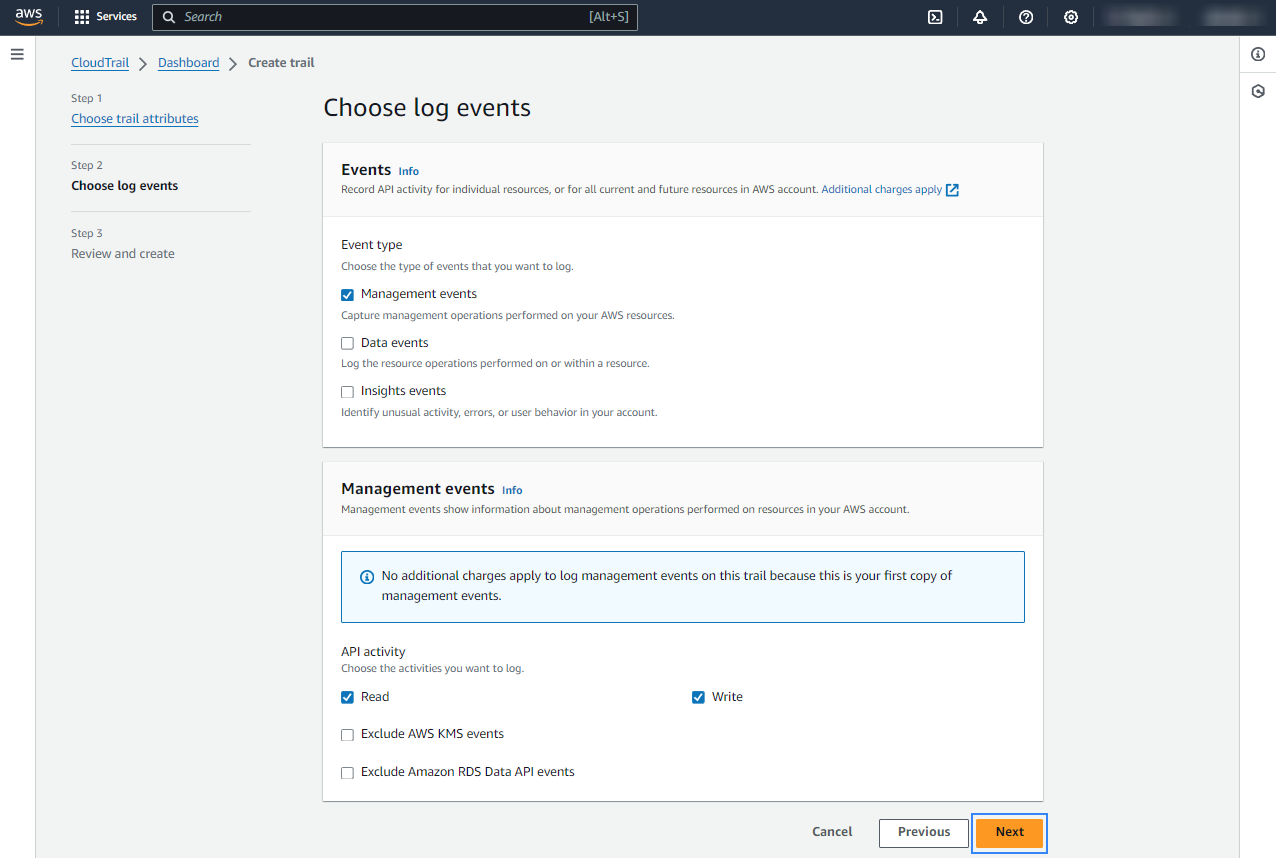
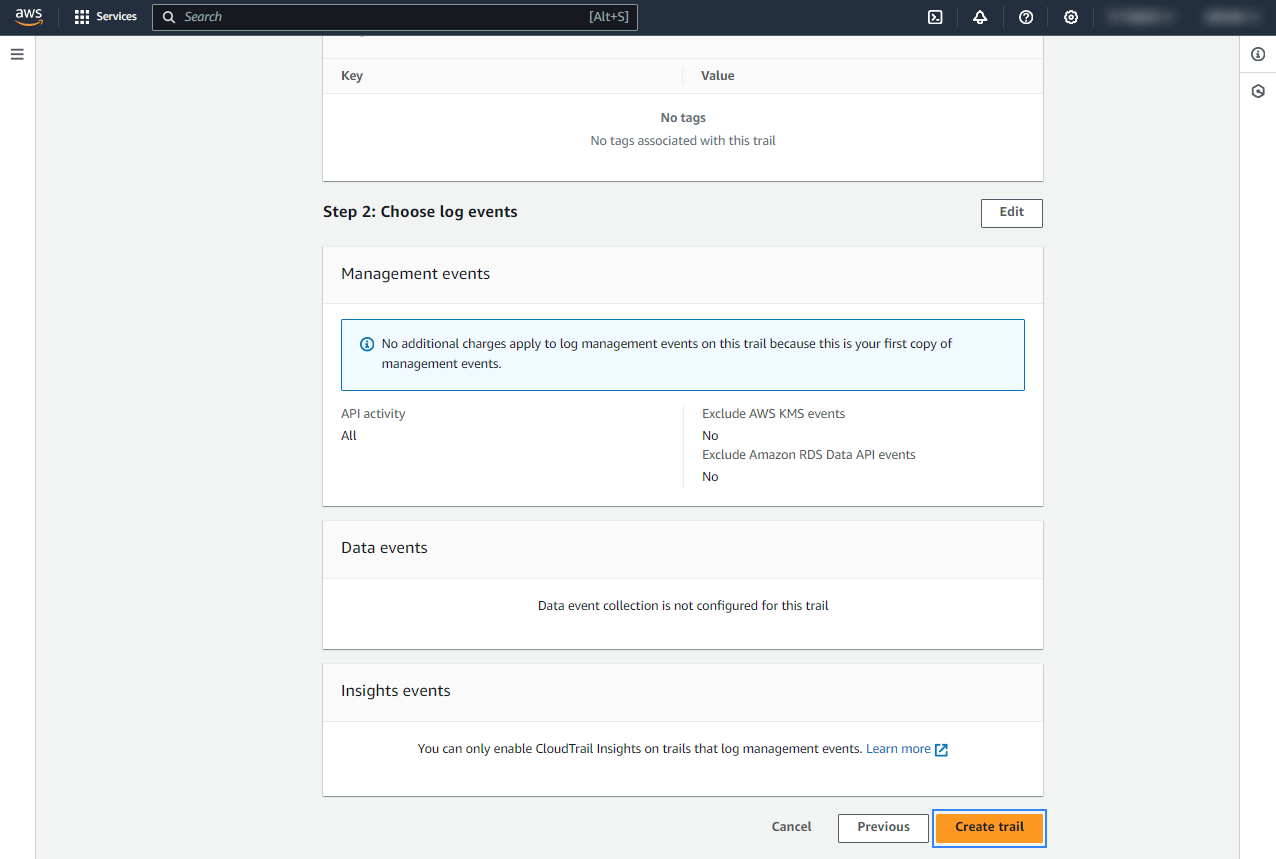
Review the configuration and click Create trail.
Policy configuration
Follow the creating an AWS policy guide to create a policy using the Amazon Web Services console.
Take into account that the policies below follow the principle of least privilege to ensure that only the minimum permissions are provided to the AWS IAM user.
To allow an AWS user to use the Wazuh module for AWS with read-only permissions, it must have a policy like the following attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::<WAZUH_AWS_BUCKET>/*",
"arn:aws:s3:::<WAZUH_AWS_BUCKET>"
]
}
]
}
If it is necessary to delete the log files once they have been collected, the associated policy would be as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::<WAZUH_AWS_BUCKET>/*",
"arn:aws:s3:::<WAZUH_AWS_BUCKET>"
]
}
]
}
Note
<WAZUH_AWS_BUCKET> is a placeholder. Replace it with the actual name of the bucket from which you want to retrieve logs.
After creating a policy, you can attach it directly to a user or to a group to which the user belongs. In attaching a policy to an IAM user group, you see how to attach a policy to a group. More information on how to use other methods is available in the AWS documentation.
Configure Wazuh to process AWS CloudTrail logs
Access the Wazuh configuration in Server management > Settings using the Wazuh dashboard or by manually editing the
/var/ossec/etc/ossec.conffile in the Wazuh server or agent.
Add the following Wazuh module for AWS configuration to the file, replacing
<WAZUH_AWS_BUCKET>with the name of the S3 bucket:<wodle name="aws-s3"> <disabled>no</disabled> <interval>10m</interval> <run_on_start>yes</run_on_start> <skip_on_error>yes</skip_on_error> <bucket type="cloudtrail"> <name><WAZUH_AWS_BUCKET></name> <aws_profile>default</aws_profile> </bucket> </wodle>
Note
In this example, the
aws_profileauthentication parameter was used. Check the credentials section to learn more about the different authentication options and how to use them.Save the changes and restart Wazuh to apply the changes. The service can be manually restarted using the following command outside the Wazuh dashboard:
Wazuh manager:
# systemctl restart wazuh-manager
Wazuh agent:
# systemctl restart wazuh-agent
CloudTrail use cases
Below you find examples of some of how Wazuh integrates with CloudTrail to monitor EC2 and IAM events. This enhances the security monitoring capabilities of AWS environments by providing near real-time detection of security incidents and compliance violations.
EC2
Amazon EC2 (Elastic Compute Cloud) provides scalable computing capacity in the cloud. When using this service, it is highly recommended to monitor it for intrusion attempts or other unauthorized actions performed against your cloud infrastructure.
Below are some use cases for EC2 monitoring.
Run a new instance in EC2
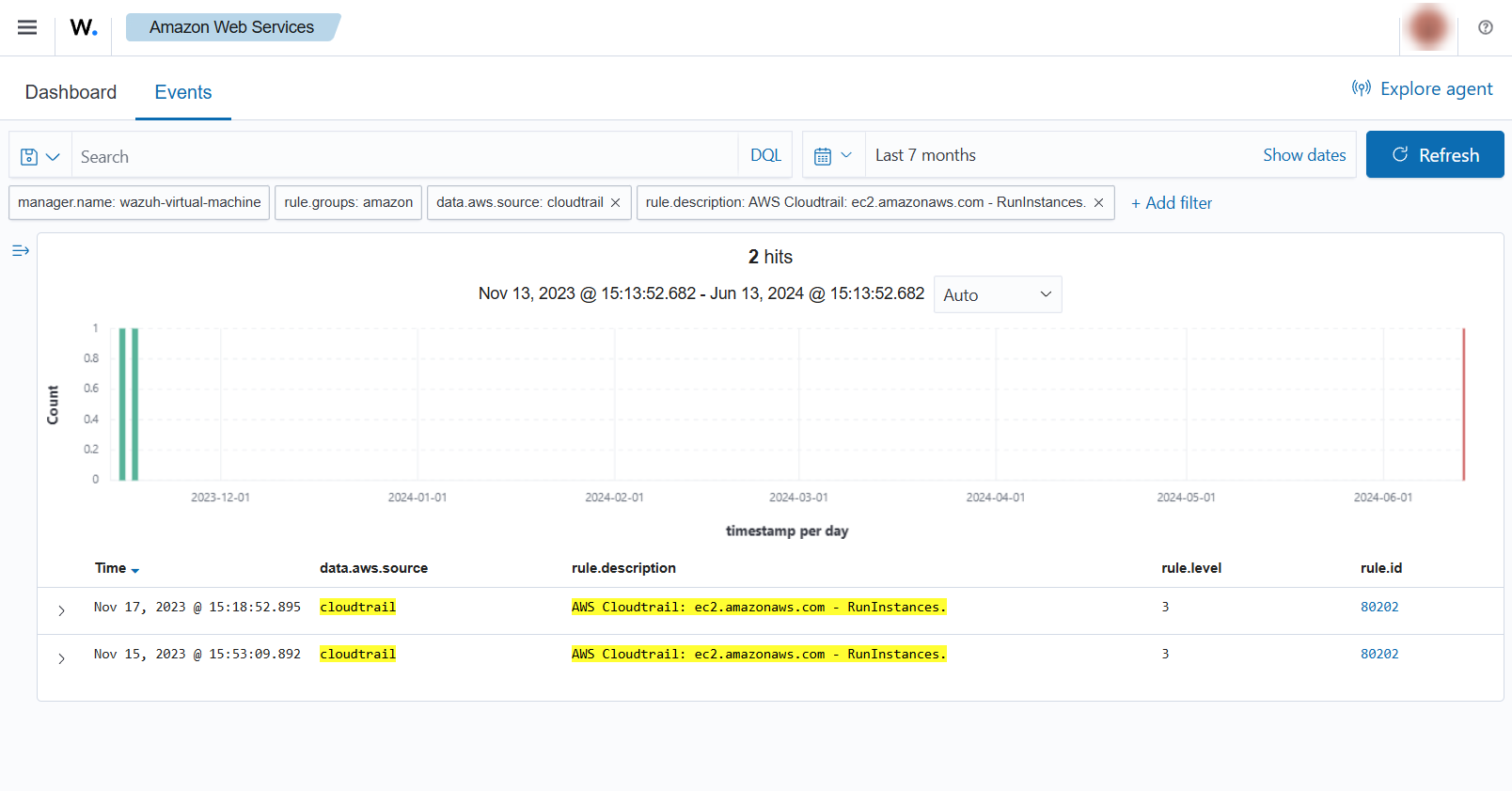
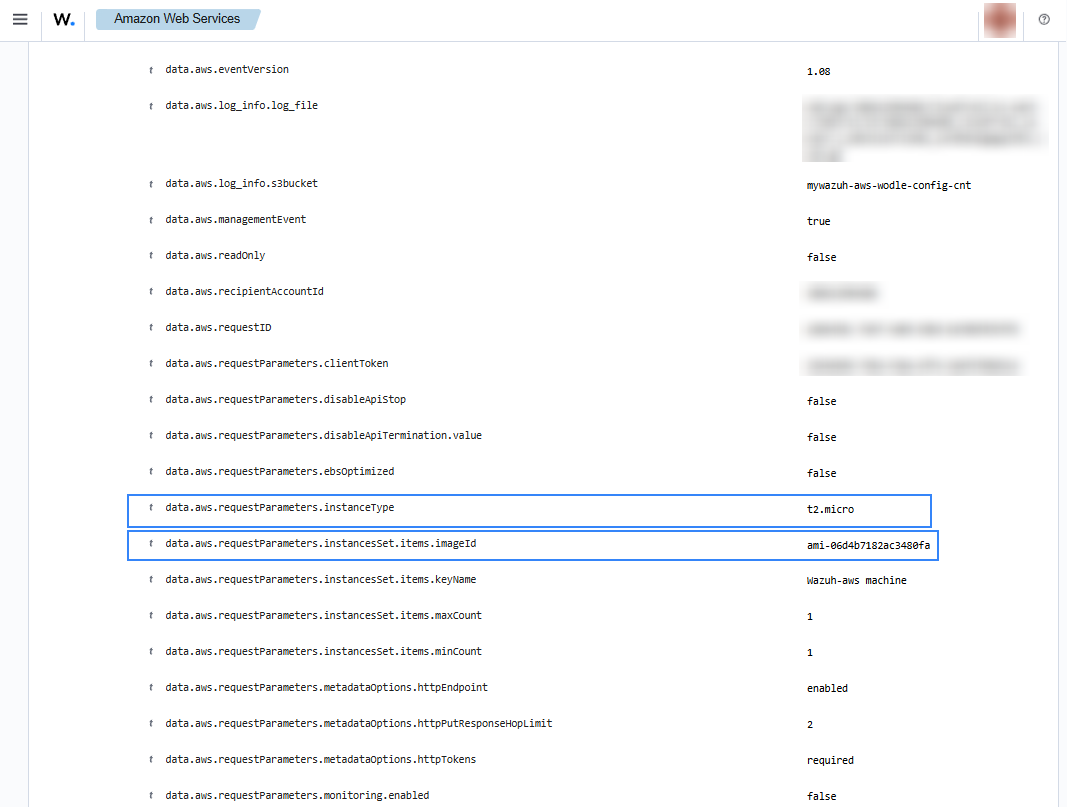
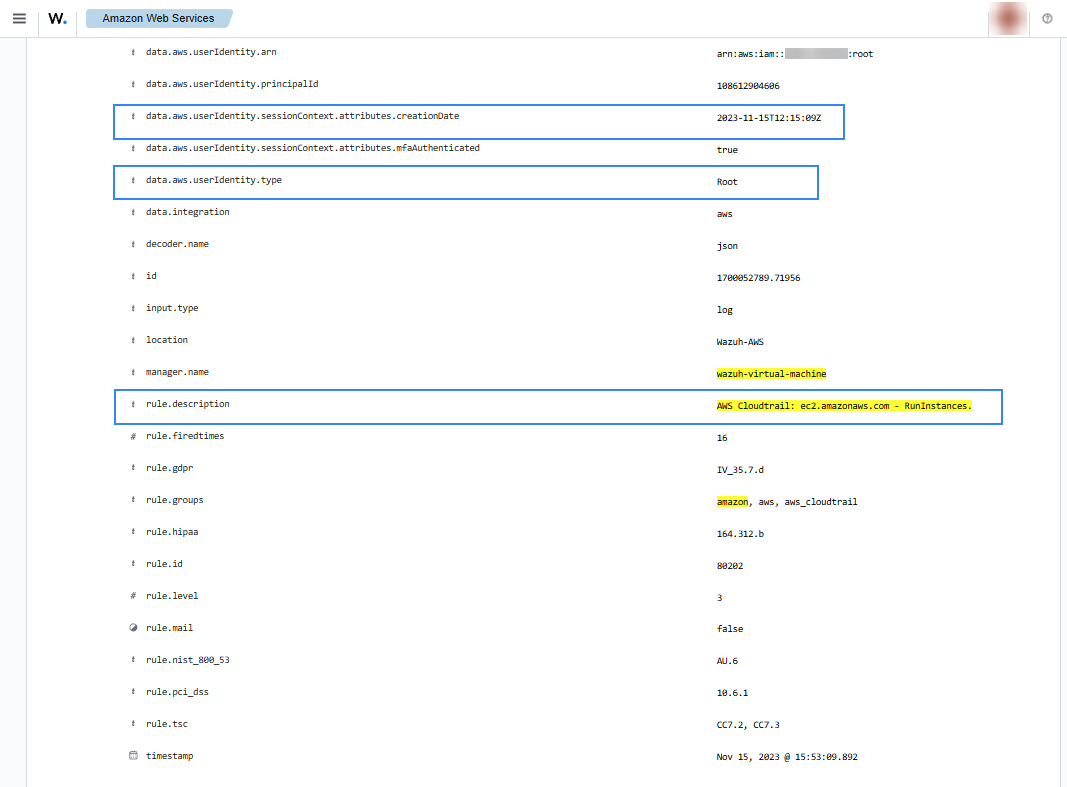
When a user creates a new instance in EC2, a CloudTrail event is generated. As previously mentioned, the log message is collected by the Wazuh agent, and forwarded to the Wazuh manager for analysis. The following alerts with rule ID 80202 will be shown on the Wazuh dashboard, it shows data such as instance type, the user who created it, or the creation date.
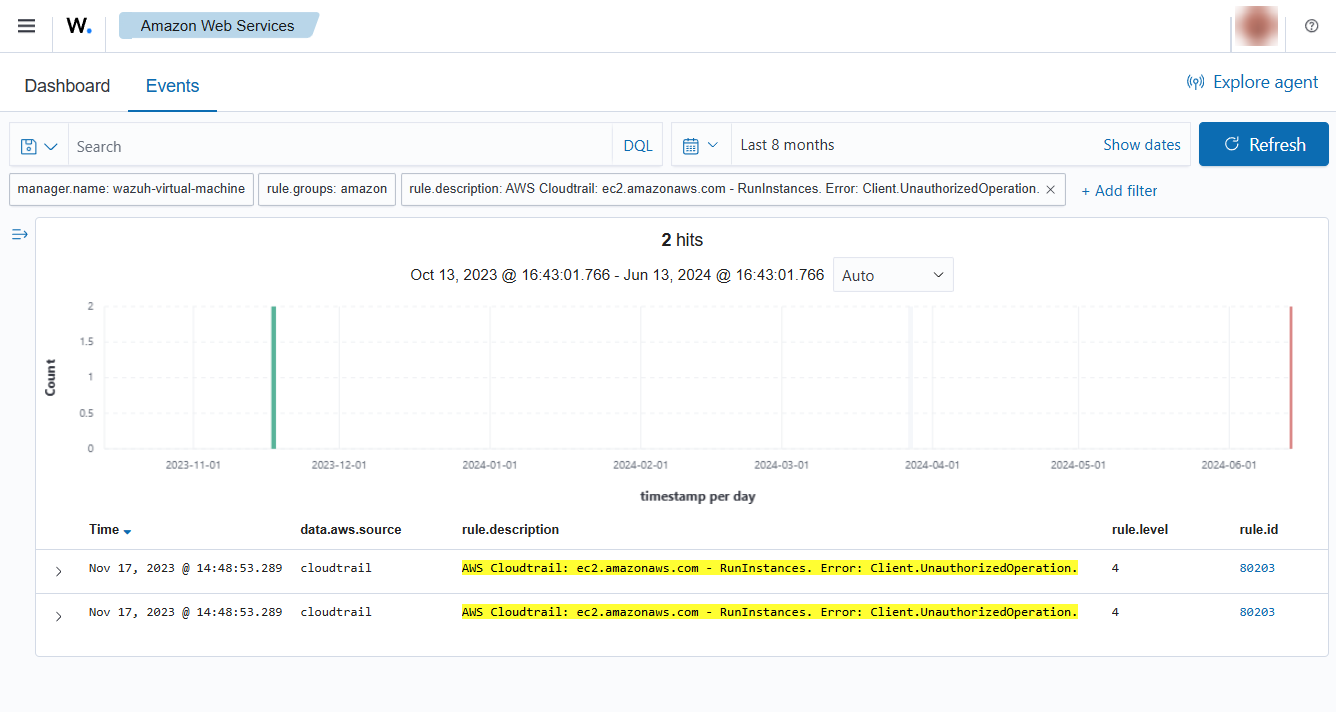
When a user tries to run an instance without relevant permissions, then the following alert with rule ID 80203 will be shown on the Wazuh dashboard.
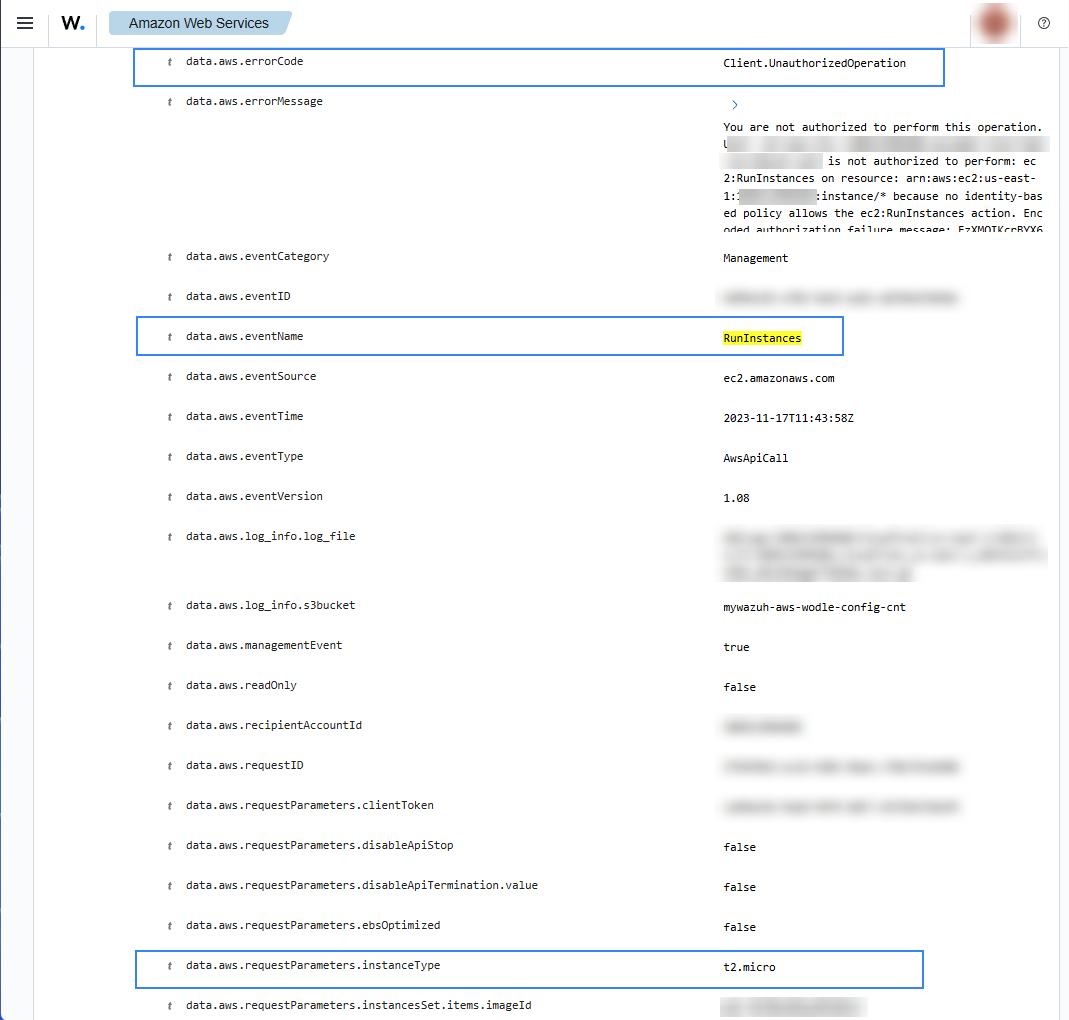
Start instances in EC2
When an EC2 instance is started, the following alerts with rule ID 80202 will be shown on the Wazuh dashboard. It shows information such as the instance ID and the user who started it.
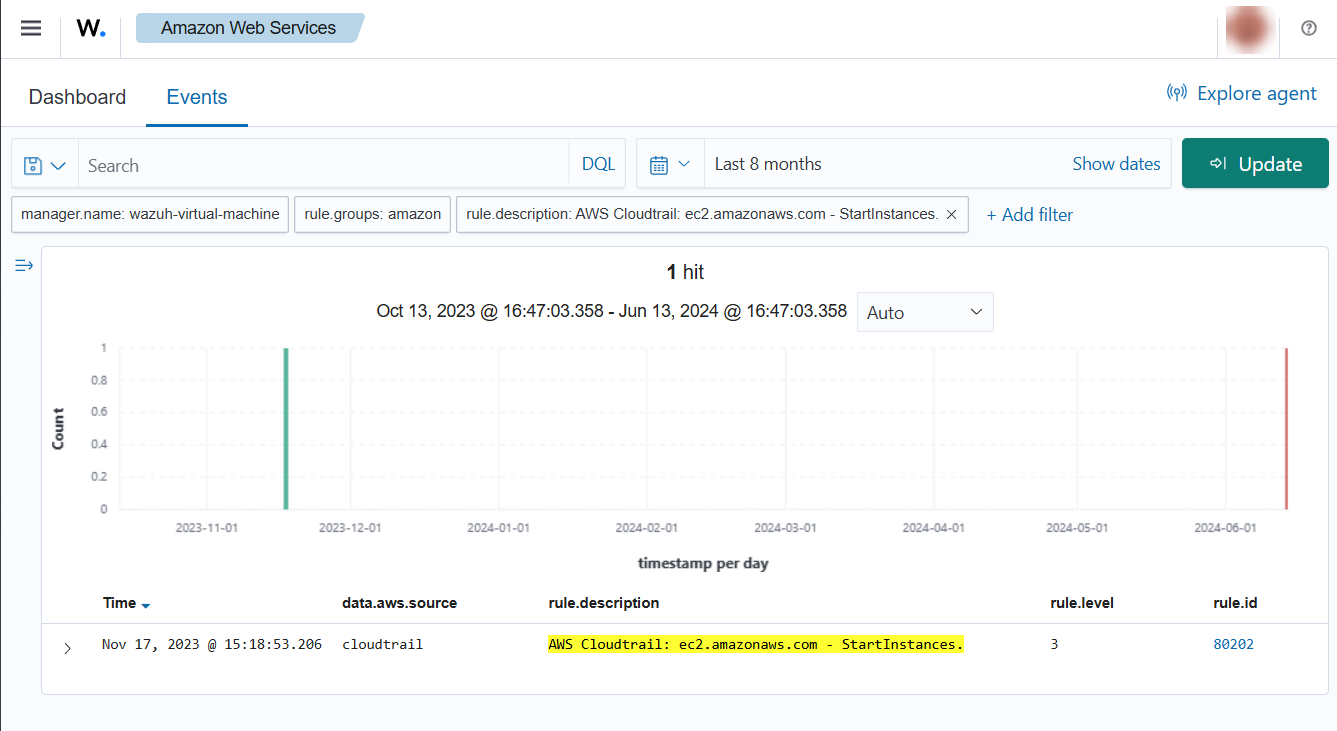
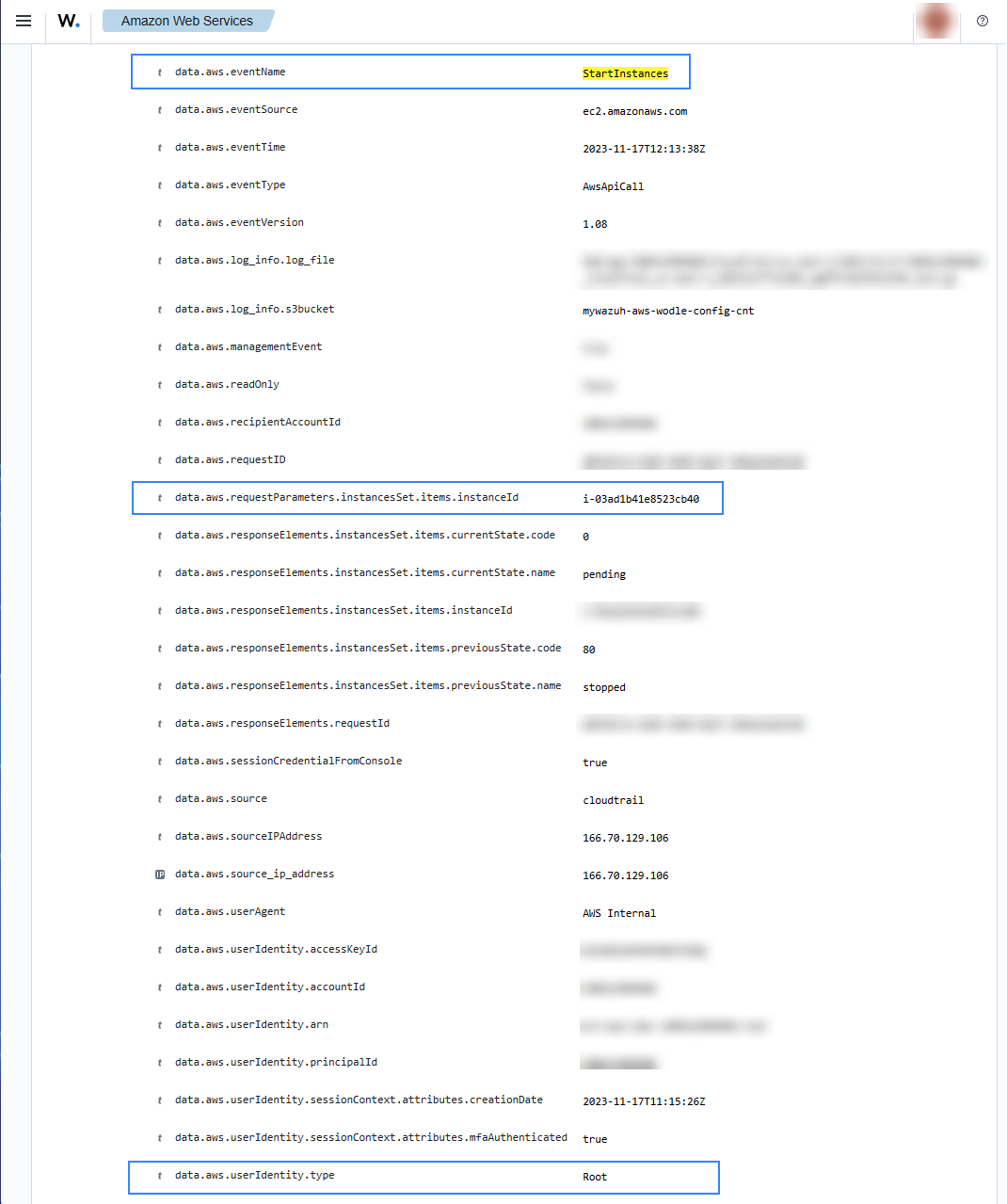
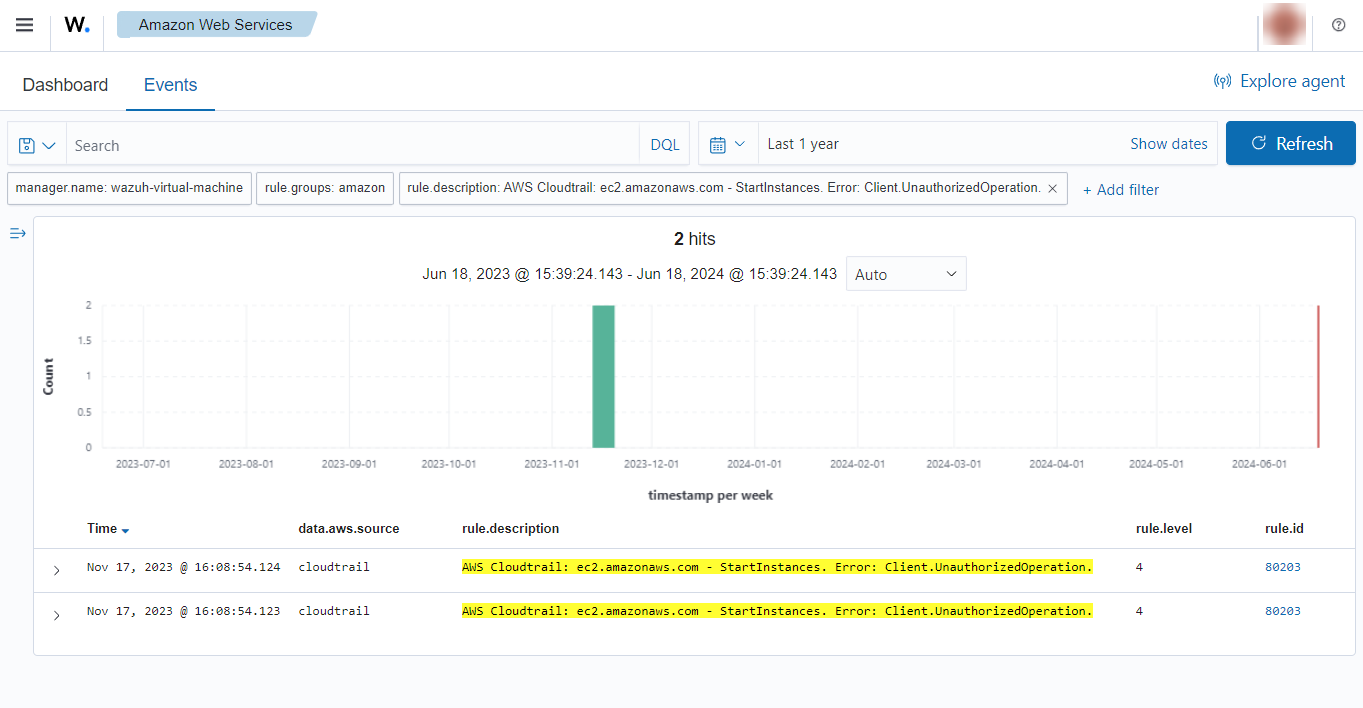
If a user tries to start instances without relevant permissions the following alert will be shown on the Wazuh dashboard.
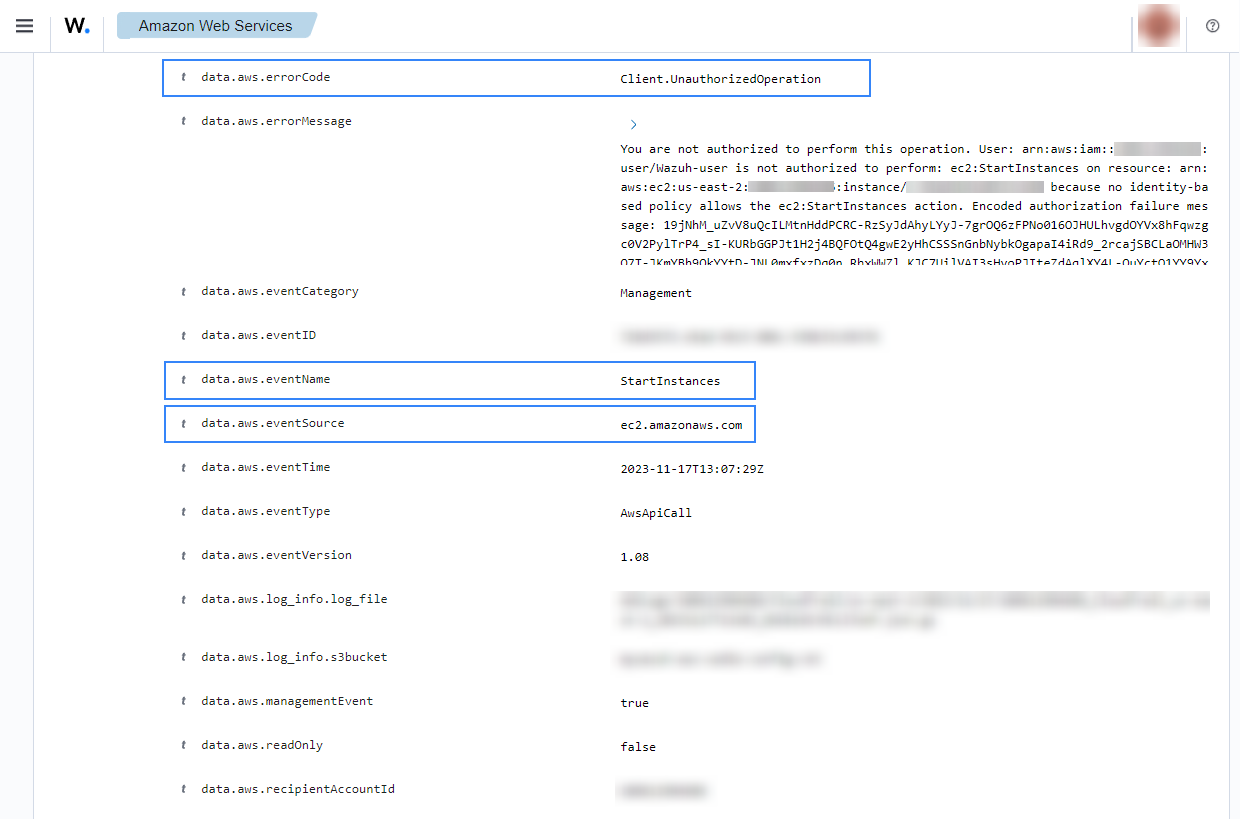
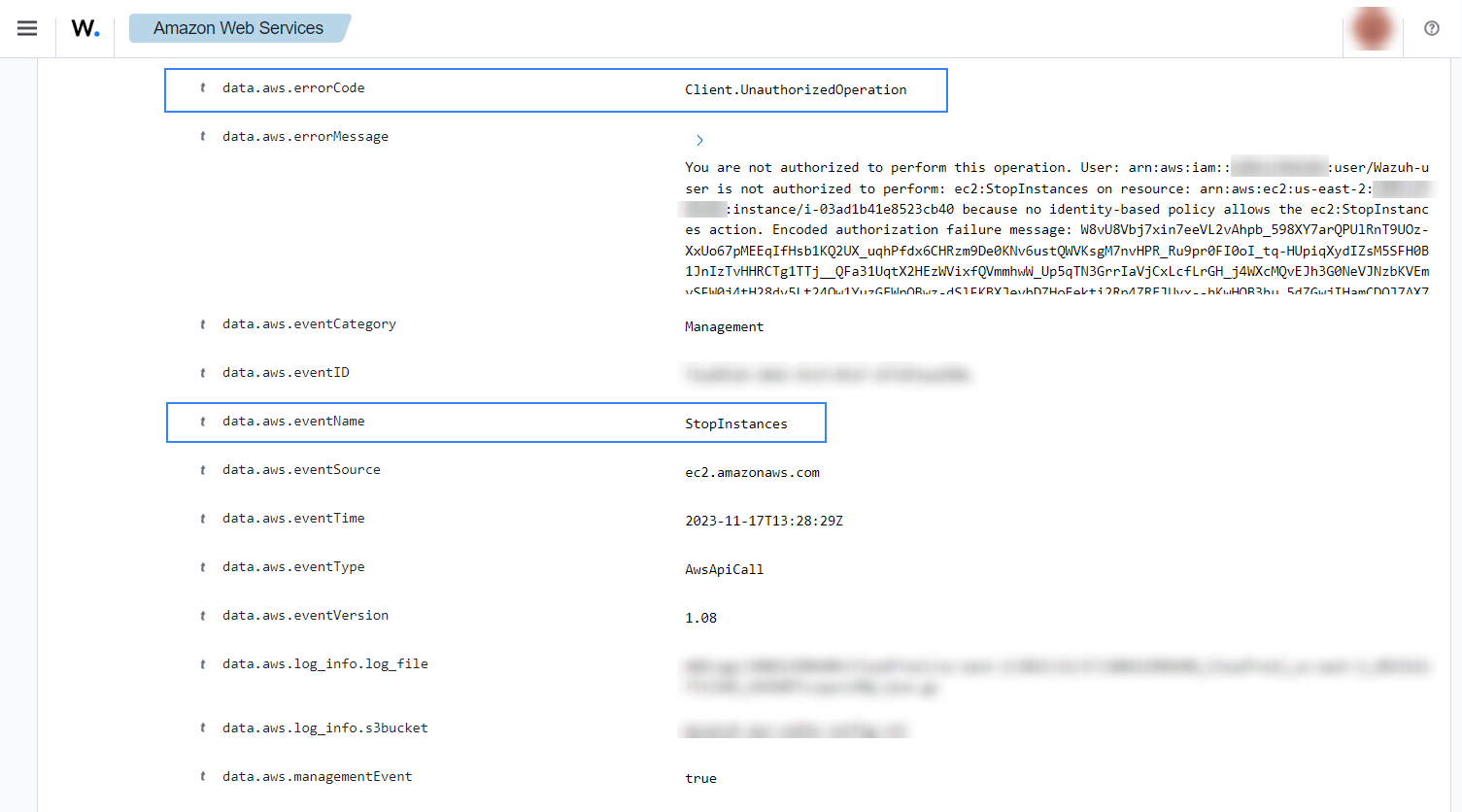
Stop instances in EC2
When an EC2 instance is stopped, the following alerts with rule ID 80202 will be shown on the Wazuh dashboard.
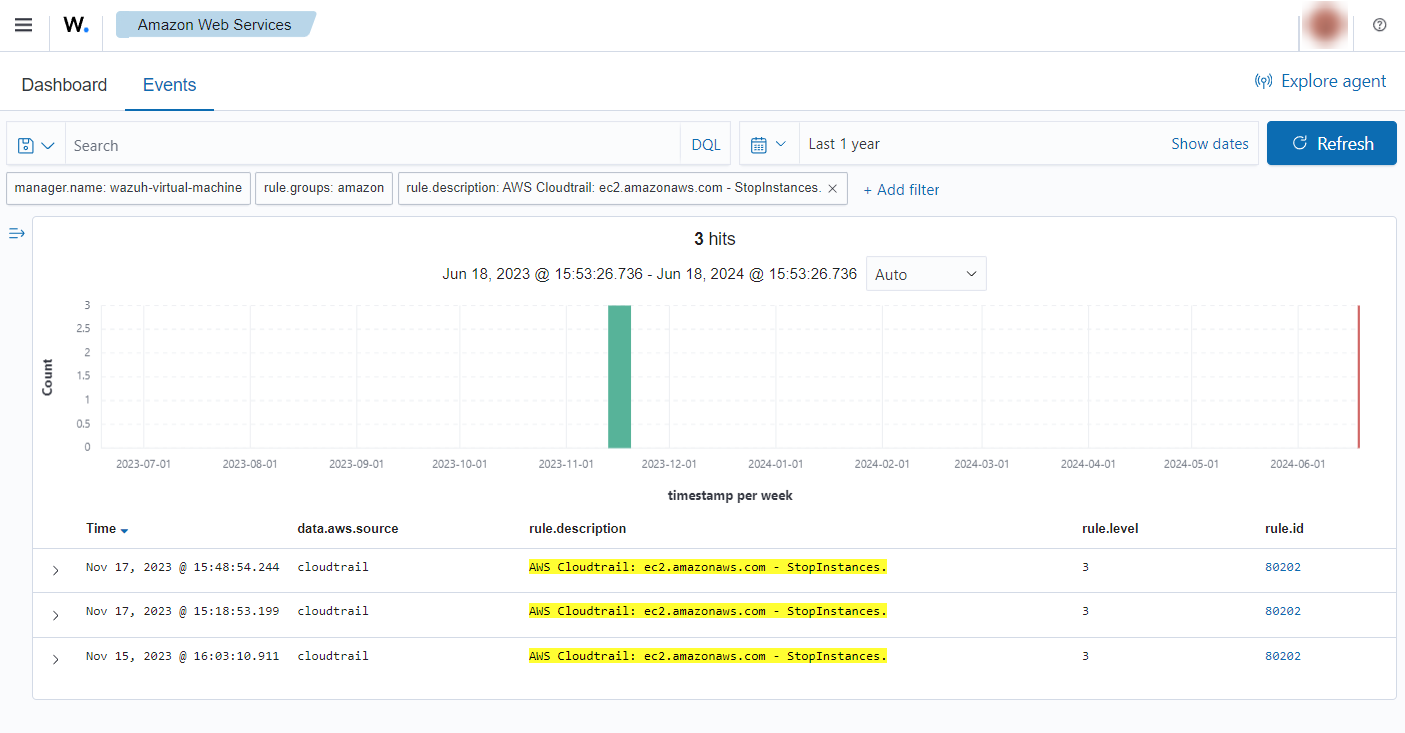
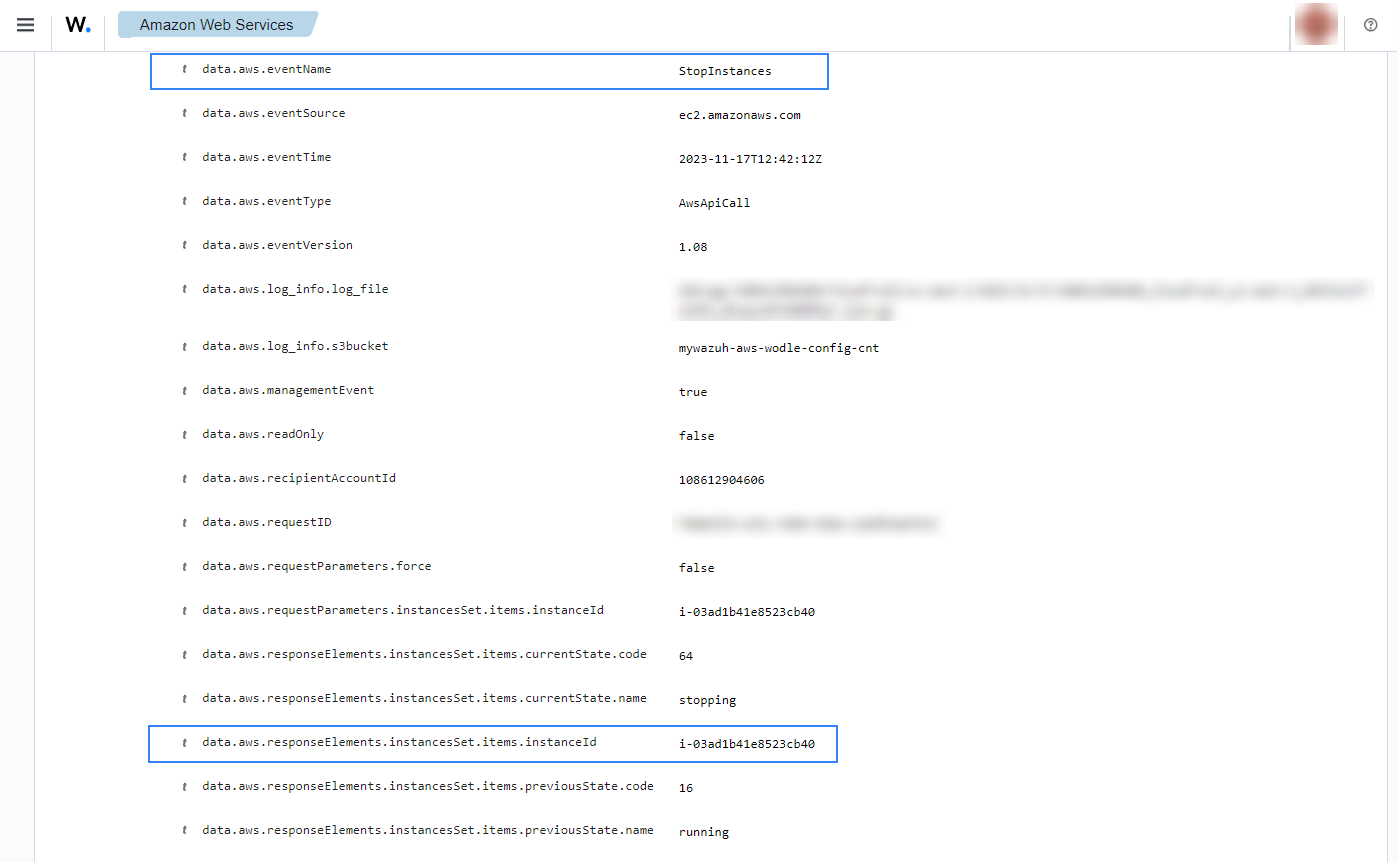
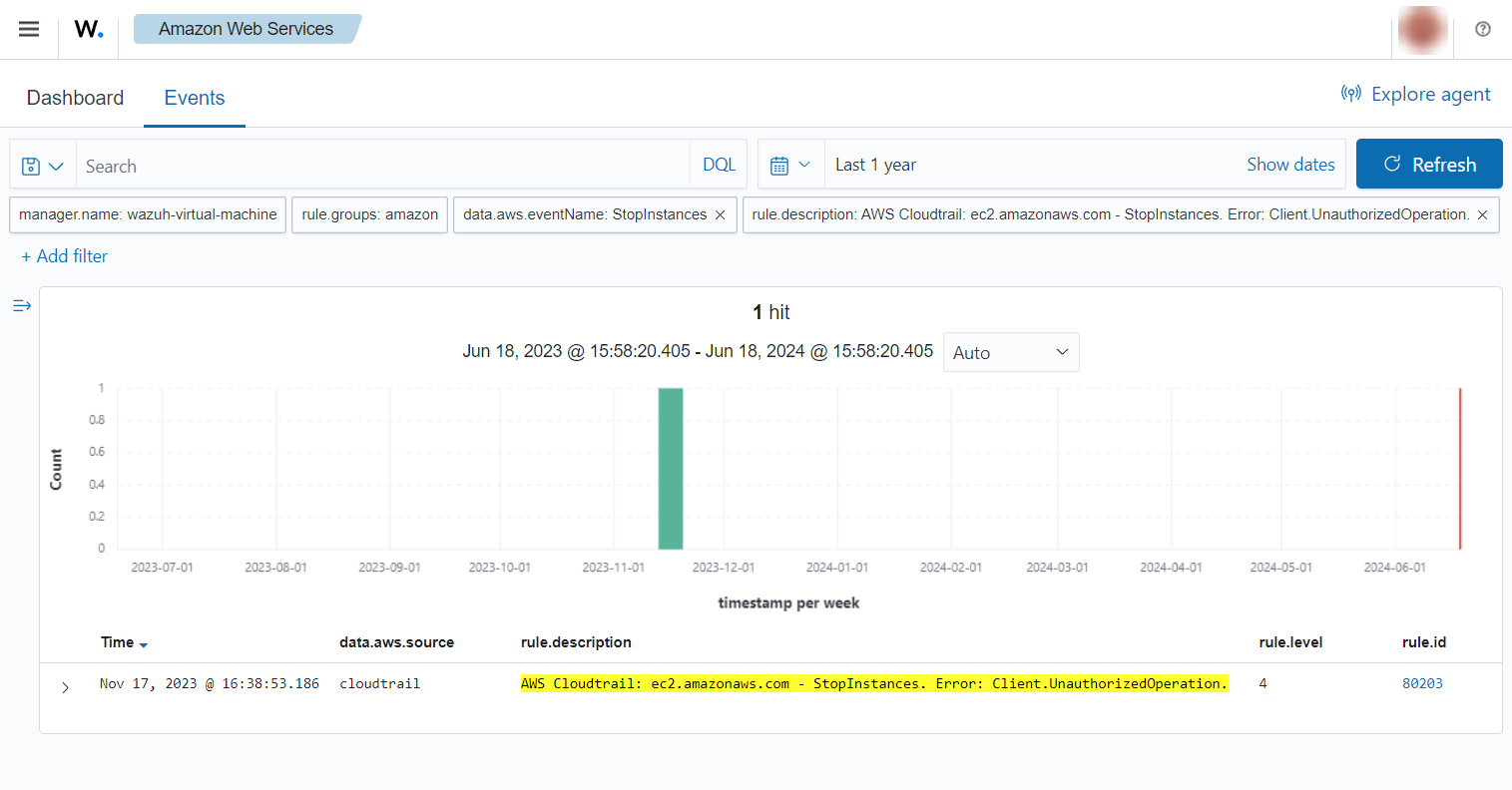
If a user tries to stop instances without relevant permissions, the following alert with rule ID 80203 will be shown on the Wazuh dashboard.
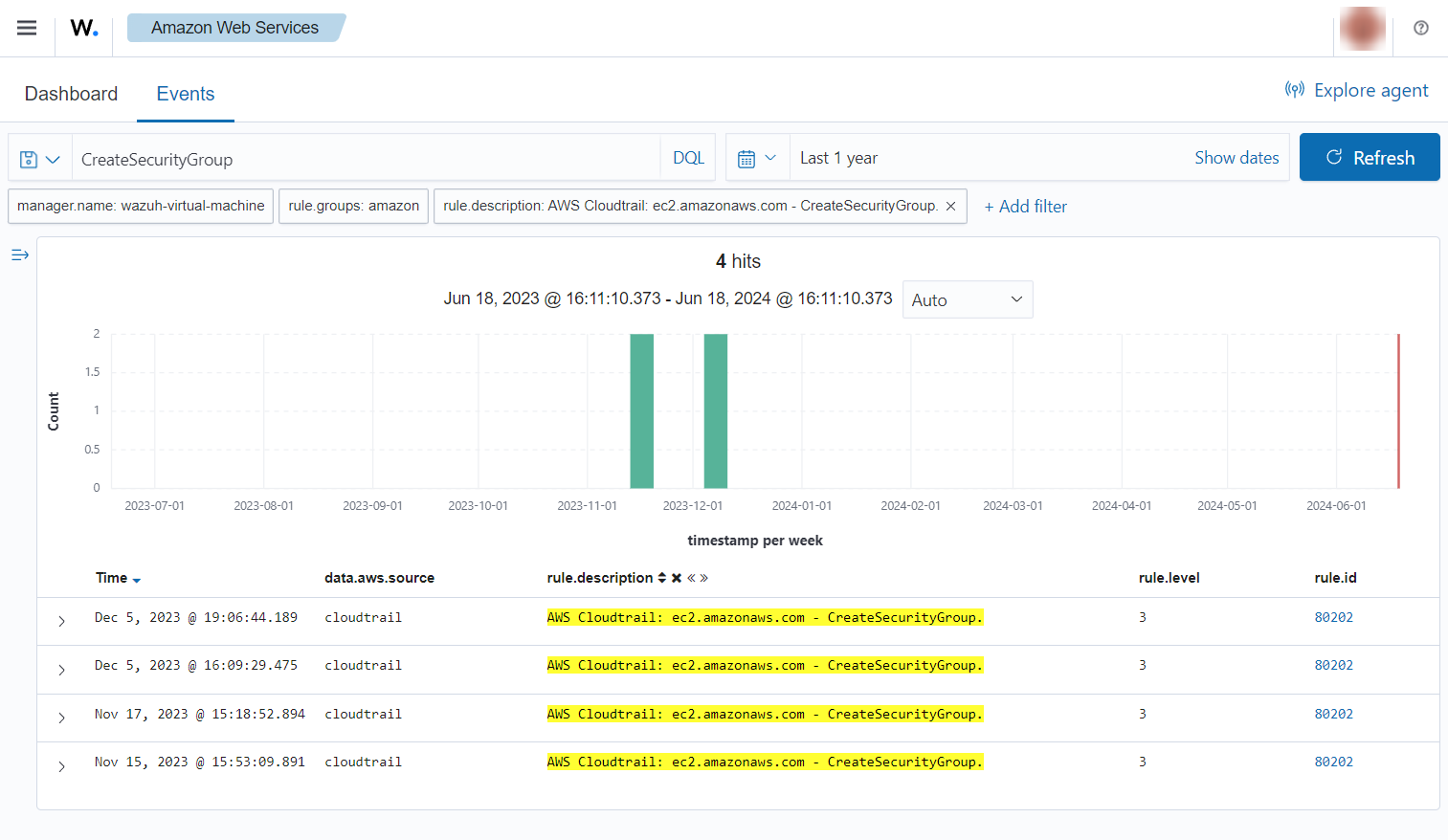
Create security groups in EC2
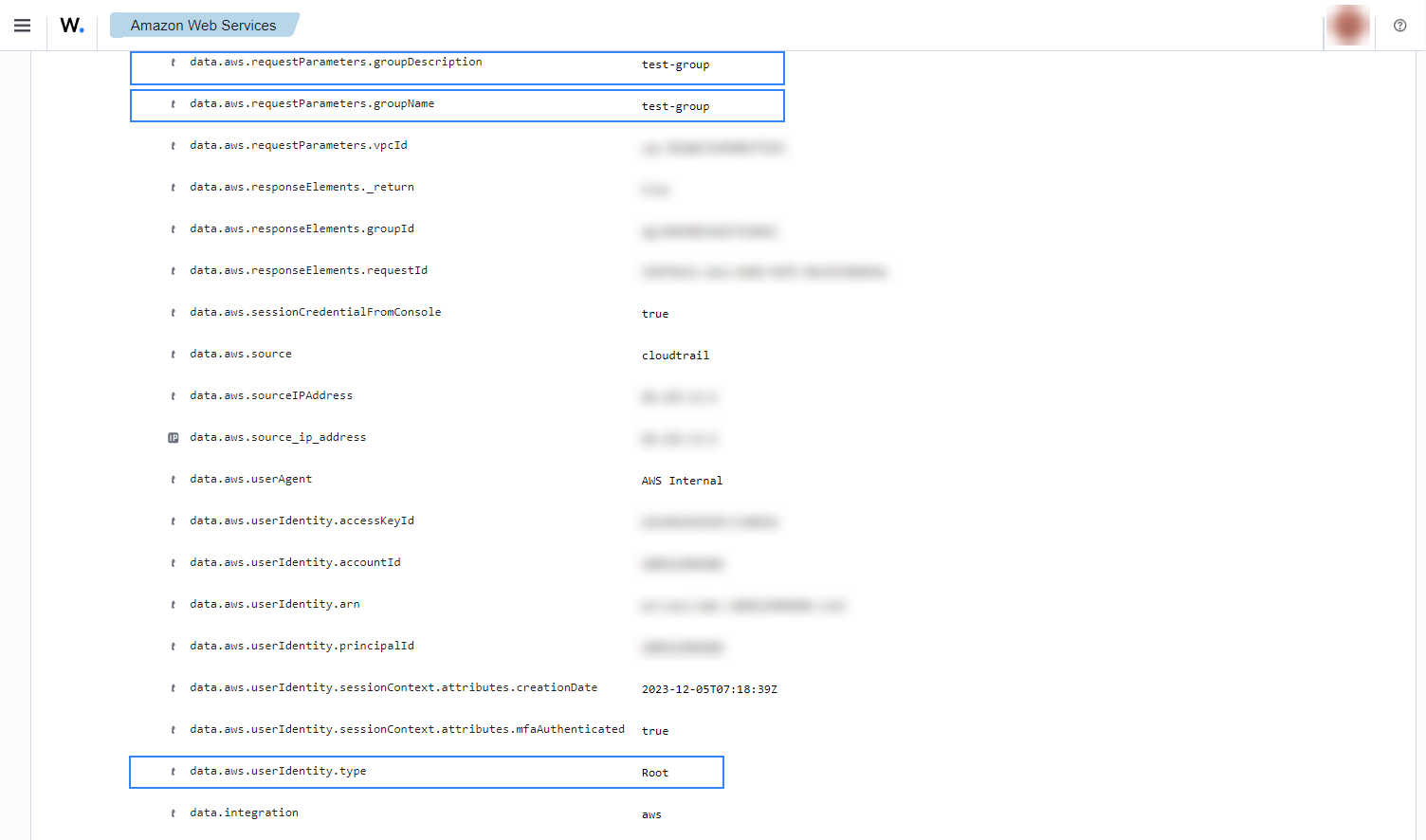
When a new EC2 security group is created, the following alerts with rule ID 80202 is shown on the Wazuh dashboard. It shows information such as the user who created it and information about the security group.
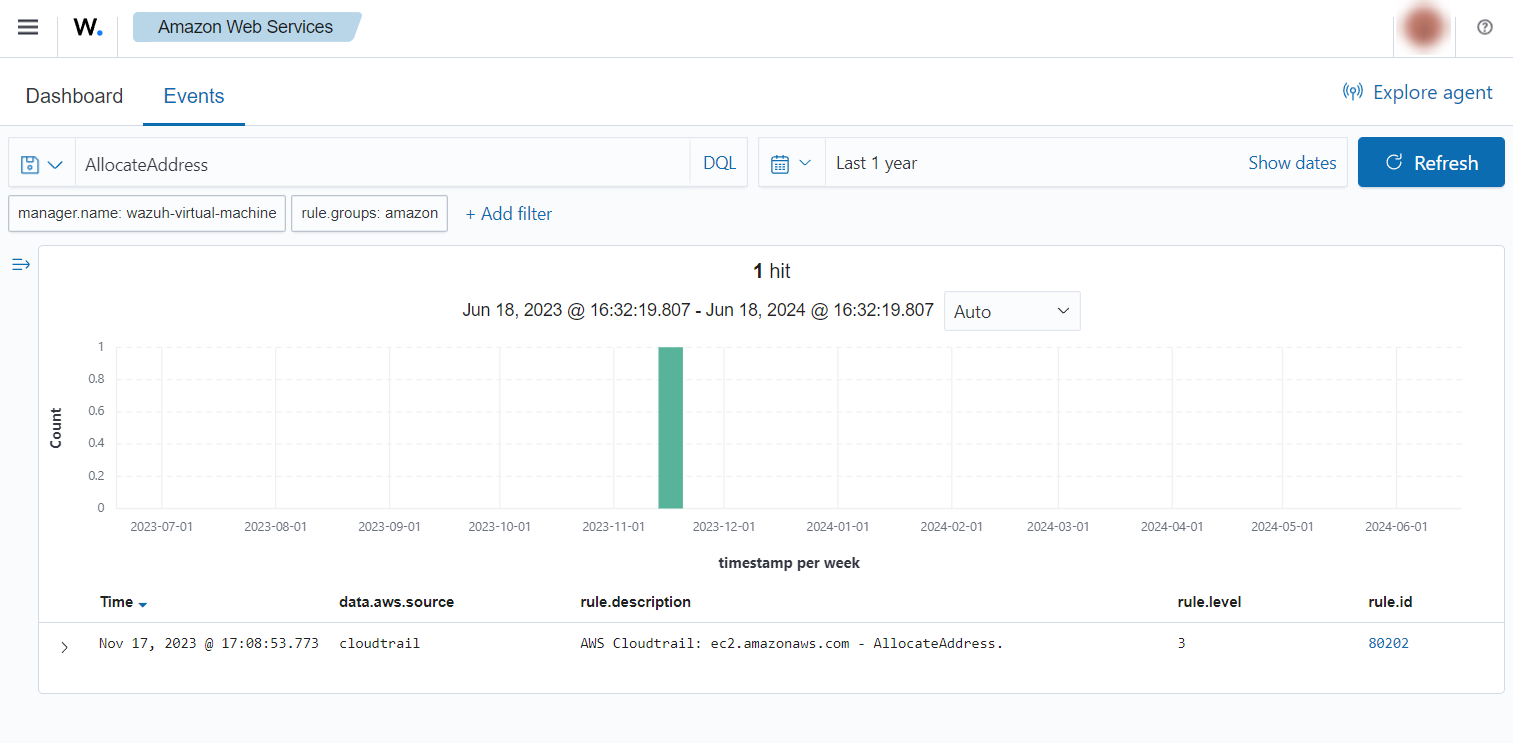
Allocate a new Elastic IP address
If a new Elastic IP address is allocated, the following with rule ID 80202 alerts will be shown on the Wazuh dashboard.
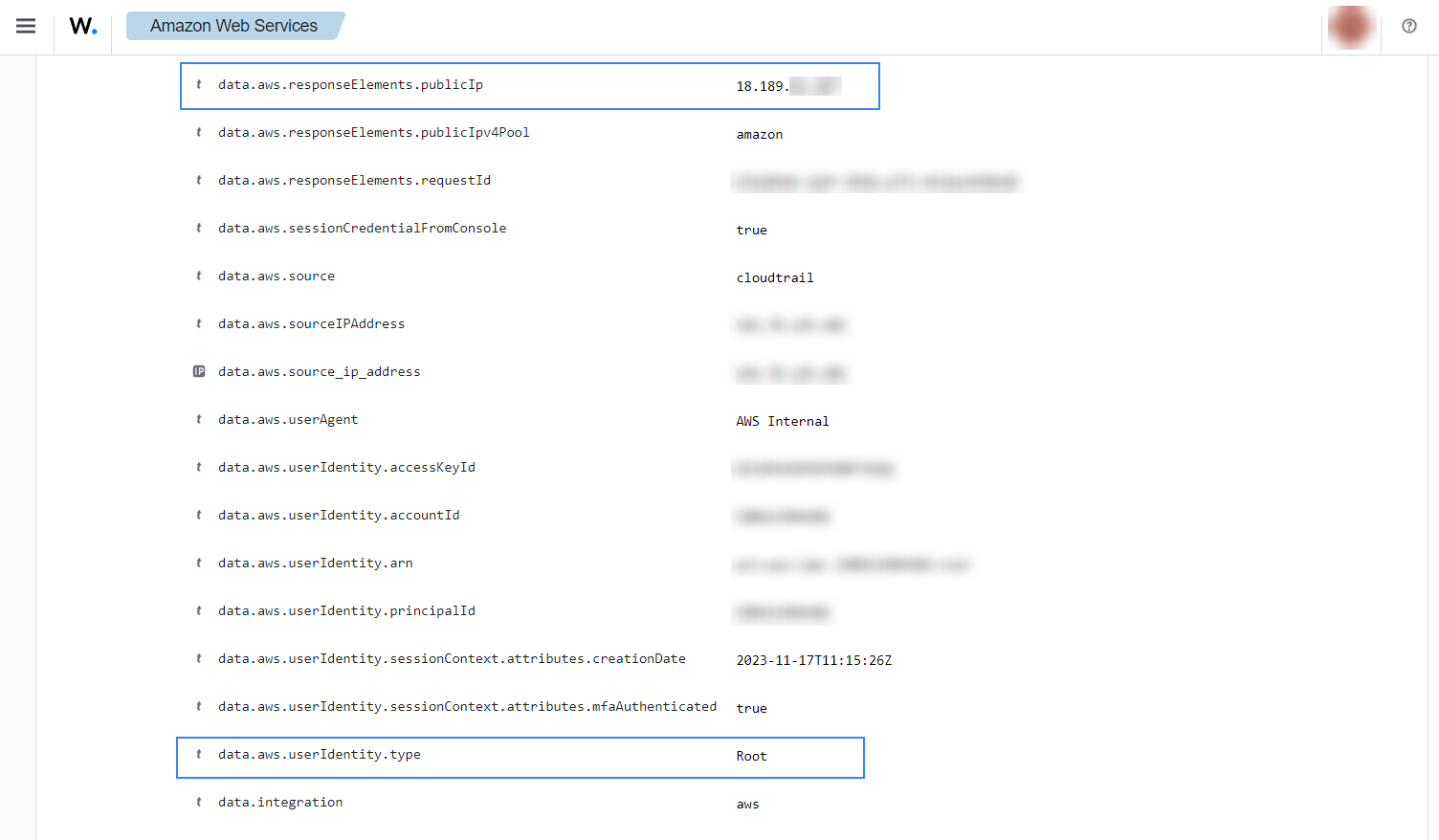
Associate a new Elastic IP address
If an Elastic IP address is associated, the following alert with rule ID 80202 will be shown on the Wazuh dashboard.
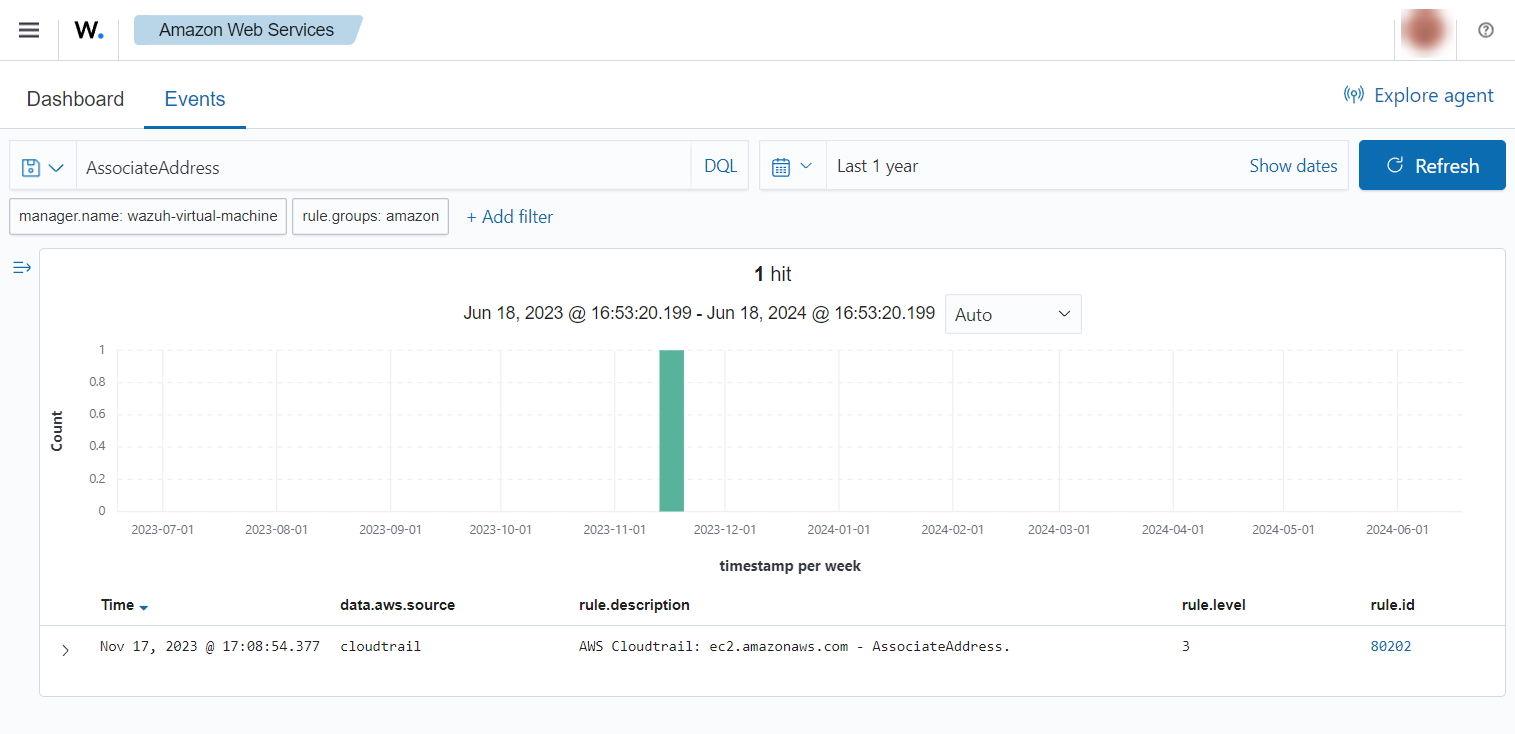
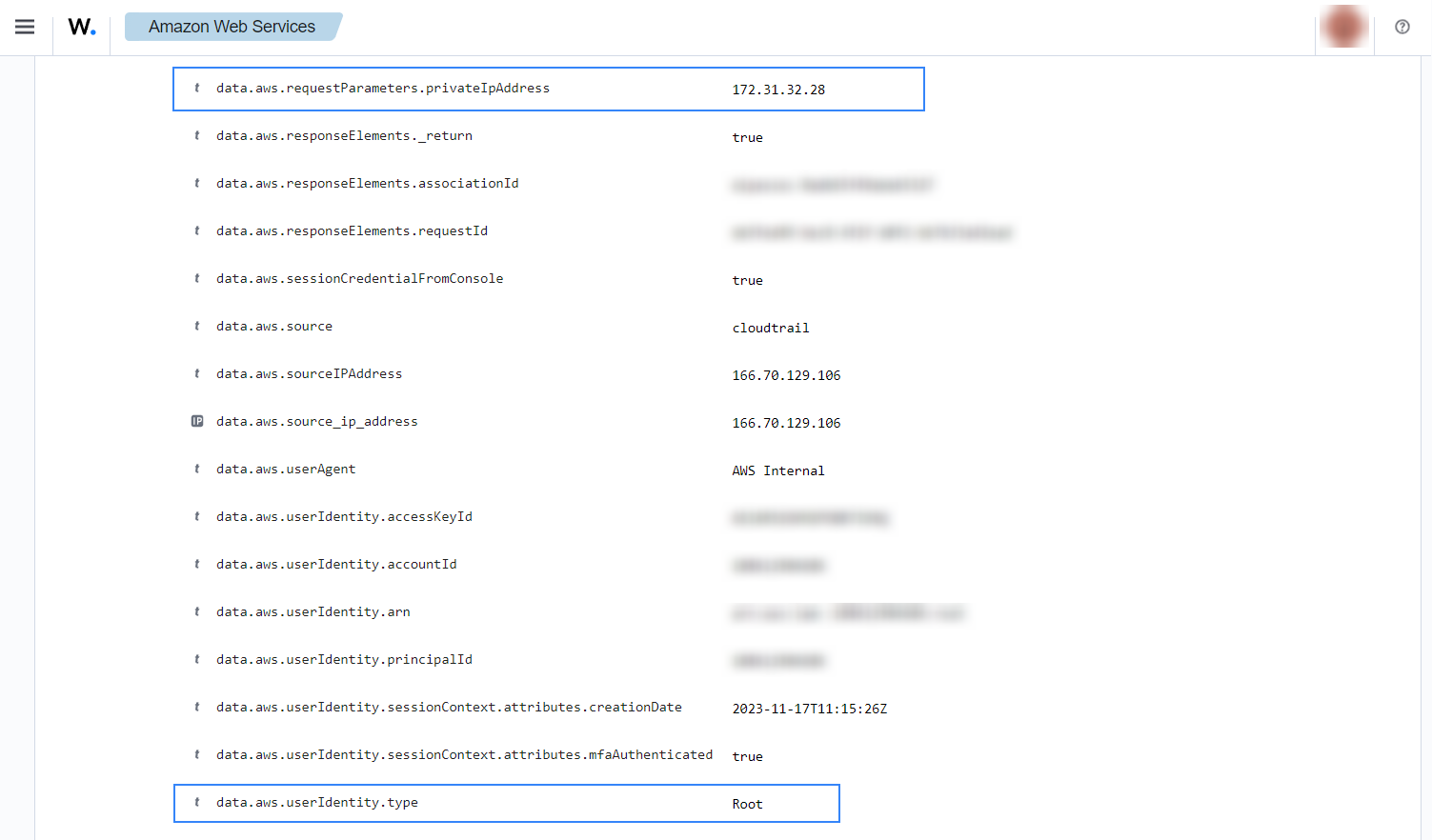
IAM
Identity and Access Management (IAM) allows you to create and manage AWS users and groups, and manage permissions to allow and deny their access to AWS resources. You can use the AWS IAM log data to monitor user access to AWS services and resources.
Below are some use cases for IAM events.
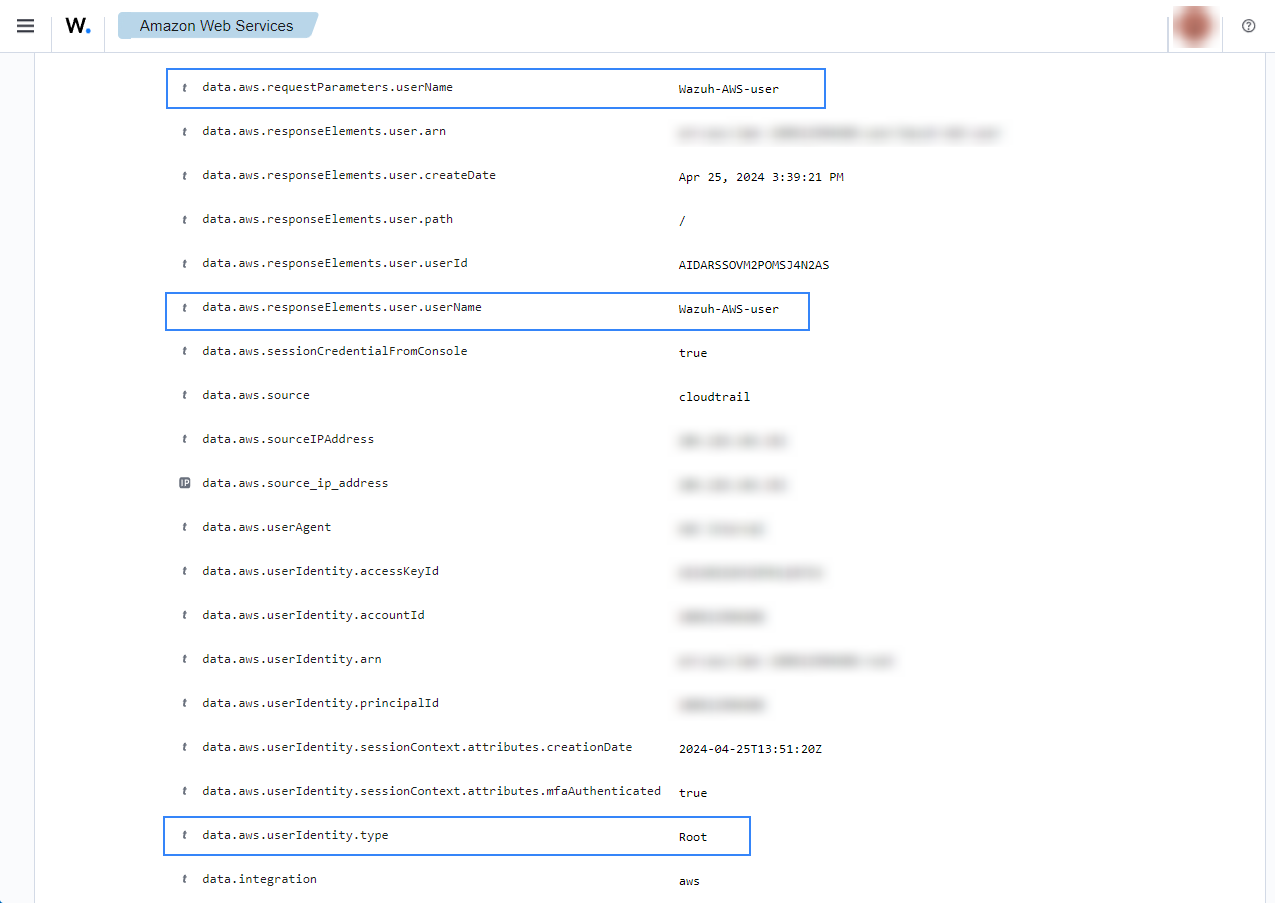
Create a user account
When we create a new user account in IAM, a CloudTrail event is generated. As previously mentioned, the log message is collected by the Wazuh agent, and forwarded to the Wazuh server for analysis. When a user account is created, the following alerts with rule ID 80202 will appear on the Wazuh dashboard. You can see the username of the created user, the time it was created, and who created it.
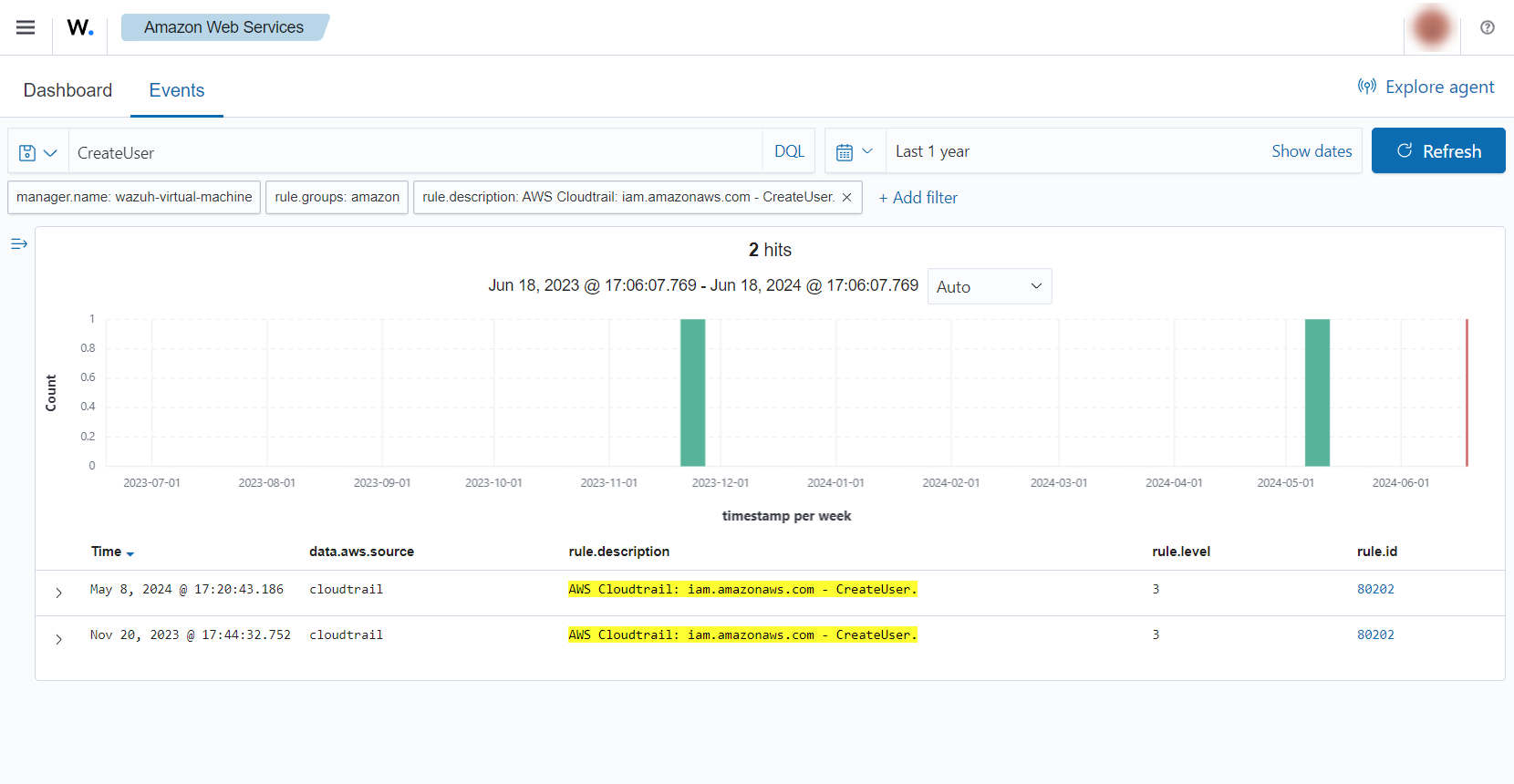
Create a user account without permissions
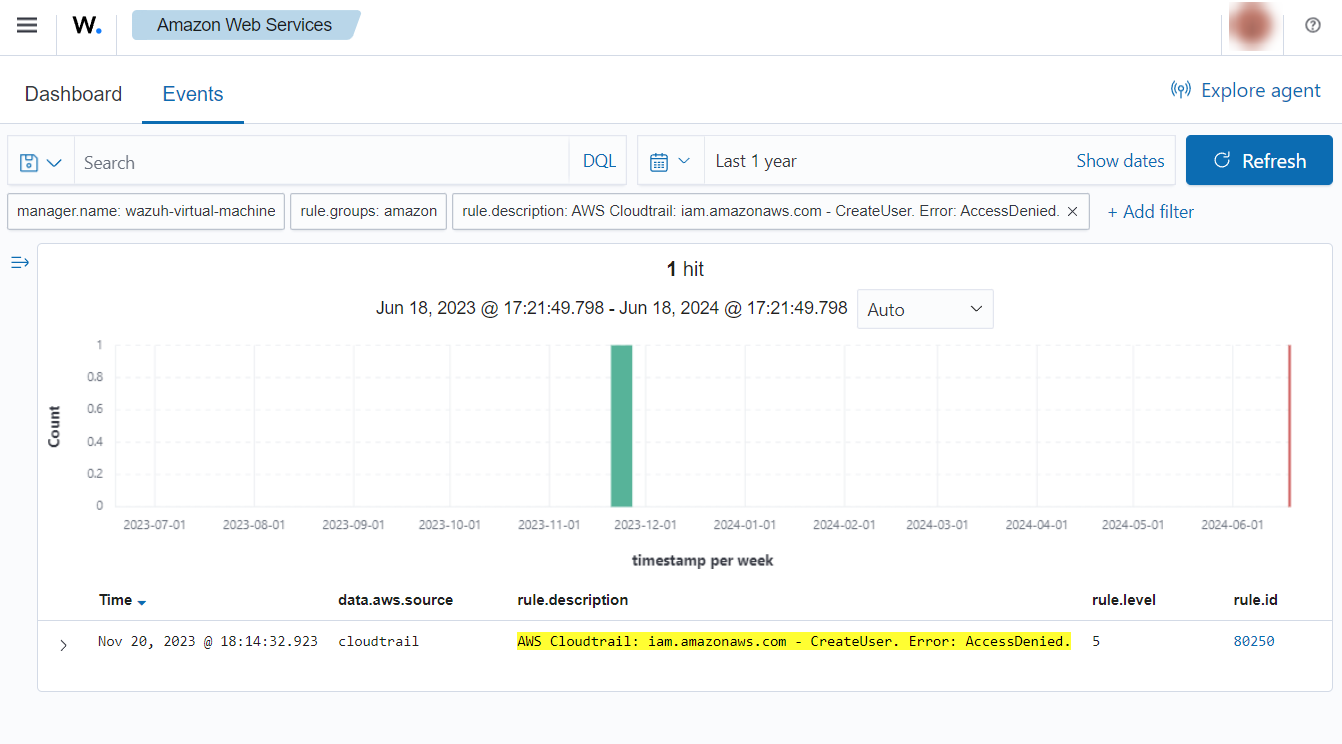
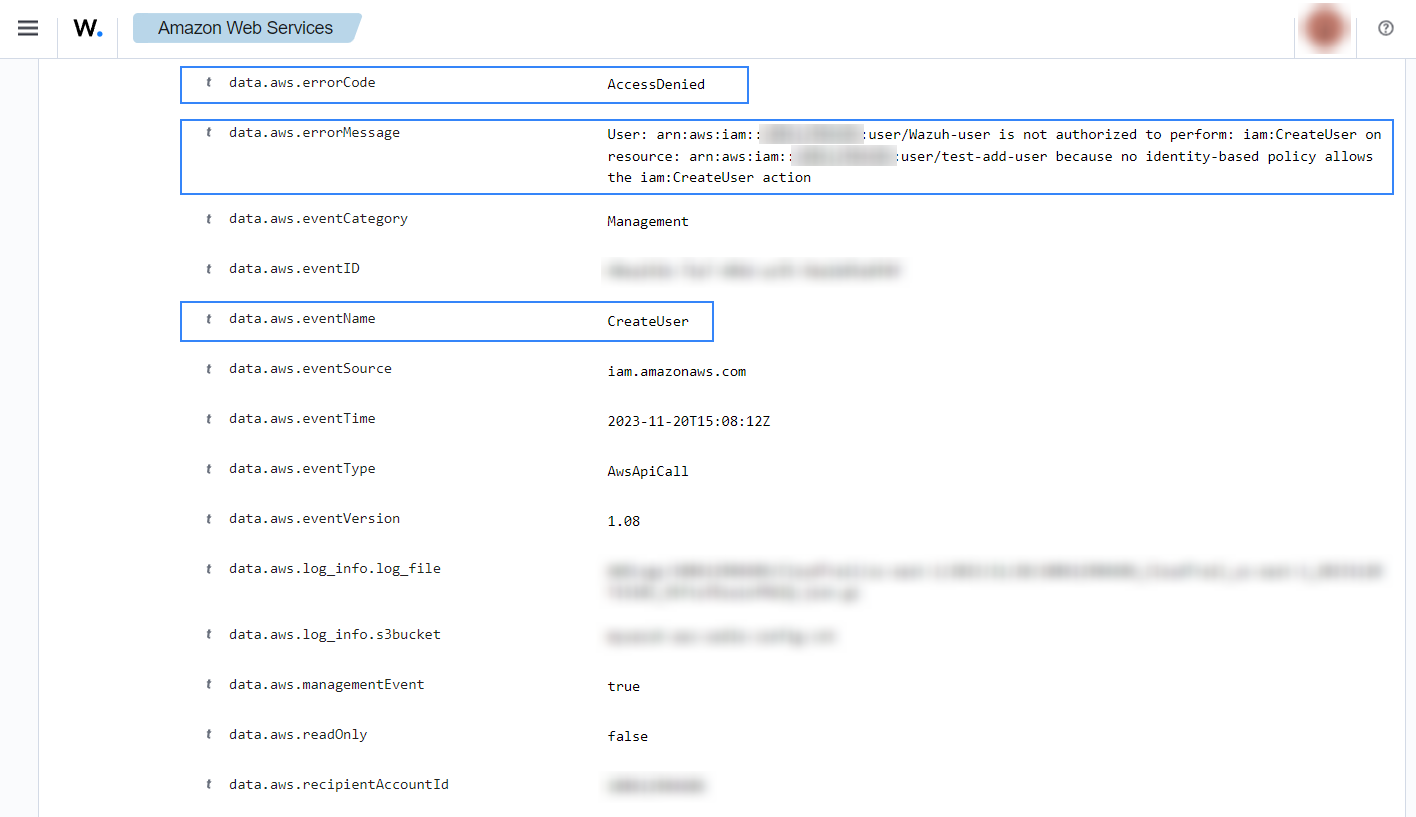
If an unauthorized user attempts to create new users, the following alert with rule ID 80250 will be shown on the Wazuh dashboard. It will show you which user has tried to create a user account and the username it tried to create.
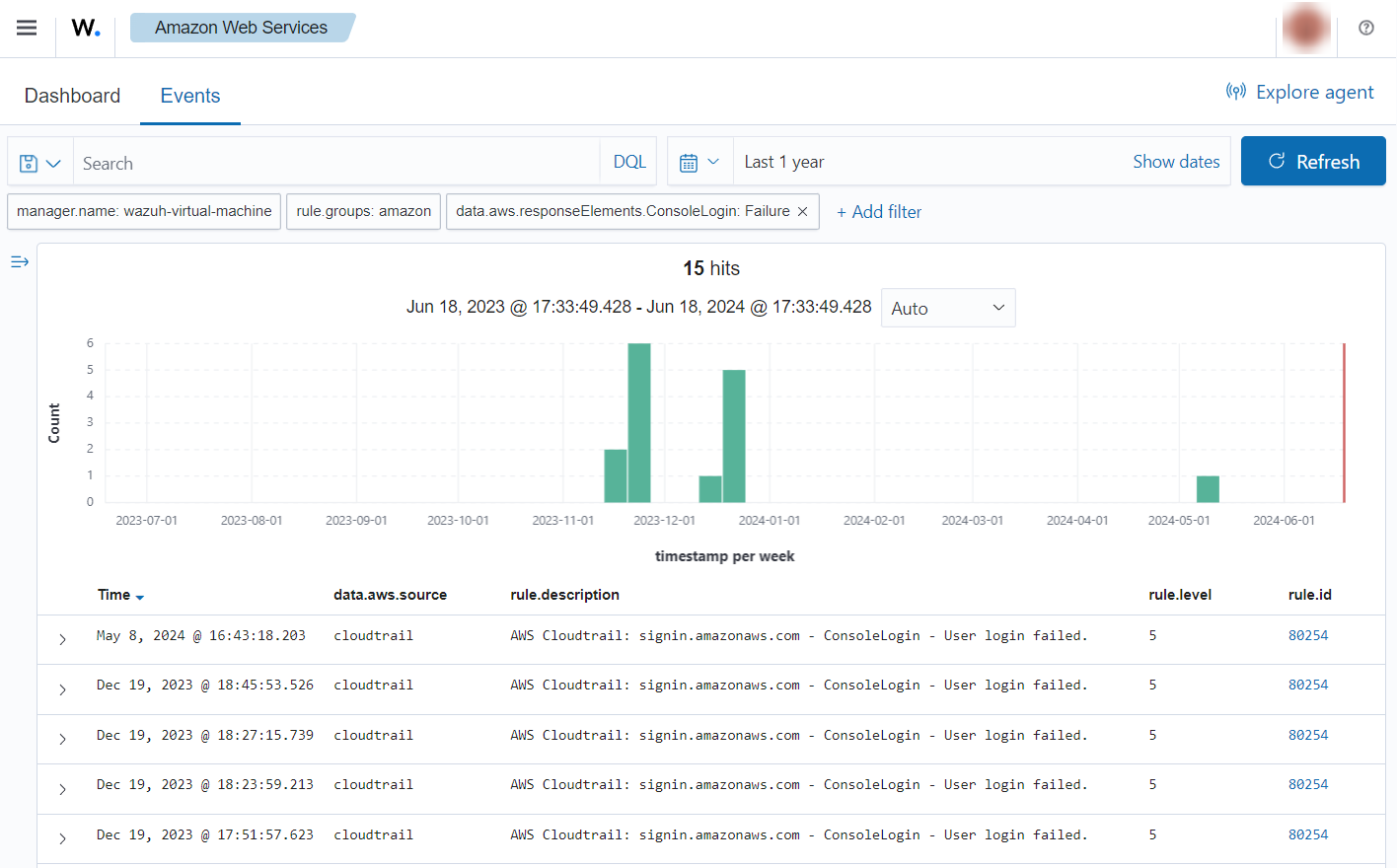
User login failed
When a user tries to log in with an invalid password, the following alerts with rule ID 80254 will be shown on the Wazuh dashboard. There will be shown data such as the user who tried to log in and the browser it was using.
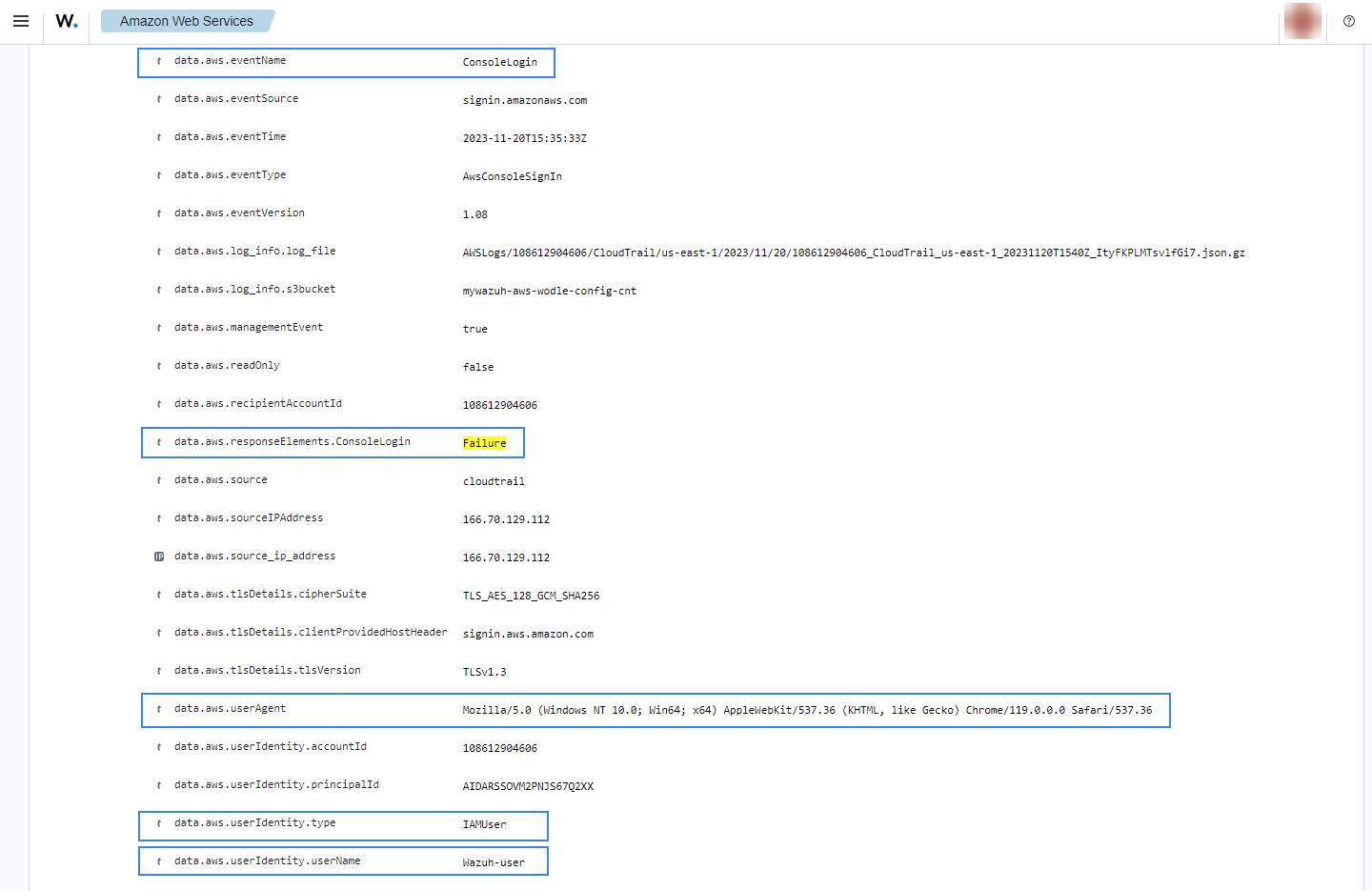
Possible break-in attempt
When more than four consecutive unsuccessful login attempts to the AWS console occur in a 360-second time window, the following alert with rule ID 80255 will be shown on the Wazuh dashboard.
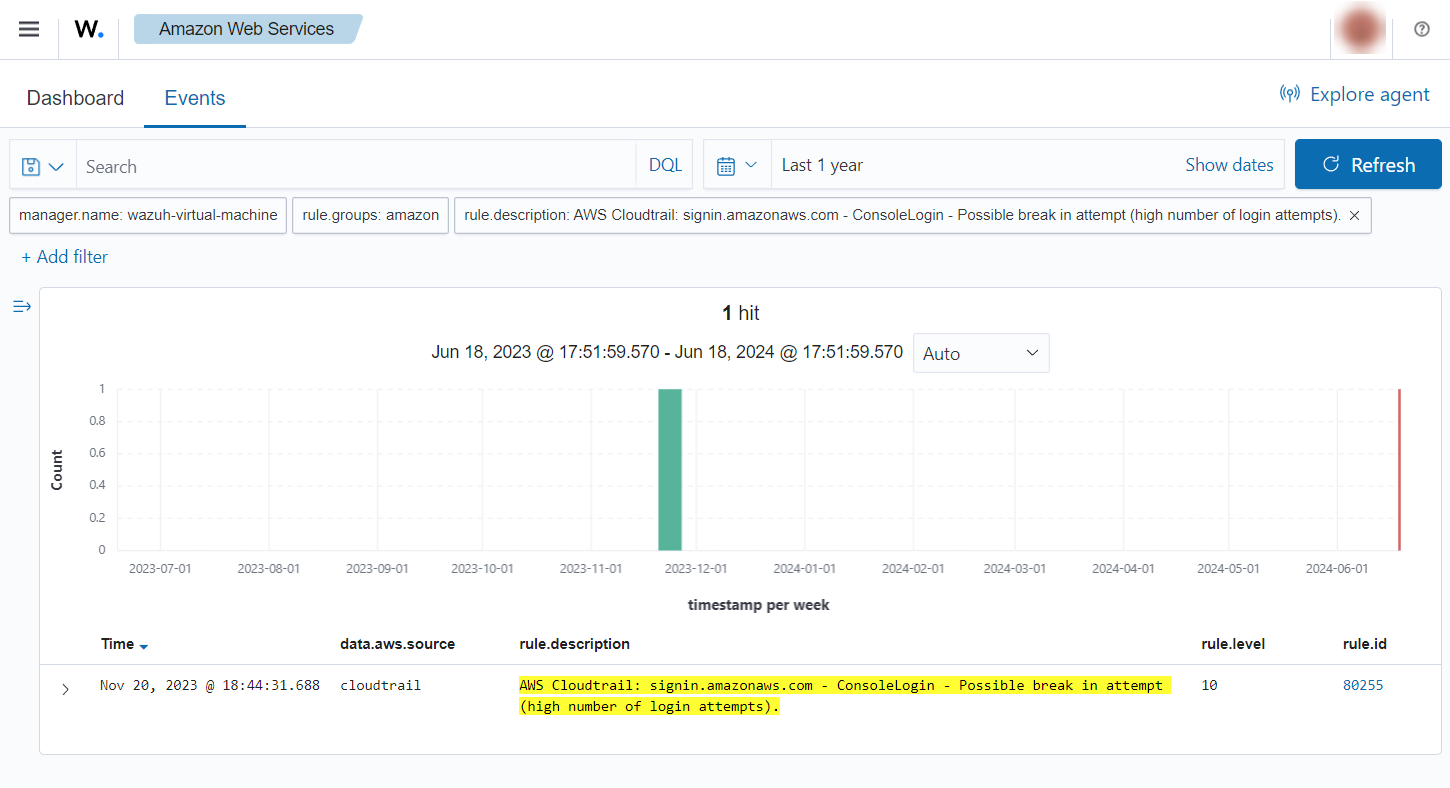
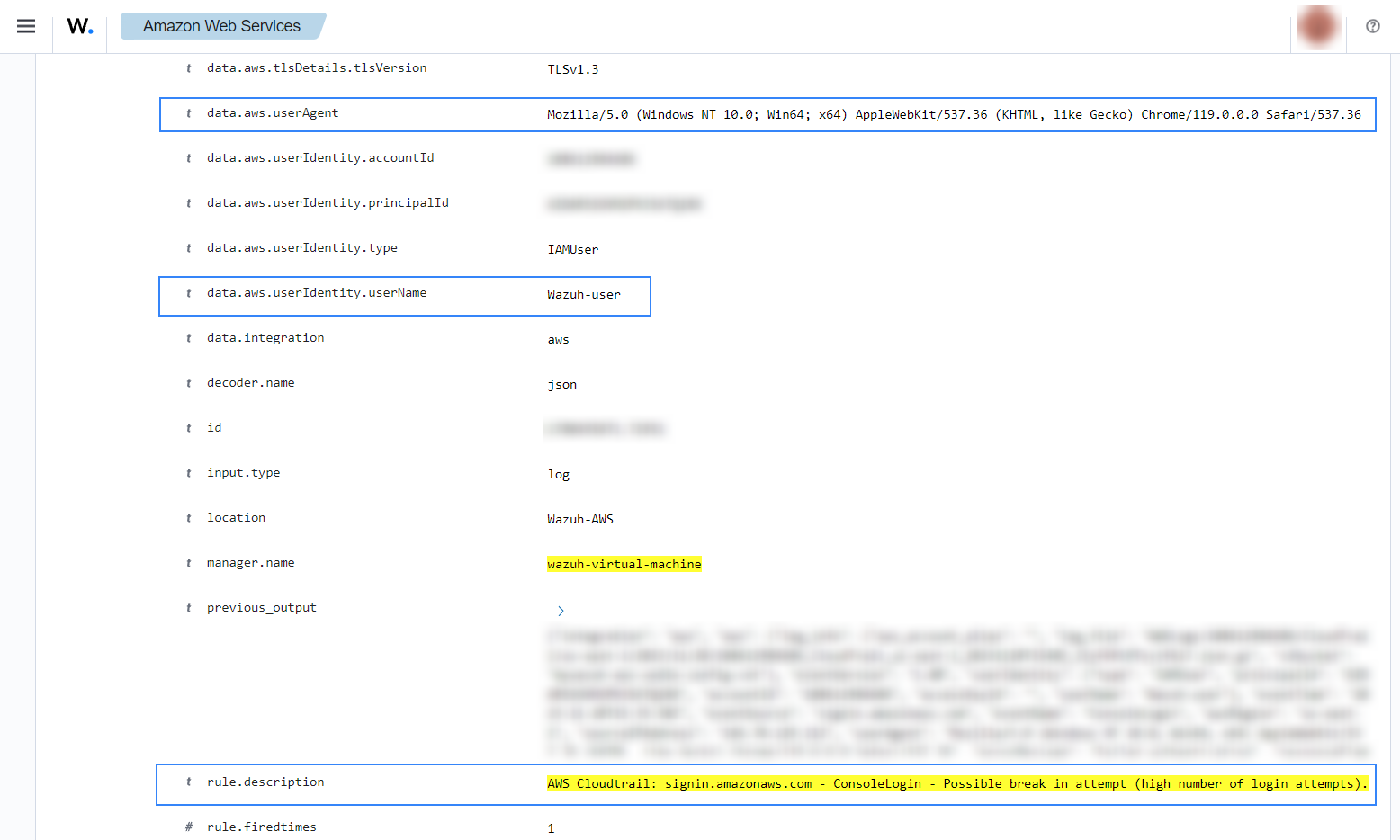
Login success
After a successful login, the following alerts with rule ID 80253 will be shown on the Wazuh dashboard. It shows the user who logged in, the browser it used, and other useful information.
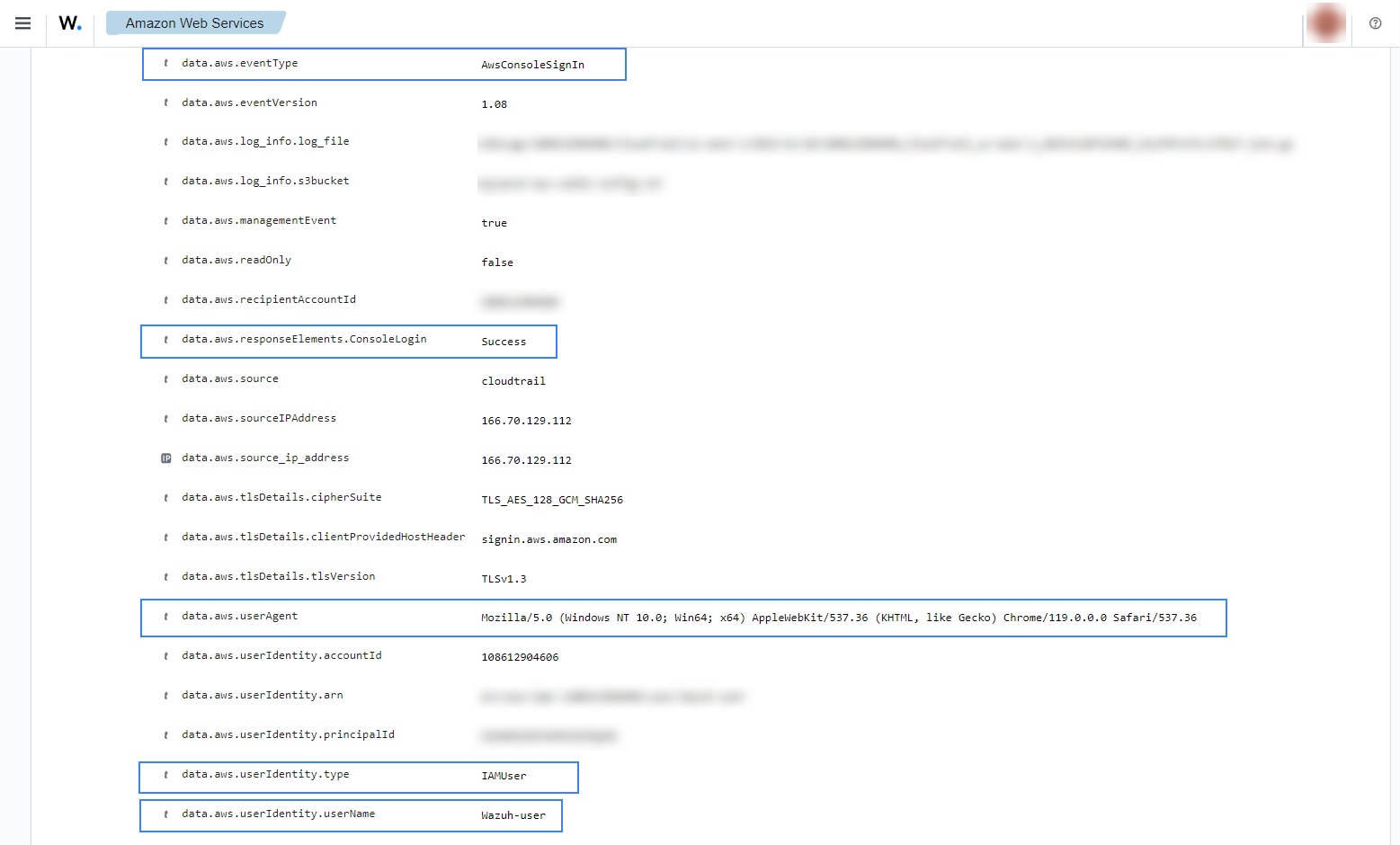
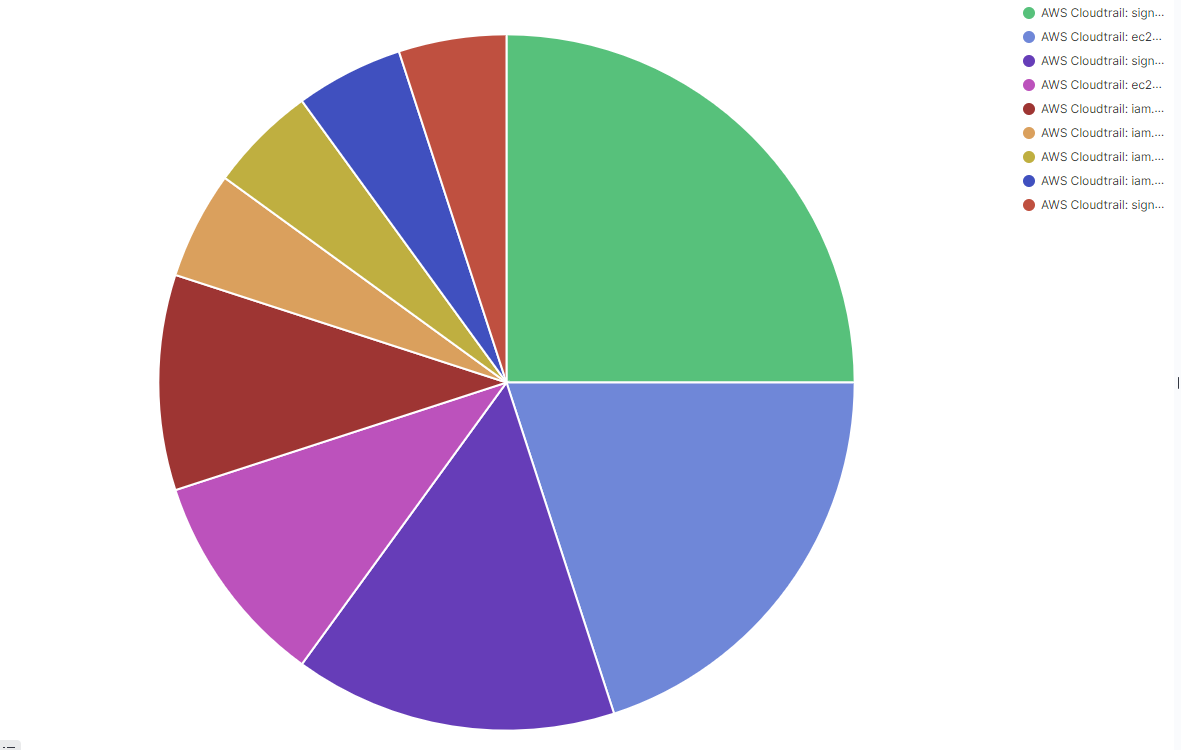
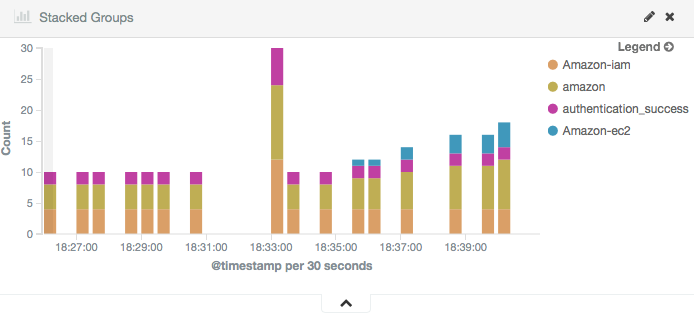
You can create visualizations like this on the Wazuh dashboard for IAM events by following the custom dashboard guide:
Pie Chart |
Stacked Groups |
|---|---|
|
|