Getting started with Wazuh
Wazuh is a free and open source security platform that unifies XDR and SIEM capabilities. It protects workloads across on-premises, virtualized, containerized, and cloud-based environments.
Wazuh helps organizations and individuals to protect their data assets against security threats. It is widely used by thousands of organizations worldwide, from small businesses to large enterprises.
Check this Getting Started for an overview of the Wazuh platform components, architecture, and common use cases.
Community and support
Wazuh has one of the largest open source security communities in the world. You can become part of it to learn from other users, participate in discussions, talk to our development team, and contribute to the project. The following resources are easily available:
Slack channel: Join our community channel to chat with our developers and technical team in a close to real-time experience.
Google group: Here you can share questions and learn from other Wazuh users. It is easy to subscribe via email.
GitHub repositories: Get access to the Wazuh source code, report issues, and contribute to the project. We happily review and accept pull requests.
Discord: Engage with our community in dynamic discussions and collaborations on the latest security trends and Wazuh developments.
Reddit: Join our subreddit to share insights, ask questions, and discuss security issues with fellow users.
X: Follow us on X for real-time updates, news, and quick tips from our development team and security experts.
LinkedIn: Stay updated with our professional network and industry news by connecting with us on LinkedIn.
YouTube: Subscribe to our YouTube channel for video tutorials, webinars, and walkthroughs of Wazuh features and configurations.
In addition, we also provide professional support, training, and consulting services.
How to install Wazuh
The Wazuh solution is composed of three central platform components and a single universal agent. For installing Wazuh in your infrastructure, you can check the following sections of our documentation:
The Quickstart is an automated way of installing Wazuh in just a few minutes.
The Installation guide provides instructions on how to install each central component and how to deploy the Wazuh agents.
Wazuh Cloud
The Wazuh Cloud is our software as a service (SaaS) solution. We provide a 14-day free trial for you to create a cloud environment and get the best out of our SaaS solution. Check the Cloud service documentation for more information.
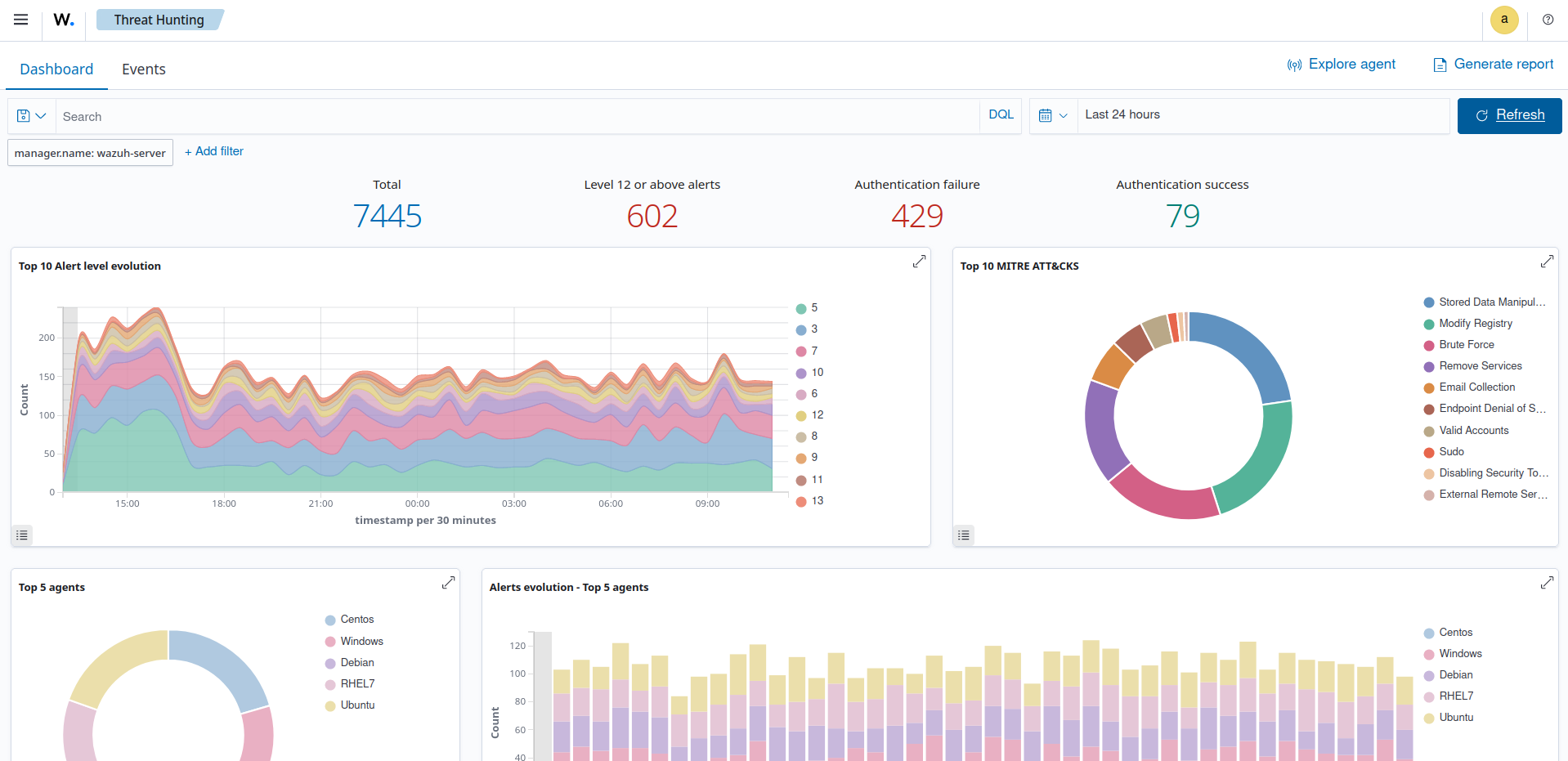
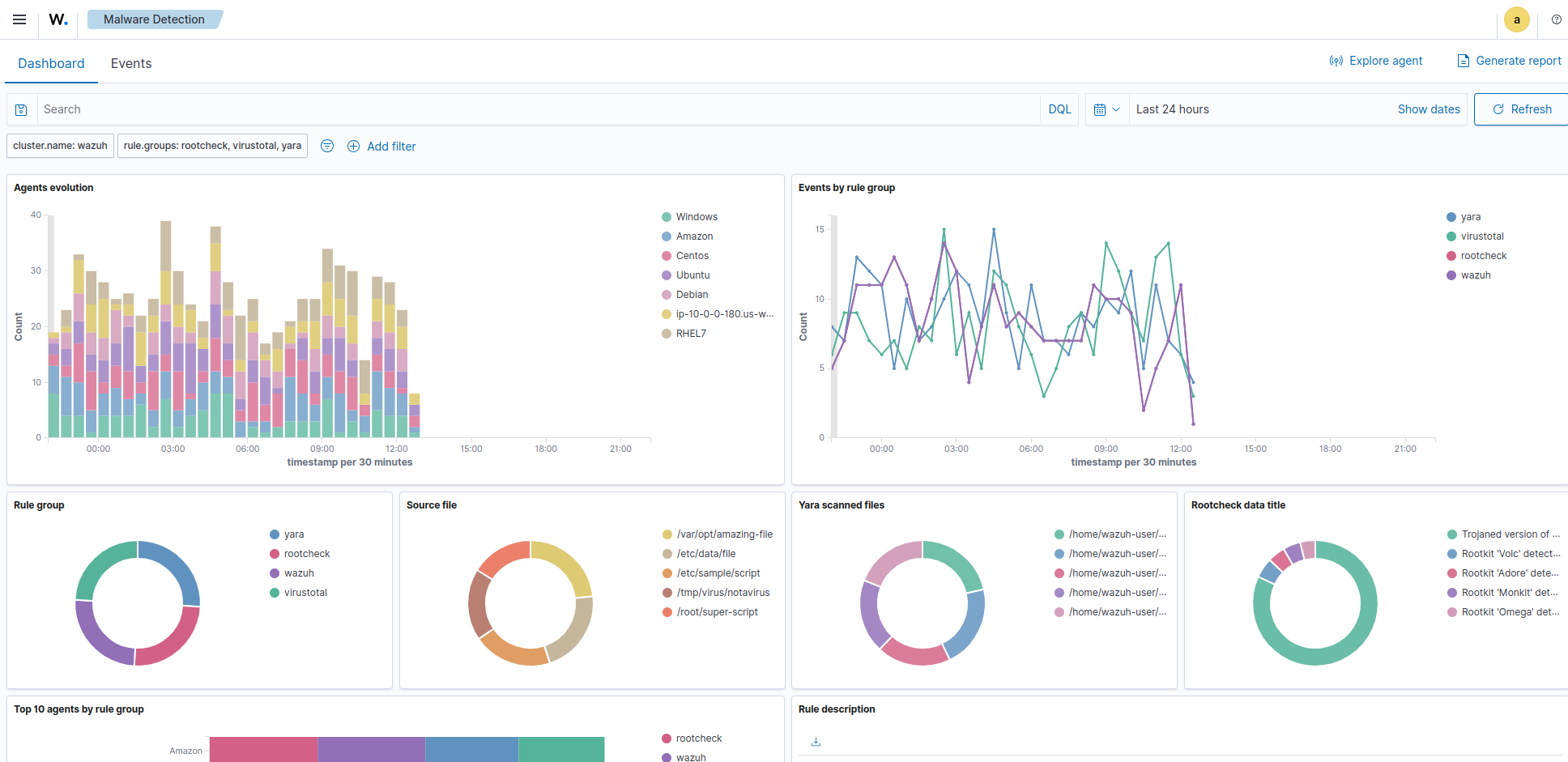
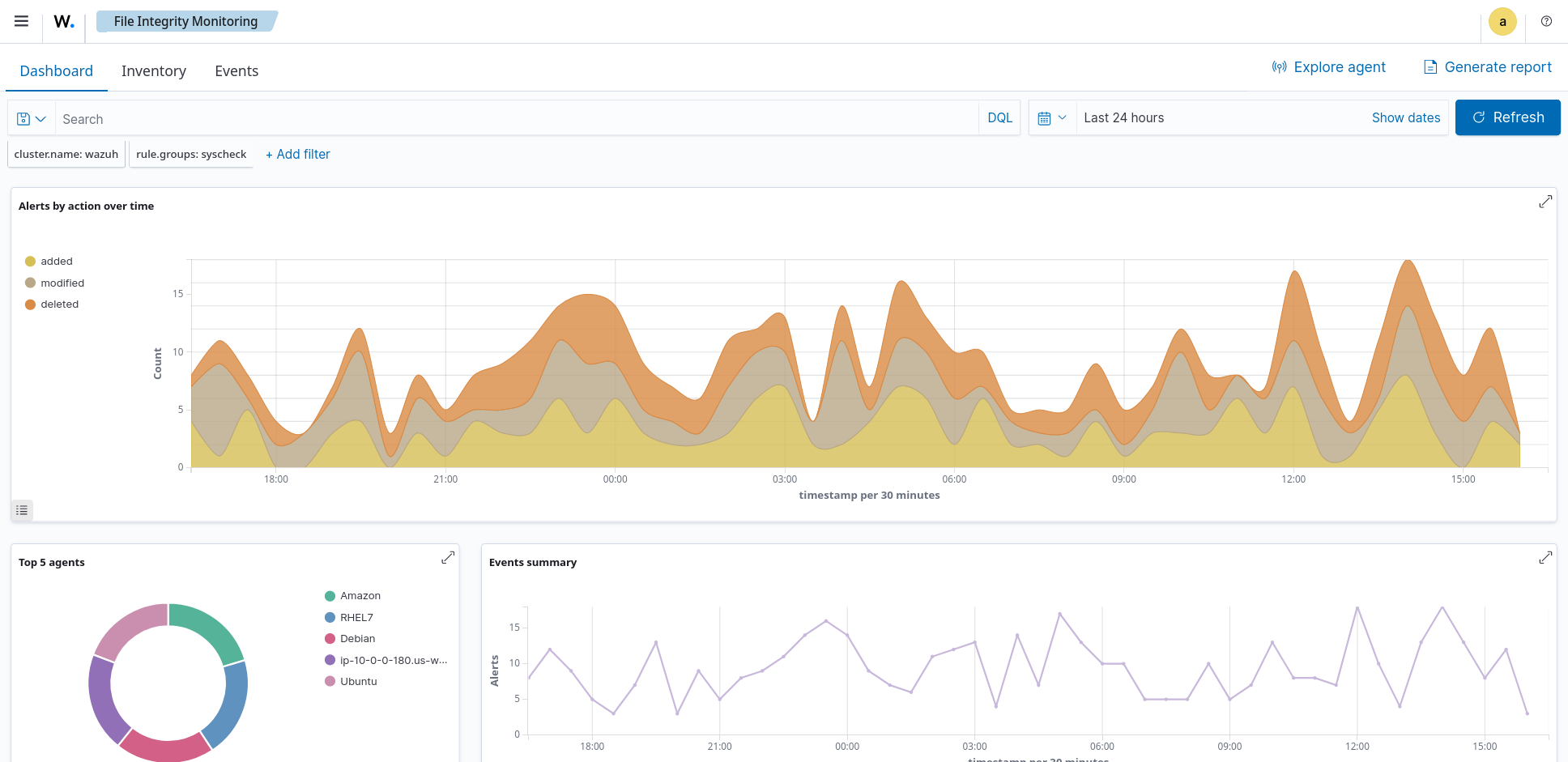
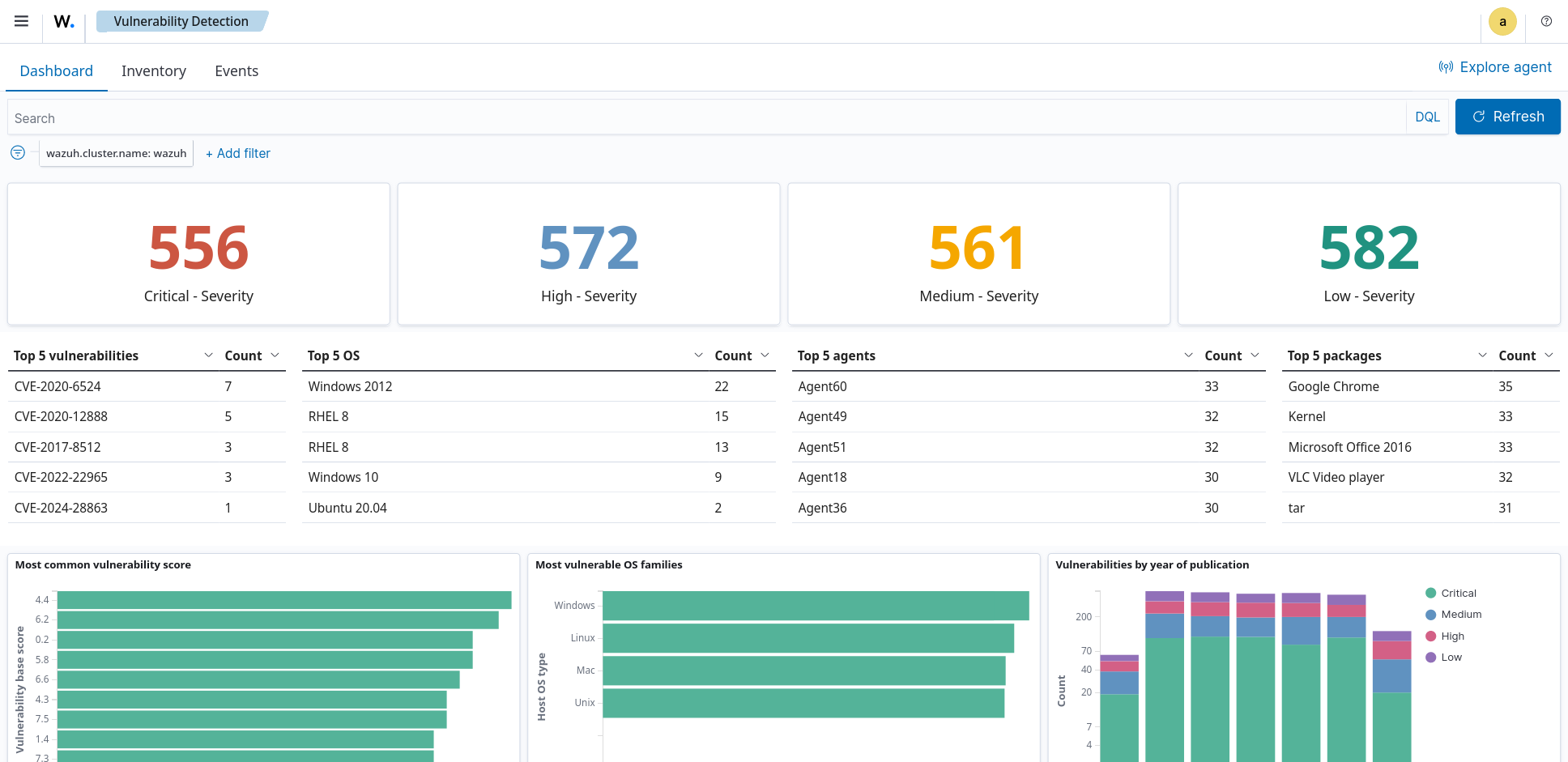
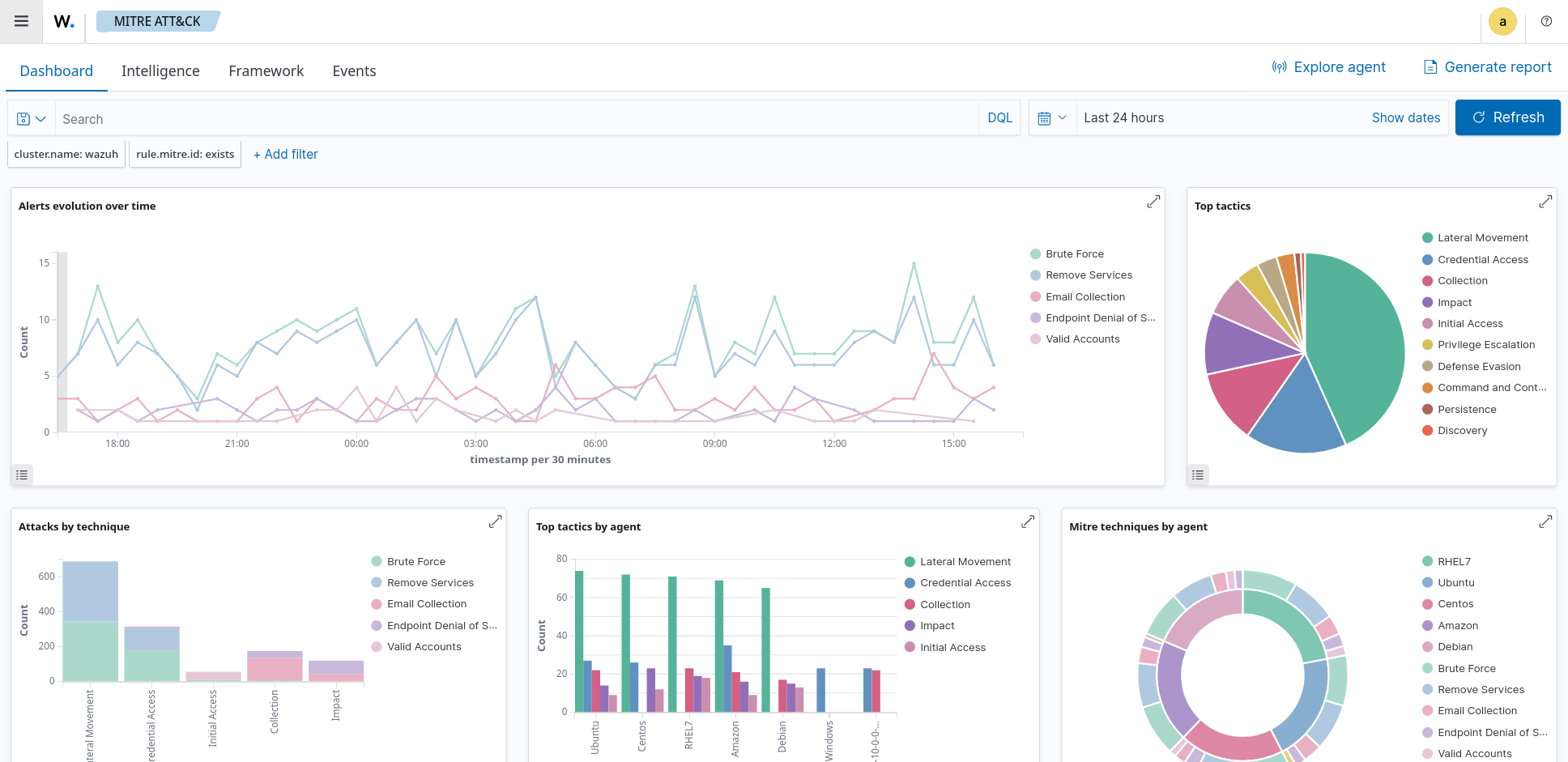
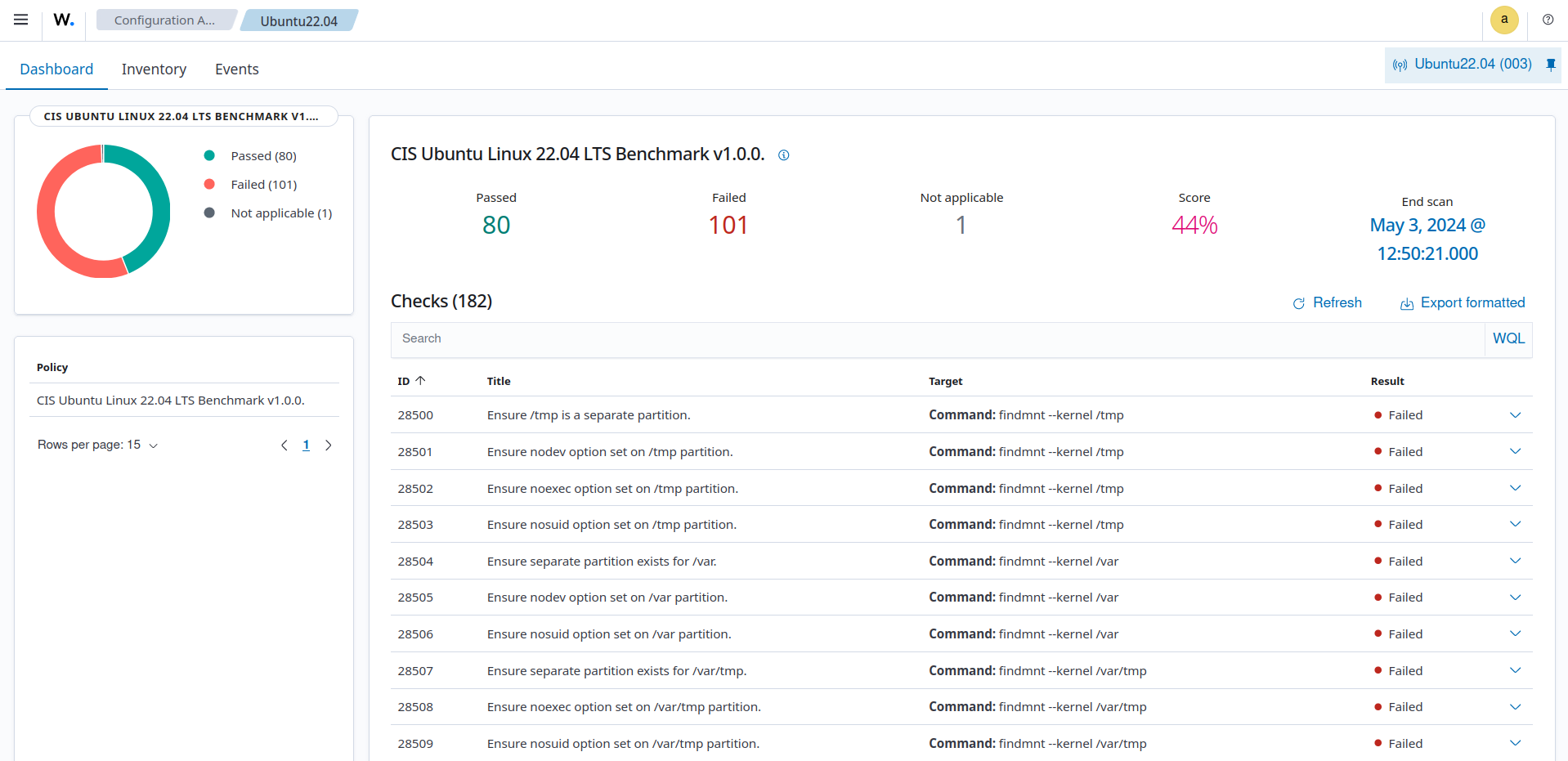
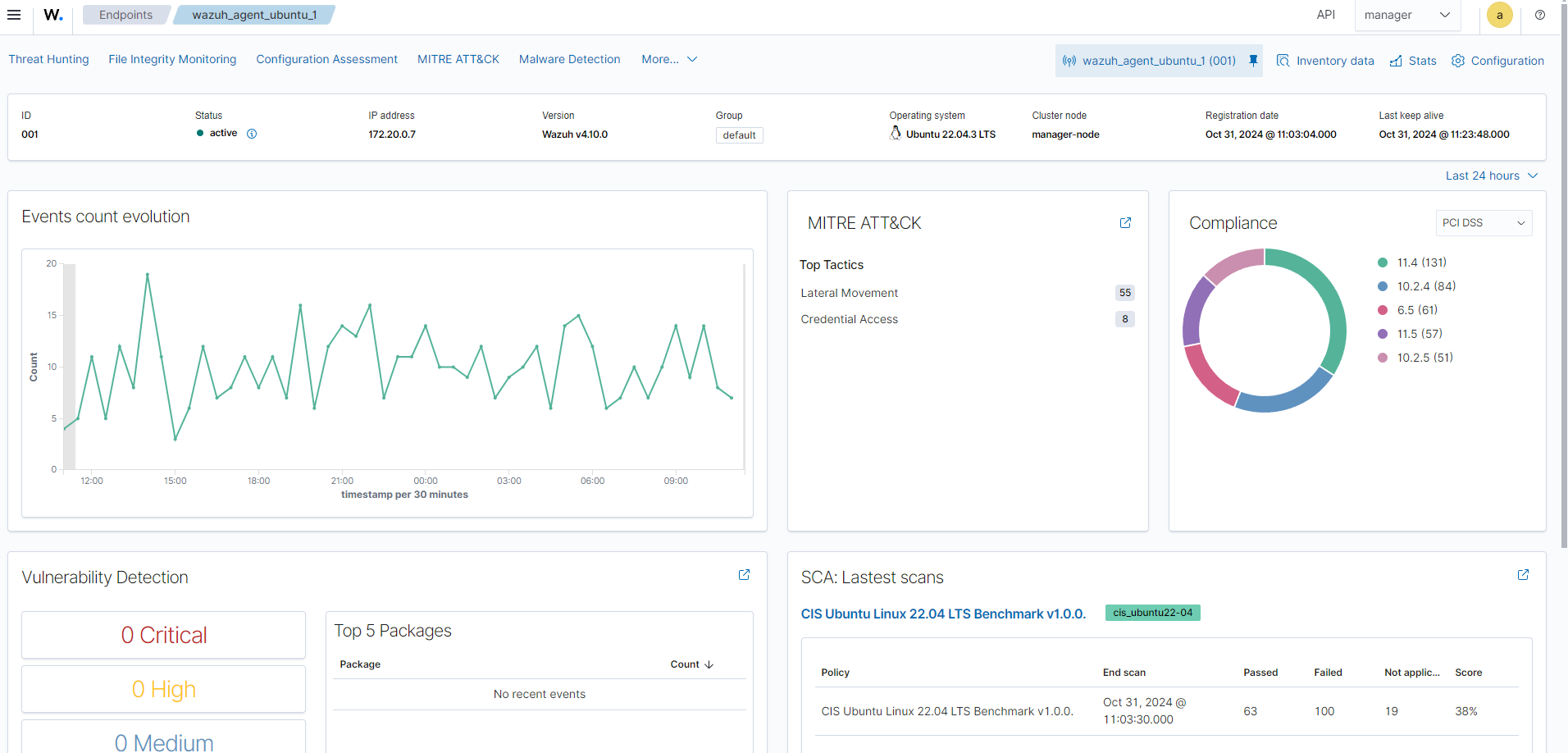
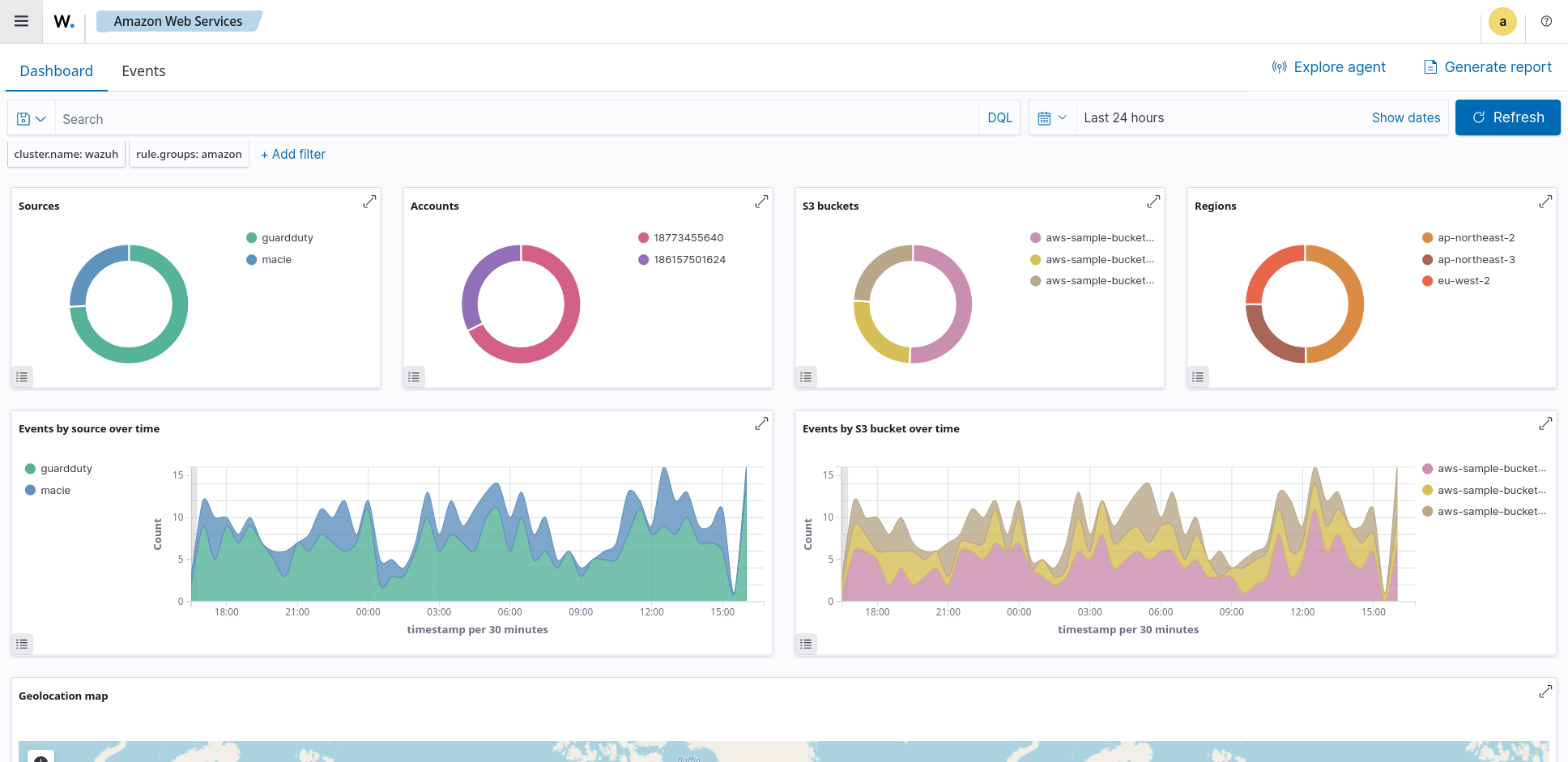
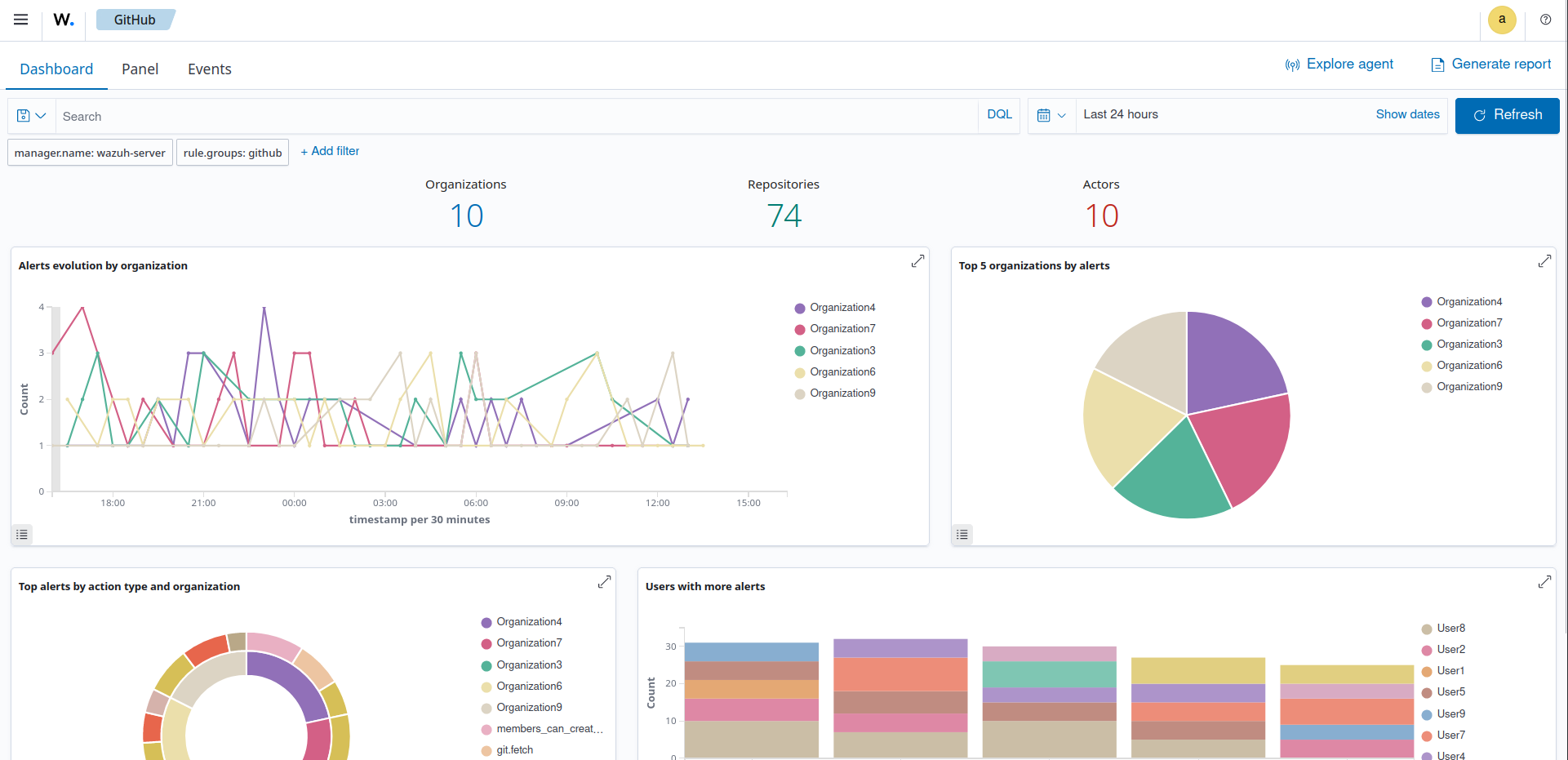
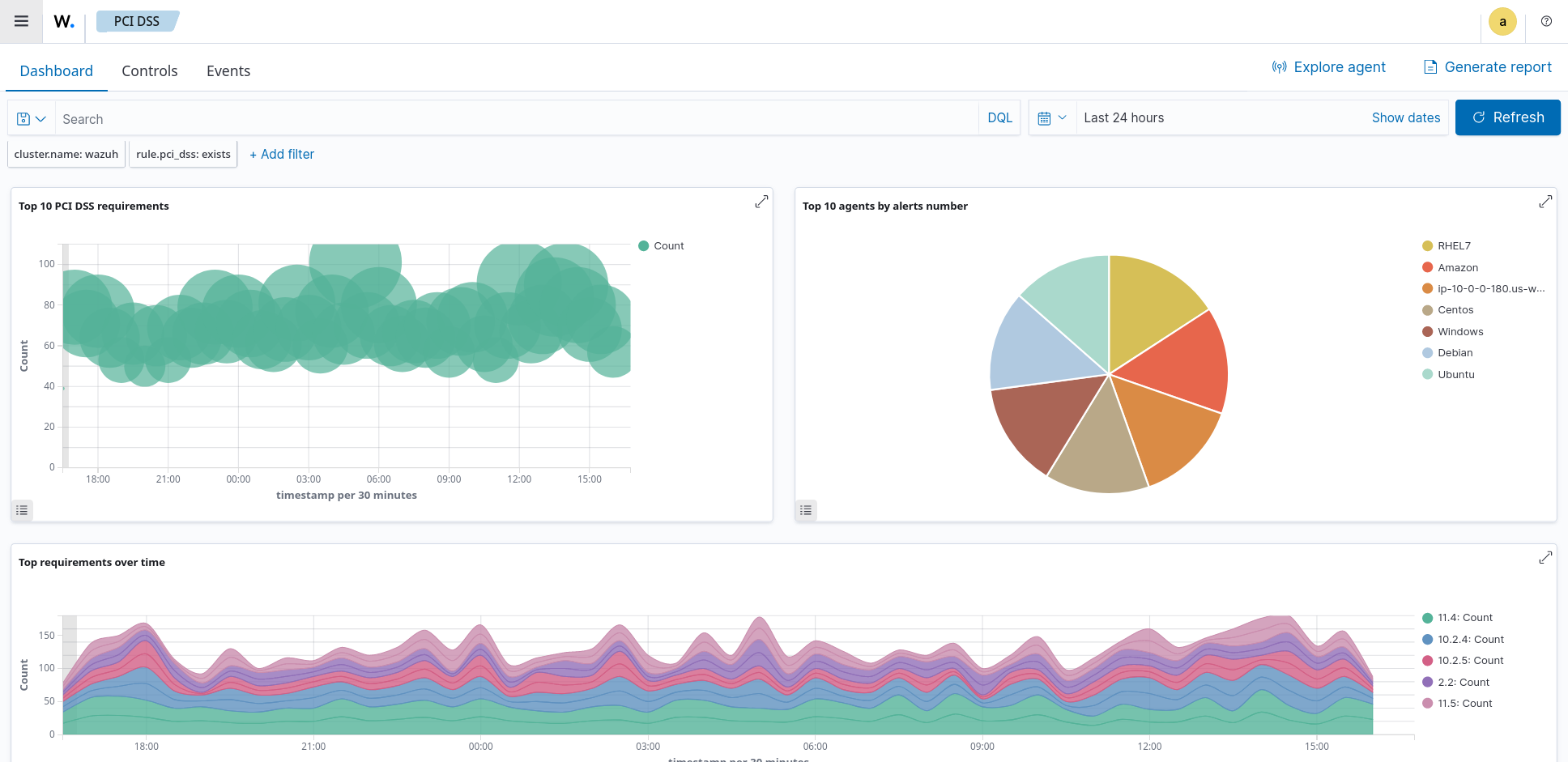
Screenshots
|
|
|
|
|
|
|
|
|
|
Building with AI and LLMs
You can use large language models (LLMs) to assist in building, managing, and troubleshooting your Wazuh deployment. To support accurate and efficient AI-assisted workflows, Wazuh provides plain text documentation and machine-readable guidance optimized for LLM consumption.
Plain text documentation (.md)
You can access most of the Wazuh documentation as plain text Markdown files by replacing .html with .md in the URL of any documentation page.
For example:
HTML page: https://documentation.wazuh.com/current/quickstart.html
Markdown version: https://documentation.wazuh.com/current/quickstart.md
Using the Markdown version is recommended when working with LLMs because it provides:
Cleaner content: Complete documentation text with minimal formatting noise and no navigation elements.
Full visibility: Content hidden behind tabs or expandable sections in the web UI is rendered linearly.
Structural clarity: Headings, lists, and code blocks preserve document hierarchy for better parsing.
Efficient context sharing: You can copy and paste entire guides into an LLM without losing structure or meaning.
AI agent standard (/llms.txt)
Wazuh hosts an /llms.txt file at the root of the documentation domain. This file follows an emerging standard to guide AI tools and agents on how to retrieve and prioritize Wazuh documentation content. It also instructs agents to prefer the current documentation version unless another version is explicitly required.
You can access it here: https://documentation.wazuh.com/llms.txt